Imagine a busy night at the emergency room. Several vehicles involved have been involved in an accident, and one little girl has been brought in by ambulance after suffering a loss of blood. Naturally, blood transfusions are a common occurrence at the ER, so everyone on the staff prepares while a nurse runs to the blood bank to grab a couple of units.
However, when she gets there, she gets some very bad news. The blood bank refrigeration systems have suddenly malfunctioned all at once, rendering all the stored blood units unusable. Nobody can figure out what went wrong. As the nurse returns to the ER empty-handed, the doctors’ chances at saving that little girl’s life have just been severely reduced.
This may sound like an episode of Grey’s Anatomy, but it could all-too-easily become a reality for any one of us – as discovered by Israeli hackers and activists Noam Rotem and Ran L, who work closely with the Safety Detective research lab.
Due to a major security breach, just about anyone can gain access to the refrigeration and temperature control systems of hospitals, major supermarket chains, pharmaceutical companies and other establishments all around the world. This puts us all at risk in ways most of us have probably never even imagined.
Is the Internet of Things Putting Us All at Risk?
Resource Data Management, a Scottish company that manufactures control and remote monitoring solutions, markets its temperature control systems to establishments in countries all over the world. Users can control all devices in their refrigeration systems through a dashboard, including adjusting temperatures, defrosting, and more.
As it turns out, hacking these online systems is as easy as one-two-three – or one-two-three-four, to be precise. They all come with a default username and “1234” as the default password. System administrators rarely bother to change these credentials.
These dashboards are accessible through any browser, using the unsecured HTTP protocol and the 9000 port (or sometimes 8080, 8100, or even simply 80). A terrorist looking to mess with a hospital’s refrigeration system wouldn’t even have to be a particularly sophisticated or experienced hacker. Pretty much anyone with an internet connection and the right URL can view data and reports, change settings and configurations, change refrigerator and freezer temperatures, or even click a button for a complete defrost.
It’s so easy, in fact, that when we instructed our office secretary on how to find the systems online, she was able to find connected devices in a cooling facility in Germany and a hospital in the UK within a few moments, using Google alone.
Now, while our secretary would never harm a fly, a potential terrorist or attacker could easily use Shodan, a search engine for internet-connected devices, to identify thousands of devices.
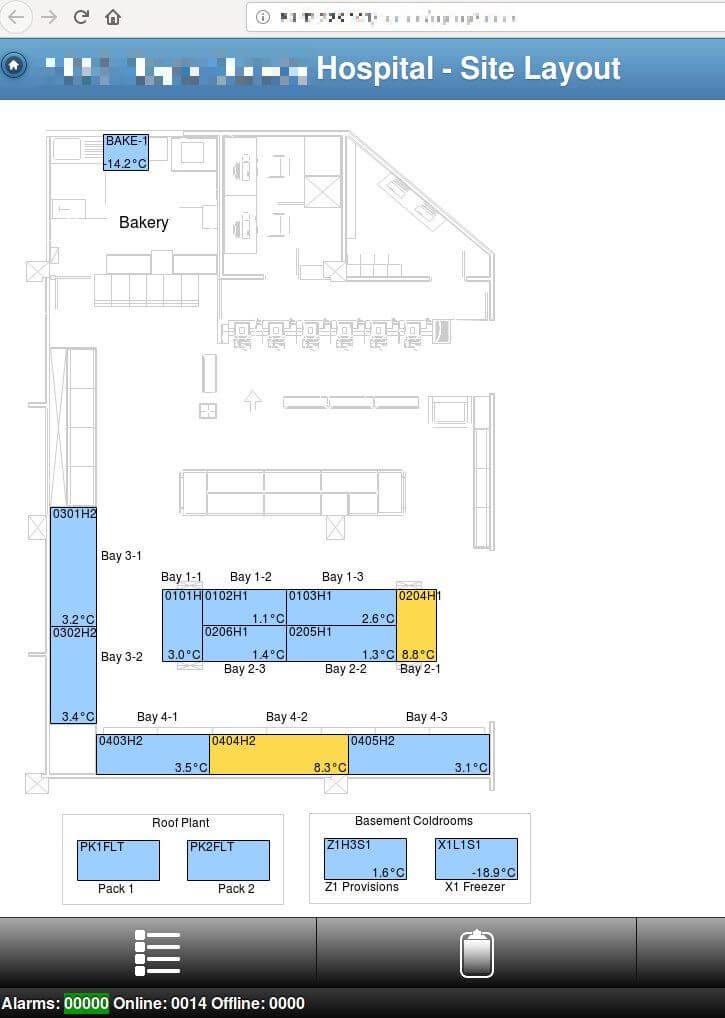
The site layout of this UK-based hospital, for instance, can easily be accessed. Anyone can change the temperature of any of these cooling devices. We can only imagine what might be stored inside. Blood units? Temperature-sensitive pharmaceuticals?
It’s a Matter of Life and Death – and Public Health
It’s not just hospitals that are at risk. These control systems are used by major supermarket chains all over the world, including Marks & Spencer, Ocado, Way-on, and many others.
A basic scan reveals hundreds of installations in the UK, Australia, Israel, Germany, the Netherlands, Malaysia, Iceland, and many other countries. As each installation has dozens of machines under it, we’re looking at many thousands of vulnerable machines. Some of them could easily be located at your favorite grocery store.
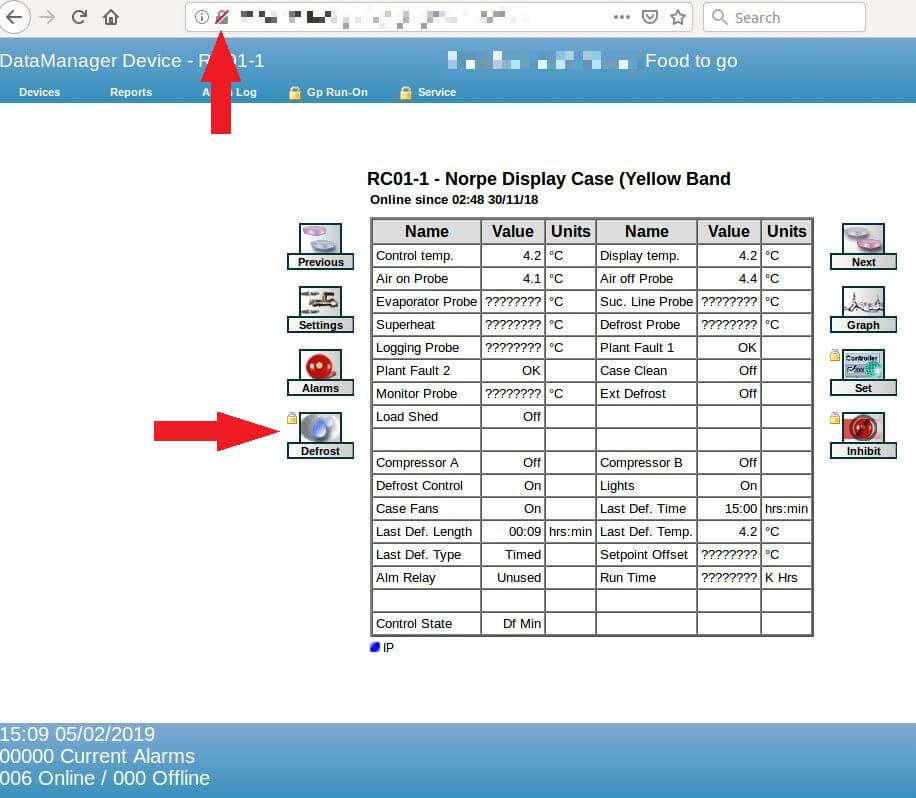
Here we see detailed data on one of those machines – a display case at a large supermarket. Note how it’s accessible through an unsecured URL. To defrost this machine, all you’d need to do is click a button and enter the default username and password.
Now, imagine a supermarket chain looking to destroy its biggest competitor’s reputation. Anyone with basic technical knowledge could easily hack into the competitor’s refrigeration system, defrosting frozen food products and refreezing them over and over.
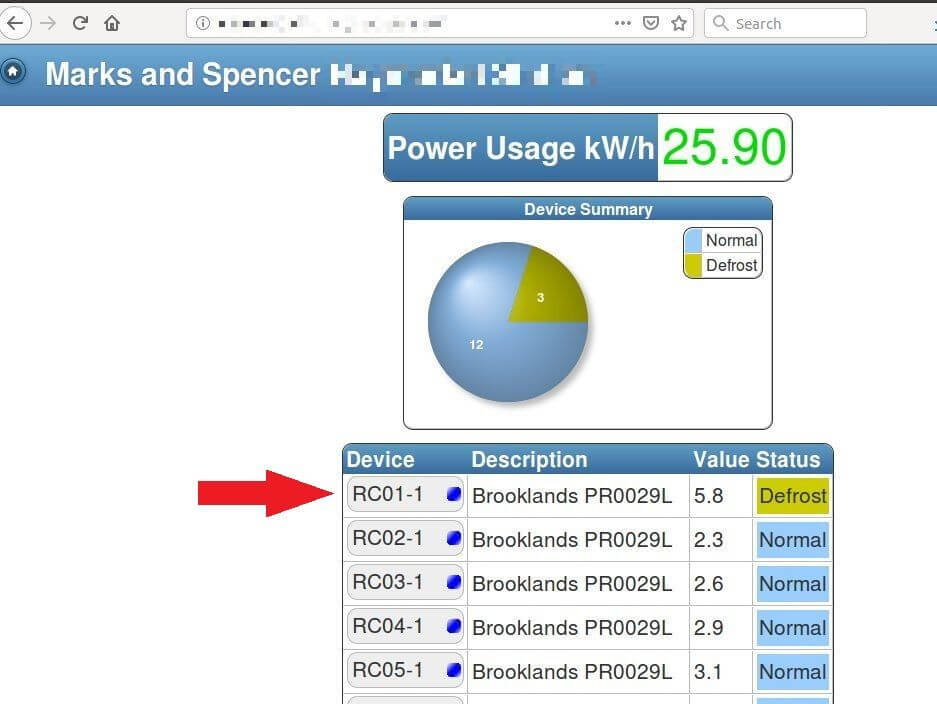
To mess around with the machines at this branch of Marks and Spencer, for instance, all you’d need to do is take your pick of any device on the list. Assuming you don’t know what’s inside them, you could even play around with them all. This online system certainly isn’t going to stop you.
Of course, it’s not just the competitor’s reputation at risk – it’s public health. Our health. Any individual or entity with sinister intentions could cause a major food poisoning epidemic with just a few clicks of a mouse.
While we want to believe not many people out there would be willing to stoop this low, we all know the world of business can get… well, dirty. And we’d sleep better at night knowing that all the food in our fridge was kept in appropriate conditions before it got there.
The system also allows you to access and modify user data, alarm systems, and more:
Keep Your Cool
In this era of the Internet of Things, system administrators need to take special care to secure their remote systems, and never rely on a manufacturer’s defaults. This is particularly true when it’s literally a matter of life and death, as we’ve seen in these examples.
But to be honest, we’d expect manufacturers of systems like these to take more responsibility, and make sure all their customers are aware of any security risks and how they can be prevented. Especially when their customers are the stores where we buy all our food and the hospitals we know will take care of us in case of emergency.
About the Author: Katrina Svensson
Katrina is a security researcher and web developer for SafetyDetective Research Lab.