In 2016, ransomware has been extremely devastating for businesses, and the statistics prove it. A new report by Kaspersky Lab shows that ransomware attacks on companies tripled from January to September. This means that one in every five businesses was affected on a global scale.
Related: Most Ludicrous Ransomware in 2016
The report reveals some staggering numbers, like:
- 62 new ransomware families were introduced to the online world;
- Researchers observed an “11-fold increase in the number of ransomware modifications: from 2,900 new modifications in January/March, to 32,091 in July/September”;
- Attacks on companies also tripled between January and September;
- One in five small and medium-sized businesses paid the ransom but never restored their data;
- Attacks on individuals increased from every 20 seconds to every 10 seconds.
The high success rates of ransomware only prove that cybercriminals will not give up on this cyber threat any time soon. The high infection rates and ever-growing numbers also depict that counter-measures are not sufficient enough to prevent the threat. Ransomware continues to evolve and become more devastating despite the efforts of law enforcement agencies and security researchers working on free decryption solutions.
Nonetheless, 2016 saw the first serious and well-coordinated anti-ransomware activity: the No More Ransom project, which brought together police, Europol, Intel Security and Kaspersky Law. The good news is that 13 more organizations joined the initiative in October. Even though there is much else to do, the collaboration led to the release of several free online decryption tools that have helped thousands of victims worldwide to restore their data.
Key Ransomware Trends in 2016
Ransomware definitely grew in sophistication and diversity, and this year saw some novelties:
changing tack if it encountered financial software, written in scripting languages, exploiting new infection paths, becoming more targeted, and offering turn-key ransomware-as-a-service solutions to those with fewer skills, resources or time – all through a growing and increasingly efficient underground ecosystem.
However, the most striking finding about ransomware this year concerns the relationship between the victim and the attacker:
Most ransomware thrives on an unlikely relationship of trust between the victim and their attacker: that, once payment is received, the ransomed files will be returned. Cybercriminals have exhibited a surprising semblance of professionalism in fulfilling this promise.
In a nutshell, 2016 met three of the most feared ransomware families – Cerber, Locky and CryptXXX, as well as 44,287 new ransomware modifications. Cerber and Locky were first released in the wild in the early spring. The distribution mainly relied on spam and exploit kits. CryptoWall, CTB-Locker and Shade continued to plague individuals and corporations, too. According to security reports, Locky alone was spread in 114 countries.
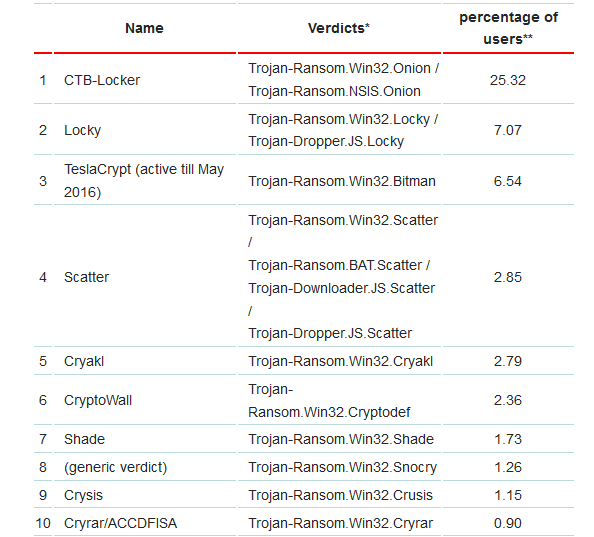
Here are the top 10 ransomware families in 2016, according to Kaspersky researchers:
The statistics above are only based on detection by Kaspersky Lab products received from users of the products. The users have consented to provide their data. This means that these numbers would be much different when combined with statistics from other security vendors.
The biggest surprise this year was the sudden disappearance of TeslaCrypt, which was triggered by the release of the master decryption key.
As for ransomware-as-a-service – it grew rapidly, with Encryptor RaaS being one of the first families to offer this business model to other criminals.
Related: 2016 Trends in Ransomware
Other notable moments in ransomware evolution this year include:
- Abuse of the “educational” Eda2 and Hidden Tear ransomware;
- Disk encryption as seen in the Petya ransomware case;
- Two-in-on infection where Shade would choose to drop spyware instead of ransomware if the victim’s system belonged to financial services.
- A line of copycat ransomware cases imitating Locky and Cerber.
Ransomware Protection in 2016
It’s the same as any other year. The single most important thing to do to avoid spending irrationally on ransomware is regular data backups.
A ransomware or any other malware attack should have an educational purpose, if nothing else. A successful attack should increase the user’s paranoia and should also make them a tad more careful with online activities of all types. The importance of regular data backups and appropriate data hygiene is bigger than ever.
As for companies, there are other activities to consider in addition to data backups:
- GPO restrictions – a great way to restrict not only ransomware, but malware of all kinds. “GPO has the ability to provide granular control over the execution of files on an endpoint, so adding rules that block activity such as files executing from the ‘Appdata’ directory or even disabling the ability for executables to run from attachments.”
- Software patches – Patching commonly exploited software like Java, Flash, and Adobe will surely prevent many malware and ransomware from infecting systems.
- Administrative rights restriction – Reducing privileges will reduce the attack surface significantly, Digital Guardian says. Plus, a 2016 survey proved that privileged users are the riskiest in an organization.
Lastly, anti-malware software, in combination with anti-ransomware protection should be present on any system.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter