A new dangerous hacker tactic has been identified as the ZeroFont phishing attack which is responsible for infections caused by Office 365 manipulation. This is done by using social engineering tactics that manipulate the users into interacting with attached documents containing zero-size fonts. This technique has proved successful and is being leveraged in an ongoing attack against targets worldwide.
ZeroFont Phishing Attack Leverages Office 365 against Users
The security researchers that revealed information on the ZeroFont phishing attack showcased that the main delivery method are direct messages that have been able to fool several anti-SPAM filters. Recipients receive email messages that look like legitimate notifications from popular services. The hackers use text and graphics taken and design the emails using the same methods. The phishing attack is marked unique as it uses an entirely new way of scamming people into interacting with the dangerous elements. According to the researchers one of the key characteristics is the use of Office 365 as the cloud service. The following steps are made by the hacker operators behind the campaign:
- The criminals look orchestrate the campaign against Office 365 email users. They may profile them using harvested information or work together with groups that have their personal information in order to create personalized mesages.
- The messages are sent to Office 365 servers and bypass Microsoft’s algorithms by using a natural language processing bypass.
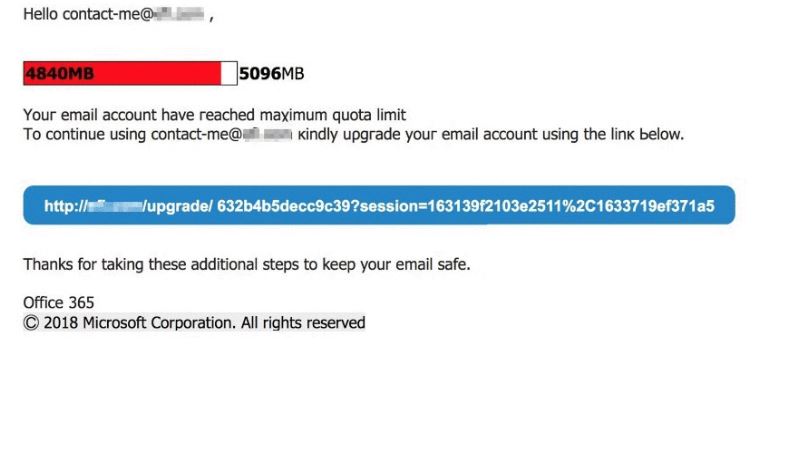
- The users receive messages in their Inbox that appear as standard security notifications.
The most concerning fact is that the hackers have been able to discover a way to go around Microsoft’s SPAM filters. This is done by emulating the design elements of real legitimate messages such as the watermarks, copyright notices and etc. The messages are constructed so that they can correlate with the sender and recipients, as well as fit into contexts that can present a real customer or service issue. The captured samples appear to impersonate 365 quota limit notifications.
The reason why the attacks are called “ZeroFont” is due to a novel technique that utilizes zero-size font content. Random text strings are inserted into the messages and programmed with a font size 0, this is interpreted by the email servers and the graphical user interfaces in the correct way. These text strings are not visible to the users. At the same time the algorithm reads the hidden text and flags it as safe content that is delivered to the recipients.
Consequences of The ZeroFont Phishing Attack: Beyond Office 365
The ZeroFont phishing attack represents the latest novel approach that hackers are taking in delivering counterfeit messages to their prescribed targets. A weakness has been found in Microsoft’s algorithm that handles natural language processing through font size modification of random letters. Public disclosures about such high-impact vulnerabilities are posted by security researchers after the company has addressed the issue.
Use of this technique can be directed against other email hosting services and cloud software. The criminal groups can use it for malicious actions such as the following:
- Ransomware Deployment — The hackers can send viruses through emails by either attaching them directly as files or hyperlinking them in the body contents.
- Malware Redirect — Such email messages can be used to redirect the victims to hacker-controlled sites.
- SPAM Messages — By overcoming the associated SPAM filters companies, hackers and other interested parties can deliver personalized and non-personalized messages for advertisement purposes.
At this point there is no information about the number of affected files nor the hackers that are leveraging the ZeroFont phishing attack.


