Computer security researchers have detected a new massive SPAM campaign which has received the code name ‘Salfram’ and targets primarily business users and companies. Several hacking groups are behind the attacks and depending on the current configuration various malware are being discovered.
New, Large and Dangerous Email Attack Campaign Dubbed ‘Salfram’ Targets Companies
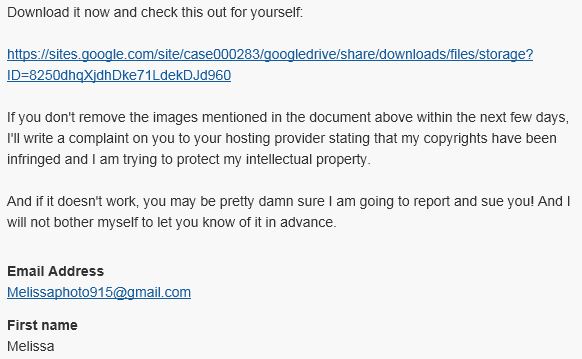
Reports of a dangerous new attack campaign carrying various malware is rapidly attacking enterprise targets and companies worldwide. It appears that this campaign builds on previous attacks done by various hacking groups. This is a particularly dangerous attack as it relies on a complex content structure that make it possible to evade security checks — the virus files are not placed in copy-and-paste typical messages. Rather than that the following distinct characteristics are indicative of this particular campaign:
- Prepared Content — Instead of inserting typical contents these malicious emails will feature web-based contact forms, scripts and interactive elements. They will emulate legitimate notifications and messages and may overcome the typical filters used by protective software./li>
- Modified Headers — All of the email messages which are part of this campaign have modified headers that include the ‘Salfram’ string which has subsequently been used as an identifier.
- Encrypted Contents — A strong cipher is included in the messages in order to obfuscate the payloads.
The attack is organized by sending out information via the contact forms which are published on the company websites. This is a legitimate form of communication which is widely used for customer support or feedback. Different kind of messages are prepared depending on the company’s industry sector and profile.
The prepared messages will include malware links that will lead the recipients to files hosted on hacker-controlled servers, cloud storage platforms and etc. In the majority of cases the retrieved files will be macro-infected documents that are prepared in all of the popular office formats. And when opened they will activate a payload delivery script leading to a virus infection.
According to the research reports the attacks are currently tweaked and will probably change in the near future. They are particularly useful for spreading dangerous malware such as the Qbot Trojan.