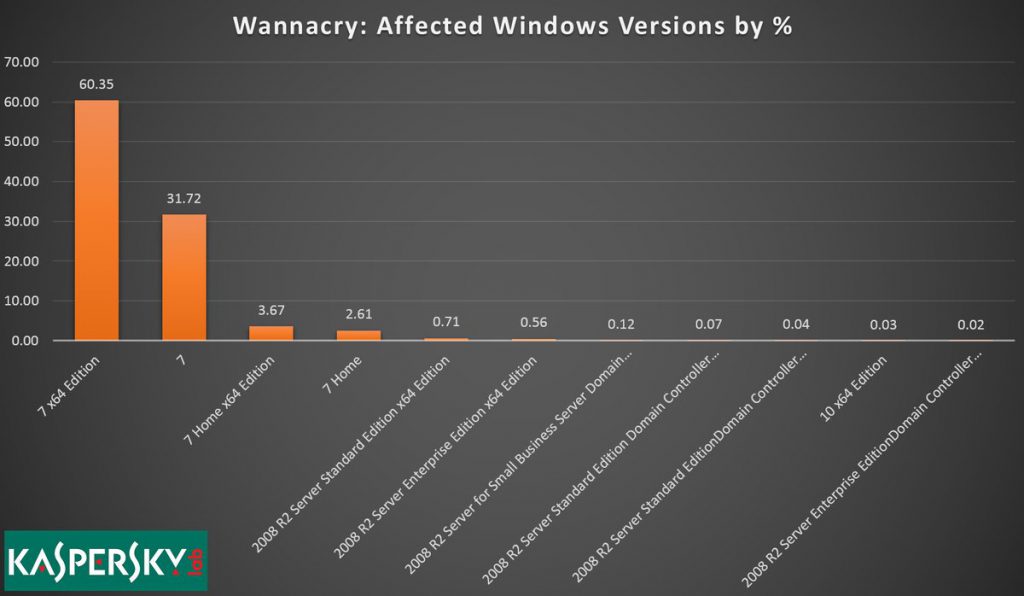
Kaspersky Lab statistics indicate that WannaCry attacks on Windows 7 accounted for 98% of the total number of infections. More particularly, over 60% of the systems attacked by WannaCry were running the 64-bit version of Windows 7, whereas 32% of victims were on the 32-bit version of the operating system. This news is not surprising because Windows 7 is still the most preferred desktop operating system with a market share close to 50%.
Windows 7: Highest WannaCry Ransomware Infection Rates
What is paradoxical here is that Windows 7 was supposed to be protected against the WannaCry ransomware campaign because Microsoft issued patches to stop the infection in March this year. But as it turned out – it wasn’t, and it got massively hit.
The popularity of the operating system almost means that approximately 1 in 2 machines are still on Windows 7, easily illustrating the high infection rates. Unfortunately, it is still a very pirated OS, meaning that millions of users are running pirated software, particularly in countries such as Russia and China. Needless to say, running copies of the OS that are not genuine is very dangerous – in most cases they cannot be updated as users have stopped updates to prevent the copy from checking for genuine product keys.
Even though Windows 7 will be supported until January 2020, users running it may want to start thinking about migrating to a newer version, security experts advise. Getting the latest security updates as soon as possible is also crucial to safety against attacks such as WannaCry.
“Oops, your important files are encrypted” is what victims of WannaCry see after their computers are infected. Once this has happened, the ransomware infection begins to append encryption algorithms to make the documents on the affected computers no longer readable. Then, !Please Read Me!.txt file is dropped on the targeted aiming to get victims to download a decryptor from a dropbox account. Finally, the ransomware demands 300$ in BTC payoff to get the data back.