 This article has been created in order to explain to you what is the Apple ID Phishing Scam and how you can remove them as well as all potentially unwanted programs delivered through them.
This article has been created in order to explain to you what is the Apple ID Phishing Scam and how you can remove them as well as all potentially unwanted programs delivered through them.
The Apple ID Phishing Scam is a popular malware tactic that attempts to manipulate Apple users into infecting themselves with viruses or disclosing their passwords. At the moment we do not have information about the perpetrators behind it. Our article gives an in-depth explanation of how it propagates and how victims can attempt to remove active infections.

Threat Summary
| Name | Apple ID Phishing Scam |
| Type | Phishing email scam |
| Short Description | The Apple ID Phishing Scam is a recent example of the scam tactic that extorts the targets into interacting with a scam site. |
| Symptoms | Victims will receive email messages that contain the phishing instructions. |
| Distribution Method | Phishing emails. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss Apple ID Phishing Scam. |

Apple ID Phishing Scam — Update April 2020
In April 2020 phishing attacks using the social engineering strategy of impersonating Apple ID messages continues. An unknown hacking group is behind the attacks. It is spread via email messages which are sent in bulk. Infected computers and web mail servers are sending out notifications that manipulate the recipients into thinking that their accounts have been locked by Apple. The users will be redirected to a hacker-controlled page, in most cases the addresses are configured to be phishing login pages. The main goal of the hackers are to hijack the credentials of the victims.

Apple ID Phishing Scam – Distribution Ways

The Apple ID phishing scam is distributed using various methods. The main one is the creation of sites that share a similar name to Apple and their services. They are distributed using various methods:
- Social Network Links — By using fake or hacker-made profiles on popular social networks (Facebook, Twitter, Instagram and etc.) the Apple ID phishing scam can be promoted. Usually shortened links are used to link the main pages.
- Email Messages — Bulk email messages containing links to the Apple ID phishing page can be sent to the users in both personalized and non-personalized forms. The malicious actors can use the same design layout, body contents and elements as real Apple emails.
- Similar Sounding Names — The Apple ID phishing scam can be distributed on various sites that all have a similar sounding domain name to Apple.
Note that the Apple phishing ID landing page can be displayed by software and files as well. A prime example is the modified software installer — the criminals take the setup files of popular software and add to them the code that shows the phishing page. The other type is the creation of infected documents that can be of any popular type: rich text documents, presentations, databases and spreadsheets. When they are opened a prompt will appear asking the users to enable the built-in scripts. When this is done the links will be opened in a browser window or directly as an embedded object.
In some cases the hackers can also make use of malware browser extensions, alternatively known as hijackers. The criminals make them compatible with the most popular web browsers in order to increase the number of victim users. They are frequently uploaded to the official hacker repositories using fake or stolen user reviews and developer credentials. The uploaded strains feature descriptions that promise the optimization of the browsers or the enhancement with newer features. If the users install them then the typical hijacker behavior will be observed. Direct effects are the manipulations of the web browsers into directly redirecting the users to the Apple ID phishing scam page. This is done by changing the default values — home page, new tabs page and search engine.

Apple ID Phishing Scam – In-Depth Overview

When the Apple ID phishing scam page is displayed to the users the basic view will show a login page that uses the design layout and elements of the real Apple site. The hackers manipulate the users into believing that a site belonging to the company is being accessed. Scams such as this one feature several distinct elements, one of the main ones is the fact that many copies of the page can be created. They can be hosted on servers around the world — not all of them will be served on the same domains. From an administrator point of view this gives the hackers greater flexibility as they can easily deploy thousands of them in a short period of time. To further coerce the users into thinking that they are accessing real Apple pages they can use include security certificates and cross-site linking.
The main goal of the page is to coerce the users into revealing their account credentials to the site. They will be automatically transferred to the malicious operators of the Apple ID phishing scam site as soon as they are entered. However there are other malicious actions that may be executed. All of them are connected to the site interaction in some way or another.
Visiting the sites can lead to the installation of tracking cookies and data collection modules. They will automatically hijack data both from the web browsers and the infected devices. There are two main categories of data that can be distinguished:
- Anonymous Statistics — The cookies will be able to track how the users interact with various web elements.
- Private Data — The data collection of information that can directly expose the identity of the victims.
Through the various scripts the machines can be come infected with cryptocurrency miners as well. They represent applications that make use of the available system resources in order to run complex mathematical calculations. When the successful tasks are reported to the relevant servers the hacker operators will receive profit in the form of cryptocurrency. An additional consequence is the delivery of intrusive ads — they can cause redirects to other malware sites or present links to sponsored content. In most cases all popular mechanisms can be used: pop-ups, banners, in-line links and etc.
If any file downloads are offered then practically all types of malicious payloads can be offered. The files themselves will probably be renamed with Apple related services, products and software. Beware that among the most frequently used strings used to rename such payloads include “update” and “manual”. Common infections include the following:
- Direct Virus Downloads — Virus files across all common types can be delivered: ransomware, Trojans, miners and etc.
- Documents with Malware Scripts — The Apple ID phishing scam page can also distribute malware via documents. The users will find that various files of all popular types can contain the malicious scripts: rich text documents, spreadsheets, presentations and databases. Whenever they are opened by the victims a prompt will appear asking for the users to enable the built-in macros. If this is done the scripts will download a preset virus from the Internet and launch it on the local computer.
- Malicious Setup Files — The criminals can also create copycat malicious installers of popular software. The most common way is to take the real file from the official vendor site and add the necessary scripts to them. The reason why this approach is particularly popular is that it targets applications that are often used: creativity suites, system utilities and productivity apps.
In some cases scams like this one can be used to spread Trojan viruses. They represent advanced malware that set up a client service to a hacker-controlled server. The connection is made both secure and constant thus allowing the hackers to overtake control of the machines at any given time. This also includes the retrieval of user data, spying in real-time and deploying other viruses at will. Through it the hackers can also recruit the machines to botnet networks which are particularly useful for organizing distributed attacks against pre-selected targets.

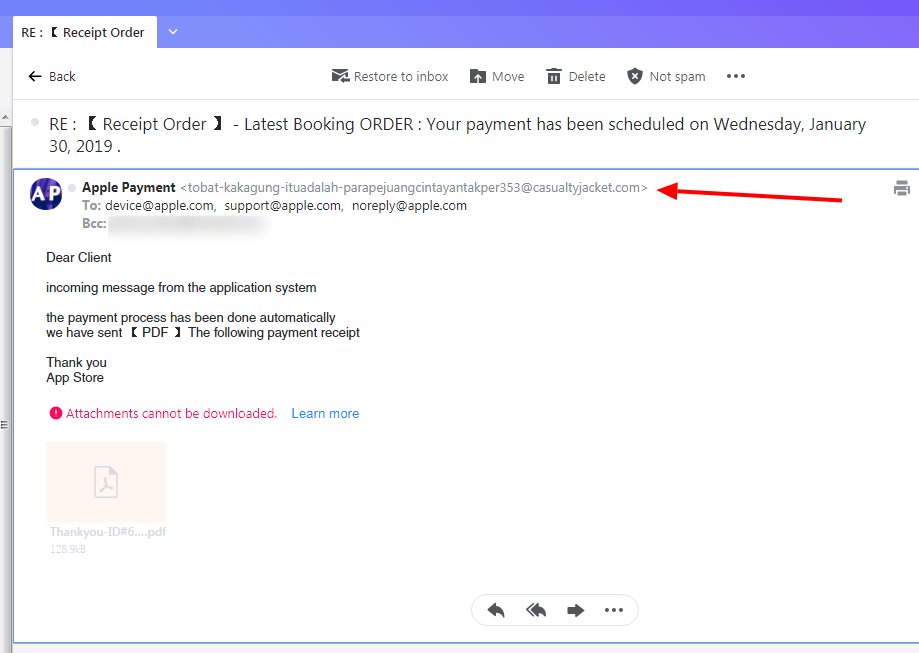
Apple ID Phishing Scam Example — Receipt Order Email
A wave of phishing Apple ID scams are being coordinated against end users using the subject line of “Receipt Order” following by information about a booking order with the company. This tactic attempts to confuse them into thinking that a made payment for Apple’s services has been processed and that information about the transaction is available in the attached payment receipt. The messages will have PDF file attachments which contain virus code in their macros or are direct samples. If the file is launched it will most likely lead to a dangerous infection.

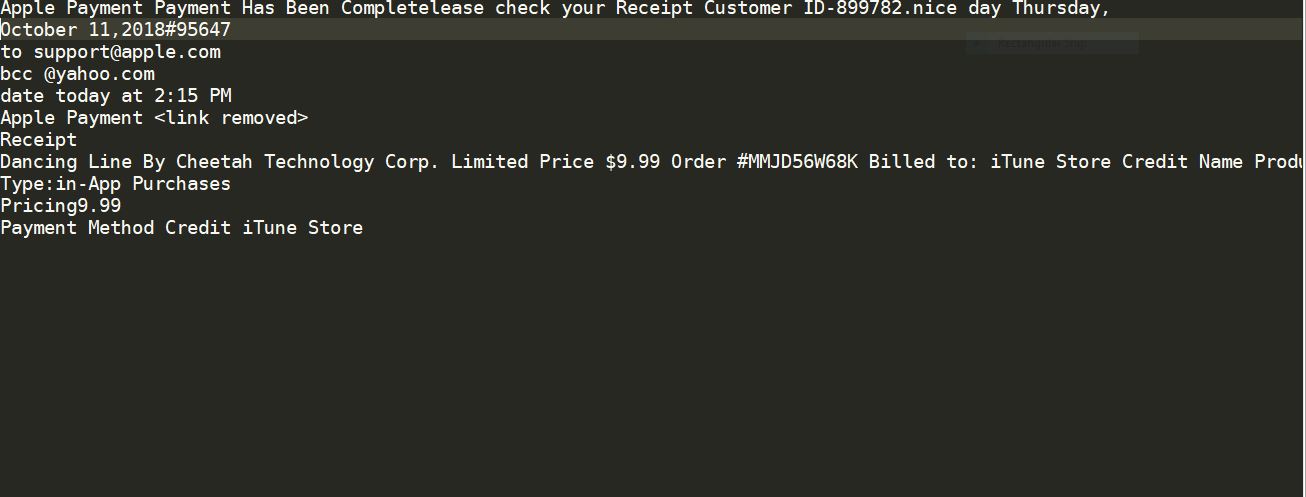
Apple ID Phishing Scam Example — Apple Payment Payment Has Been Complete
Security alerts indicate a new phishing scam making use of malicious web pages and social network messages as the main medium. We have received an email-based sample which is made to look like as it was sent by Apple. The message contents will include elements that may be mistaken for real data:
- Customer ID
- Date
- Receipt Details
The message motions to the targets that a payment through Apple has been made quoting randomly-generated fields such as customer and order ID and the date of completion. This scam is deemed very effective as Apple payments are widely used in some areas and users might not be aware that this is a fraud notification. The email may insert links to various end pages. Some of the possible ones include the following:
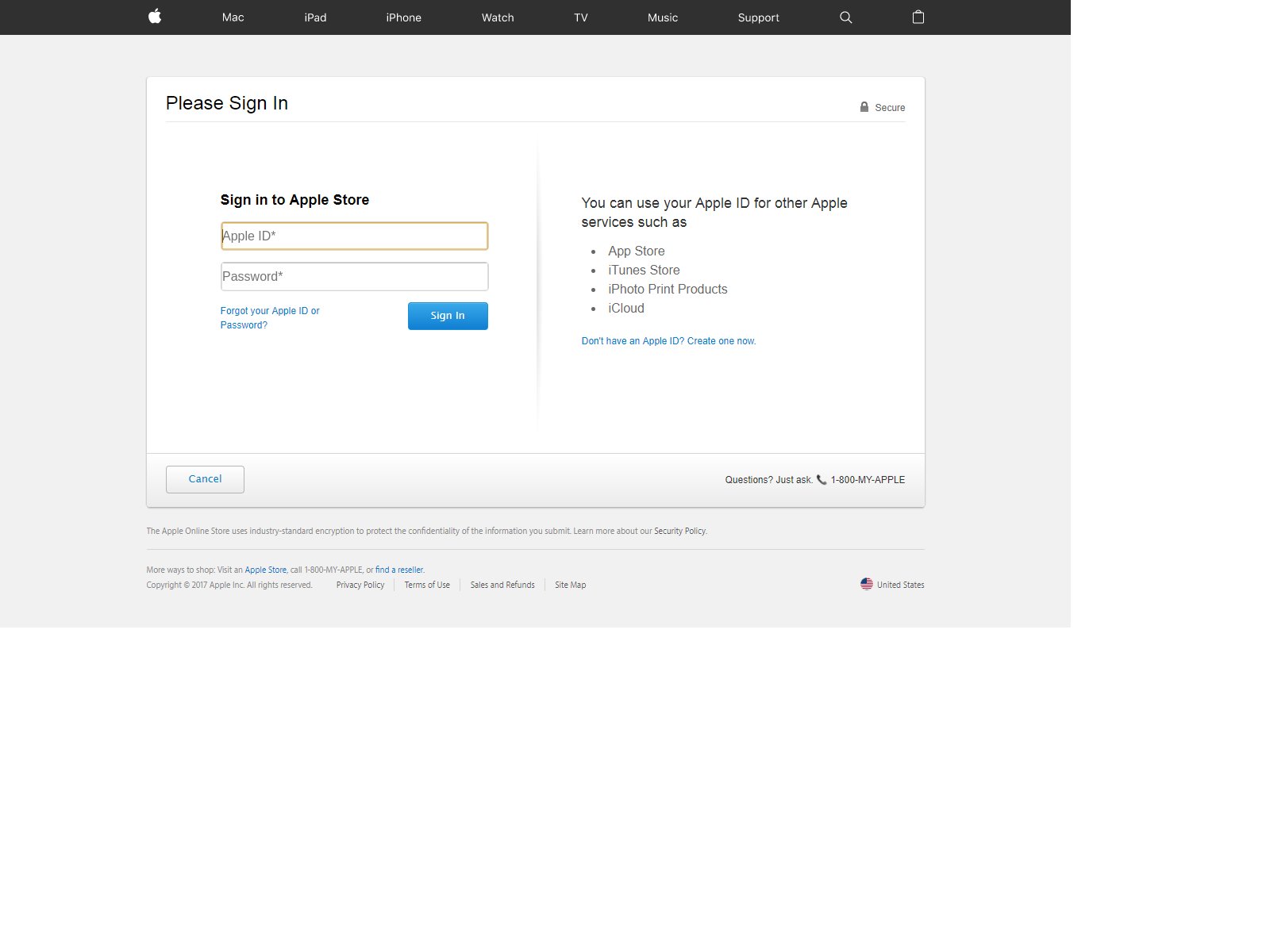
- Fake Login Pages — The victims can be forwarded to fake Apple login pages where the victims are requested to enter in their Apple ID credentials. The pages can be designed to look just like the real ones and the only difference can be the domain name or security certificate. As soon as the information is entered the hacker operators will be able to take over the accounts. This makes it possible to conduct both financial abuse and identity theft.
- Virus Downloads — The other possible end goal is to deliver a malicious payload via one of the links found in the emails. It can be any of the popular virus types: miners, Trojans, ransomware and etc.
- Advertisements — The other possible outcome is to direct the targets to a page with intrusive advertisements. For every click a profit of several cents will be made for the operators. Larger campaigns can generate a good source of income for the criminal collective directing such attacks.
An example message reads the following:
Apple Payment Payment Has Been Completelease check your Receipt Customer ID-899782.nice day Thursday, October 11,2018#95647
to support@apple.com
bcc @yahoo.com
date today at 2:15 PM
Apple Payment Receipt
Dancing Line By Cheetah Technology Corp. Limited Price $9.99 Order #MMJD56W68K Billed to: iTune Store Credit Name Products: Large Coin Box
Type:in-App Purchases
Pricing9.99
Payment Method Credit iTune Store

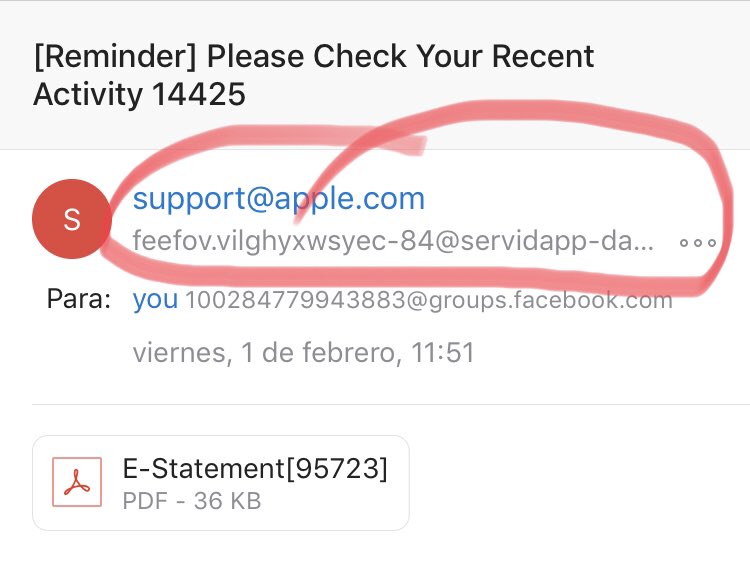
Apple ID Phishing Scam Example — Please Check Your Recent Activity 14425 Email Messages
A recent wave of phishing email messages have been detected by researchers. According to the available reports the newest attack campaign is launched against users at a global scale. In it a contact address belonging to Apple has been spoofed (support.apple.com) and the subject line reads generic titles such as this one: [Reminder] Please Check Your Recent Activity 14425 wherein the number can be changed to a random one. No body contents is available and the users will see only an attached PDF file. They may be enticed into clicking on it which will lead to a malware infection.

Apple Phone Phishing Scams
A new wave of phishing scams has been discovered in early January 2019 utilizing phone calls. The hackers will automate calls to the intended targets with spoofed company elements: logo, address and real phone number. The quoted trigger message delivered to the victims is that a data breach has occurred.
When the targets call the number a man with Indian accent will pick up the phone and persuade them into thinking that they have called the legitimate Apple support line. If the users fall for the fraud call then their personal information will be gathered, as well as Apple account credentials. They may be guided into paying a “security fee”.

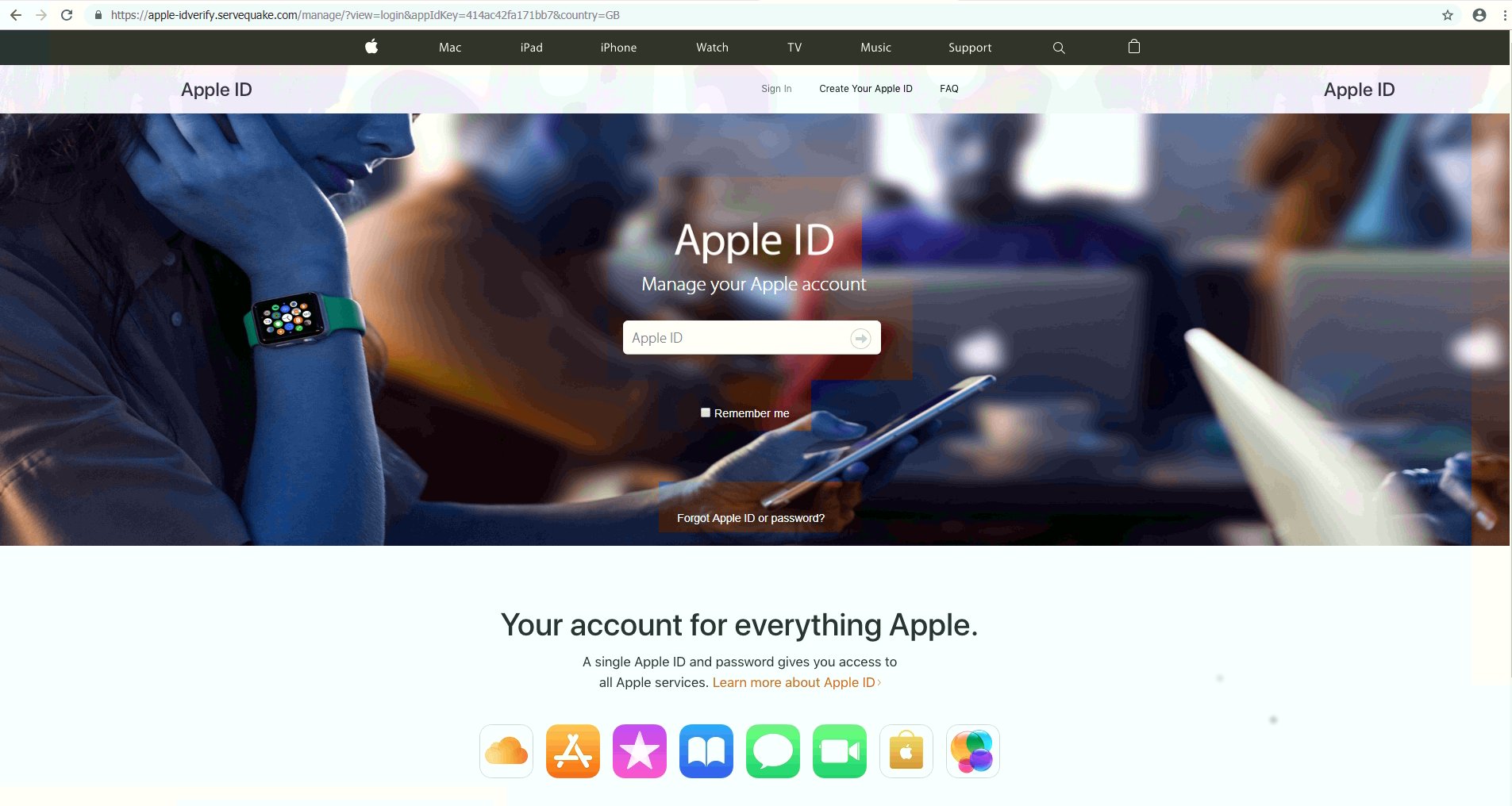
Apple ID Phishing Scam Example — Apple Store Login
This is another landing page based phishing scam which attempts to coerce the targets into revealing their account credentials. The page will copy Apple’s design and will probably be hosted on several domains that bear an almost identical name to Apple or any of its products. This is intentionally made to navigate the users into it if they accidentally mistype the legitimate address.
While presenting a login page with links to real Apple pages is a classic approach, there are many ways through which it can spread. Depending on the actual means of distribution the outcome can vary. If several methods are used at once then there will be a very high number of potential victims. This Apple ID scam landing page is very likely to be found via shortened links that are sent via email messages and social network profiles (both posts and direct messages). The hackers can retrieve whole databases of base information and start the outbreak.

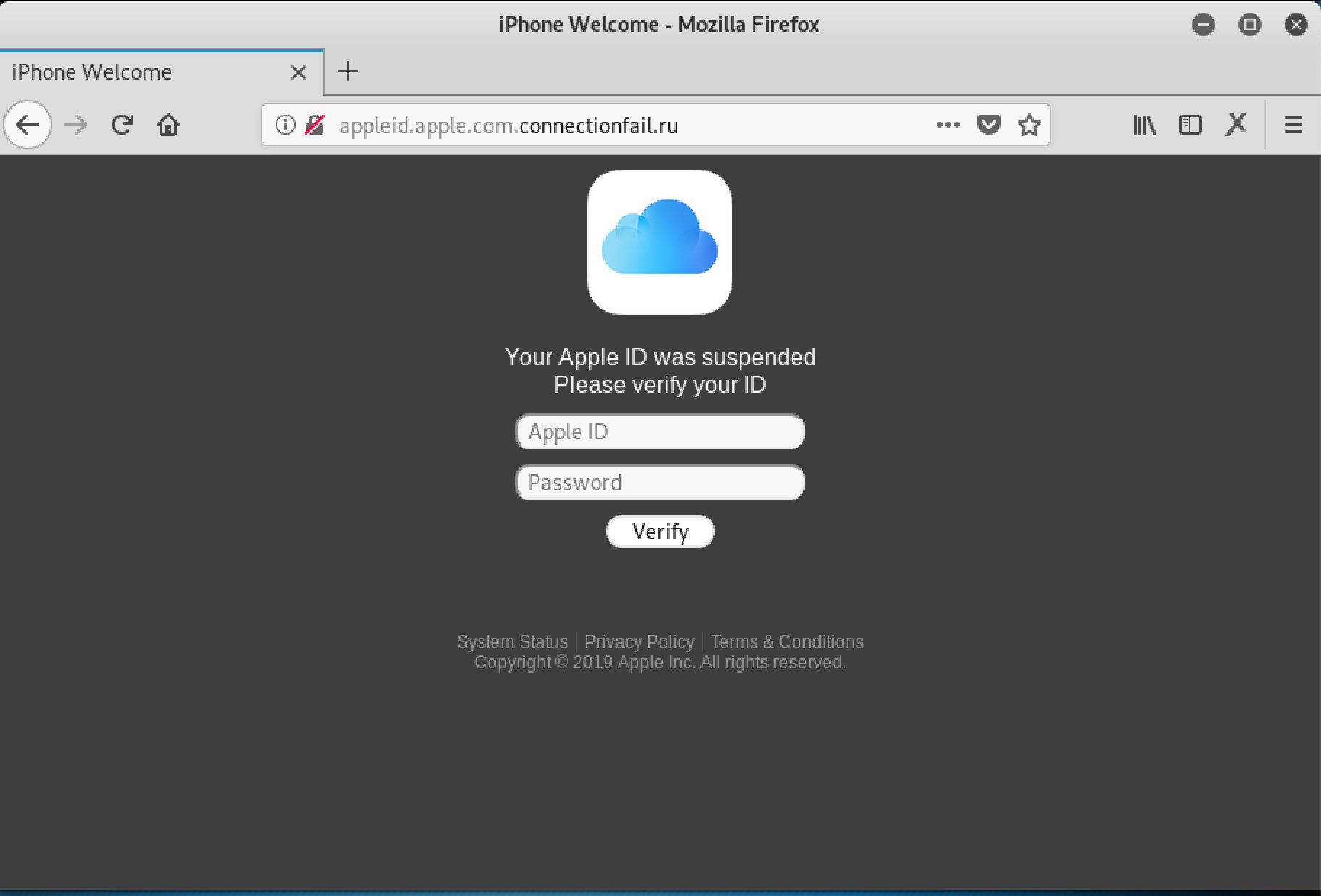
Apple ID Phishing Scam Example — Suspended Apple ID
A new scam related to the other Apple phishing campaigns has been detected. It is being distributed as a landing page that requests the victims to enter in their Apple ID details. There are several forms of possible source however we anticipate that email messages and payload carriers are the most likely delivery agents.
The landing page will not have a security certificate issued to Apple and users may find that some of the links will not lead to the Apple site. Bear in mind that landing pages like this one are also short-linked and uploaded to social media profiles that are either stolen or hacked. The user accounts are either hacked or stolen.

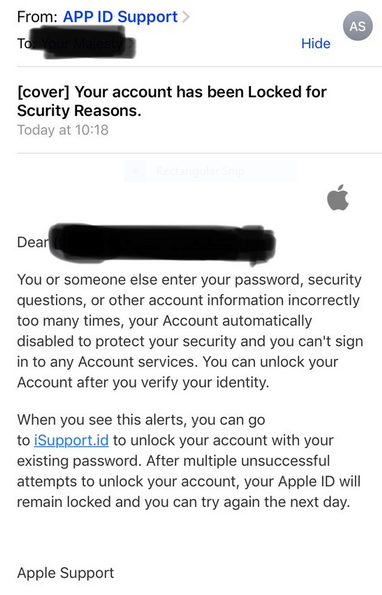
Apple ID Phishing Scam Example — Locked Account Warning
The hackers will send out a fake notification message that is created in a way that resembles Apple Support. Its body contents will persuade the recipients into believing that their Apple account is locked due to incorrect login attempts. To unlock them they are redirected to a fake login page which will request their email address and password combination. If they are entered the credentials will immediately be transferred to the hacker operators of the scam and they will take over he victim accounts.

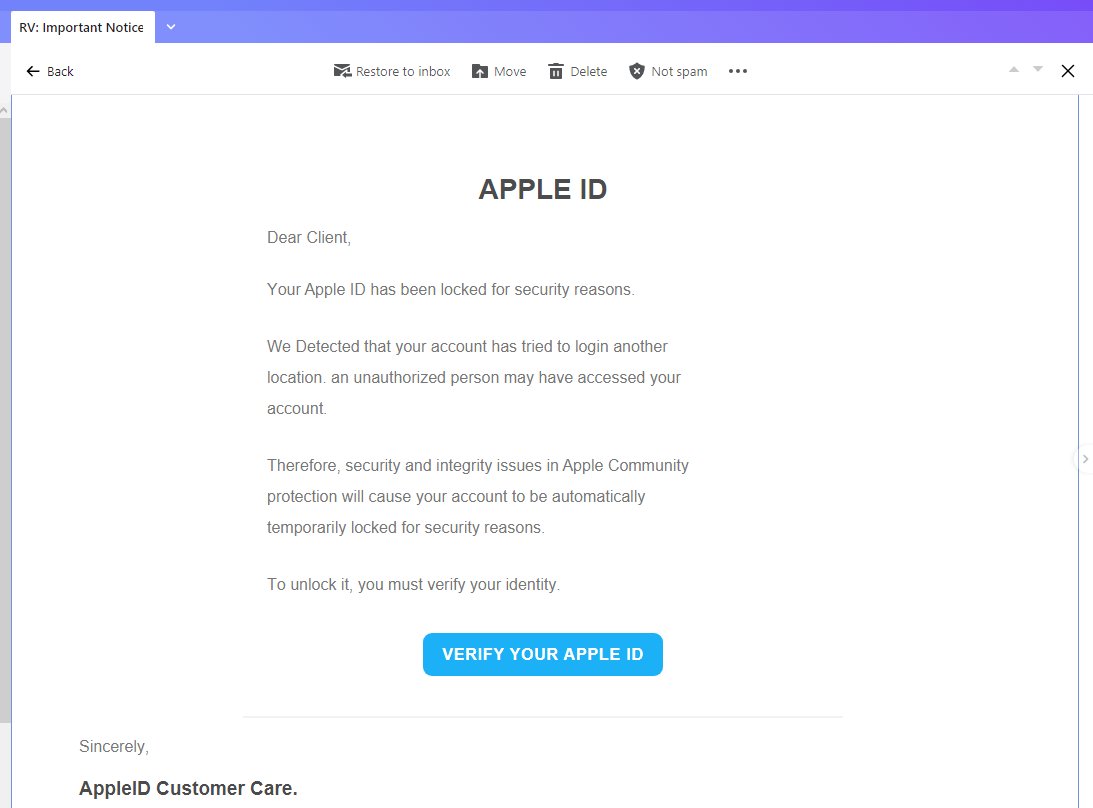
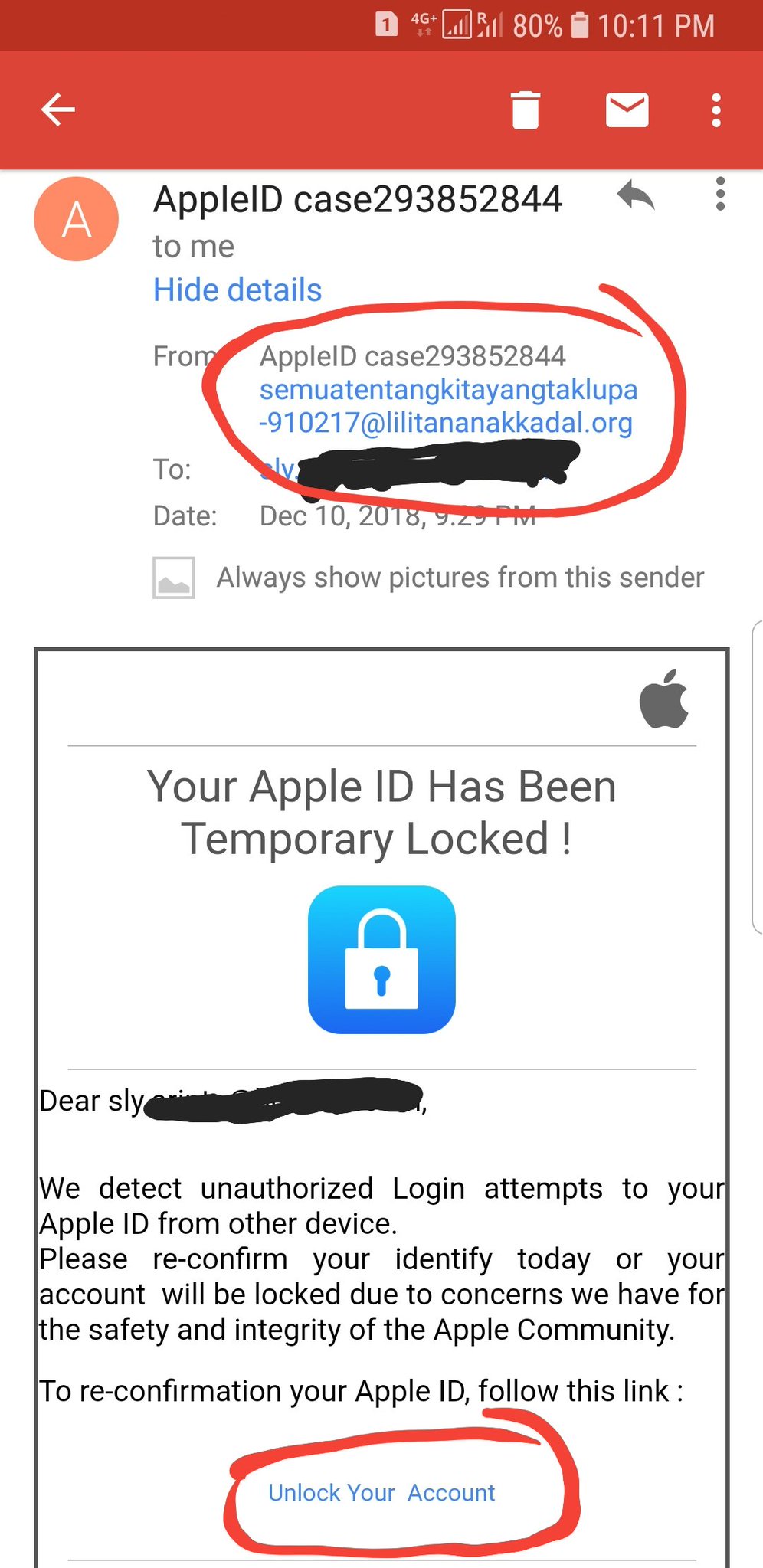
Apple ID Phishing Scam Example — Your Apple ID Has Been Temporary Locked
Another Apple ID scam that has been identified is an email phishing tactic that manipulates the recipients into thinking that their Apple ID has been locked. Like the other examples it uses familiar Apple-like styling and presents a link to “unblock” the said accounts. When it is accessed it will lead to the same phishing landing page. The users will be asked for their email, username and password or any other combination of credentials in order to “verify” their information. Take note that some Apple ID scams can ask for other information as well — secret questions and answers combinations or birth dates.

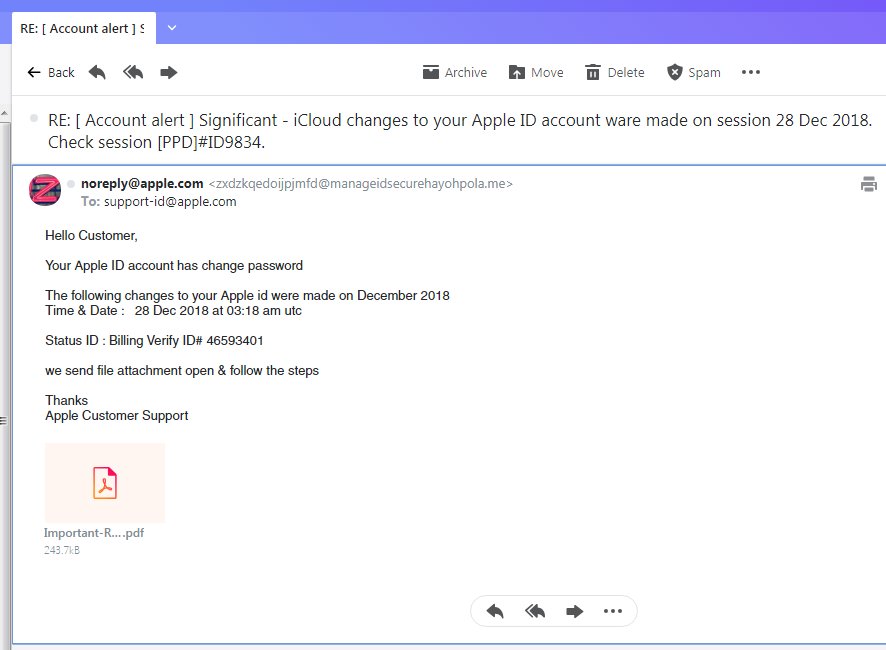
Apple ID Phishing Scam Example — Apple ID Changed Password
This is a recent example of an Apple ID phishing scam which coerces the recipients into thinking that they have received a legitimate Apple security warning. The email message will read that the user’s account has had their password changed. Following this action a report has been generated which is attached as a PDF file. This is a classic case of a payload delivery scheme. As soon as the file is opened a virus delivery will be initiated. It can be done either instantly or when the users choose to activate the built-in scripts.
What’s particularly worrying about this particular scenario is that the message will quote time and date of the purposed incident, along with a status ID ticketing which may appear very convincing to many Apple users. The message will feature a bounced sender field coming in from the Apple.com domain. The non-personalized approach may feel similar to the approach Apple has with its own legitimate message notifications.

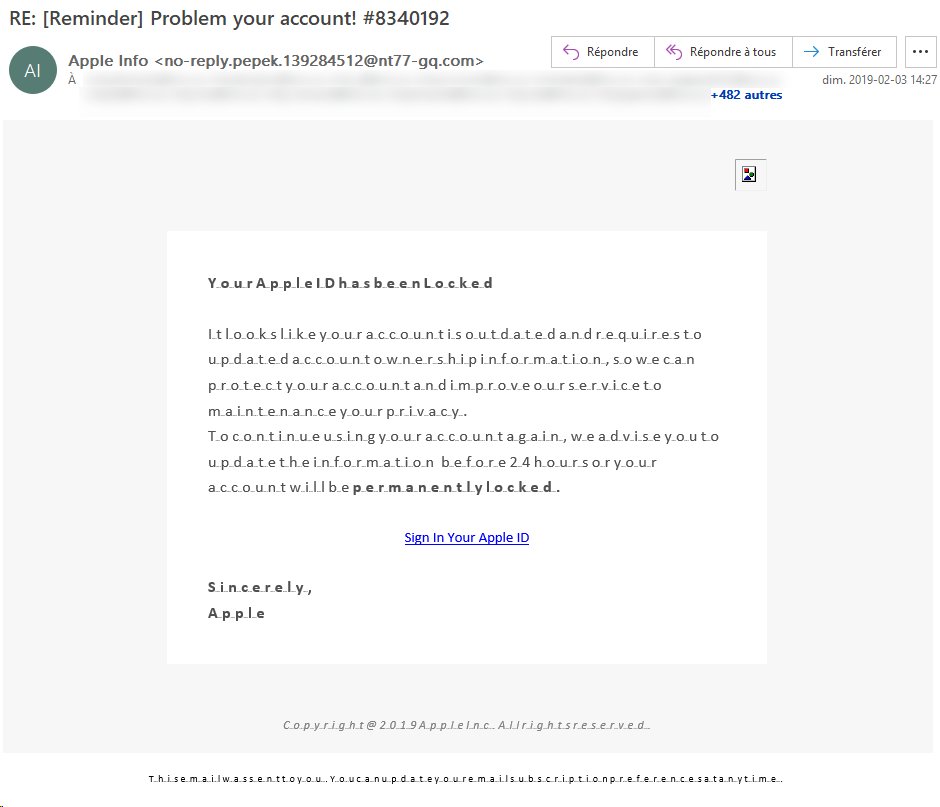
Problem Your Account Reminder Apple ID Scam
A distinct phishing email message that an Apple ID user might receive is the fake reminder with the subject line “Problem your account!”. These messages are being sent by a hacker-controlled email address that identifies itself as “Apple Info” and sends out an incorrectly-formatted notification that informs that recipients that they need to sign in to their Apple ID accounts.
The victim users will notice that the body contents of the email messages contains broken text layout — this is intentionally done in order to emulate an issue that the users may be having with their computer. This is linked to the made-up locked account which can additionally entice the targets. The warning signs that this is a fake message are the fake subject line — the number quoted in the end does not represent any ID or another form of personalized greeting to the victim. The body layout and text contents from Apple will never be styled in this way and the sender’s email address will be from the company’s domain name. Additionally the “Sign In Your Apple ID” will lead to a fake login page — the URL is traced to a domain not owned by the company.

Remove Apple ID Phishing Scam from Windows and Your Browser
If you want to remove the Apple ID Phishing Scam from your computer, we strongly suggest that you follow the removal instructions posted underneath this article. They have been created with the main idea In mind to help you delete this virus either manually or automatically. Be advised that according to experts the best way to try and remove the software that is causing the Apple ID Phishing Scamming pop-ups is to use an advanced anti-malware software. Such program is created with the idea in mind to fully scan your computer and try to eliminate any traces of unwanted programs while protecting your computer against future infections as well.
Steps to Prepare Before Removal:
Before starting to follow the steps below, be advised that you should first do the following preparations:
- Backup your files in case the worst happens.
- Make sure to have a device with these instructions on standy.
- Arm yourself with patience.
- 1. Scan for Mac Malware
- 2. Uninstall Risky Apps
- 3. Clean Your Browsers
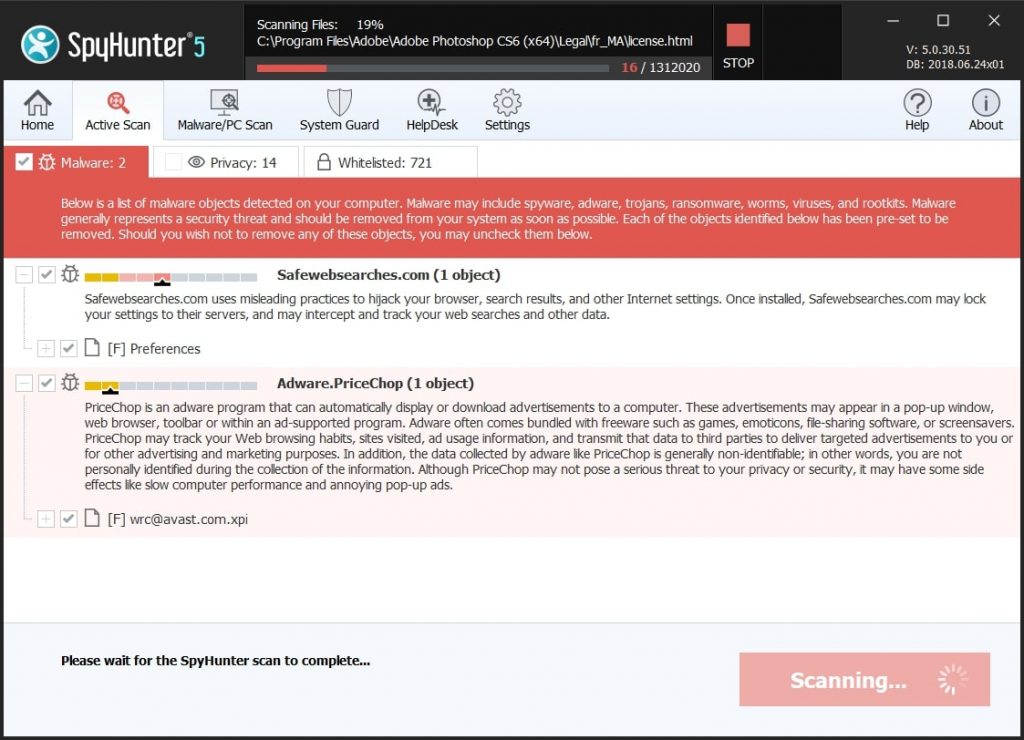
Step 1: Scan for and remove Apple ID Phishing Scam files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as Apple ID Phishing Scam, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Quick and Easy Mac Malware Video Removal Guide
Bonus Step: How to Make Your Mac Run Faster?
Mac machines maintain probably the fastest operating system out there. Still, Macs do become slow and sluggish sometimes. The video guide below examines all of the possible problems that may lead to your Mac being slower than usual as well as all of the steps that can help you to speed up your Mac.
Step 2: Uninstall Apple ID Phishing Scam and remove related files and objects
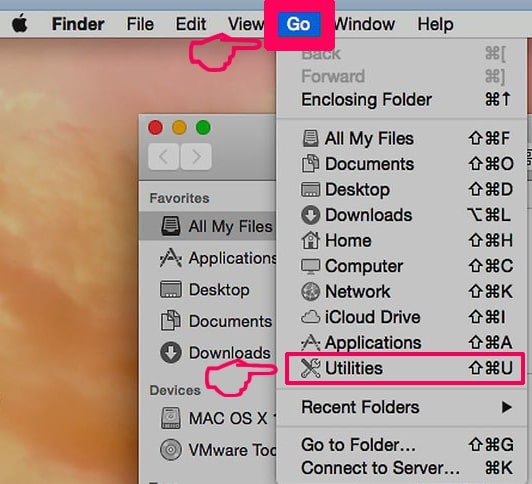
1. Hit the ⇧+⌘+U keys to open Utilities. Another way is to click on “Go” and then click “Utilities”, like the image below shows:
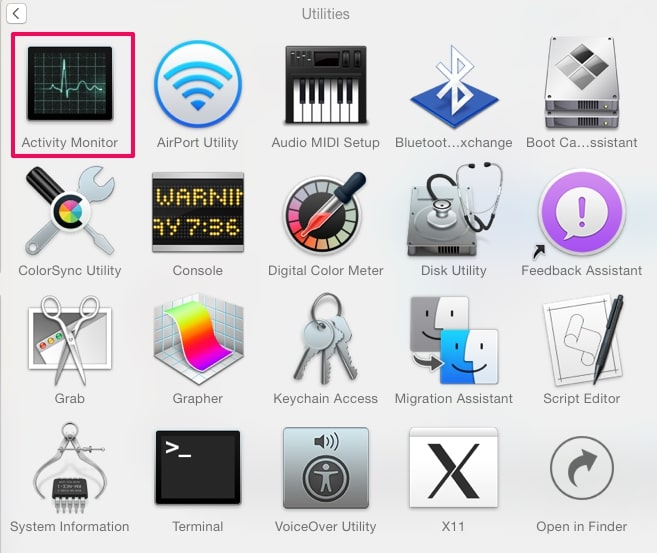
2. Find Activity Monitor and double-click it:
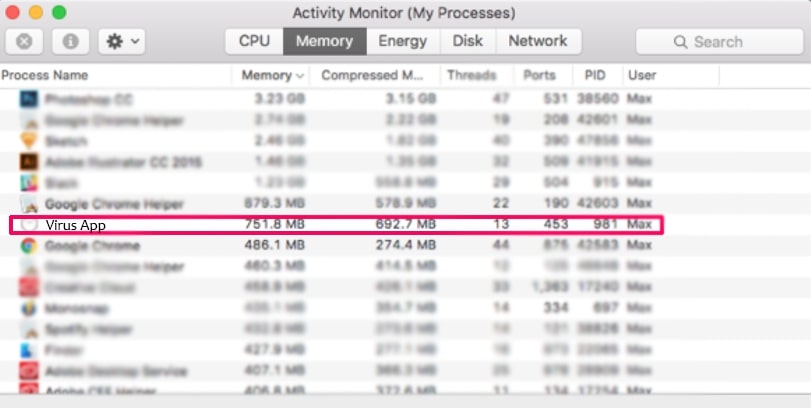
3. In the Activity Monitor look for any suspicious processes, belonging or related to Apple ID Phishing Scam:
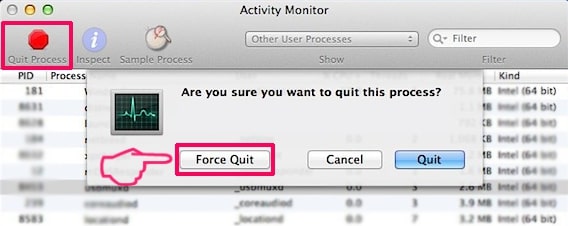
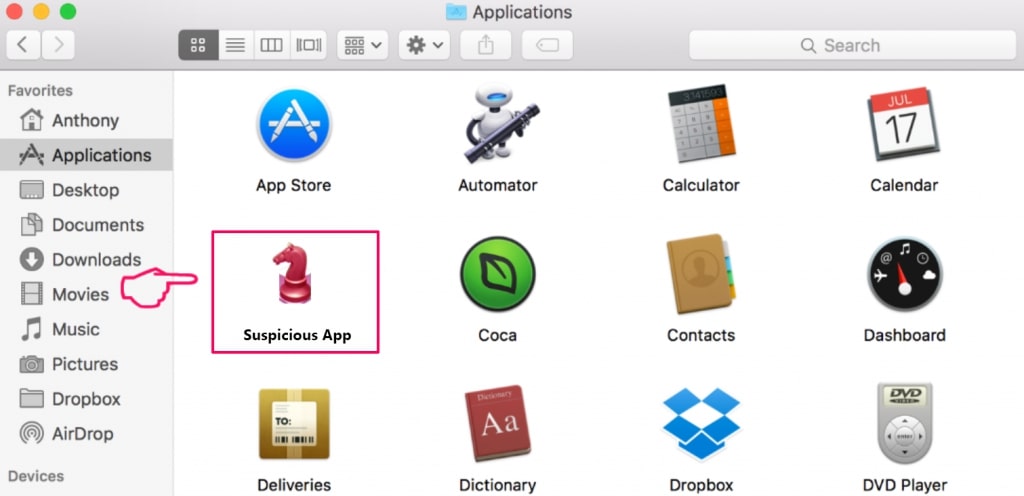
4. Click on the "Go" button again, but this time select Applications. Another way is with the ⇧+⌘+A buttons.
5. In the Applications menu, look for any suspicious app or an app with a name, similar or identical to Apple ID Phishing Scam. If you find it, right-click on the app and select “Move to Trash”.
6. Select Accounts, after which click on the Login Items preference. Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to Apple ID Phishing Scam. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
7. Remove any leftover files that might be related to this threat manually by following the sub-steps below:
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove Apple ID Phishing Scam via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
1. Click on "Go" and Then "Go to Folder" as shown underneath:
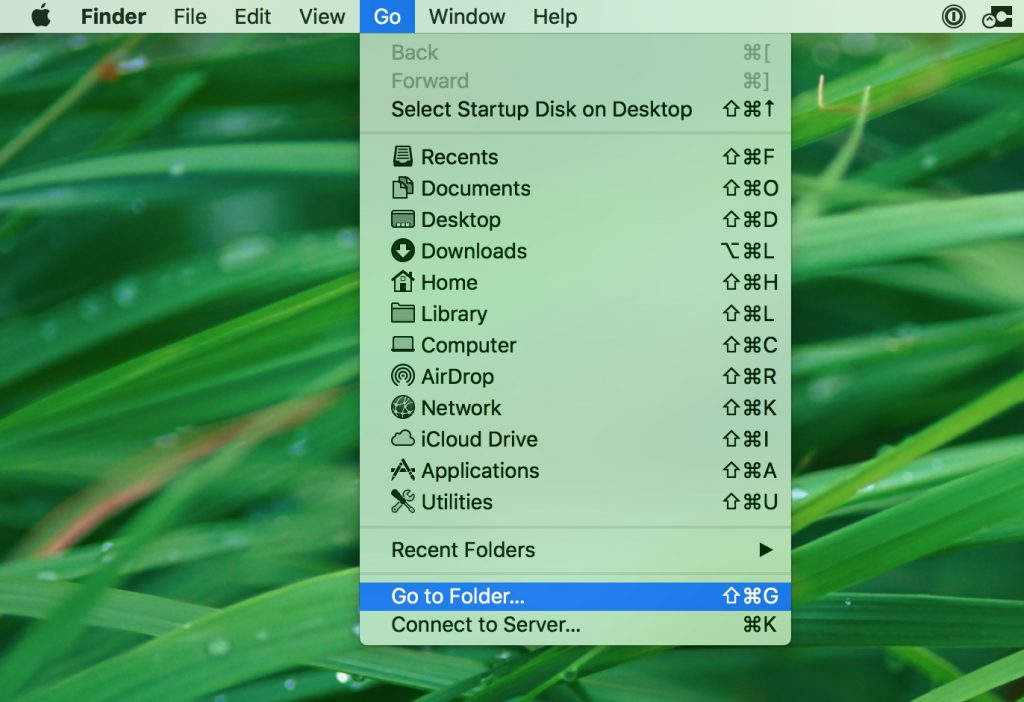
2. Type in "/Library/LauchAgents/" and click Ok:
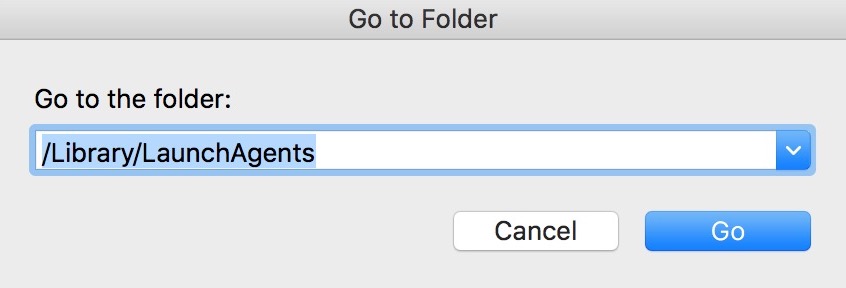
3. Delete all of the virus files that have similar or the same name as Apple ID Phishing Scam. If you believe there is no such file, do not delete anything.
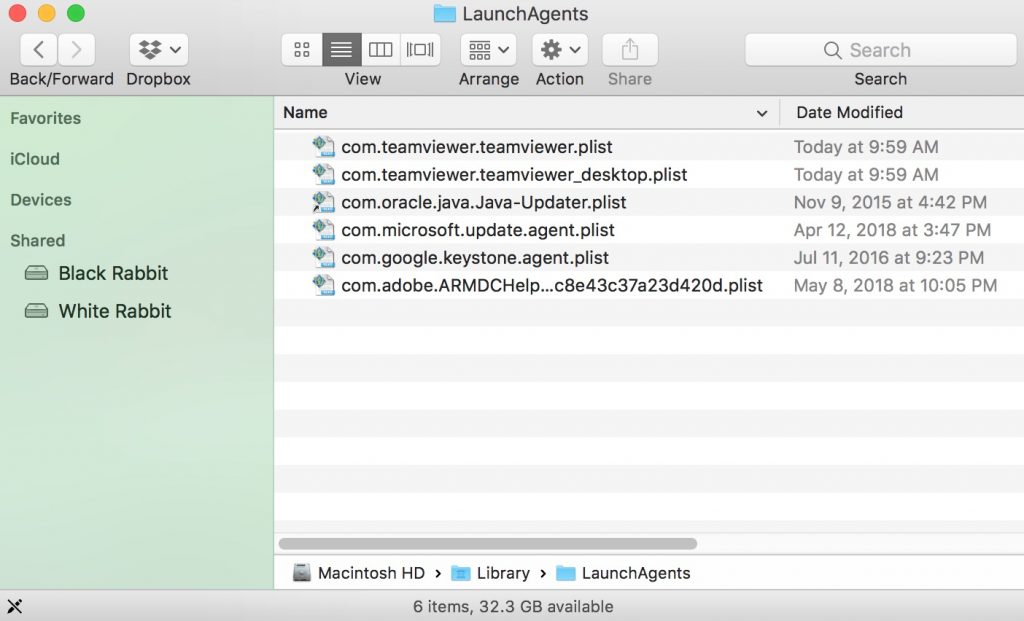
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
Step 3: Remove Apple ID Phishing Scam – related extensions from Safari / Chrome / Firefox
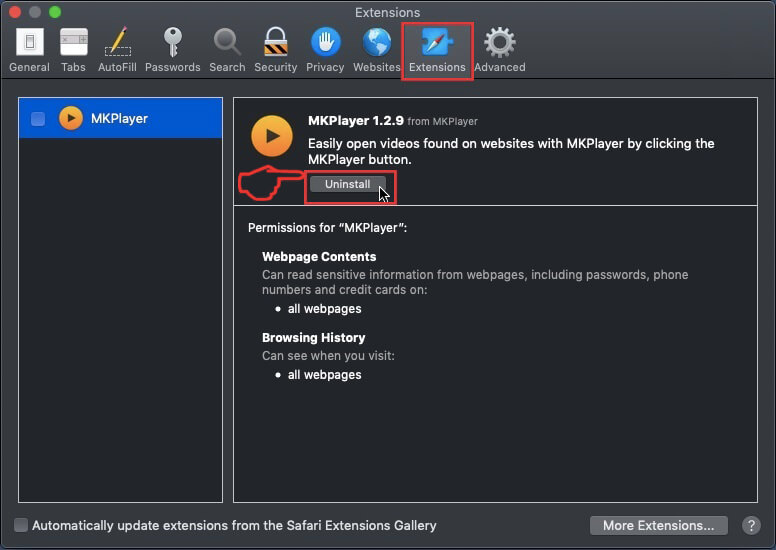
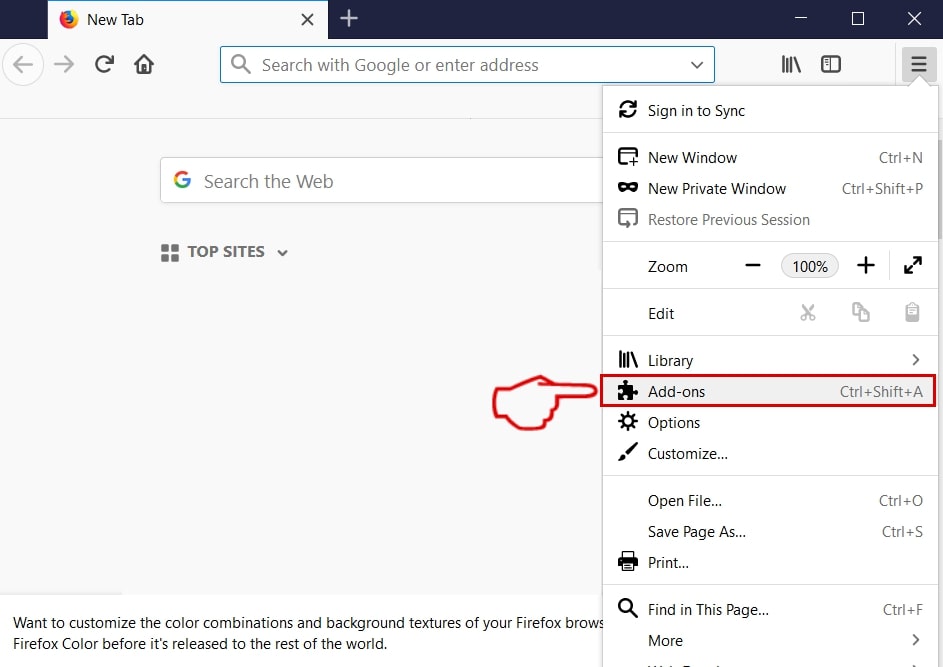
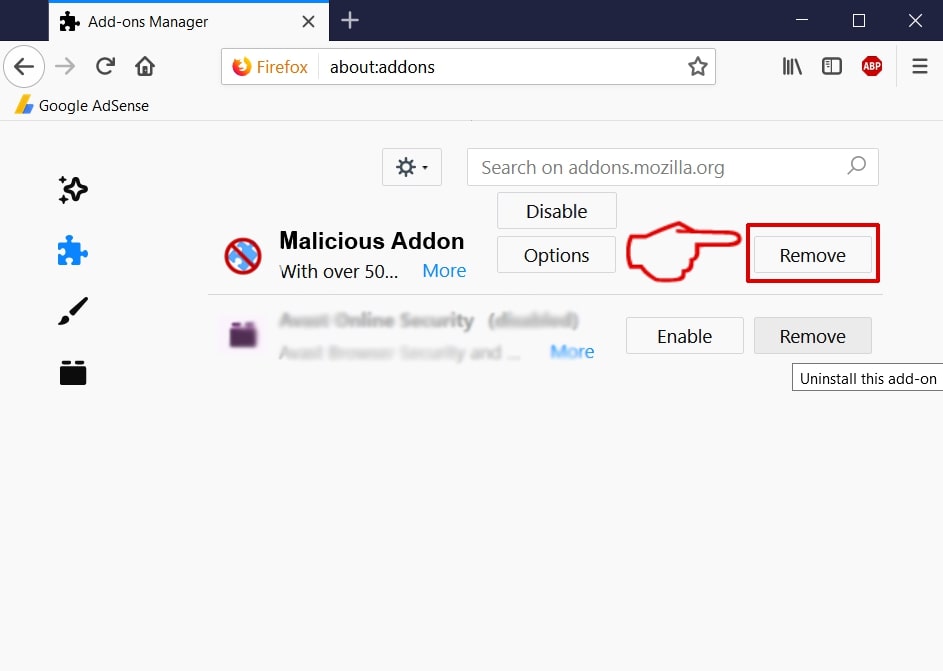
Apple ID Phishing Scam-FAQ
What is Apple ID Phishing Scam on your Mac?
The Apple ID Phishing Scam threat is probably a potentially unwanted app. There is also a chance it could be related to Mac malware. If so, such apps tend to slow your Mac down significantly and display advertisements. They could also use cookies and other trackers to obtain browsing information from the installed web browsers on your Mac.
Can Macs Get Viruses?
Yes. As much as any other device, Apple computers do get malware. Apple devices may not be a frequent target by malware authors, but rest assured that almost all of the Apple devices can become infected with a threat.
What Types of Mac Threats Are There?
According to most malware researchers and cyber-security experts, the types of threats that can currently infect your Mac can be rogue antivirus programs, adware or hijackers (PUPs), Trojan horses, ransomware and crypto-miner malware.
What To Do If I Have a Mac Virus, Like Apple ID Phishing Scam?
Do not panic! You can easily get rid of most Mac threats by firstly isolating them and then removing them. One recommended way to do that is by using a reputable malware removal software that can take care of the removal automatically for you.
There are many Mac anti-malware apps out there that you can choose from. SpyHunter for Mac is one of the reccomended Mac anti-malware apps, that can scan for free and detect any viruses. This saves time for manual removal that you would otherwise have to do.
How to Secure My Data from Apple ID Phishing Scam?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your e-mail passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activiites with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these reccomendations, your network and Apple devices will become significantly more safe against any threats or information invasive software and be virus free and protected in the future too.
More tips you can find on our MacOS Virus section, where you can also ask any questions and comment about your Mac problems.
About the Apple ID Phishing Scam Research
The content we publish on SensorsTechForum.com, this Apple ID Phishing Scam how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific macOS issue.
How did we conduct the research on Apple ID Phishing Scam?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of Mac threats, especially adware and potentially unwanted apps (PUAs).
Furthermore, the research behind the Apple ID Phishing Scam threat is backed with VirusTotal.
To better understand the threat posed by Mac malware, please refer to the following articles which provide knowledgeable details.