The latest in Android ransomware, called “Simple Locker” is essentially a lockscreen type of malware that affects all types of devices. The malware may infect users via spam e-mails offering new applications which are in fact the malicious files themselves. The ransomware also features a scareware message that “convicts” users into crimes they did not commit and asks for paying “fee” in return for the access of their device. All users, whose mobile devices were affected by this ransomware are strongly advised to plug out their SIM cards and follow the instructions after this article.
| Name | Simple Locker |
| Type | Ransomware, RaaS |
| Short Description | SimpleLocker locks the user out of his device and demands a payment. The Ransomware may be encountered on Android devices as well as other mobile OSs. |
| Symptoms | Access to apps and files is locked and a ransom message is displayed. Instructions are included. |
| Distribution Method | Distribution method is not clear yet. SimpleLocker may be distributed via malicious apps, etc. |
| Detection tool | Download Advanced anti-malware tool, to See If Your System Has Been Affected By Simple Locker |
| User Experience | Join our forum to discuss Simple Locker. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |
Simple Locker Ransomware Distribution
This lockscreen malware may use fake app downloads through malicious emails sent out to the user’s account. The email subjects may be connected with something the user is likely to tap on, for example:
- “New version of your game.”
- “New PayPal app.”
- “The mobile app you subscribed for.”
After downloading the app, and starting it, it locks the user’s screen displaying the ransom message.
Simple Locker Ransomware In Detail
As soon as simple locker has been activated it may immediately lock down the screen of the user. After it locks down your screen, you may enter the main menu of your phone but the app will open the ransom message seconds after your action.
The message itself is written in Russian, but directly translated, it means the following:
→ “Attention! Your phone has been blocked! The device has been blocked for the distribution of child pornography, zoophilia, and other sick things. To unlock your phone, you need to pay 900 hryvnias.
1.Find a payment fulfillment terminal, located in your proximity.
2.In it, locate Money.
3.Enter
4. Input 260 hryvnias and tap on ‘Pay’
Do not forget to take your receipt! After the payment has been conducted your device will be unencrypted in 24 hours. IN CASE, YOU HAVEN’T PAYED YOU WILL LOSE ALL THE DATA ON YOUR DEVICE FOREVER!”
This locking of the screen is particularly bad in case you have saved your contacts or important files on your phone, because the Ransomware may block it in case you connect via USB to your computer. It is a clear sign of the ever increasing spread of ransomware infections across different devices with operating systems. This is especially scary when we put into perspective “the internet of things”, while looking towards the future.
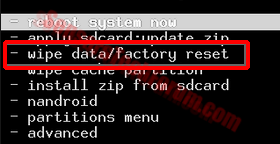
Remove Simple Locker Ransomware from Your Mobile Device
So far, we have encountered Simple Locker only on Android devices. However, this does not exclude the possibility that this ransomware may also be spread throughout Apple devices and Windows mobile ones as well.
Since removing Simple Locker may erase your data, we have suggested several methods to do it effectively and safely in case you have an Android or Apple device in the step-by-step instructions below.