The article will aid you to remove GANDCRAB v5.0.4 ransomware effectively. Follow the ransomware removal instructions given at the bottom of this article.
GANDCRAB v5.0.4 is the latest version of the nefarious GandCrab cryptovirus. The virus will encrypt your files and the criminals behind it will try to extort money from you to allegedly recover your files back to normal and return your computer to its original operation state before it was struck with GandCrab.
After files become encrypted, they will receive a random 8-letter extension. The ransom note’s name is formed by using this extension in capital letters and adding -DECRYPT.txt or -DECRYPT.html afterward. Slight variations in the ransom notes might exist with different versions of GandCrab cryptovirus. Continue to read the article and see how you could try to potentially recover some of your encrypted files and data.
Threat Summary
| Name | GANDCRAB v5.0.4 |
| Type | Ransomware, Cryptovirus |
| Short Description | The GandCrab ransomware encrypts files on your computer system and demands a ransom to be paid to allegedly recover them. |
| Symptoms | The ransomware will encrypt your files with an 8-random-letter extension and leave a ransom note with payment instructions. |
| Distribution Method | Spam Emails, Email Attachments |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss GANDCRAB v5.0.4. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

GandCrab Ransomware – Update February 2019

GANDCRAB v5.0.4 Virus – Update January 2019
The GANDCRAB v5.0.4 Virus keeps on spreading on a massive scale and the newest email campaign for it features an interesting script file. The file is named “Love_You_34029936-2019-txt.js” and poses to be a simple text file with the header “My love letter for you“. The file might be inside a .zip file with the same name. If the criminals have somehow obtained a contact list with known email addresses to the victims they send the emails to, that would be even more clever.
The JavaScript file will download and install the the GandCrab 5.0.4 ransomware as well as the [wplinkpreview url=”https://sensorstechforum.com/vmprotect-vmprotectss-exe-xmrig-monero-cpu-miner-remove/”] XMRig Monero Miner cryptocurrency mining malware. The following processes are run:
- wincfg32scv.exe
- 1119713827.exe
- 2987227227.exe
Among these suspicious processes, other files might also be added to aid the ransomware in maintaining its persistence on the compromised machine.

GANDCRAB v5.0.4 Virus – Update December 2018
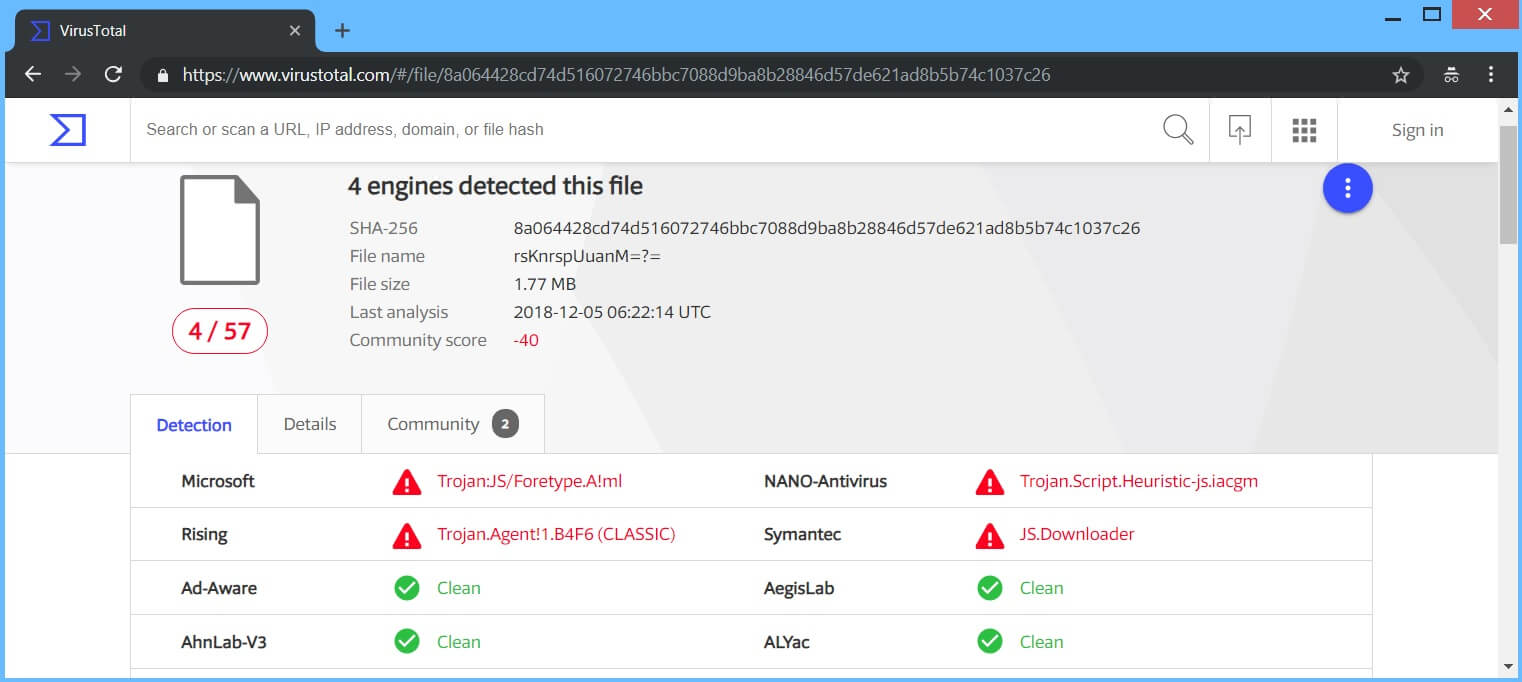
GANDCRAB v5.0.4 Virus keeps going like hot cakes in December 2018, just as it was when it initially came out. Over two dozen new samples have been reported by malware researchers and even more have been spotted in the wild. You can see one of them being dissected inside VirusTotal’s service, from the screenshot provided here:
In addition to all of those attack vectors, GANDCRAB v5.0.9 Cryptovirus is already out and new victims already have their computer systems compromised.

GANDCRAB v5.0.4 Virus – Distribution Tactics
The GANDCRAB v5.0.4 ransomware might distribute itself via different tactics. A payload dropper which initiates the malicious script for this ransomware is being spread around the Internet, and researchers have gotten their hands on a malware sample. If that file lands on your computer system and you somehow execute it – your computer device will become infected.
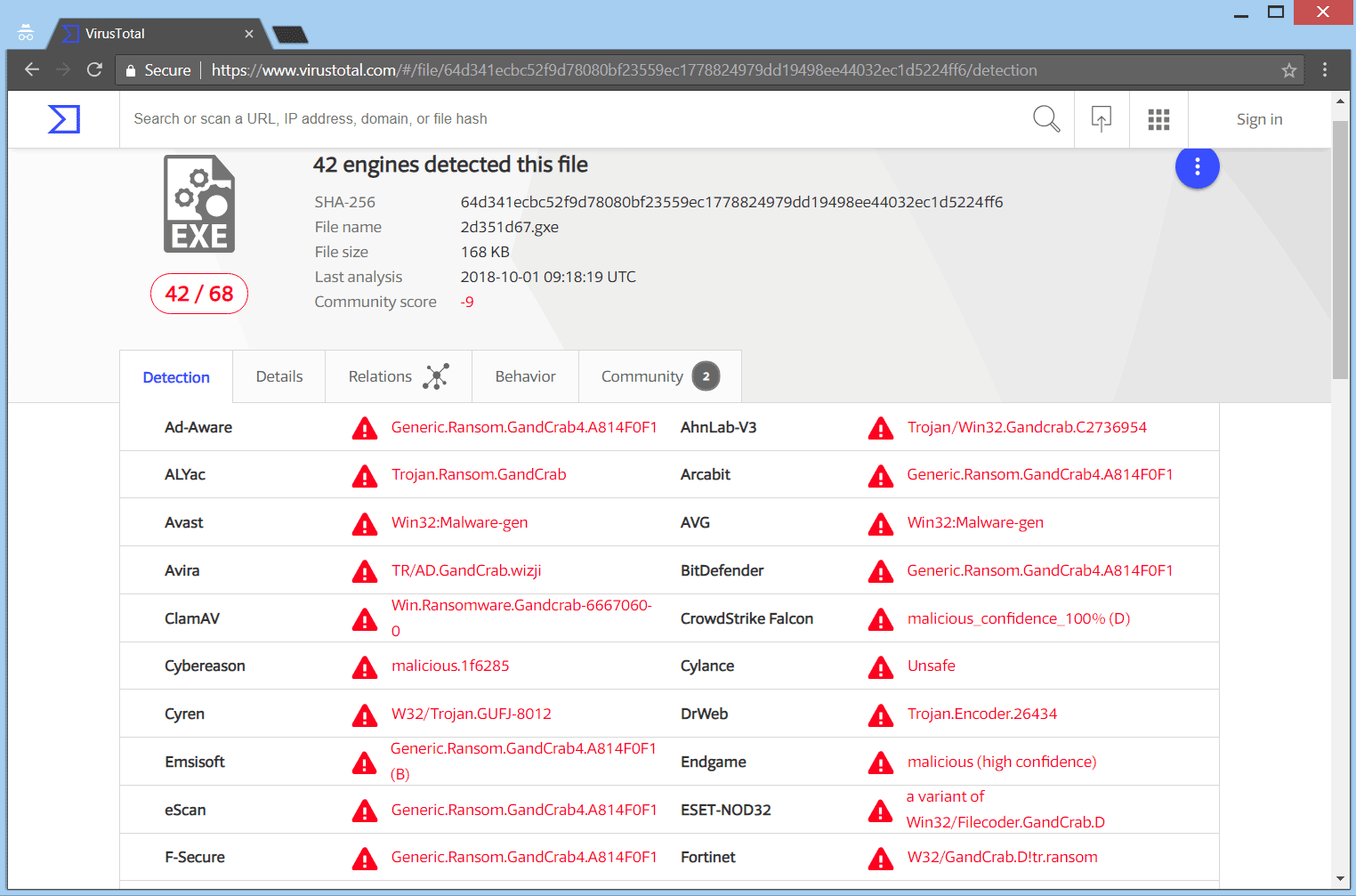
Below, you can see the payload file of the cryptovirus being detected by the VirusTotal service:
We have also been contacted by infected users that file-distribution trackers such as PirateBay have executables dropping the GANDCRAB v5.0.4 ransomware. Do not download cracked software and games from torrent sites.
Freeware which is found on the Web can be presented as helpful also be hiding the malicious script for the cryptovirus. Refrain from opening files right after you have downloaded them. You should first scan them with a security tool, while also checking their size and signatures for anything that seems out of the ordinary. You should read the tips for preventing ransomware located at the corresponding forum thread.

GANDCRAB v5.0.4 Virus – Technical Information
GANDCRAB v5.0.4 is a virus that encrypts your files and leaves a ransom note, with instructions inside it, about the compromised computer device. The extortionists want you to pay a ransom fee for the alleged restoration of your files. Previous GANDCRAB 5.0 versions are said to use the [wplinkpreview url=”https://sensorstechforum.com/cve-2018-0896-gandcrab-v5-0-1/”] CVE-2018-0896 vulnerability. That could be exploited with this new version as well. Other vulnerabilities and exploit tactics are not excluded from being used in addition to the one mentioned above.
Version 5.0.4 of GandCrab was spotted by malware researcher Ben Hunter (with Twitter handle @B_H101) earlier today (02.10.2018).
GANDCRAB v5.0.4 ransomware makes various entries in the Windows Registry to achieve persistence, and could launch or repress processes in a Windows environment. Such entries are typically designed in a way to start the virus automatically with each boot of the Windows Operating System. Below you will see the list with registries that are tampered with:
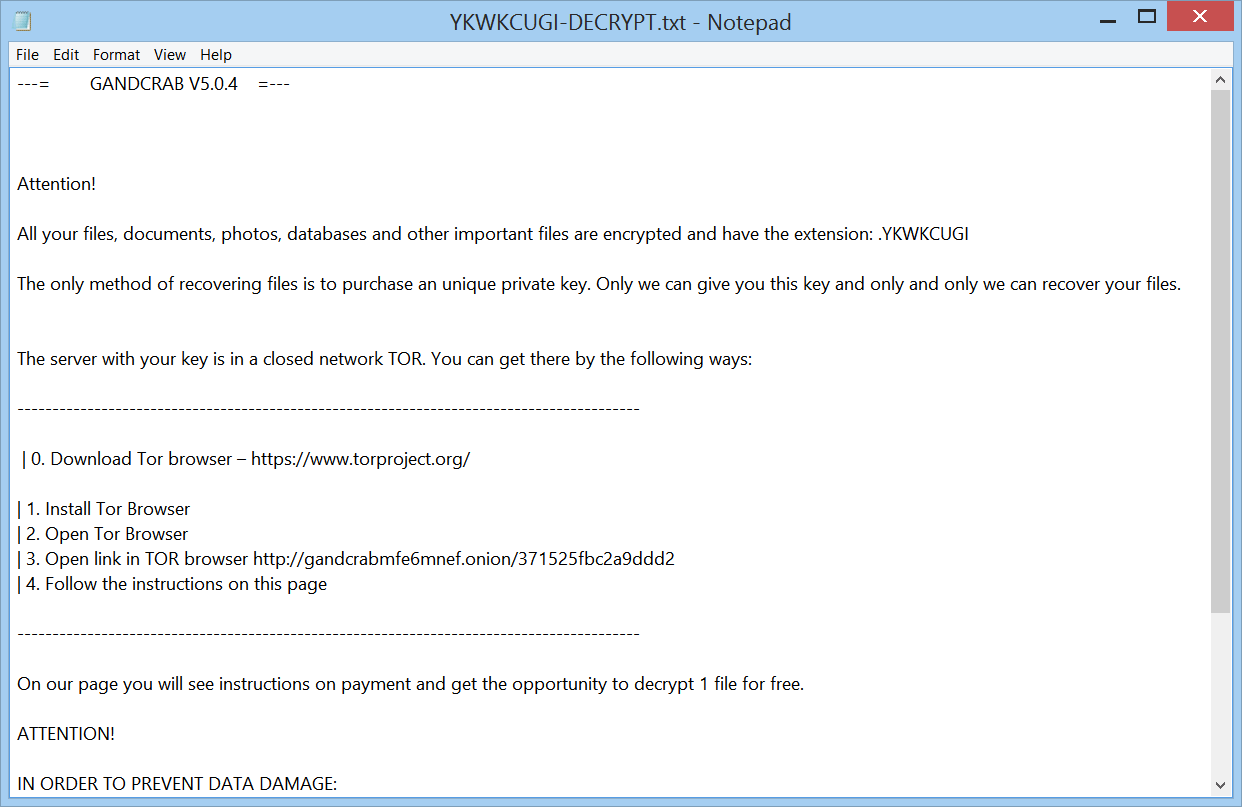
After encryption the GANDCRAB v5.0.4 virus will save a ransom note. The ransom note’s name is formed by using this extension in capital letters and adding -DECRYPT.txt or -DECRYPT.html, so as an example the note with instructions would be called YKWKCUGI-DECRYPT.txt.
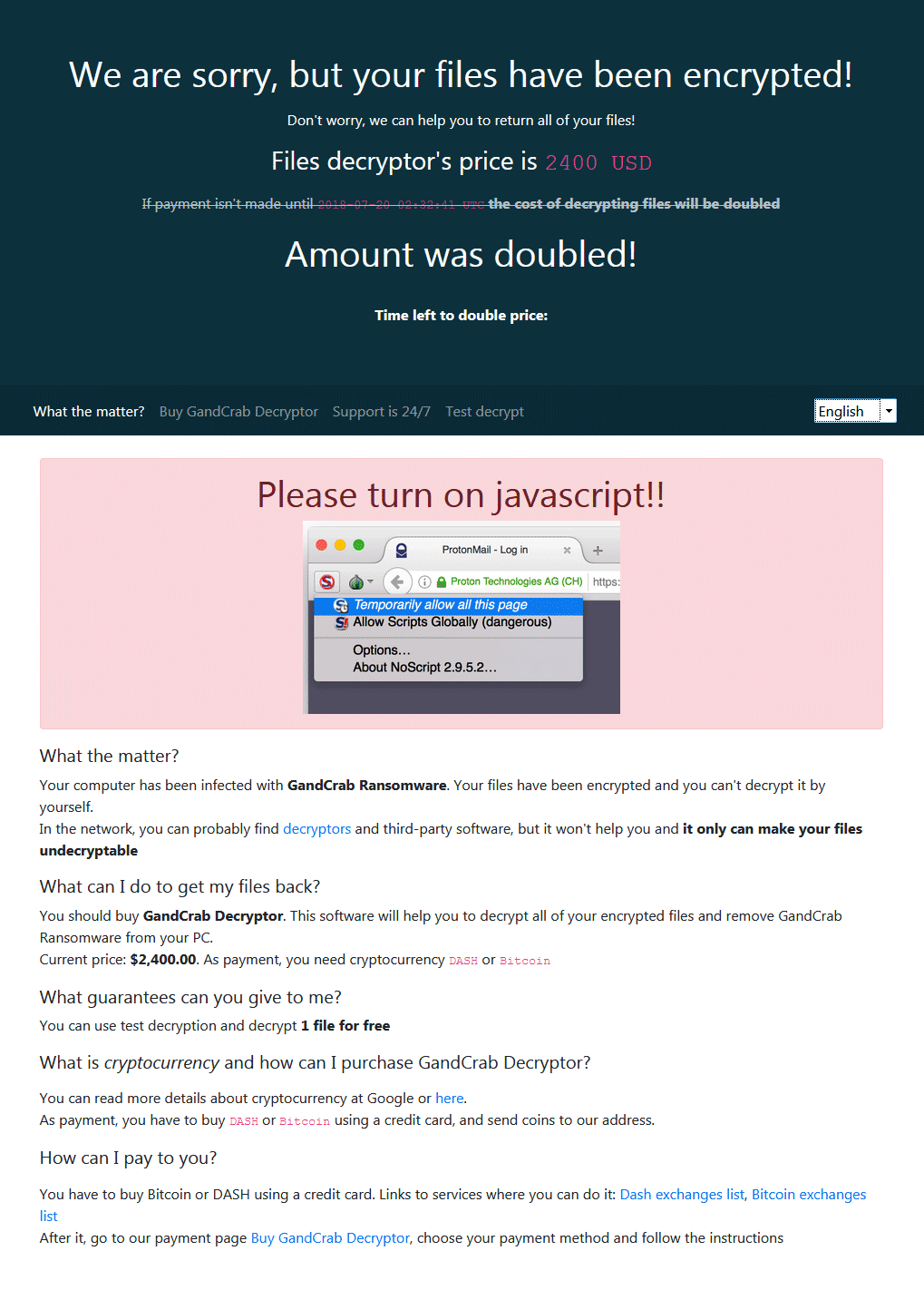
The ransom note is displayed below:
That ransom message has the following contents:
—= GANDCRAB V5.0.4 =—
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension: .YKWKCUGI
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————–
| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor Browser
| 2. Open Tor Browser
| 3. Open link in TOR browser https://gandcrabmfe6mnef.onion/371525fbc2a9ddd2
| 4. Follow the instructions on this page—————————————————————————————–
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW—BEGIN GANDCRAB KEY—
IAQAADcGuK20868jo rVSSQNHeCNCzn LVthNchP1cchrZ+ZK64yengprthG 1oan 1 BmSjZWIVyseGGDBKUiOnX4NfUDgoNh rthhDaVWAetprp+ystBhHoerAGVbtaprwIXUeKItyFQJUkFlmE+J9/91W3ngfXUDpB13408PijhAwijqUnWNZBMXD4TQrv… [REDACTED] —END GANDCRAB KEY——BEGIN PC DATA—
wfKD6iudumBkmpL8IRr4U7WxEFa3OW3tyzxyOuL12FYqvNmWPB5KYaxd5ZYqTpNRu3YM7nNWsbfaTHGHjR4qBMvz39M074b6dEHXDG/iHZJy8+LFIv/dmMngioqtOiJtTit2DjRIuBtNYA==
—END PC DATA—
Inside the ransom note it is described to visit a payment page hosted on the TOR network that looks like the following:
We are sorry, but your files have been encrypted!
Don’t worry, we can help you to return all of your files!
Files decryptor’s price is 2400 USD
If payment isn’t made until 2018-07-20 02:32:41 UTC the cost of decrypting files will be doubled
Amount was doubled!
Time left to double price:
—————————————————————————————–
What the matter? Buy GandCrab Decryptor Support is 24/7 Test decrypt
—————————————————————————————–
Please turn on javascript!!
What the matter?
Your computer has been infected with GandCrab Ransomware. Your files have been encrypted and you can’t decrypt it by yourself.
In the network, you can probably find decryptors and third-party software, but it won’t help you and it only can make your files undecryptable
What can I do to get my files back?
You should buy GandCrab Decryptor. This software will help you to decrypt all of your encrypted files and remove GandCrab Ransomware from your PC.
Current price: $2,400.00. As payment, you need cryptocurrency DASH or Bitcoin
What guarantees can you give to me?
You can use test decryption and decrypt 1 file for free
What is cryptocurrency and how can I purchase GandCrab Decryptor?
You can read more details about cryptocurrency at Google or here.
As payment, you have to buy DASH or Bitcoin using a credit card, and send coins to our address.
How can I pay to you?
You have to buy Bitcoin or DASH using a credit card. Links to services where you can do it: Dash exchanges list, Bitcoin exchanges list
After it, go to our payment page Buy GandCrab Decryptor, choose your payment method and follow the instructions
The message above, displayed by the GANDCRAB v5.0.4 ransomware virus indicates that your files are encrypted. You are demanded to pay a ransom sum in either Bitcoin or DASH cryptocurrency to allegedly restore your files. However, you should NOT under any circumstances pay any ransom sum. Your files may not get recovered, and nobody could give you a guarantee for that. Adding to that, giving money to cybercriminals will most likely motivate them to create more ransomware viruses or commit different criminal activities. That may even result to you getting your files encrypted all over again after payment.
In addition, a picture of Valery Sinyaev will be dropped by the ransomware with the following accusations:
“Valery Sinyaev destroy families, people, fire people, he is a asshole that believe he is god. Deserve it and more…stay tuned company if you don’t take actions against him!”
We see more and more people being the face of ransomware viruses, but they are mostly political figures or ex-politicians.

GANDCRAB v5.0.4 Ransomware – Encryption Process
The encryption process of the GANDCRAB v5.0.4 ransomware rather simple – every file that gets encrypted will become simply unusable. Files will get an extension composed of eight random letters. The newly added extension will be added as a secondary one, without changing the original extension.
A list with the targeted extensions of files which are sought to get encrypted is believed to be the same as for the original 5.0 version, as shown below:
→.1st, .602, .7z, .7-zip, .abw, .act, .adoc, .aim, .ans, .apkg, .apt, .arj, .asc, .asc, .ascii, .ase, .aty, .awp, .awt, .aww, .cab, .doc, .docb, .docx, .dotm, .gzip, .iso, .lzh, .lzma, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .rar, .sldm, .sldx, .tar, .vbo, .vdi, .vmdk, .vmem, .vmx, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xps, .z, .zip
The files used most by users and which are probably encrypted are from the following categories:
- Audio files
- Video files
- Document files
- Image files
- Backup files
- Banking credentials, etc
The GANDCRAB v5.0.4 cryptovirus could be set to erase all the Shadow Volume Copies from the Windows operating system with the help of the following command:
→vssadmin.exe delete shadows /all /Quiet
In case the above-stated command is executed that will make the effects of the encryption process more efficient. That is due to the fact that the command eliminates one of the prominent ways to restore your data. If a computer device was infected with this ransomware and your files are locked, read on through to find out how you could potentially restore some files back to their normal state.

Remove GANDCRAB v5.0.4 Virus and Try to Restore Data
If your computer system got infected with the GANDCRAB v5.0.4 ransomware virus, you should have a bit of experience in removing malware. You should get rid of this ransomware as quickly as possible before it can have the chance to spread further and infect other computers. You should remove the ransomware and follow the step-by-step instructions guide provided below.
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
Step 1: Scan for GANDCRAB v5.0.4 with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall GANDCRAB v5.0.4 and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by GANDCRAB v5.0.4 on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by GANDCRAB v5.0.4 there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove GANDCRAB v5.0.4





Step 5: Try to Restore Files Encrypted by GANDCRAB v5.0.4.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
1 Right-click on the decrypter and click on Run as Administrator as shown below:
2. Agree with the license terms:
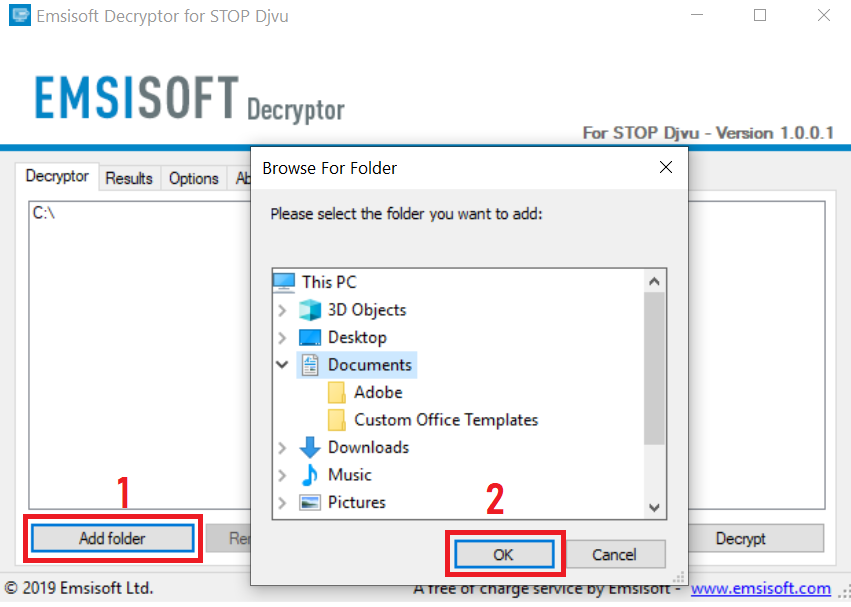
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
4. Click on "Decrypt" and wait for your files to be decoded.
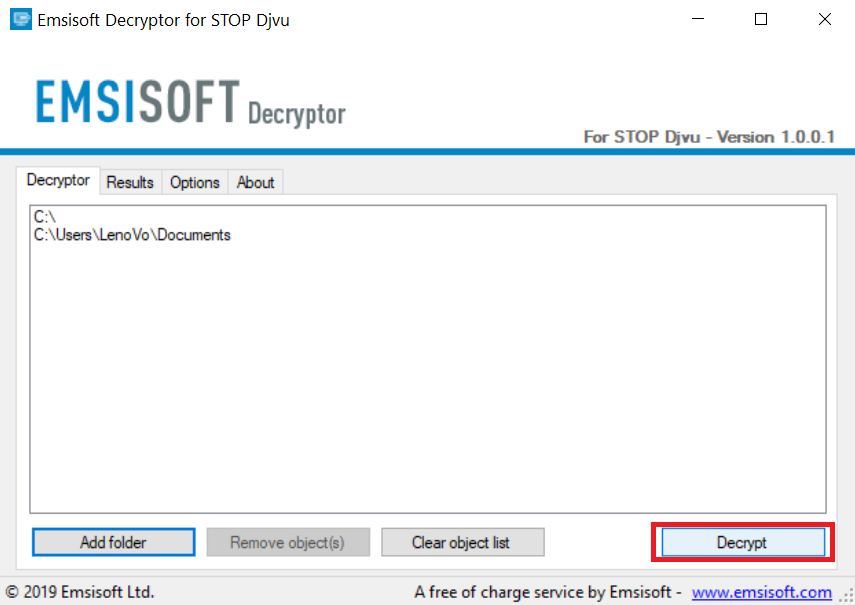
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and GANDCRAB v5.0.4 aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
GANDCRAB v5.0.4-FAQ
What is GANDCRAB v5.0.4 Ransomware?
GANDCRAB v5.0.4 is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does GANDCRAB v5.0.4 Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does GANDCRAB v5.0.4 Infect?
Via several ways.GANDCRAB v5.0.4 Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of GANDCRAB v5.0.4 is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .GANDCRAB v5.0.4 files?
You can't without a decryptor. At this point, the .GANDCRAB v5.0.4 files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .GANDCRAB v5.0.4 files successfully, then do not despair, because this virus is still new.
Can I Restore ".GANDCRAB v5.0.4" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .GANDCRAB v5.0.4 files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of GANDCRAB v5.0.4 Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate GANDCRAB v5.0.4 ransomware and then remove it without causing any additional harm to your important .GANDCRAB v5.0.4 files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can GANDCRAB v5.0.4 Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the GANDCRAB v5.0.4 Research
The content we publish on SensorsTechForum.com, this GANDCRAB v5.0.4 how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the GANDCRAB v5.0.4 ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.





GANDCRAB V5.0.4 *.tncmnygcon
Data is encrypted with “GANDCRAB V5.0.4 having extension of .EUPXEH.
Please help.
Hola buenos días me tocó el GANDCRAB V5.0.4 con la extensión ( odokubbgw )
he conseguido eliminar el bicho, pero necesito ayuda para la recuperación de los
archivos.
Gracias TENTENIGUADA
Data is encrypted with “GANDCRAB V5.0.4 having extension of .FKVVQQCE
Please help.
Hello panda842, Awais Khan, TENTENIGUADA and Asim Javed.
As said in the article encrypted files will receive a random 8-letter extension. You can try the decryption tool available for previous GandCrab versions and hope it to work – sensorstechforum.com/decrypt-gandcrab-ransomware-files
I have tried but it says “Intionalization failed”
Have you tried more than once?
I have already tried this tool but didn’t worked out. It does not identify this type of encryption and display message ” No Encrypted files found”.
This tools work on GANDCRAB v 5.0.3 while new encryption is of GANDCRAB v 5.0.4.I have searched on different forum and found that decryption tol for this ransomware is not yet developed.
That is very unfortunate, Awais Khan. However, if there is a decryption method for the previous versions, maybe the newer variants could get decrypted as well…
What if I said “to hell” with all my files and did a system restore? I didn’t have much on my laptop and know how to find whatever was lost.. But will it be gone for good this ransomness?
If you do a system restore, you might restore the ransomware’s files as well. I wouldn’t advise that, but if you don’t care about losing files, use an anti-malware tool and then re-install your computer system. But know that if you do a reinstall, you won’t be able to use a data recovery program later, if you change your mind. Good luck!
Best Regards
.LIAUZG
But the key is important, the extension is random
True – the extension is indeed random, but thanks for reporting. Very unfortunate how this version proves to be so tough to decrypt. All of you will be notified if there is a decryptor found or another method to recover files.
Georgios, a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Hallo,
bin neu hier und leider bin ich auch betroffen. Meine ganzen Bilder ca.45GB sind verschlüsselt mit Gancrab v5.0.4 es wäre echt super wenn es eine Lösung gibt.
You can try the decryption tool available for previous GandCrab versions and hope it to work – sensorstechforum.com/decrypt-gandcrab-ransomware-files
However, users report that they get errors, so you can be unlucky.
Es gibt für GandCrab 5.0.4 noch keine Entschlüsselung. Ich hoffe, die kommt bald…
I find it interesting that an entire industry has evolved professing they have the cure to this Gabdcrab Ransomware. If only you purchase my malware removal tool, you will be saved.
After so very many charlatans have created so much malware and caused so much grief why would we simply believe that a Saviour can cure your computer if only we provide them with money, rather than the GandCrab Cabal?
Hey Bud,
there are charlatans, but we don’t make malware,
and we don’t lie. A malware removal tool will remove the malware, but it won’t decrypt the files.
Plus, users have a choice on whether they want the malware to stay on their machines, or to remove it, either manually or using an anti-malware program (regardless of which program they choose, as long as it is legitimate). Nobody is telling you what to do. And there is a GandCrab decryption tool made by BitDefender, but it doesn’t work for all versions (yet).
NLJKZMQMNF v5.0.4 malware bytes stopped it a little late i got infected i don’t mind i just switch to another computer and carry on what i was doing
The threat keeps on spreading it seems. Sad to hear that you are also a victim of it. You will be notified of the decrypter gets updated to properly work with v 5.0.4. For now you can try it, but people report they even have problems with v 5.0.3.
Anyway, thanks for the update and I wish you luck in the future to not get hit by any malware. Make backups of your important files on another device, so you can recover them if you get hit by ransomware again.
Kish, a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Just infected today.The malware has encrypted all my files in one drive folder linked to the pc,not much can I do except formatting the pc and let all files gone .
Hey Man,
formatting is an option, but you will lose your files that way.
Before doing that, you could also make a backup of the encrypted files and ransom note in case a decrypter program is released. In case you would like to have some files back, that is.
Hi, Mr Ventsislav Krastev
On November 2018, I discovered that my PC was affected by GANDCRAB V5.0.4 by referring to HRMGI. It seems to be everywhere in my computer. I have downloaded Bitdefender GandCrab V1, V4, V5 .
I have also followed the steps properly. Each time I try to scan using Bitdefender GandCrab V1, V4, V5 Decryptor – system looking for encryption key. After a while, it is shown that initialization failed.
Hi, Amr Helmy.
I am not Mr Krastev, but I know that the current BitDefender’s decryptor does not work with version 5.0.4 of GandCrab and some people even have problems with v5.0.3.
V4 means v4.0.0 (and maybe v4.xx) and not 5.0.4. BitDefender might develop a decryptor soon, but that is uncertain.
Best Regards,
Tsetso Mihailov from STF
My PC has infected by GANDCRAB V5.0.4 – extension: MLKOL. They ask me for $450 to provide the decrypt tools, and start count down from 7 days.
Any work around to get back some files?
Hello Triet Tran,
Currently, there is no remedy for that version of the virus. However, malware researchers might make a decryption tool soon. Keep your files for a few months and see whether such a tool gets developed.
I got the GandCrab v5.0.4 on Nov 27. with the Encryption extension of .pkwxuuzxut. Hopefully a decryptor will become available soon. As of right now, I am transferring all my files 2+TBs to and external for saving until I can decrypt them. I hope I will be notified when a decryptor comes available for this version
Hello Todd Wantz,
hopefully you are right and the current BitDefender tool gets further developed to decrypt files for GandCrab versions 5.0.3 and above.
You have done the right thing to save your files. You will be notified if such a tool becomes available.
Todd, a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
My PC has infected by GANDCRAB V5.0.4 – extension: FAAEYA . Hopefully a decryptor will become available soon .
We at SensorsTechForum are hoping for that as well.
Infettato da GANDCRAB V5.0.4 estensione .emchw. Nessun tool funziona nel decriptare i file..
Hello Angelo.
Unfortunately, yes, no tools work in decrypting GandCrab V5.0.4 files for now.
Mi PC se ha infectado por V5.0.4 GANDCRAB – Extensión: OAFCHZES. He probado la utilidad de bitdefender pero al scanear sale el mensaje de initializacion failed. Por favor me podrían dar algún consejo que no sea pagar al delincuente?
Hello Bernardo.
Wait 1-2 months. If BitDefender has made a decryption program for the previous variants, they should be able to make one for the newer 5.0.3 and above. Let’s hope a newer tool is released soon.
Locked with GandCrab 5.0.4 (extension: KRPWPQLU)
Please help
The extension of GandCrab v5.0.4 is random for each user. Currently there is no decryptor, but one might be made soon. Just wait – help might be on its way soon.
UPDATE! There is a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Muchas gracias Tsetso
I also have been encrypted with Gandcrab V5.0.4 with the suffix ‘.rflnsfdbuo’. Will I be informed when and if a decryptor is found please?
Yes, Andy Loran.
We will try to inform everybody as best we can.
Andy, good news! I’m notifying you of the new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
ik heb een grandcrab decryptor 5.0.4 bemachtigd na kleine betaling te doen, werkt dit voor alle gehackte personen of alleen die van mij?
I don’t know. The decryption program might be universal, but the key for each individual PC to be different… You can share the decryption program if you want.
We got the Gandcrab 5.04 Ransomware last week. (w/e 14/12/2018). We decided not to pay and just reset Windows 10. The Windows 10 system reset didn’t work. This might have been the plan of the ransomware developers, but we don’t know. However, we had recently done a Windows 10 reboot on a USB stick, and we used this to do a compete reset. The result was very good. Afterwards, we searched our drives for all files and folders with the random encryption string. We found several minor folders and files still encrypted and left on the system – eg drivers, intel log files, etc. We added “old” to the folder names, put these into a separate folder, where they will wait until we see what will happen, if anything. They’ll be deleted after a month or so if they prove to be not needed. The reset procedure left the old ransomware-encrypted Windows 10 system files on the system and it put them all into a folder called Windows – old. After the reset procedure, we deleted this folder immediately. Then we simply set about re-installing all our programs again. Overall, we were very happy with the reset procedure. We took a really good lesson from it all – be careful what we download from dubious sources, and be extra careful about false positives!! This was our story. We hope that it might help you. The souls who are involved in this ransomware are simply playing silly games, and don’t realize the consequences that their actions will bring them. Universal law of cause and effect cannot be gainsaid!
Hello Amsha,
thank you for sharing this story.
It proves that you really have to be careful from where you download files and do more research on the source and files.
It also proves that having a backup is the best bet to prevent your files from being lost forever. Ransomware is really hard to remove, so I am not surprised you found the ransomware files after the reset. I won’t be surprised if there are more files left, including registry entries and whatnot.
Happy that you have recovered the system and can re-install the programs you need.
Happy holidays!
Hello Tsetso,
Thank you for your sympathetic comment. You are quite correct about having a good backup to save files being lost. Our backup system saved us from a catastrophe with this Ransomware.
To add further: we searched the Registry for the encryption string and found only one instance of the string, and that was just the existence of the string in file extensions (FileExt) in Internet Explorer, and we deleted it straight away. This is an important realization when trying to be rid of this Ransomware. It means that a Windows reset does in fact get rid of almost everything associated with the Ransomware files. The few remaining instances of it in both the file system and the Registry were harmless – lame ducks with no power or mojo.
I am happy that you fully exterminated the ransomware, Amsha!
Yes, a reset could really help if it works properly, when you have backups and don’t care about the encrypted files. Deleting everything related to the ransomware is important, as the threat might find itself in your PC system somehow. Better be safe than sorry.
I’m going to find this cock sucker, cut his face off, then wear it when I murder his entire family starting with the youngest member.
anyways, I have 5.0.4 . how will I know when the decryptor can decrypt this version? I hope its soon, but Im willing to wait!
Thanks guys!
Hey Evan,
your frustration is understandable. We at STF also hope that the new version of the decryptor will be released soon. You will be informed here on the comment section and the article will have an update message.
Evan – a new GandCrab Decryption tool got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Bonsoir
moi c est GANDCRAB V5.0.4 extension WRMUUI , tout mes fichiers ont été cryptés les photos de ma mère morte y a 1 mois plus des vidéos elle était malade …..je n`ai plus rien j`ai essayé l’outil BitDefender mais rien , j`attends j`espère…..
Bonsoir Rens,
never lose hope! I strongly believe that researchers should be able to crack the 5.0.3 and 5.0.4 versions of the ransomware soon. Just wait and maybe in January there will be a decryptor. I really can’t give a prediction, but I hope we will see good news in the near future.
Hello friends, I have been hit with good old Gandcrab 5.0.4. Managed to remove the adware/malware/ransomware programs using malwarebytes and EEK.
I have an Asus laptop and all the encrypted files are in my C:\eSupport folder. This folder appears to contain the laptop hardware drivers and recovery software.
I’ve got most stuff backed up and am happy to format but does the location of the encrypted files mean a full format is likely to not work and destroy the laptop altogether?
I thought the recovery software would be on a partition? Sorry I don’t know a great deal about this and don’t have a recovery disk unfortunately.
Any advice appreciated.
Hello Vinod,
the laptop cannot be destroyed. You can damage the Operating System, so formatting without being able to install the OS afterward will damage it and you will not be able to boot it afterward. So, before doing anything, just make sure to download an image of an OS installation setup on a USB or a Disk. You can probably format the other partitions and manually erase the registry entries of the malware, but first make sure you have a backup and the OS prepared, just in case.
Move the Support folder to a safe place, too.
i also have been encrypted with Gandcrab V5.0.4 with the suffix ‘.PHAEUMI’. Will await for decryptor
Yes, there is no working decryptor for v5.0.4 yet, so that is your best option – save your files and wait.
i have been encryted with GandCrab 5.0.4 with .DJAWTN. Hopefully the decryptor available soon… but for a while, what should i do ? do this save if i just waiting without do anything to my pc and keep to do some work as ussual with it?
That is your option – save the files that are important to you and wait for a decryptor. The previous decryptor needed 1 encrypted file and its non-encrypted original equivalent to decrypt files. So you could remove the virus and continue to work.
Que les puedo decir tambien fui de alguna manera contagiado de GandCrab v5.0.4 y mi maquina es de contabilidad ya se imaginaran que dolor de cabeza me esta dando ahorita mas que es fin de año…. pues ya probe todas las herramientas disponibles….pero ninguna funciono es de seguir esperando entonces…….
Yes, version 5.0.4 is not decryptable yet. You just have to wait, although no one really knows how long it is going to take for a working tool to be available.
i also have been encrypted with Gandcrab V5.0.4 with the suffix ‘.myqtqrz’. Will await for decryptor
Hi,
I was infected at 11:20 am on December 26, 2018 with GandCrab 5.0.4 with extension QXFCEHV (extension is in caps). Many files are encrypted and some files are not. I cleaned/killed the virus with scans from Malwarebytes and Avast, however, I notice that there appears to be something, remnants or something that tends to return with every restart or boot because I have removed the same file over and over again and now I notice I am not removing it, but I haven’t restarted either. Right now I am going through every file to see and a QXFCEHV-DECRYPT.txt file or the ransom note. Prior to understanding this crap a little better, I attempted to reinstall my OS and guess what? I could not as it stated things such as my user profile was missing. I tried to boot into safe mode and I couldn’t it kept giving me a wrong password message when I would go into safe mode and sign in. So, right now at this moment, I am trying to recover anything that I can recover. My first recovery run was sort of a test run to see if I could do it since it seems that there are things I cannot do. I used Disk Drill once and now I am using EaseUS recovery once. I am going to get an external drive and recover all I can to this drive to hold. Afterward, I am going to contact the PC manufacturer–talk to them–then I’m taking it to be professionally wiped clean and have the OS reinstalled since I cannot do it. I am praying for a new decryptor soon and until then I have kept those encrypted files so I can decrypt them later. One thing I do know is, no matter how bad something is, there is always someone that can find something to defeat that bad something. Nothing is original, better manipulated and mixed up, but not original. A working decryptor will be released. I wish the infected family nothing but the best. Keep your heads up! Reply with anything you’d like to tell me or add. Thanks so much!
It appears that GandCrab 5.0.4 is much more dangerous than its previous variants. We at SensorsTechForum are sorry to hear that this misfortune has happened to you and your computer. You are on the right track. It might be some registry settings that the cryptovirus made, which make the virus re-adding files on every boot. To remove them, you usually need to be in safe mode or find a tool that removes such. However, it could be that another, harder to detect, malware is on your PC helping the GandCrab ransomware.
Nobody knows for sure that there will be a decryption tool released, but hopefully there will be.
Hi again…oh yes, registry yes, I tried to rip them out using Regassassin…and no success…it told me that it could not remove the key(s). So I am truly baffled so I will stick to the plan I am working now. I don’t know what else to do but pray every day, so I will continue. Thanks so much!
Di
No problem! And if one counter-part of the virus is not working, the thing as a whole shouldn’t work either. Maybe the registries are over-written and there aren’t bad ones left. Hopefully, you have eradicated the threat and you won’t have problems after this point.
Hi again…I have a question…is every ransom note the same in which only the extension is changed? or are keys different for everyone? I am trying to understand a little better.
And another question… does it help to post the ransom notes received since they contain keys? Helping..in a way to spread information and to educate others or no?
Thanks!
The extension and ID are different for each infected computer system. Therefore keys should be different, too. You can post the ransom note if you think it might help, but the general text should be the same as in the article. The keys inside the ransom notes might help researchers differentiate versions and if a decryptor is made, to help for the tool to recognize the specific version. So, if you want – you can share, of course.
My computer was infected with GranCrab 5.0.4 too with the extension URZDT on Dec 28. It encrypted about 540G of my data! I moved all encryted files into one subfolder. The reason it did so much on my computer was I did not know how to stop it. Could not kill it from Task Manager, every time I reboot my computer it ran again and windows prevented me to delete the source files. I finally shut down windows and booted it into safe mode, deleted new folders created by malware, removed all suspicious executable lines in Run>Start, registry Run & RunOnce. Then I rebooted windows and installed a malware tools. My computer is now clear of the ransomware but I have a big scar from that. Hopefully, there will be a decryption tool soon for this GrandCrab 5.0.4
Sorry to hear that the virus took such a big toll in your case. We at STF are waiting on a decryption tool as well. You will be notified if such a program is released.
Nguyen, a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
extension GGCEGFLQ
Is it decryptable?
If it’s GandCrab 5.0.4 – it is not decryptable (yet). By judging the length of the extension, I’d say this is 5.0.4 but there is a chance it could be an earlier variant. Try with this decryption program: sensorstechforum.com/decrypt-gandcrab-ransomware-files
Bonjour je viens d’être infecté aussi et l’extension est ZLUZQQS. S’il vous plait que puis je faire pour récupérer mes donnés ( des fichiers 3D à rendre avant fin février 2019 ) .
Try the decryption tool of BitDefender : sensorstechforum.com/decrypt-gandcrab-ransomware-files
If it doesn’t work, then you will have to wait for a new version of the decryption program.
gandcrab 5.04 extension .zsodezbz.
Please help me.
Unfortuantely, GandCrab 5.0.4 is undecryptable at the moment.
My GandCrab version is also v5.0.4
The extension I got was .GCIPKJSOBT
I am hoping that you can help us all.
Thank you so much and more power
Hi Adam, unfortunately, there still isn’t a decryption tool available for this ransomware. We will update our article once such a tool is released.
As a GandCrab 5.04 victim, I became a victim because of Kaspersky.
I don’t think Kaspersky doing or planning to do something about it. I shared my experience and files with Kaspersky for the problem but the answer was not satisfactory.
There was an .exe file in my Laptop. Before clicking and running the file, I check the file with Kaspersky. After scanning the file Kaspersky reported the result as “There is no threat”. So after being sure with the updated Kaspersky, I clicked on the file and it destroyed my files. After communicating with Kaspersky, the representative said “Kaspersky is working on it and planning to continue to study about it”. Funny, isn’t it ? I told them that these type of malvares exist since 2013 and you tell me that Kaspersky is still planning to do something ? When you sell your product you say it is the best software for Ransomewares, but you don’t have anything for any version of GandCrab. And after I scanned the file, giving a report like “there is no threat” was not acceptable. Your software may not clean it but at least, it should detect the malware instead of saying “there is no threat”.
So I’m very pissed of with Kaspersky because it misled me and caused this problem.
For starters, I don’t know how kaspersky operates, but that is strange indeed.
The GandCrab ransomware is still widely spread and there can be from 30 different samples to many more per day for this cryptovirus alone. Maybe you were unlucky and got a really new sample of the virus that infected your computer.
I am really sorry to hear about your experience. You should run a second layer of defense, like a specific anti-malware tool, anti-ransomware tool, a firewall software, a sandbox… anything that adds another layer of protection.
Most of all, you should make backups of your important files on an external device that is not connected to your main computer system. If your files become encrypted, you can always recover from backups. Note that even cloud backups have reportedly failed from time to time, so having more than just 1 backup is recommended.
Bonjour, ayant toujours monté et installé windows moi-même j’ai toujours fait des partitions pour ne pas mélanger system et les divers documents. Donc infecté par gandcrab 5.04 le 19/12 avec extension BGUBOEJG, j’ai d’abord désinfecté mon ordinayeur et formater les 2 partition systeme et windows. réinstallé windows 10 avec tant qu’à faire la version 1809. Mes documents cryptés seront donc récupérable pour le jour ou bit défendeur aura créé ce décrypteur pour cette version 5.04.
Presque tous mes documents et photos et films (environ 70 %) ont été crypté, il n’a pas eu le temps de tout crypter avant que j’éradique le ramsonware mais il a quand même fait du mal.
J’espère donc qu’un décrypteur verra le jour bientôt et que vous pourrez m’aider..
Merci
Bonjour, Jacques!
We cannot help you at this time, as GandCrab 5.0.4 is still undecryptable. We hope that a newer version of the BitDefender decryptor program is released soon, too.
Update February 2019: A new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
bonjour a ts meilleur vœux!!! infecte comme beaucoup .NSVDQN mais peut apres avoir fait une reinstallation compléte donc pc vide mais disque dur externe branche fuck
pour savoir si j’ai “bien” fait pour virer le virus
j’ai debranché le hdd externe “contaminé” ou plutôt “CRYPTE”
j’ai formaté et reinstallé win 7 a l’aide de ma clé usb ts les driver maj ok
installation Kaspersky essai scan il ne me trouve aucun virus meme sur l’externe
contrôle avec spyhunter 5 idem aucun virus trouvé meme sur le disque externe
mais les video photo sont tjs crypter sur le disque externe
sinon mon pc tourne bien pas de fenetre qui souvre ou quoi que se soit donc j’aimerai savoir si pour mon pc c’est bon il est clean et si pour le hdd externe je peut le concervé comme ca jusqu’à se qu’une solution soit trouvé?
Hi steph,
You should be good after the re-installation, but make sure to do a thorough scan and check the registry for leftover files.
gandcrab 5.04 extension .EODFVWZIU pls HELP
Unfortunately, there is nothing we can do to help you at this time.
GandCrab 5.0.4 is undecryptable at the moment. We are all waiting for a decryption tool to be released. If that happens, the article will get duly updated and you notified of the good news.
Tomas, a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Gandcrab 5.0.4 con estensione .uwneb
Non si può fare niente, nessun rimedio per recuperare i files.
Unfortunately, for now there is no decryption tool yet.
Hi!
I was infected with Grandcrab 5.0.4, extension .KXRPAQD.
I’m sure there is nothing what can be done, right now, but I hope for great news in the future. I realy hope that a newer version of the BitDefender decryptor program will be released soon.
We hope so, too!
GANDCRAB V5.0.4 extension.YGLAX
my computer was affected yesterday and I made a reset to my local disk C. But it also affected my other local disk can I get those decrypted when the new version decryption tool is released.
Probably you can get them decrypted. As the decrypter is taking longer to be developed, we are wondering IF a decryptor will really ever be released.
UPDATE: Speak of the devil and we got a new decryptor today – it works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Hello,
My PC was infected in mid-November 2018 with the Grand Grab 5.0.4 Cryptovirus. Many data were encrypted with the random 8-letter extension “aszljtm”. Many data was not backed up at this time and can not be recovered. It takes a lot of time to recreate the essentials. For example, images can not be recovered.
I spent a lot of time and money decrypting the files. Unfortunately without success. Also the usig of the “BitDefenderGandCrabDecryptTool” is without success. Will there be any possibility of decryption in the near future – is there be working on it or will I rather have to accept the loss of the data? Thank’s a lot. Please excuse my not perfect english.
It is unknown. The BitDefender tool has never worked with 5.0.4 version. We hope that it is worked upon and a newer version of the decryptor will be released soon, but time will tell.
UPDATE: A new GandCrab Decryption tool got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Hi everybody. Just wanted to ask; can we buy the decryptor by paying a small amount each of us and then use it for everyone? Would that work?
The decryptor by BitDefender is free and does not work with 5.0.4.
If you are asking to buy the original decryption tool from the ransomware creators – that will not work, because everybody may get the same decryption tool, but the key for each person is individual for that person’s computer only. On another note, it is not a good thing to pay cybercriminals.
UPDATE: A new GandCrab Decryption tool got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
If you were to put all of your files on a flash drive and then let the malware delete the files, will the files on the flash drive also be deleted?
If you have that flash drive connected to the computer – yes.
If you connect it after you have the malware on the PC – again, yes.
So if you make a backup on a flash drive, do not connect it to the computer until you have removed the malware.
Update: Good news! There is a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Data is encrypted with “GANDCRAB V5.0.4 having extension of .KXETJL
Please help.
Hi Basha and Patrick,
Unfortunately, there is no decrypter for this version of Gandcrab.
Bonjour,
j’ai été infecter par GRANDCRABE V5.0.4 cle de l’extension : .INKGUOVGDA j’ai utilisé l’utilitaire de BitDefender mais sans résultat….Du coup j’ai isolé mes dossier data infectés et reformater mon PC.
Que pui-je faire de plus.?
Bonjour Patrick!
New GandCrab Decryption tool for you to try: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Data is encrypted with “GANDCRAB V5.0.4 having extension of .ZIGPSWTUXY
Please help.
My data is encrypted with “GANDCRAB V5.0.4 and having extension of .ZIGPSWTUXY
Please help.
Ales / Mesky – good news! There is a new GandCrab Decryption tool that got released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Data is encrypted with “GANDCRAB V5.04 having extension of .FAJSHAXF”
what should i do ? please help.
Tegar, download this new GandCrab Decryption tool that released today! It works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Hello to the forum. Well i also infected by grandcrab 5.04. With extension jjvcj. All started when i tried to dowload a program and run the exe. Emediately i noticed ubnormal activity of the exe. I opened the command cosole to terminate the processes the ransomeware was causing. I also pluged out the ethernet cable to stop internet. I was very lucky cause the infection stopped. For example in my music file from a to z the infection stopped to b. I have 5 discs in my pc and started infected from first to last folder/file. Thankfully the infection didnt encrypt the system folder and all folders with personal data and photos. What i noticed anyway was that when i changed the encrypted extention to its original of the mp3 only file. The mp3 worked like a charm as it had never been encrypted. Maybe this is a week point of this gradcrab type. Anyway all other files have to wait till an encryptor will be released. Hold on there all gradcrab victims including me. We will wait but no way to pay those bastards.
Kerveros, good news! There is a new GandCrab Decryption tool that works with versions until GandCrab 5.1 (including 5.1) – you can download it from BitDefender labs: labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
Thank you so much! Works like a charm!
That saves my butt!
I am glad that it works, Jan!
Thank you Tsetso… Just started decrypting and checking and double checking the decrypted files (with old backups). You gave me a big piece of happiness today. All the best to you and all the people made this.
Thank you so much Tsetso, Bitdefender research team, Cybersecurity experts…
My PC was infected with Grandcrab 5.0.4, extension .OYOMJRSUB.
All my encrypted data is now again decrypted and usable. Works perfectly!
Have a nice day
Thank you very much. Decrypted all files. thanks again.
Hi there,
Great news! Remember to be more careful in the future… and backup your data!
Die Daten werden verschlüsselt mit GANDCRAB V5.04 mit Erweiterung von Typ CZVPLSK-Datei
bitte kann mir jemand helfen, gibt Entschlüsselungswerkzeug für diese CZVPLSK-Datei
sa ne fonctione pas pour ses fichier IAWHN-DECRYPT.txt et ULENWDK-DECRYPT.txt
This is GandCrab ransomware. Question is, which version exactly? Since they all make a random extension from ~5 to 10 symbols. If it is GandCrab v5.2 – there is no solution. If it is v5.1 or below, try the decryption tool made by BitDefender – labs.bitdefender.com/2019/02/new-gandcrab-v5-1-decryptor-available-now
The new tool is Awesome!!! really i appreciate your effort.
Data is encrypted with “GANDCRAB V5.2 having extension of ..ZTJZHTABE”
what should i do ? please help.
Unfortunately, there is no decryption tool for this version of GandCrab.
Please help me!. they will encrypt all of my files.
What should i do??????
Hi Faheem,
What is the extension you see appended to your files?
.ZTJZHTABE this one
Please Help Me…. Please!
dear sir
i am using that software but not recover my data
Update to STOPDecrypter v2.1.0.20 with more OFFLINE keys.
OFFLINE ID: ZivCxija0GBwtwtwD0q4JRy80spT6lUyybPYhot1
Extensions: .lapoi
OFFLINE ID: Q2fNGjIEoR7J8UnURFiIH13JGa23UqaNUDz4ret1
Extensions: .todar
i check my files in ID Ransomware – Identify What Ransomware Encrypted Your Files
result
This ransomware may be decryptable under certain circumstances.
Please refer to the appropriate guide for more information.
Identified by
ransomnote_email: gorentos2@firemail.cc
sample_extension: .todar
sample_bytes: [0xC8B5 – 0xC8CF] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
Click here for more information about STOP (Djvu)
please help me please
please
my data is not Decrypter
dear sir
i change my infected pc with new pc my data was not decrypt
i am using that software but not recover my data
Update to new version STOPDecrypter with more OFFLINE keys.
OFFLINE ID: ZivCxija0GBwtwtwD0q4JRy80spT6lUyybPYhot1
Extensions: .lapoi
OFFLINE ID: Q2fNGjIEoR7J8UnURFiIH13JGa23UqaNUDz4ret1
Extensions: .todar
i check my files in ID Ransomware – Identify What Ransomware Encrypted Your Files
result
This ransomware may be decryptable under certain circumstances.
Please refer to the appropriate guide for more information.
Identified by
ransomnote_email: gorentos2@firemail.cc
sample_extension: .todar
sample_bytes: [0xC8B5 – 0xC8CF] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
Click here for more information about STOP (Djvu)
please help me please
please
my data is not Decrypter
i chang my infacted pc with new pc my data was not decrypt
please help me