
Unsecured wi-fi networks have proven to be a gateway to many attacks. More particularly, poorly configured access point encryption (or services that allow data to be sent without being encrypted) has been outlined as one of the biggest threats to users.
To illustrate the risks stemming from unencrypted traffic at wireless access points, Kaspersky researchers have conducted a research that answers questions like, what actually happens in practice? Is traffic always encrypted on public Wi-Fi networks? How does the situation differ from country to country?
What Kaspersky did was compare the situation with wi-fi traffic in different countries via data from their threat database. They also counted the number of both reliable and unreliable networks in these countries. It’s important to note that the countries they based the research on have more than ten thousand access points.
Related Story: Which Is the Most Hackable Country?
The team analyzed statistics from Kaspersky Security Network (KSN) and went through nearly 32 million Wi-Fi hotspots accessed by the wireless adapters of KSN users.
The Findings, Based on Kaspersky’s Threat Database
Apparently, 24.7% of world-wide Wi-Fi hotspots don’t employ any encryption at all.
“This basically means that by using an antenna capable of sending and receiving data at 2.4 GHz, any individual located near an access point can easily intercept and store all user traffic and then browse it for data they are interested in. Fortunately, modern online banking systems and messengers do not transfer unencrypted data,” the report said.
Furthermore, researchers explained that the WEP (Wired Equivalent Privacy) protocol for encryption of data transmitted over Wi-Fi signal is employed by 3.1 per cent of the analyzed access points. Unfortunately, this protocol was created a long time ago and is now outdated and unreliable. Malicious hackers only need a couple of minutes to break it.
“From a data security point of view, using WEP is not much different from using open networks. This protocol is being relegated to oblivion everywhere, but as we see from the chart above, it can still be found in use,” the added.
The research unveiled that about three-quarters of all access points used encryption based on the WPA (Wi-Fi Protected Access) protocol family. These protocols are considered to be the most secure, at least for now. A successful WPA hack would depend on the its settings and the complexity of the password set by the hotspot owner.
“It is worth noting that an attempt to decipher traffic from “personal” (WPA-Personal, PSK authentication) wireless networks (with public access points) can be made by intercepting the handshakes between the access point and the device at the beginning of the session. “Corporate” versions are protected from this sort of interception because they use internal company authorization.”
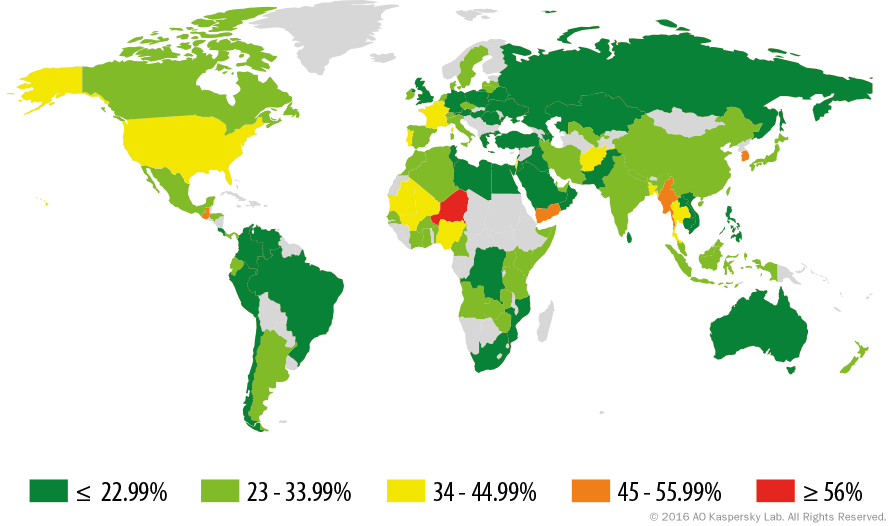
Which Countries Have the Most Unsecured Wi-Fi Access Points?
Korea has 47.9% of unsecured Wi-Fi access points and ranks in the first five countries. France (40.14%) and the US (39.31%) rate 9th and 12th in this list.
Kaspersky’s research shows that Germany is the most secure country in Western Europe, with 84.91% of access points secured via WPA/WPA2 protocol encryption.
What Are the Risks of Using Public Wi-Fi Networks?
Or what type of cyberattacks could happen over an unsecured wi-fi network?
Man-in-the-Middle Attacks
This type of attack would allow threat actors to capture users’ traffic, as they will be “situated” between users and the server. Once this is done, hackers can steal sensitive information, including banking and credit information, and they can even manipulate data packages.
Network Snooping
In fact, network snooping is a type of a man-in-the-middle attack. It involves monitoring the incoming and outgoing traffic on a public network with malicious intent in mind. Unfortunately, network snooping can be done pretty easily. Tools that enable this type of attack, such as Wireshark, are available online, as well as tutorials on how to pull off such an attack.
Malware Injection
Not surprisingly, it is also possible to deliver malware over unsecured wi-fi networks. If threat actors use some snooping tools to inspect the traffic and the data over it, they can definitely intercept it and drop malware on users’ devices. The malware injection type of attack involves intercepting a web server’s response before it reaches the user’s endpoint, and inserting malicious code on targeted pages that users will open. This type of attack is quite covert, and if done professionally, you won’t even notice that something is wrong.
What Can Users Do to Protect Their Personal Data When Using Public Wi-Fi Networks?
Security researchers advise the following:
- Users shouldn’t trust networks that are not password-protected.
- Even if a network requests a password, users should remain cautious. It’s not difficult for attackers to obtain a public network password, and then craft a fact connection with the same password. This is done to steal personal user information.
- Users should turn off Wi-Fi connection when they are not using it. It’s also recommended to disable automatic connection to existing Wi-Fi networks.
- If you don’t have a choice but to connect to a dubious network, users should limit their actions to only searching information. Entering login credentials is very dangerous, under these specific circumstances.
- Users should also consider enabling the “Always use a secure connection” or HTTPS in their devices’ settings.
- Connecting via a VPN is also considered a good option. This way attackers wouldn’t be able to read users’ data even when access to it is obtained.
- Last but not least important is the employment of security solutions on mobile devices.




El VPN es la mejor solucion..