The last time we wrote about wiper malware was in December when Shamoon returned to the malware scene.
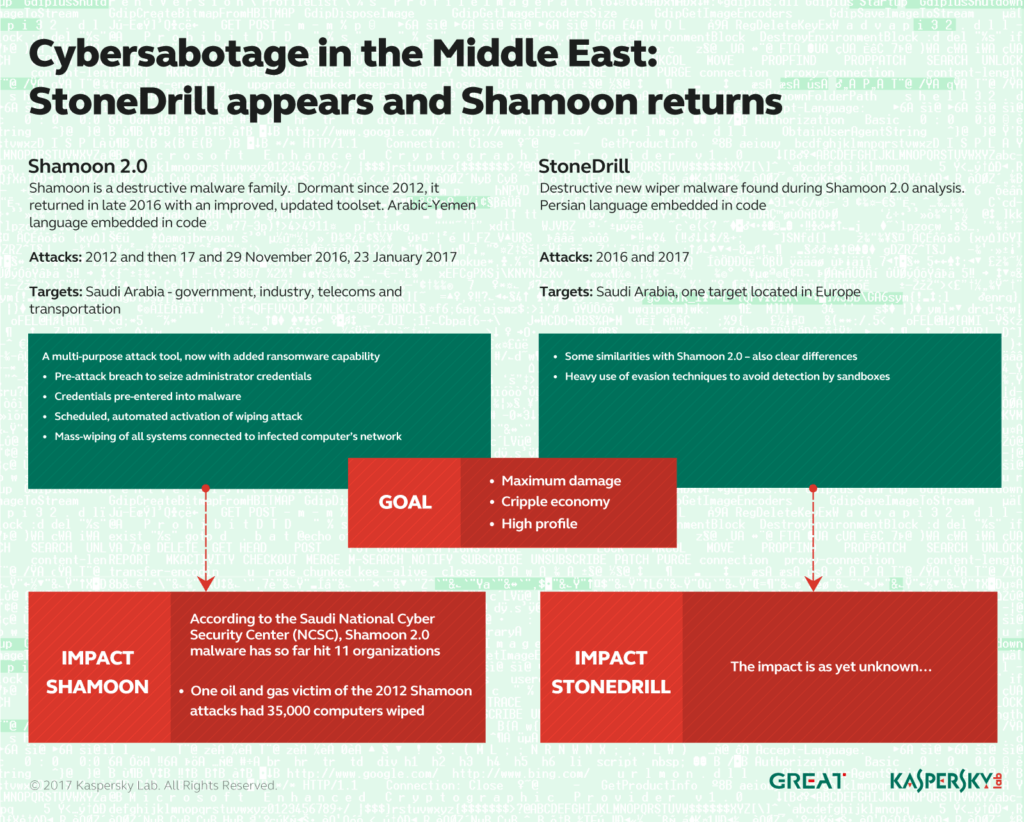
Shamoon, a.k.a. Disstrack was initially detected about four years ago in attacks against Saudi Oil Company Aramco. Its intention was to wipe thousands of computers.
In December 2016, the malware was targeting another Saudi organization. And its agenda was not just wiping companies’ machines but also overwriting their Master Boot Records with the image of Aylan Kurdi’s corpse. The attack took place on November 17, a Muslim holiday. The attackers most likely chose that date to bypass security measures.
Related: The Resurrection of Shamoon Wiper Malware
Now, another wiper malware dubbed StoneDrill has been unearthed in disastrous campaigns against European and Middle Eastern organizations. Kaspersky Lab researchers, however, say that this piece is more sophisticated and destructive than Shamoon, even though the two share many similarities. StoneDrill has been designed to destroy everything on targeted machines. Plus, it is persistent to both detection and eradication.
Researchers Find StoneDrill While Investigating Shamoon 2.0 Attacks
Beginning in November 2016, Kaspersky Lab observed a new wave of wiper attacks directed at multiple targets in the Middle East. The malware used in the new attacks was a variant of the infamous Shamoon worm that targeted Saudi Aramco and Rasgas back in 2012.
Shamoon 2.0 attacks share many similarities with previous campaigns but they feature new tools and techniques, researchers explain. During the first stage of an attack, hackers obtain administrator credentials for the targeted network. Then, they build a custom wiper which exploits the credentials to spread deeply inside the targeted organization. The final stage takes place on a predefined date when the wiper activates, “rendering the infected machines completely inoperable”. The final stage is entirely automated, and there is no need of communication with the command and control server.
Related: How Easy It Is To Hack an Organization
While investigating the Shamoon 2.0 attacks, Kaspersky Lab also discovered a previously unknown wiper malware which appears to be targeting organizations in Saudi Arabia. We’re calling this new wiper StoneDrill.
As already mentioned, StoneDrill shares some similarities with Shamoon, but is better at evading detection. In addition to suspected Saudi targets, another StoneDrill victim was observed on the Kaspersky Security Network (KSN) in Europe, according to the research team. “This makes us believe the threat actor behind StoneDrill is expanding its wiping operations from the Middle East to Europe”, the Kaspersky team concludes.