A Web browser can be two things. A person who browses the Internet and the instrument he uses to do so. We all know about the first one, so what do we know about the second?
NB! Make sure to check which is the most secure browser for 2016!
Let’s Talk Money: Browsers and Corporations
We know that nowadays web browsers are represented by several, let’s call them by name, corporations (aside from Mozilla which is a nonprofit organization). No matter if we want to admit it or not, corporations have quite the impact on our lives – online and offline. Just for the sake of information sharing, the span of the leading world corporations is more than impressive. Modern life is utterly dependable on multinational enterprises. They provide us with products, services, and jobs. Top public companies are found in all major economy sectors such as oil, insurance, investment, pharmacy, food & beverages, investment, banking.
Where does Apple stand?
Shell, or Royal Dutch Shell, is one of the biggest companies in the field of petrochemical and alternative energy sources. Shell stations are scattered all around the globe. In the list of leading public companies made by Forbes, Shell is number 13. Right after… Apple. Shell assets are estimated at $353.1 billion. In comparison, Apple’s assets are evaluated at $261.9 billion. We are pretty sure that the difference of $91.2 billion goes right into the mouth of another hungered multi-culti beast.
What about Microsoft?
Apple’s abiding competition is just around the top 20 corner and is nailed at number 25 with the humble assets of $174.8 billion. However, do these numbers apply to the popularity of Apple’s Safari and Microsoft’s Internet Explorer and Edge browsers? And where does the rest of the bunch stand (Mozilla Firefox, Google Chrome) as of August 2015? Are there any new alternative pieces on the browser market, or do we have to stick with what we know?
Wait… Did we leave out Google?
Google is a leader, but obviously – it is not THE leader, at least not assets-wise. Despite the company’s efforts to impose Google products on everyone, Forbes has put them at number 39 with their assets being $131.1 billion. Nonetheless, Google may hold the torch as a brand since it has become a synonym for ‘search’. Do you say ‘search it on the Internet’ or simply ‘Google it’?
Let’s start from the beginning.
Web Browser History: the First Browser
Corporation-ran or not, the Internet cannot exist without browsers. As a matter of fact, the very first web browser was invented back in 1990 by Tim Berners-Lee, the director of W3C (World Wide Web Consortium). As all tech geeks know, Sir Berners-Lee is a world renowned computer scientist who invented the WWW. In March 1989, before his creation outgrew his name, he made a proposal for an information management system. This is when he also administered the first successful connection between an HTTP client and a server. The pioneer browser was called WorldWideWeb, but the name was changed to Nexus in 1994.
When the first webpage was created, a web browser had to be created as well. The essential point about Berners-Lee’s browser, Nexus, is that it was a browser-editor. As pointed out by Digital Archeology, when Tim Berners-Lee’s first website is open, the page is displayed separately from the browser.
Evolution of Web Browsing
How have web browsers evolved since the WorldWideWeb and Nexus pioneers?
The evolution process of web browsing is surely complicated and full of ups and downs. One thing is definite – Web browsing is as common as drinking coffee at Starbucks – and the two often come together. During the past few years, the browser market has seen lots of popularity battles. Those battles are nothing but periodic and are often cause and effect of new software products, mobile trends and vastly changing market shares. Since the beginning of 2015, we are also witnessing a notable emerging of niche browsers such as Vivaldi.
Thus, everything comes down to the question… Which is the best browser security-wise of 2015?
Browser Stats: The Best Browser of 2015
Because we know that truth tends to reside in the middle, what we can do to appraise a winner is evaluate the pros and cons of widely used browsers. Additionally, identifying the best alternative browsers is also crucial to building a detailed depiction of the modern WWW tools.
In terms of security, browser vulnerabilities can be divided according to their impact:
- Critical Vulnerability. It can be used to run malicious code and install software, and it needs no user interaction beyond normal browsing.
- High Vulnerability. It can be deployed to harvest sensitive data from web sites in other windows or inject data or code into the same websites, again requiring nothing else but normal browsing activities.
- Moderate Vulnerability. It could be high or critical except it only works in uncommon non-default configurations. Furthermore, it requires the user to perform actions that may appear unlikely.
- Low Minor Vulnerability. It can be Denial of Service attacks, minor data leaks, or spoofs.
Vulnerabilities in Mozilla Products
A total of 1228 vulnerabilities have been found and fixed in Firefox since its first release.
According to Mozilla.org, 16 vulnerabilities have been enclosed and fixed in Firefox 40. Some of the vulnerabilities were found thanks to code inspection. Interestingly enough, those weak spots are often high in impact and can be quite problematic.
As of August 2015, three vulnerabilities have been discovered via code inspection, and reported by security researcher Ronald Crane. The vulnerabilities can exploit:
- The use of unowned memory.
- The use of a deleted object.
- One particular memory safety bug.
The vulnerabilities could affect Firefox, Firefox ESR, Firefox OS, and Thunderbird. Accordingly, they were fixed in:
-
Firefox 40
Firefox ESR 38.2
Firefox OS 2.2
Thunderbird 38.2
Vulnerabilities in Google Chrome
According to CVE details, a total of 1228 vulnerabilities have been located in Chrome.
As of June 2015, multiple bugs have been identified in Google Chrome, which could lead to remote code execution. The vulnerabilities can be exploited in the context of the browser when a user is redirected to an attacker page. The risk of the enclosed vulnerabilities is defined as High for governments, businesses, and common users.
Here is a list compiled by Multi-State of the bugs that affect Google Chrome prior to Google Chrome 44.0.2403.89:
- Heap-buffer-overflow in pdfium (CVE-2015-1271)
- Heap-buffer-overflow in pdfium (CVE-2015-1273)
- Settings allowed executable files to run immediately after download (CVE-2015-1274)
- UXSS in Chrome for Android (CVE-2015-1275)
- Use-after-free in IndexedDB (CVE-2015-1276)
- Heap-buffer-overflow in pdfium (CVE-2015-1279)
- Memory corruption in skia (CVE-2015-1280)
- CSP bypass (CVE-2015-1281)
- Use-after-free in pdfium (CVE-2015-1282)
- Heap-buffer-overflow in expat (CVE-2015-1283)
- Use-after-free in blink (CVE-2015-1284)
- UXSS in blink (CVE-2015-1286)
- SOP bypass with CSS (CVE-2015-1287)
- Uninitialized memory read in ICU (CVE-2015-1270)
- Use-after-free related to unexpected GPU process termination (CVE-2015-1272)
- Use-after-free in accessibility (CVE-2015-1277)
- URL spoofing using pdf files (CVE-2015-1278)
- Information leak in XSS auditor (CVE-2015-1285)
- Spell checking dictionaries fetched over HTTP (CVE-2015-1288)
- Various fixes from internal audits, fuzzing and other initiatives ( CVE-2015-1289)
Vulnerabilities in Internet Explorer
There was a time when Internet Explorer was the most prevalent browser. However, many things have changed since then, and many vulnerabilities have been discovered. As a total, 613 vulnerabilities have been identified in IE, 13 of them were updated in August 2015. Let’s have a look:
→CVE-2015-2502 CVE-2015-2452 CVE-2015-2451 CVE-2015-2450 CVE-2015-2449 CVE-2015-2448 CVE-2015-2447 CVE-2015-2446 CVE-2015-2445 CVE-2015-2444 CVE-2015-2443 CVE-2015-2442 CVE-2015-2441
12 of the listed CVEs are aimed at denial-of-service attacks, and one of them is described as bypass+info (CVE-2015-2449).
Vulnerabilities in Safari
The belief that Apple is invincible is clearly a myth. According to CVE details, a total of 598 vulnerabilities has been reported in Apple’s Safari, 28 of them updated in August 2015. Most of them are a denial-of-service type (DoS Exec Code Overflow Mem. Corr.), and the rest are “Info” and “Bypass + Info”.
In terms of security, the conclusion is that there is no such thing as a safe browser. It all depends on the company patch policy, and the time it needs to address and fix the security loopholes.
What about popularity rates?
Which is the most preferred browser of 2015?
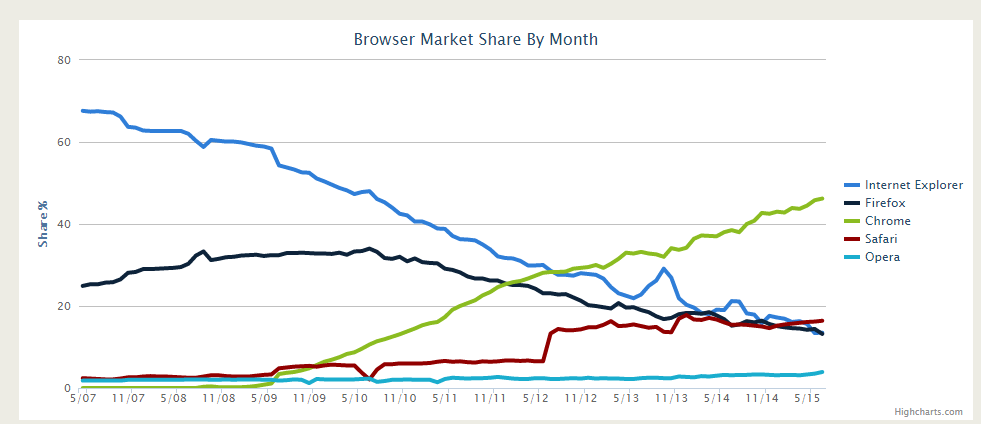
According to Global Web Stats from W3Counter, the most prevalent web browser of 2015 is Google Chrome.
Also, make sure to check out Most Secure Browser for 2014
What about the Edge Browser?
As we have already written, the Edge Browser doesn’t turn out to be popular among Windows 10 users. According to analytics vendors, the market share for Edge is quite tiny. For July, the percentage of user share is estimated at only 0.39. Because Edge only runs on Windows 10, it was run by 36% of potential clients.
More about Edge Browser
A New Browser on the Horizon: Vivaldi Browser
Have you heard about the Vivaldi Browser? It is a freeware web browser developed by Vivaldi Technologies for Windows, OS X, and Linux. The company is established by former Opera cofounder and CEO Jon Stephenson von Tetzchner. Vivaldi is aimed at heavy Internet users and ex-Opera users that were disappointed by the company’s transition from the Presto layout engine to the Blink one.
The change resulted in the removal of many popular features. Hence, it is safe to assume that the Vivaldi browser has emerged from a stable background and will attempt to evolve the old features of Opera 12 and include new, innovative technique on the niche browser marker. According to Wikipedia, Vivaldi is updated on a weekly basis and has already gained popularity among users.
Browser Security 2015: The Conclusion
Browsing is something we all need to do. Some of us may be more educated on the IT security topic while others tend to forget that the Internet is not as safe as it once may have been. By identifying the vulnerabilities in widely used browsers – Firefox, Chrome, Explorer, and Safari – it’s easy to jump to the conclusion that no browser is as safe as we would like it to be. Whatever you do while browsing the Web, just keep in mind that you’re not anonymous and can be easily tracked and identified. Unless you share genes with Mr. Robot’s Elliot Alderson.
In addition, to make sure that your browser hasn’t been leveraged, you can scan your system and frequently update your AV program.
| Download SpyHunter, to See If Your System Has Been Affected |






Nice “conclusion.” Afraid to alienate people by not taking sides?
Haha, not at all :) Detailed information about vulnerabilities in widely used browsers is provided in the article. However, we all have our own preferences, and articles shouldn’t decide instead of people, should they?
Stay tuned,
Milena
But it’s not subjective, one browser is the most secure. Which one is it?
In 2015/2016 Chrome was most secure, but has a doubtful privacy (Google spying on you: logging everything you do. But since Chrome’s sourcecode is not 100% open, we cannot be sure, but there were tests with networksniffing suggesting this.).
Firefox is best for privacy (Firefox also is the only one that open sourced 100% of their sourcecode, making it a very reliable browser, because people study this code, looking for mistakes)
IE is reasonable good since version 10.
Edge is largely unknown (small userbase)
Hi Erwin and Cubzy,
Here’s our 2016 edition: sensorstechforum.com/which-is-the-most-secure-browser-for-2016-firefox-chrome-internet-explorer-safari-2
So why put a conclusion if you didn’t pick one? The whole article basically just showed info but no decision. I know you don’t wanna take sides but at least put what you guys would pick. Forget the fanboys stats don’t lie so if ones better and more secure list it
If you look at the actual exploit database statistics that break down exploits by category, Chrome looks to be the most secure and that is in spite of having double the listed vulnerabilities of Internet Explorer, for example.
The reason why is because IE, FireFox, and Safari all have more “code execution” exploits. The majority of Chrome’s listed exploits are DOS (Denial of Service), which are annoying, but not nearly as severe in the big scheme of things.