 This analysis has been created to inform you and show you with instructions how you can remove the GANDCRAB 5.1 ransomware virus from your computer and how you can try and restore files, encrypted by it.
This analysis has been created to inform you and show you with instructions how you can remove the GANDCRAB 5.1 ransomware virus from your computer and how you can try and restore files, encrypted by it.
New variant of the notoriously dangerous GANDCRAB ransomware virus has been recently detected. The ransomware is version 5.1 and it aims to encrypt the files on the computers attacked by it and then set a random file extension in either lowercase or uppercase letters. GandCrab cryptovirus has been active for quite some time now and has been released in tons of new variants all of which aim to get victims to a TOR web page, where the ransom virus extorts them to pay ransom in BitCoin and even DASH cryptocurrencies. In case your computer has been infected by GANDCRAB v5.1 ransomware virus, we suggest that you read this article to understand more about it and learn how you can remove it from your computer, plus try to recover your data.

Threat Summary
| Name | GANDCRAB 5.1 |
| Type | Ransomware, Cryptovirus |
| Short Description | New version of the [wplinkpreview url=”https://sensorstechforum.com/remove-gandcrab/”]GANDCRAB ransomware virus family. Aims to encrypt your files and ask you to pay ransom in order to retrieve them. |
| Symptoms | Files are encrypted with an either uppercase or lowercase file extension that ranges from 6 to 8 random letters. A ransom note is dropped with the file extension for it’s name and it ends in “-DECRYPT.txt”. |
| Distribution Method | Malcious URLs, Email Attachments, Executables |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss GANDCRAB 5.1. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

GANDCRAB v5.1 Ransomware – Update October 2019
The newest information involving GandCrab 5.1 ransomware virus is that FBI has released Master Decryption Keys of the virus, meaning that GandCrab is over with. The tweet comes from Benjamin Carr Ph. D who reported that the Federal Beaurau of Investigation have released the keys:
https://twitter.com/BenjaminHCCarr/status/1154192546161201152
According to the information, the master decryption keys can allow absolutely everybody to craft their own decryptor and decode files, encrypted by GandCrab version v5.1 and v5.2.

GANDCRAB v5.1 Ransomware – Update February 2019
GandCrab 5.1 seems to keep its malvertising campaigns up and running in February, 2019. Below you can see one of the new e-mail messages that are being sent to try and lure more victims to this devastating ransomware:
I made transfer
Hello, I made transfer into your bank account
I’ll attach invoice on WeTransfer with password, I don’t think you can extract them from mobile, please extract from Desktop
hxxp://104.248.163.221/invioce.php
Password for rar: invoice123
Please let me know
Regards,
Mark
As you can see, a link is provided, which leads to a malicious domain, that automatically downloads and runs GandCrab 5.1. Refrain on clicking links which seem suspicious even if the sender looks like to be somebody you know.

GANDCRAB v5.1 Ransomware – Infection
GandCrab 5.1 ransomware virus is deemed a very persistent threat from the GandCrab ransomware family that uses a lot of different [wplinkpreview url=”https://sensorstechforum.com/file-types-used-malware-2019/”]file types to conduct an infection. The malware continues to be spread with the aid of malicious .JS files, but may also be replicated as a result of other distribution methods and the ransomware virus is capable of also infecting users with the aid of rogue sites, cracks, ad-supported programs and suspicious downloads. The latest method which GandCrab v5.1 has started to use to infect vicitms is currently contucted via malicious e-mails that carry around fake picture files, embedded in .ZIP folders that are attached to e-mails, looking like the following:
2019/01.28 10:40
Giovanni Price Giovanni33@4311.com
Attachment: PIC0101302924102-jpg.zip (69 KB)
E-mail Body: ;)
Once the victims open the .zip file, they extract the file PIC0101302924102-jpg.JS, which is a JavaScript type of file and if it is executed, an infection with GandCrab v5.1 is inevitable. Once this file is triggered, it spawns the following malicious processes:
→SHA256:dffc26736e57470e4c56e4adf3f0425080c43a136d0dd72c22075fde3efd2239
Name:TempoJB62.exe
SHA256:be0c8cdc1937d05242c672e3e61097dd1b48466839ac0a64e883d159a8df7343
Name:2510619273.exe
For the moment, researchers keep discovering new and new payloads that belong to the GandCrab ransomware virus. We have found the following GandCrab Payload files and listed them below, so if you encounter these files, be sure to scan them before actually opening them, since you risk getting infected with GandCrab ransomware yourself:
Malicious files infecting with GANDCRAB 5.1 Ransomware:
→ SHA-256:85671f4675ccc98133a5a6de2e4faeb6df119ad9460f3651e231eaba4ce2b872
File name:3449440902.exe
File size:185.5 KB
SHA-256:c1a66da25419855f684261ac55f796127d84ca7bb9e089b1eb18afde66d1da7c
File name:GandCrab v5.1.exe
File size:421 KB
SHA-256:07de185bb18610f471a31358c74c2e2da0dc505ade21cbe9cae5c8ba3fd66add
File name:putty.exe
File size:595 KB
SHA-256:47b9249590b764e24d0da606efa1858d41bdd57886329014b61f44701668c080
File name:Analysis’s Restrain
File size:630 KB
SHA-256:befb77f972b225791b9f84644939be3e599f0bc361b7a20ad4cde696361c78ba
File name:Technologyword
File size:694.5 KB
SHA-256:5b13e0c41b955fdc7929e324357cd0583b7d92c8c2aedaf7930ff58ad3a00aed
File name:output.115120150.txt
File size:609 KB
SHA256:c7197601b0e5cf5a38abe626007ffd05d36d4f205b6b62ab5d6f940590d42c8d
File name: 4.exe
SHA-256:9e90a004a26fe2f58f4c725a7034fa6c4fd95000dc86c573e2036a75e83c0705
File name:1.exe
File size:288.5 KB
Not only this, but researchers, like Valthek have also discovered new samples of GandCrab ransomware that were compiled earlier in January 2019, with the main difference that they create a hidden Window with the ame “AnaLab_sucks” and it has a timer to stay for a bit and create a threat that initiates GandCrab’s normal procedure. Other users have asked for tools to decrypt files, encoded by GandCrab ransomware, but researchers still have not been able to find new information.
Another method of infection, which was recently detected by researchers is to use Microsoft Word Macros to infect vicitms. The scripts hijacker the Ursnif data-stealing Trojan Horse in combination with GandCrab ransomware in the wild so if you have GandCrab, chances are that your computer might be infected with a Trojan Horse too. The way these infections tend to take place is the user having to download Malicious Macros, which could eventually lead to one of about 180 versions of MS Word files that target victims with VBS scrips, which run Windows PowerShell commands and perform infection with GandCrab ransomware on the targeted systems. And to hide those scripts, they are encoded in base64 which executes the next stage of infection with GandCrab that downloads it’s main payload files on the infected computer without the virus being detected.
The primary infection method that was used so far in relation to GANDCRAB 5.1 infection is e-mails that are composed in the following way:
From: Deanna Bennett <>
Subject: Payment Invoice #93611
Attachment: DOC402942349491-PDF.7ZDear Customer,
To read your document please open the attachment and reply as soon as possible.
Kind regards,
TCR Customer Support
Besides the “Payment Invoice #93611” subjects above, we have also detected other fake subject e-mails:
- Document #72170
- Invoice #21613
- Order #87884
- Payment #72985
- Ticket #07009
- Your Document #78391
- Your Order #16323
- Your Ticket #23428
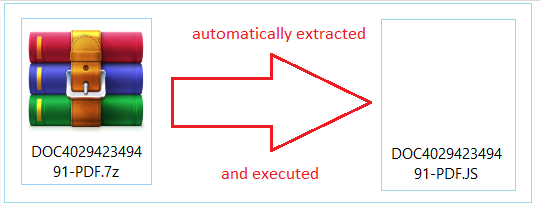
The e-mails contain an e-mail attachment that is often a malicious .JS(JavaScript), a .docx (Microsoft Word) or .PDF (Adobe Reader) file that leads to a .docx file. The file is named randomly, like the example associated with GANDCRAB which we detected earlier shows:
→DOC402942349491-PDF.7Z
DOC402942349491-PDF.docx
DOC402942349491-PDF.js
DOC402942349491-PDF.PDF
Love_You_2019_300232289-txt.ZIP
Love_You_2019_300232289-txt.JS
If the malicious file is from the .JS type (JavaScript), simply extracting and executing it will result in infecting your computer, like we have demonstrated below:
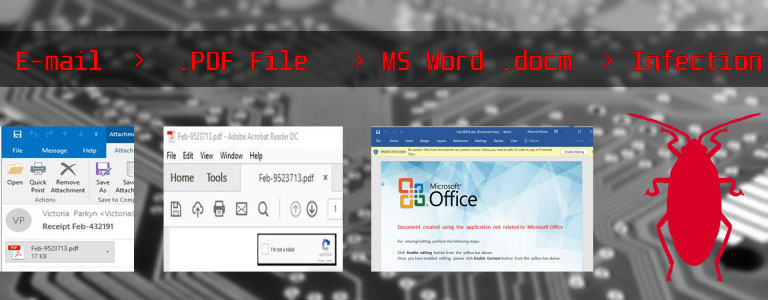
If the malicious file is a document, then the infection will go through malicious macros that are embedded within the Microsoft Office or Adobe PDF document and they want you to Enable Content or Enable Editing in order to see what is in the document. Clicking on this “Enable Editing” button results in the following infection activities to take place:
Besides via e-mail, the infection process with GANDCRAB 5.1 ransomare may take place online. Researchers at Fortinet have previously detected GANDCRAB to infect users by pretending to be a software crack of the following programs:
- Merging Image to PDF.
- Securitask.
- SysTools PST Merge.
More information about GANDCRAB infecting victims via software cracks can be found in the related article underneath:

GANDCRAB 5.1 – Malicious Activity Report
The main infection file of GANDCRAB 5.1 ransomware virus has been reported to have the following IOCs (Identificators of Compromise):
→Name:1.exe
Size: 361.50 Kb
MD5: E387BD817E9B7F02FA9C2511CC345F12
SHA256:39514226b71aebbe775aa14627c716973282cba201532df3f820a209d87f6df9
SHA1: 98b3ec47b64198e3604c738f8c1f4753e0afa8c7
Once this file is dropped on your computer, it may immediately trigger the Windows component “wmic.exe” as an administrator in order to delete the shadow volume copies of your PC. This will prevent you from recovering your files via the Windows Recovery service. GANDCRAB 5.1 triggers the following command as an administrator in Windows Command Prompt:
→ “C:\Windows\system32\wbem\wmic.exe” shadowcopy delete
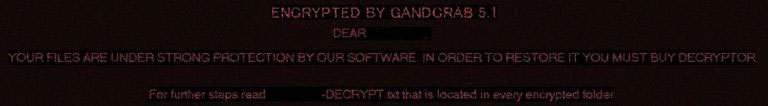
As soon as GANDCRAB 5.1 has deleted the backed up files, the ransomware begins to drop it’s ransom note file, which has the following message to the victims of the virus:
—= GANDCRAB V5.1 =—
UNDER NO CIRCUMSTANCES DO NOT DELETE THIS FILE, UNTIL ALL YOUR DATA IS RECOVERED
FAILING TO DO SO WIL RESULT IN YOUR SYSTEM CORRUPTION, IF THERE ARE DECRYPTION ERRORSAttention!
All your files, documents, photos, databases and other important files are encrypted and have the extension:
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————–
| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor Browser
| 2. Open Tor Browser
| 3. Open link in TOR browser https://gandcrabmfe6mnef.onion/ b6314679c4ba3647/
| 4. Follow the instructions on this page—————————————————————————————–
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
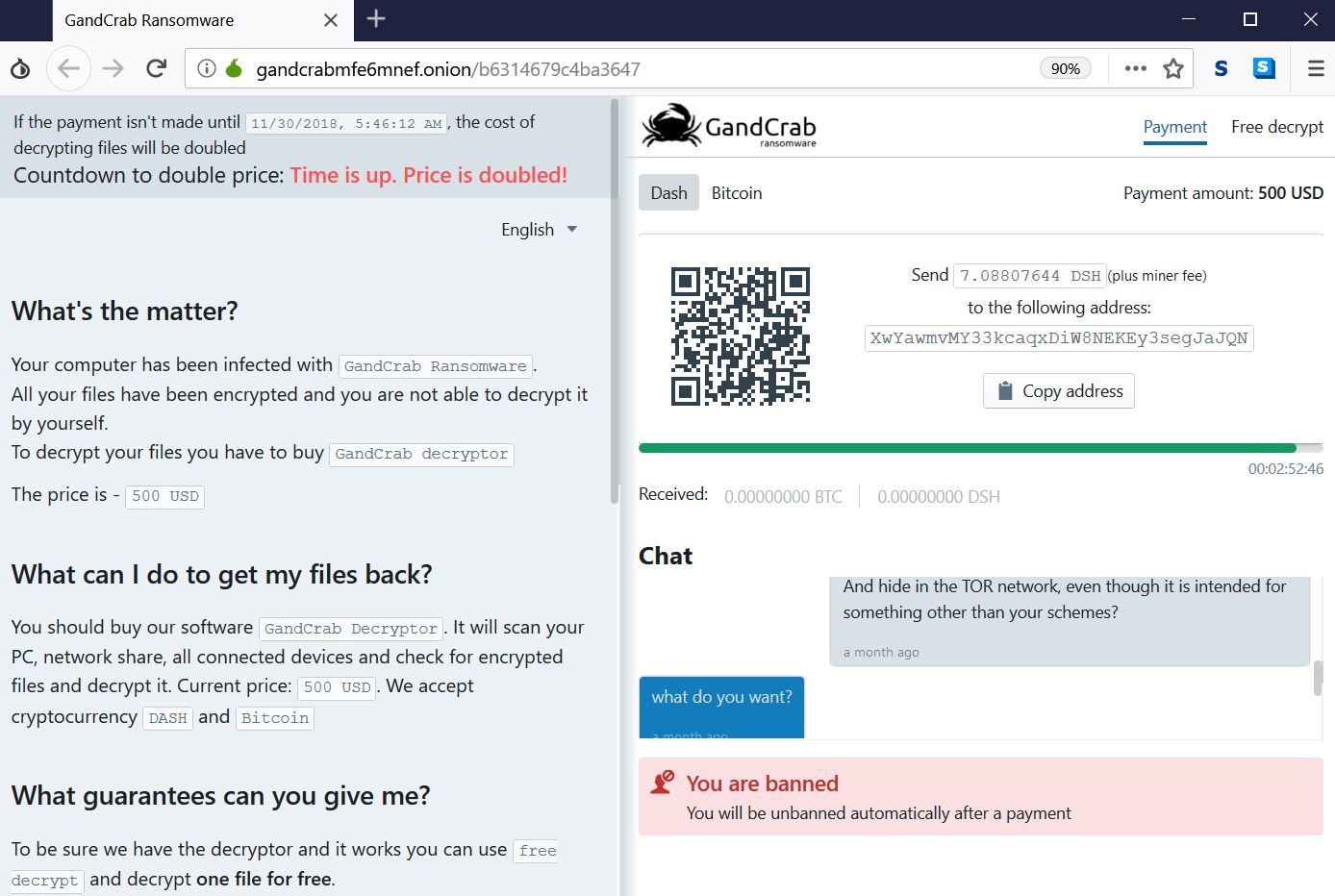
The ransom note of this particular sample of GANDCRAB 5.1 which we have analyzed leads victims to the following ransom note web page, which can be opened only in the TOR browser listed in the instructions:
When the victim’s payment deadline timer expires, GandCrab may also show the following version of the ransom note, which says the price has doubled.
The ransom note has the following instructions to victims:
What’s the matter?
Your computer has been infected with GandCrab Ransomware.
All your files have been encrypted and you are not able to decrypt it by yourself.To decrypt your files you have to buy GandCrab decryptor
The price is – 500 USD
What can I do to get my files back?
You should buy our software GandCrab Decryptor. It will scan your PC, network share, all connected devices and check for encrypted files and decrypt it. Current price: 500 USD. We accept cryptocurrency DASH and Bitcoin
What guarantees can you give me?
To be sure we have the decryptor and it works you can use free decrypt and decrypt one file for free.
But this file must be an image, because images usually are not valuable.
I don’t have Bitcoin (BTC) or DASH (DSH). How can I make the payment?
Easy. The list of the most popular exchange services:BuyBitcoin
CoinMonitor.io
LocalBitcoins
CoinMama
Changelly.com
PAYEER
CEX.IOThe full list of exchange services for Bitcoin here and for DASH here.
Create an account
Charge the balance with a credit card or paypal
Buy requested amount of coins (Bitcoin or DASH)
Make withdrawal to our address
And in addition to those activities, [wplinkpreview url=”https://sensorstechforum.com/remove-gandcrab-5-1-6-ransomware/”]GANDCRAB ransomware may also eventually change the wallpaper on the infected computer with the following picture:
And in the ransom note page, the virus offers 1 encrypted file for free download, just so the victim can see that it works. Which basically means that the virus may contain Trojan capabilities to copy files from the infected machine and upload them on TOR:

GANDCRAB 5.1 – Encryption Process
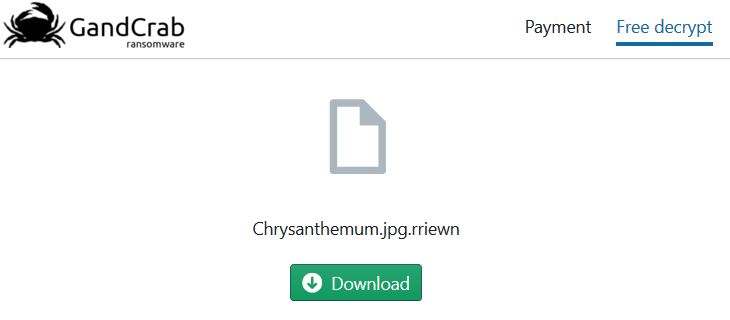
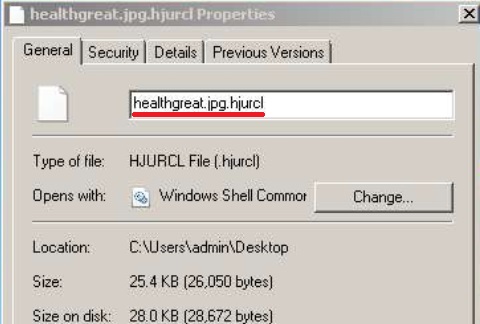
The main encryption algorithm that is used by GANDCRAB 5.1 is the Salsa20 cipher. Unlike RSA and AES encryption algorithms, the Salsa20 is much faster and can encrypt all files in around under a minute time. Just like other GandCrab versions, v5.1 also uses random file extension which it gladly ads to the encrypted files after it encrypts them. The files become scrambled and looking like the image below shows:
The ransomware skips encrypting files if they are located in the following Windows directories:
→\ProgramData\
\Program Files\
\Tor Browser\
Ransomware
\All Users\
\Local Settings\
The encryption process of GANDCRAB ransomware is conducted in a way that the virus likely creates copies of the original files and then encrypts those copies by replacing blocks of data from the file with the scrambled data. The cyber-criminals may delete the original files and since they delete the shadow copies as well, there seems to be little chance to recover the files unless you pay the crooks, which we would highly advise to refrain from doing.

Remove GANDCRAB 5.1 and Try to Restore Files
Before beginning to even think about removing GANDCRAB 5.1 ransomware, we would recommend that you do a backup on your files, even if they are encrypted, because if you try to remvoe this variant of GANDCRAB, chances are your PC could malfunction and break down your OS irreversibly.
For the removal of GANDCRAB 5.1, we have prepared the steps below. Make sure to follow the first two steps only if you have some experience in malware removal and know what you are doing. Otherwise, we would recommend what most cybersecurity experts advise victims – to scan your computer for the GANDCRAB malware files with an advanced anti-malware program and remove all malicious files and objects belonging to it automatically.
For the file recovery, we would suggest that you check out the step “Try to Restore files encrypted by GANDCRAB 5.1” below. They contain multiple methods that explain what recovery method is the best for you and even though the methods provided do not come with a 100% guarantee to recover your files, you might theoretically be able to restore at least some of your files.
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
Step 1: Scan for GANDCRAB 5.1 with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall GANDCRAB 5.1 and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by GANDCRAB 5.1 on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by GANDCRAB 5.1 there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove GANDCRAB 5.1





Step 5: Try to Restore Files Encrypted by GANDCRAB 5.1.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
1 Right-click on the decrypter and click on Run as Administrator as shown below:
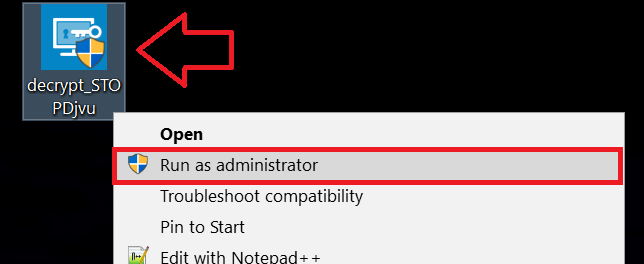
2. Agree with the license terms:
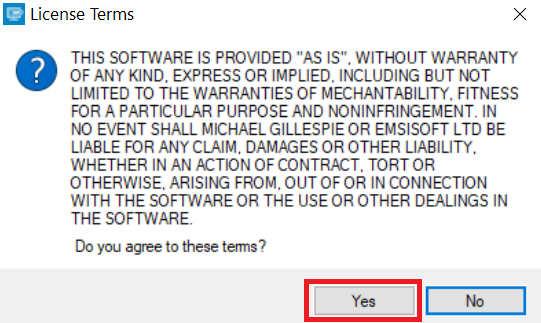
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
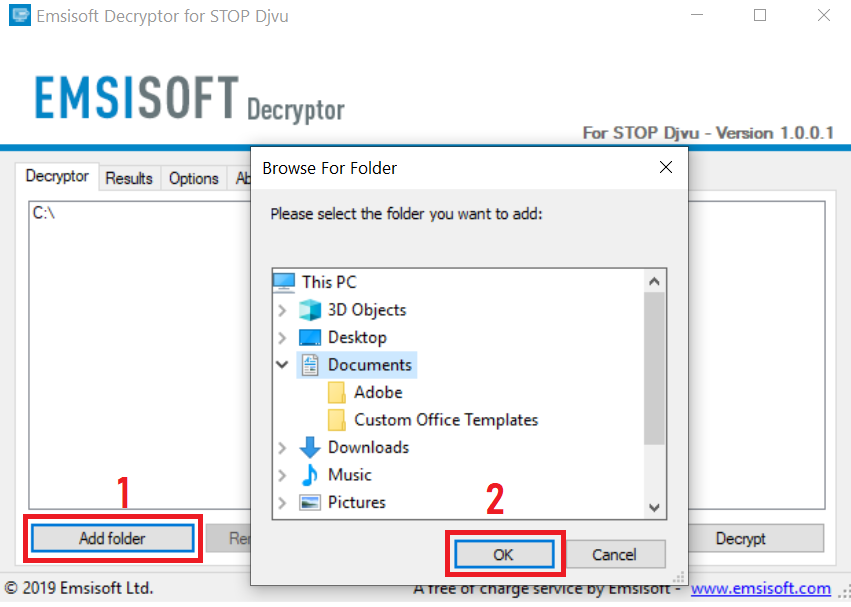
4. Click on "Decrypt" and wait for your files to be decoded.
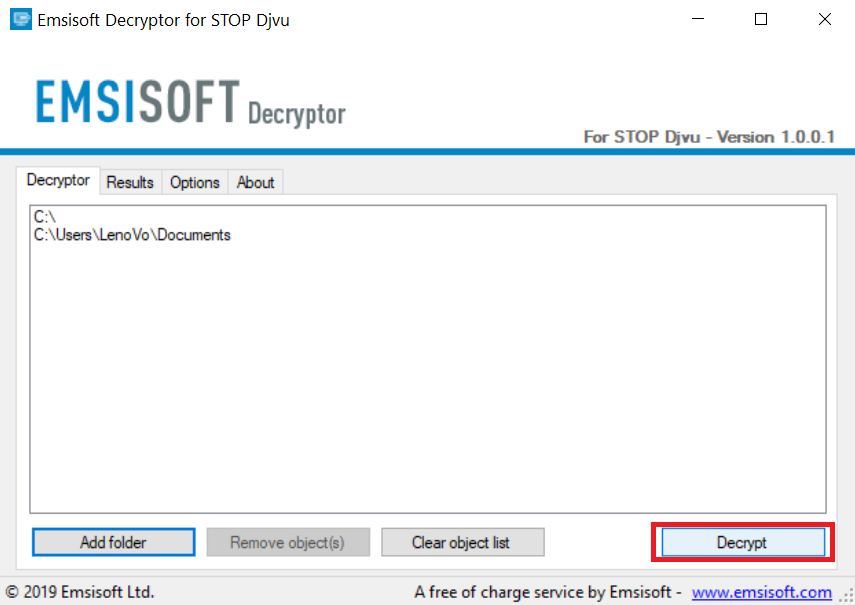
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and GANDCRAB 5.1 aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
GANDCRAB 5.1-FAQ
What is GANDCRAB 5.1 Ransomware?
GANDCRAB 5.1 is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does GANDCRAB 5.1 Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does GANDCRAB 5.1 Infect?
Via several ways.GANDCRAB 5.1 Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of GANDCRAB 5.1 is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .GANDCRAB 5.1 files?
You can't without a decryptor. At this point, the .GANDCRAB 5.1 files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .GANDCRAB 5.1 files successfully, then do not despair, because this virus is still new.
Can I Restore ".GANDCRAB 5.1" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .GANDCRAB 5.1 files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of GANDCRAB 5.1 Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate GANDCRAB 5.1 ransomware and then remove it without causing any additional harm to your important .GANDCRAB 5.1 files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can GANDCRAB 5.1 Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the GANDCRAB 5.1 Research
The content we publish on SensorsTechForum.com, this GANDCRAB 5.1 how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the GANDCRAB 5.1 ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.




hola buenas tardes, tengo virus grandcrab 5.1 extension .utxuoip y modifico mis archivos particionados, porque la unidad del sistema no la afecto porque la tengo congelada con deepfreeze pero todos los archivos de particiones los secuestro, e intentado recuperar a ver si el virus habia borrado, pero no encuentro ninguno, es como si simplemente modifico todos los archivos existentes y los encriptó, ayuda por favor
Hi
this is the note after I got infected with gandcrab V5.1
:(
And just hope counter tool for encryption might be made…
LInk to notepad tht is in the encripted folders:
dropbox.com/s/5qskms1rkgtjtxg/QEZAKCPQH-DECRYPT.txt?dl=0
Hi there,
Unfortunately there is no decrypter for this version of the ransomware. You can try alternative data restoration methods as described in the article, but there is no guarantee they would work.