 This article has been created in order to help you by explaining to you how to remove the popular 2021 phishing scams which can be encountered via email messages.
This article has been created in order to help you by explaining to you how to remove the popular 2021 phishing scams which can be encountered via email messages.
Our 2021 Phishing scams guide reveals all popular phishing attempts that have been reported against individual services. We reveal some of the top trending schemes that can both extract sensitive information from the victims or hijack their money — both real currency and cryptocurrency. Continue reading to learn how to protect yourself.

Threat Summary
| Name | Phishing Scam |
| Type | Scam |
| Short Description | Computer hackers in 2021 continue to rely on phishing scams to manipulate victims into giving out sensitive information. Such crimes are linked with blackmail, financial abuse, and manipulation, and can take different forms. |
| Symptoms | Receiving familiar-looking email messages, accessing strange websites, abnormal browser behavior. |
| Distribution Method | Email messages, instant messaging notifications, in-browser popups |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss Phishing Scam. |
2021 Phishing Scams Trends
Expert analysis from multiple sources, as well as our own analysis, shows that in 2021 phishing campaigns are going to be on the rise. As a result of the global COVID-19 pandemic computer criminals will send out fake ad offerings via email messages. Due to the job losses many citizens search for jobs and to the criminals, this presents a great opportunity to create new campaigns.
Phishing messages are created alongside specially-created websites that are hosted on domain names that sound similar to the services and companies that are represented. Adding this the phishing messages can be one of the following:
- Fake Job Offers
- Fake Covid-19 Vaccines
- Fake Notifications
The other type of phishing content that is prepared by the hackers is a notification designed to present vaccine schedules, offers, and information. Scams in 2021 that are related to these areas can also use other types of web content types: social media, classified portals, dating sites, and etc.
These phishing messages all aim to collect personal information about the users, which can be used for various crimes such as blackmail and financial abuse.
Over the last few years the computer criminals have also started to rely heavily on instant messaging clients together with social media sites and applications. The familiar tactic of social manipulation is done by the criminals — they use fake identities, hijacked content, and false images to coerce the victims into opening links. With the COVID-19 vaccines and fake job offers the victims will be manipulated into giving up their information through them.

2021 Phishing Scams — Overview and Main Distribution Methods
All popular 2021 phishing scams are deployed via email messages as the main distribution tactic. The victim recipients will be sent messages that are disguised as legitimate notifications from a service, program, product, or another party that a certain type of interaction is required. Most of the time the scams are related to account activity, fraud transactions or password reset reminders. All of these are legitimate reasons for sending out activity messages and as such can easily be confused with the real notifications. In almost all cases similar sounding domain names and security certificates (self-signed, stolen, or hacker-issued) will be implemented in the landing pages to confuse the recipients that they are visiting a safe site. Furthermore, the legitimate design layout, elements, and text contents can be copied from legitimate sites.
Construction and maintenance of fake web sites can additionally lead to the delivery of phishing messages. They are the second-stage delivery mechanisms as the email messages link to them. In many cases, they can are placed stand-alone by the hackers by simply using a single letter change from the domain name of the desired spoofed service. Every time a computer user unknowingly mistypes the address they will be redirected to the fake address.
An alternative to these two methods is the reliance on social media profiles — they can be either stolen, hacked, or hacker-made. Usually, hundreds and thousands of profiles will generate predefined posts, private messages, and profile information with the phishing scam links. To coordinate these attack waves the criminals usually acquire botnets of infected computers and databases of hacked user account credentials. Using automated tools and scripts they carry out the necessary scam delivery.
Phishing scams, especially some of the most popular examples, may also be redirected from browser hijackers which are dangerous plugins made for the most popular web browsers. They can be found uploaded to the relevant repositories with fake user reviews and developer credentials offering enhancements such as feature additions and performance optimizations. Their main goal is to redirect the victims to the phishing landing page in this particular case. Usual modifications include the default home page, new tabs page, and search engine.
Various infected payload carriers may also be hosts of the phishing scams. Two popular examples are the following:
- Malicious Documents — The criminals can embed the necessary scripts that will redirect the users to the phishing scam in documents across all popular file formats: rich text documents, text files, presentations and databases. Links to the pages can be placed in the multimedia or interactive contents or automatically opened when the files are opened. In certain cases, the documents may spawn a notification prompt requesting that the built-in scripts are run in order to “correctly view” the document or to enable the embedded functionality. If this is allowed the redirect code will be triggered.
- Software Installers — The redirect installation code can also be embedded application installers of popular software. Usually, software that is often downloaded by end-users is chosen: creativity suites, system utilities, productivity, and office apps and etc. As soon as the installer is started or the installation process has finished a browser window or an in-app tab will be opened with the phishing landing page. The installers can be programmed to continue running only until the relevant user interaction has been recorded.
Already existing malware infections may additionally trigger the phishing landing page display. This is usually the case with Trojan horse clients. They will set up a secure and constant connection to a hacker-controlled server and allow the operators to spy on the victims, overtake control of their computers and also hijack information. As soon as control of the machines has been acquired the hackers can automatically open the browser window or when certain events are called by the victim users.
Hacked web pages of services, download portals, news sites, and other commonly visited areas will mostly display phishing landing pages or lead to virus infections. Phishing attacks can also be done via commonly used services, one of the best-known examples is the BaseCamp October 2020 attack. It was a devastating blow against this online collaboration platform, as the phishing attack has also lead to Trojan and Ransomware virus infections.
Not many users actually don’t know what to do when they encounter a phishing scam link. The best advice that we can give is to follow these steps:
- Blacklist –Put the phishing site’s blacklist in your security software (antivirus and/or firewall), so that it cannot be accessed either directly or through any redirects and links.
- Prevent — In many cases when the phishing site, form, redirect, toolbar, or other form is accessed it provides information about the party behind it. This can help out to filter out other similar threats.
- Report — Scams can be reported to security software vendors, or alternatively, to Government agencies. Steps that American citizens can make are found on a special page.
2021 Phishing Scams #1 — Apple Payment Scam
Apple-related scams are among the most widely distributed in 2019, 2020, and 2021 which is seen as a continuation of the 2018 campaigns that were set against Apple ID users. At the start of this year, we have received several reports of phishing tactics that attempt to coerce the victims into believing that they have received a legitimate message from the company. The medium of choice is once again email messages that are designed to appear as being sent by the company’s servers.
Unlike most other Apple scams the captured messages do not seem to copy the distinct text layout and elements of the real notifications. Nor in any case they are designed as particularly believable, there are several ways that the fake messages can be distinguished from the real Apple notifications:
- Source Addresses — The senders of the messages do not come from the official Apple site.
- Non-Apple Design — The text layout and body contents do not correspond to the way Apple notifications are made.
- Attached Documents — Apple will not send out documents related to account activity and especially in the .DOCX format.
The Apple payment scam can potentially affect thousands of users as many Apple users make online transactions through the company’s services. A security or privacy incident can lead to concerns surrounding the use of such services. This allows for social engineering tactics like this to take place.
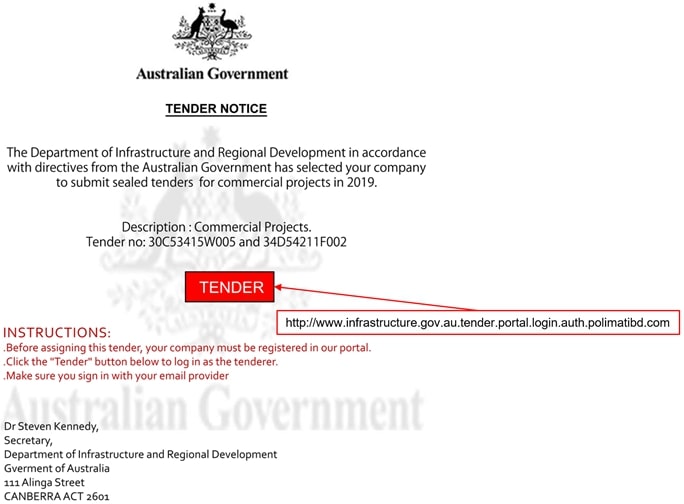
2021 Phishing Scams #2 — Australian Government Contractors Phishing Scam
A dangerous phishing scam was detected on January 9 2019 when a security company found out about the active campaigns. According to the released reports, a criminal collective has spoofed email messages that are designed to appear as being sent by the Australian Government. The recipients are tenders for commercial projects and the end goal of the phishing attempt is to extract personal information pertaining to them or to the projects that they are working on. The way this is done is by impersonating a department invitation to bid to sealed tenders.
The option that is given to the recipients is to open an attached document called Australia Tender Invitation.pdf. The file contains a “Tender” button which redirects the recipients to an online landing page. When it is opened the users will see a copycat scam page that mimics the legitimate Department of Regional Development, and Cities registration page. The accompanying site will request personal information and account credentials from the victim visitors.
The security company has issued a list of guidelines that can reduce the risk of Tender-related messages:
- Organizations and companies should instruct their employees into spotting out suspicious emails. Larger establishments should invest in a cyber security awareness training programs.
- Opening up suspicious and unsolicited emails that contain links and attachments should be disregarded as potentially dangerous. Cyber security staff should be alarmed before any interaction is actioned.
- Looking out for all warning signs of phishing emails should be mandatory: poor grammar, spelling and punctuation. A generic reference such as “Dear Sir/Madam”, “Client”, “Customer” and etc .should be disregarded as legitimate messages will mostly address the person with their full name and relationship (client, partner, customer and etc.) listed with them.
- Larger organizations should invest in email authentication standards implementation and deploy the required filtering services.
- Advanced hacker attack campaigns can make use of the digital footprint available online. Harvested information from the Internet can be used to design personalized messages that can hardly be distinguished from the legitimate notifications.
- Double check that the senders of a suspicious message are indeed those who they claim to be. If possible verify by other means and alert system and/or network administrators.
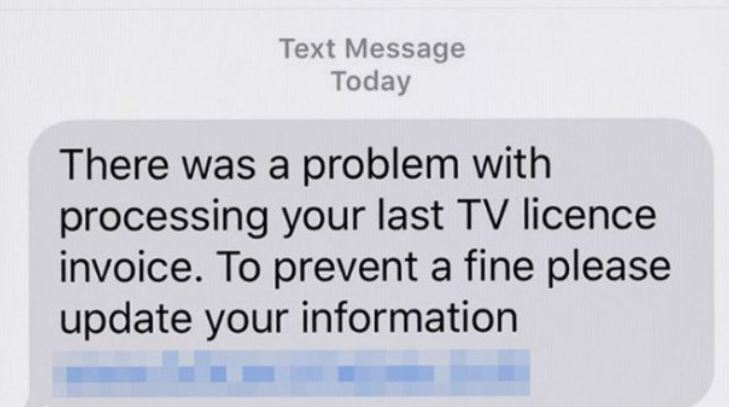
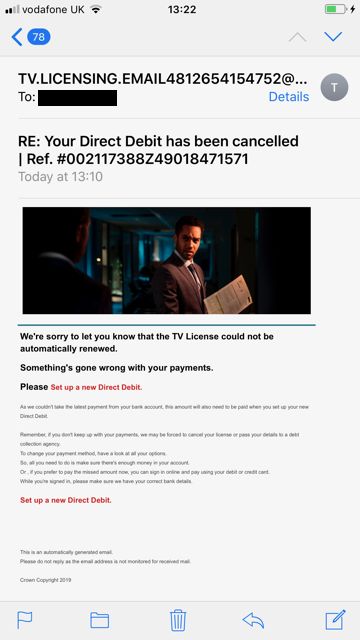
2021 Phishing Scams #3 — TV License Phishing Scam Offers
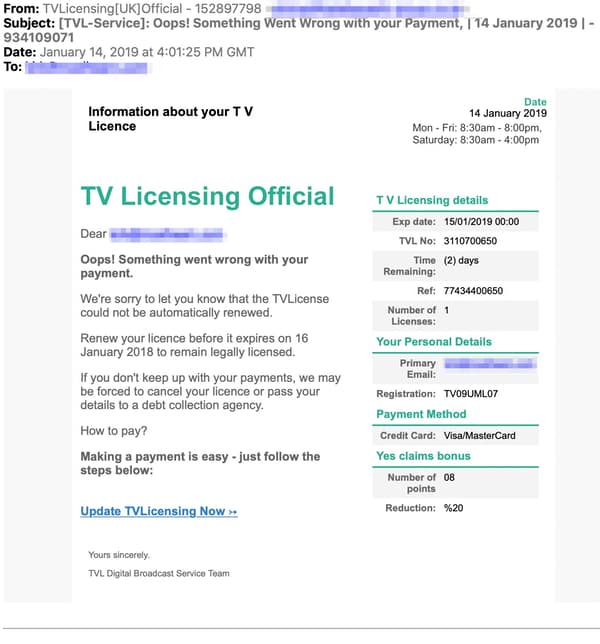
Several criminal collectives have been found to target Internet users en-masse with tv licensing renewal and subscription prompts. Two are the main methods of distribution of the relevant messages — email notifications and SMS messages. In most cases, the data about the victims is hijacked from the underground hacker markets and is based on identity theft. The criminals who are overseeing the campaign can personalize the messages and make them indistinguishable from possible legitimate messages. The only elements that can show the warning signs are the domain name and embedded elements that are not found with the relevant service. The official TV Licensing website has posted numerous notifications about the scam tactics, an investigation has been started that aims to reduce the risks by eliminating the hacker collectives.
One of the disturbing characteristics is that the criminal collective has been able to harvest the mobile phone numbers of the recipients. The SMS messages that are sent out have a high chance of being actioned upon by the targets. They will state that a problem has been identified in the processing of their last TV license invoice. A link will be offered to update their information — the accompanying warning will list that this is required in order to avoid a fine.
Whatever the method of distribution the landing page that is displayed will request personal information about the users and their payment card details. The fraud site requests full information about the purposed of payment: full cardholder’s name, phone number, card number, verification code, expiration date, and etc. Using the harvested information the criminals can carry out both identity theft and financial abuse crimes.
The TV Licensing site has posted tips on preventing phishing attacks in this particular case. They specifically state that the service will never email victims asking for personal information, bank details, or direct payment data. Email messages sent by the official service will always include the full name of the recipients. The email subject lines can be used to scan for any of the typical ones used in attack campaigns: “Action required”, “Security Alert”, “System Upgrade”, “There is a secure message waiting for you” and others. The email addresses from which the warnings are sent should also match with the official domain.
2021 Phishing Scams #4 — DocuSign Phishing Scam
A large-scale DocuSign phishing campaign has been reported both by victims and the company itself. According to the released reports and notifications, there are several hacking collectives that are orchestrating such attacks. There are two main types of the scam:
- Malicious Site — Scam landing pages are the most common signs of such hacking tactics. They will not be hosted on the official domain and fake or stolen security certificates will be added. Usually, the links to the fake sites will be found in browser hijackers, malicious portals, email messages, or redirects using short URL services. The destination addresses of these fake sites will direct the users to a landing page that will scam them into thinking that they have accessed a legitimate portal page owned by DocuSign. Interaction with any of them can also install spyware on the victim systems — Trojans, miners, and ransomware. The dangerous characteristic of these infections is that they can happen merely by visiting the site using the built-in scripts.
- Email Message — The fake email messages will include a sender that does not originate from the DocuSign service. Many of the scam messages will contain attached PDF files — the service specifically states that such documents are sent only after both parties have signed it digitally. Other warning signs of the scam messages include generic greetings that and using words that will psychologically coerce the recipients into carrying out certain actions. Any use of pop-ups is a sure sign that the message is not legitimate. Example scam email subject lines include the following: “You received / got invoice from DocuSign Signature Service / DocuSign Electronic Signature Service / DocuSign Service”.
One of the newer waves of DocuSign related phishing pages uses another approach — it shows a DocuSign-branded portal page with links to popular services: Gmail, Outlook, Office 365, Yahoo!, AOL, and “Others” stating that the contents of these services have been encrypted by the service. In order for the users to “unlock” or “decrypt” the files, they will be led to a login page requesting their account credentials. If they are provided the criminals will instantly receive the information allowing them to carry out both financial abuse and identity theft crimes.
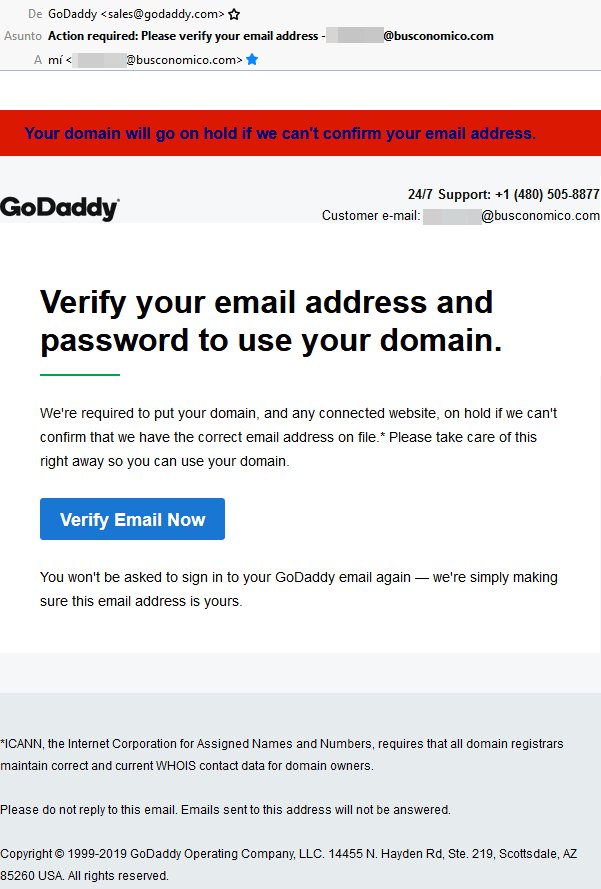
2021 Phishing Scams #5 — GoDaddy Email Verification Phishing Messages
Several user reports indicate that a new GoDaddy-themed campaign is underway by sending out email messages that pose as being sent by the hosting company. They will copy to a large extent the layout and contents of real notifications and instruct the victims into verifying their email addresses by clicking on a link button. This will most likely redirect them to a login page requesting their credentials. If this is done then the information will directly be transmitted to the hacker operators, consequently, they will be able to hijack the GoDaddy accounts. The hosting plans are usually ordered through sign-up pages, as an effect of these various crimes can be undertaken — identity theft and financial abuse.
Clicking on the links can also lead to other dangerous consequences:
- Malicious Redirects — Following the account theft operations the GoDaddy scam page can redirect the victims to other dangerous web pages. Examples include portals that distribute viruses or ad sites that contain intrusive banners, pop-ups and miners.
- Analytics Gathering — The sent emails can contain scripts that will track the users engagement giving further information about their habits to the hacker operators. This can be used to optimize the future attacks.
- Payload Delivery — As soon as the email message is loaded or the accompanying site is visited other threats can be deployed to the victims as well. They range from file-encrypting ransomware to Trojan horse infections that allow the operators to take over control of the victim machines at any given time.
If the first wave of GoDaddy phishing emails prove successful and are able to hijack user accounts then the criminals behind it may choose to launch improved versions. Typically such attacks are targeted against certain types of users or set against a certain time period.
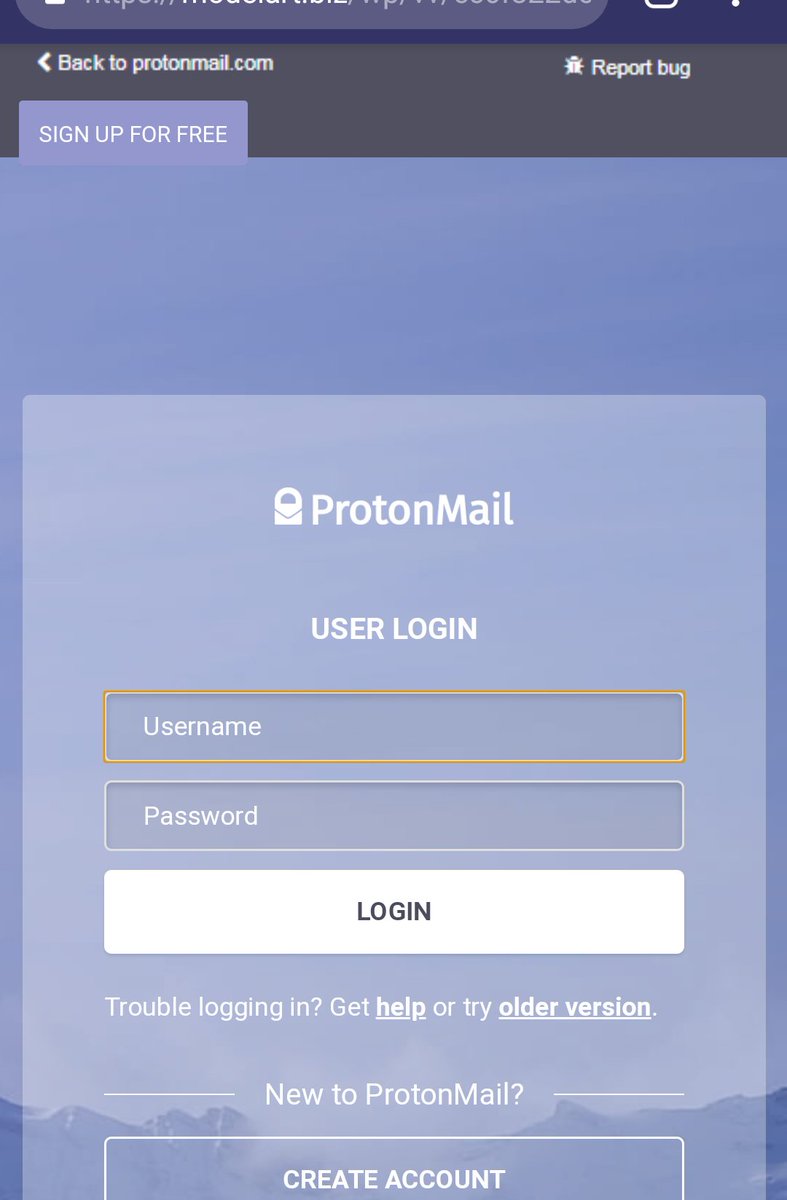
2021 Phishing Scams #6 — ProtonMail Login Pages Scams
Recently many users reported being redirected to a fake ProtonMaiil landing pages. They are made to copy the design of the legitimate email service and coerce the victims into entering in their details. The ends goal of the criminal collective behind it is to acquire as many user accounts as possible. Most of these phishing scams are done in order to access the private email inboxes of the victims, however there are other cases where such data can be used:
- Identity Theft — The ProtonMail service is widely used to hide the identity of the people subscribed to it. As such access to their private messages can be used for identification of their personal information. The obtained data can be used for blackmail purposes.
- Sale of Data — The obtained information can be recorded in databases which are then sold on the underground markets.
- Malware Distribution — The accessed inboxes can be setup to send out malicious samples of all kinds.
There are many sources of the ProtonMail phishing scams, the most common ones include website redirects, malware pop-ups and banners, and email messages. The emails are sent in a bulk-like manner and coerce the victims into interacting with the built-in content. They may copy the design of legitimate notifications which makes it harder to distinguish the real from the fake ones.
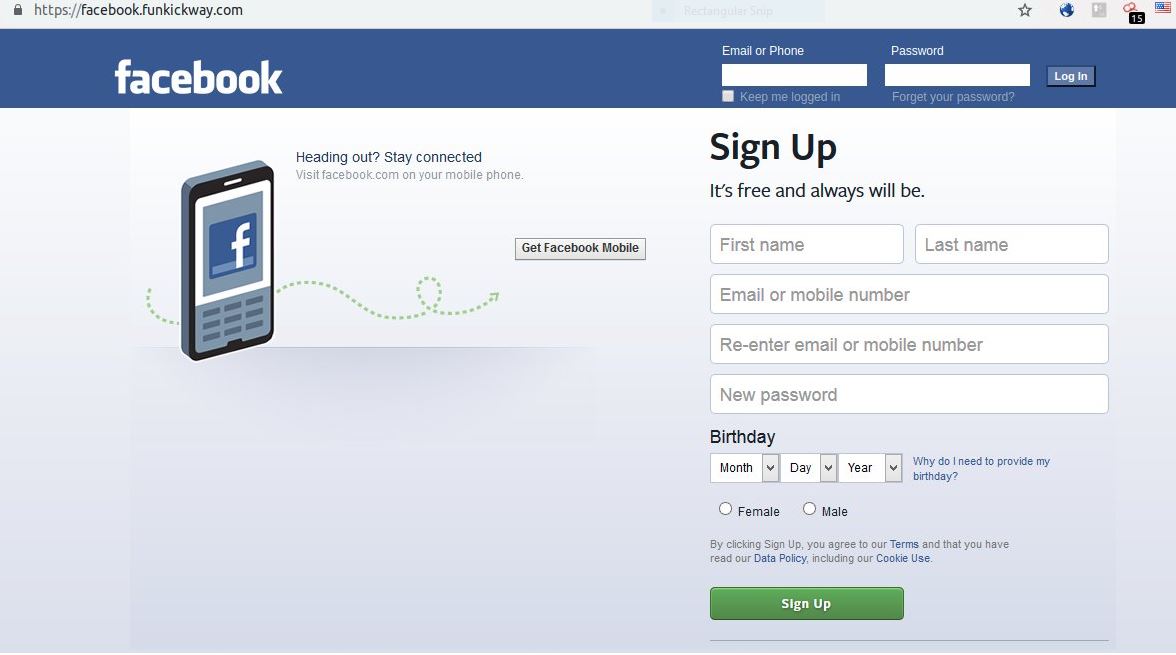
2021 Phishing Scams #7 — Fake Facebook Login Pages
In early February 2019, there have been several reports of fake Facebook login pages that are widely distributed using the popular methods mentioned earlier. This is a typical case of a copycat scam site that has taken the original design and layout of the social network and is attempting to deceive the visitors that they are accessing Facebook. Links to such services are usually embedded in phishing email messages that may appear as being sent by the popular service. Instead of leading the users to the legitimate login page, they will be shown the copycat address. The visitors can tell the difference only from their domain name.
Experts from Myki have uncovered a technique used by computer criminals that reproduce the Facebook login page in a very realistic way. This is done by constructing an HTML block in which all elements look exactly like the legitimate prompt: status bar, navigation bar, content, and shadows. These prompts are placed in hacker-controlled sites or spread through malicious search engines and portals. The pages will spawn the login attempts — usually, these are the common buttons called “log in with Facebook” which will open a pop-up asking for the social network credentials.
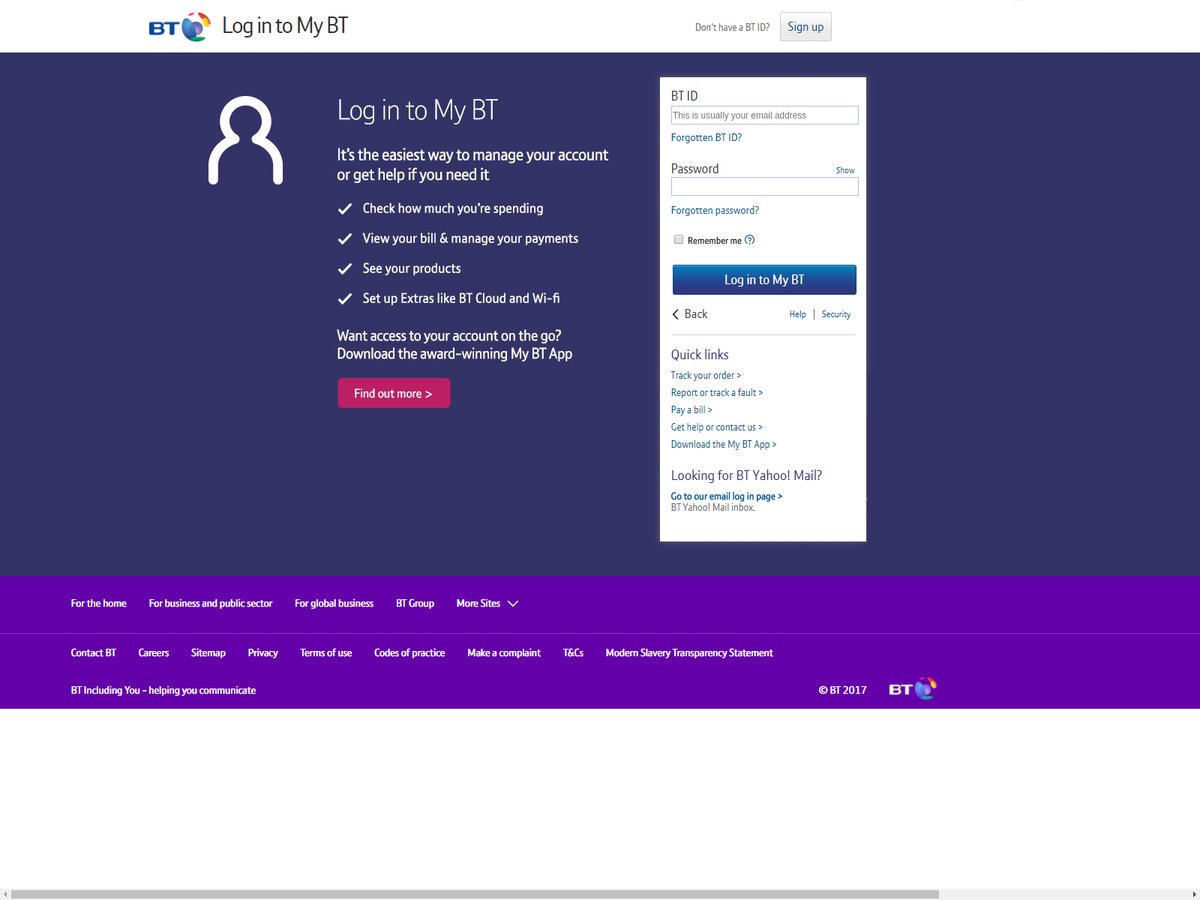
2021 Phishing Scams #8 — Fake BT Login Pages
An attack campaign carrying fake BT login pages has been reported to us recently. The tactic is to make the visitors believe that they are accessing the legitimate BT service. Successful attempts at infecting targets en-masse include both the traditional email phishing scams and links sending via social networks. This is done via hacker-made or hacked accounts that will post links to the malicious site. In most cases they will be offers or “account change information” — to the victim users will be explained that they will need to login to their profiles and “verify” their identity.
The other strategy that is used in this context is the “special offers” one. Through the hacker-created profiles, email messages and other communication channels the victims will be promised exclusive deals if they log in to their account through the fake login page.
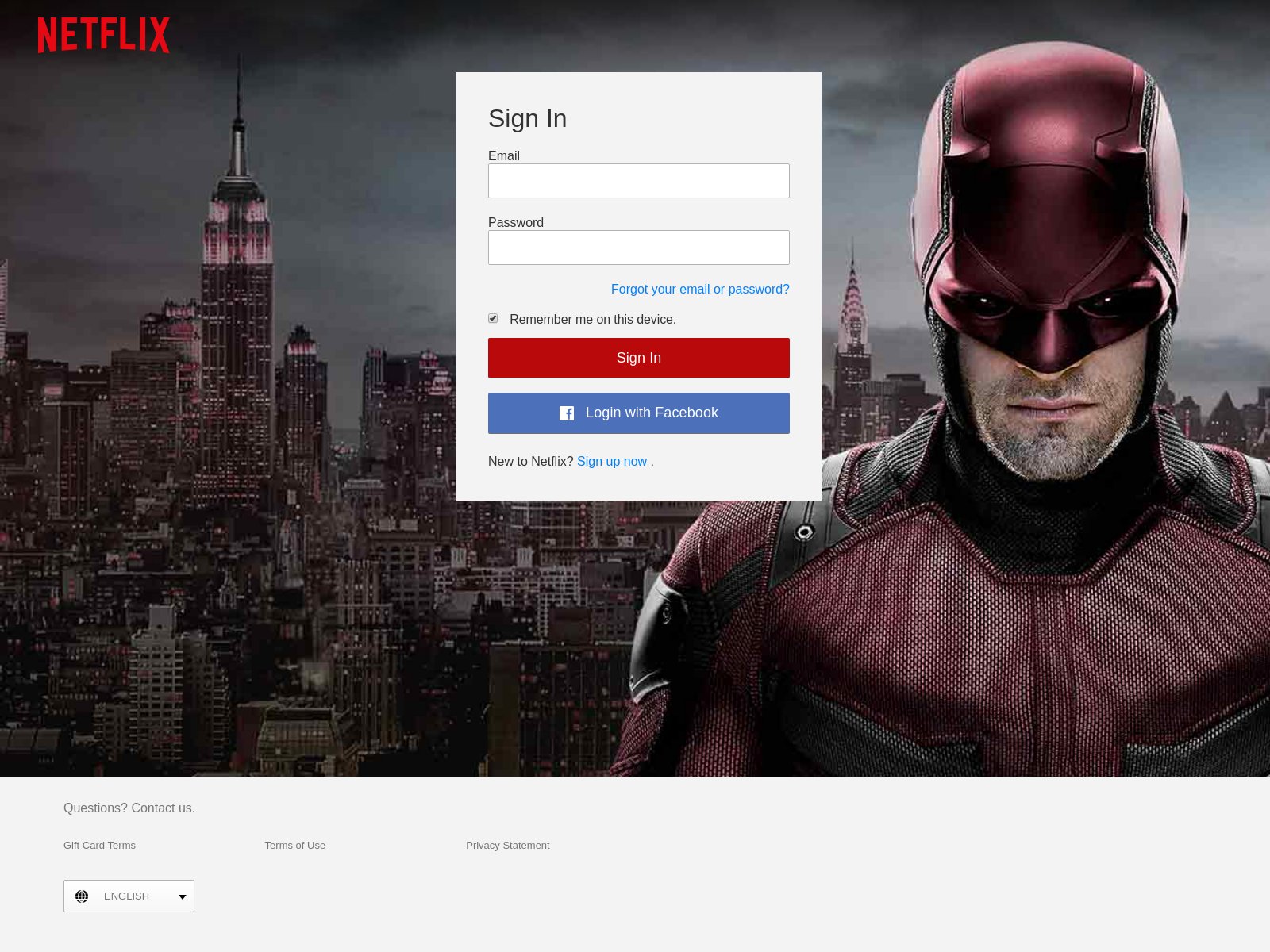
2021 Phishing Scams #9 — Fake Netflix Login Pages
One of the most popular approaches to scamming victims is to send out bulk email messages via email messages that will lead to the fake Netflix login screens. The goal of the hackers is to coerce the victims into entering their account credentials via the login form. They are hosted on similar-sounding domain names, utilizing security certificates, and copying the body contents and design.
There are many alternative forms which can all be launched at the same time:
- Search Engine Placement — The malicious sites can be designed with search engine optimization in mind. They can rank high among the search results thus confusing the victims that they are accessing the legitimate site.
- Social Network Posts and Messages — Using hacker-made or stolen account credentials the collective behind the Netflix phishing scams can constrct various forms of campaigns on these networks. A popular variant is the posting of special “offers” and “deals” — the victims will be told that they have to enter in their login credentials.
- Malicious Ads — Using hacker-controlled sites and intrusive ads (placed on relevant networks) the hackers can run campaigns that point to the dangerous sites.
All kinds of changes can be expected from the Netflix campaigns.
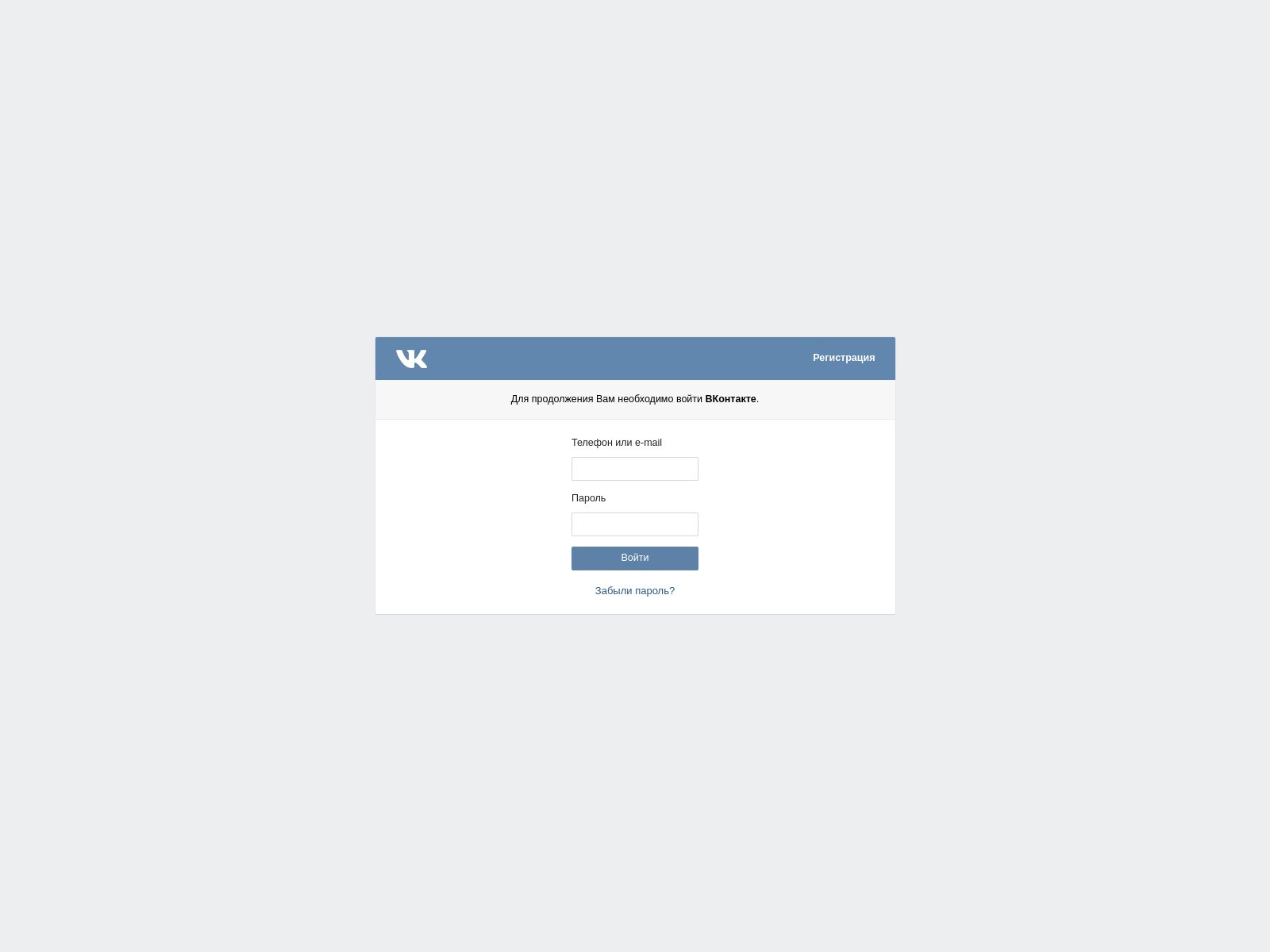
2021 Phishing Scams #10 — Fake VK (Vkontakte) Login Pages
VK is one of the most popular social networks worldwide, it is one of the most visited sites in Russian-speaking countries and is also a target for phishing scams. The reason why they are popular with criminals is that VK can be accessed both via desktop and mobile clients and also apps for most of the popular devices. As such phishing attempts can be made via a wide range of strategies. Some of them are the following
- Fake Websites — One of the most common ways is to construct fake sites that pose as the legitimate domain. They are hosted on similar-sounding domain names, include fake security certificates, and replicate the design and layout of the legitimate VK page. They can be positioned high on the search engine ranking and this factor is used to lure in victim users that may not differentiate the fake from the real address.
- Social Media Posts — The hackers can use specially made or stolen credentials that can link to the fake VK site. Usually, they are profile links, media, or special deals — all of them are created in a way that entices the targets into clicking on them.
- Ad Campaigns — The malicious VK sites can be spread via malware ad campaigns that can be found across websites displaying such content.
- Email Phishing Messages — This is one of the most popular methods — the criminals will run campaigns that imitate legitimate email notifications from well-known services or products. Whenever they interact with the fake pages will be displayed.
Other methods can be used as well, this list contains only a small sample of the possibilities for redirecting the victims to the fake VK sites.
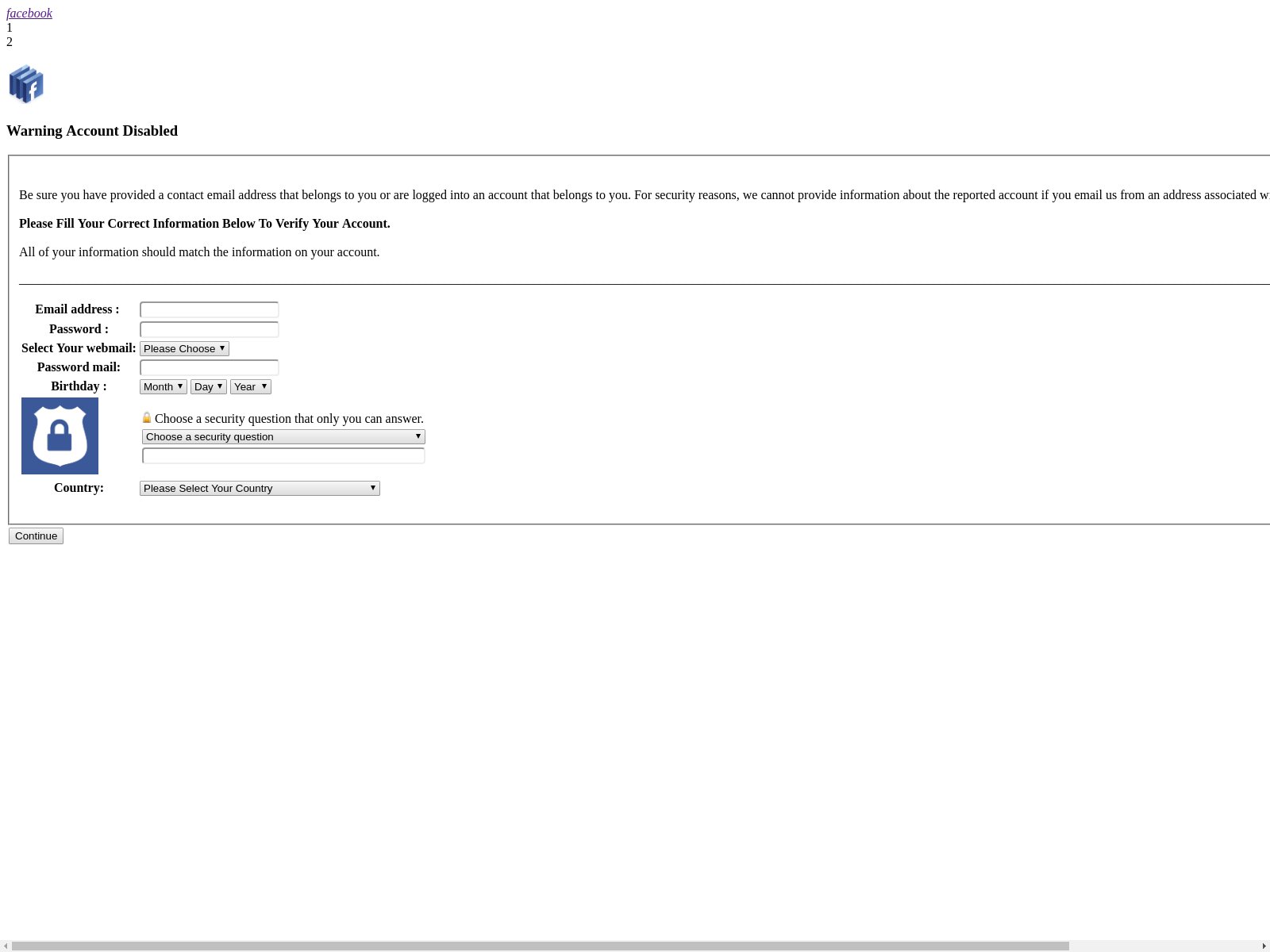
2021 Phishing Scams #11 — Facebook Warning Account Disabled Scam
In 2019 a Facebook related scam has been detected which uses malware pages that bear the title “Warning Account Disabled”. They are constructed with bland design, still containing a layout that has a similarity with the social network. This is done in order to grab the attention of the targets — they will see that there that the page may be hosted by Facebook and that they have issued a warning screen. Using the Facebook logo and the design layout which is familiar they might be enticed into entering in the requested information. The captured samples request the following data:
- Email Address
- Password
- Webmail Type
- Password Mail
- Birthday
- Security Question & Answer Combination
- Country
There are multiple ways in which this scam can be deployed to the recipients. A popular scenario is to send out links to the page via scam email messages. They appear as being sent by the social network and will coerce the victims into clicking on the link which will direct them to the phishing page.
Various malicious domains that may appear as being owned or affiliated with Facebook can be created — they will feature links, security certificates, and elements thus appearing as being part of the social network. Various posts, pages, users, and other in-Facebook content can also be created to spread the site.
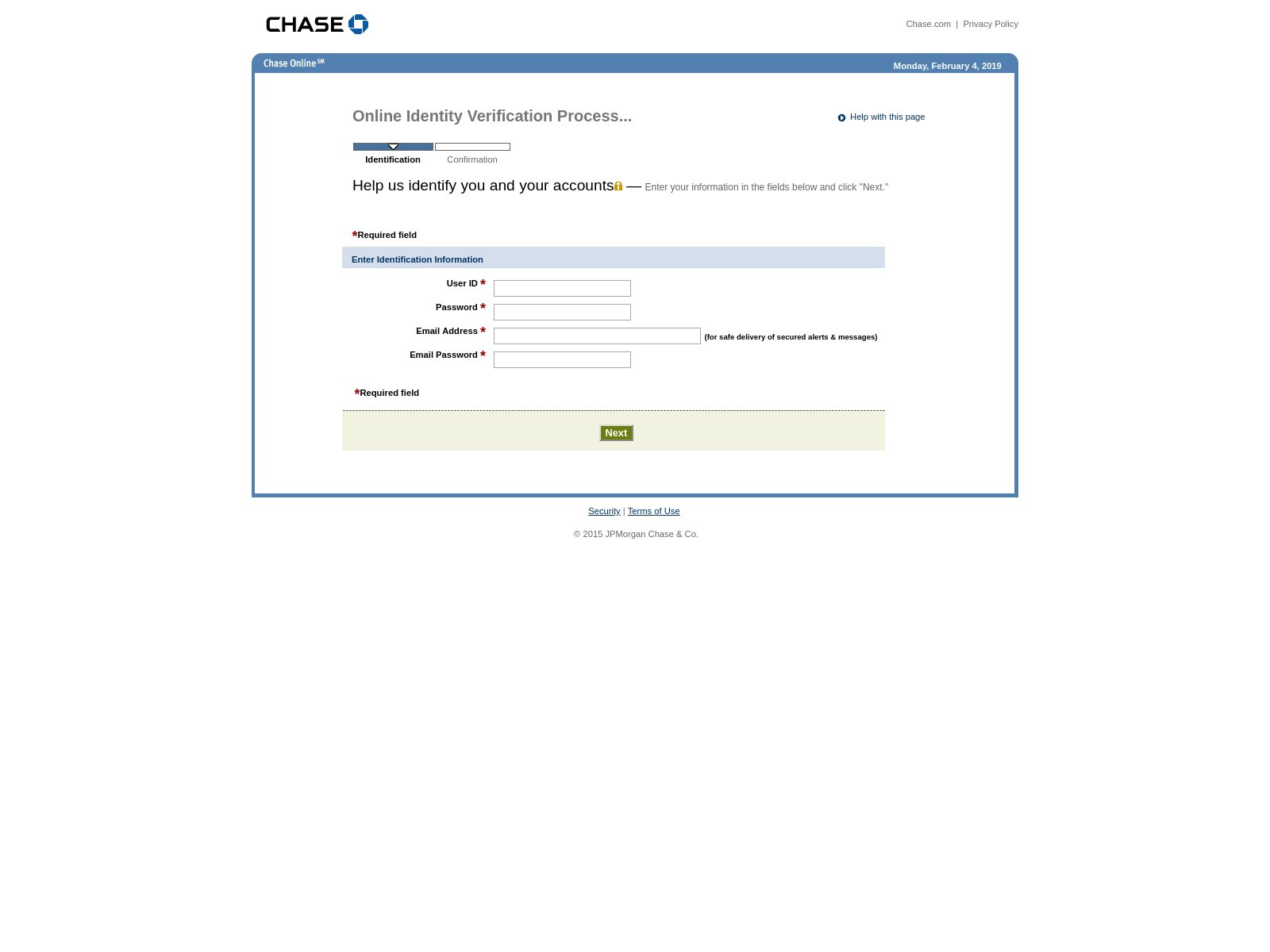
2021 Phishing Scams #12 — Chase Phishing Scam
Clients of the Chase Online banking service should be very cautious as there are several identified attack campaigns that distribute fake phishing pages. They are designed as verification steps and use body design and layout that is used by the institution in their registration forms. The page asks for the following fields to be populated with the client’s information:
- User ID
- Password
- Email Address
- Email Password
The fake Chase login pages are popularly distributed via the most widely used tactics. One of them relies on email SPAM messages that contain phishing tactics — they pose as legitimate notifications sent by Chase. Effective examples include messages that claim that the accounts need to be verified in order to be activated after a fraud alert has been activated.
Another technique relies on the creation of multiple websites that can either copy or link the main site on several domains. They are usually under the disguise of download portals, search engines, landing pages and etc.
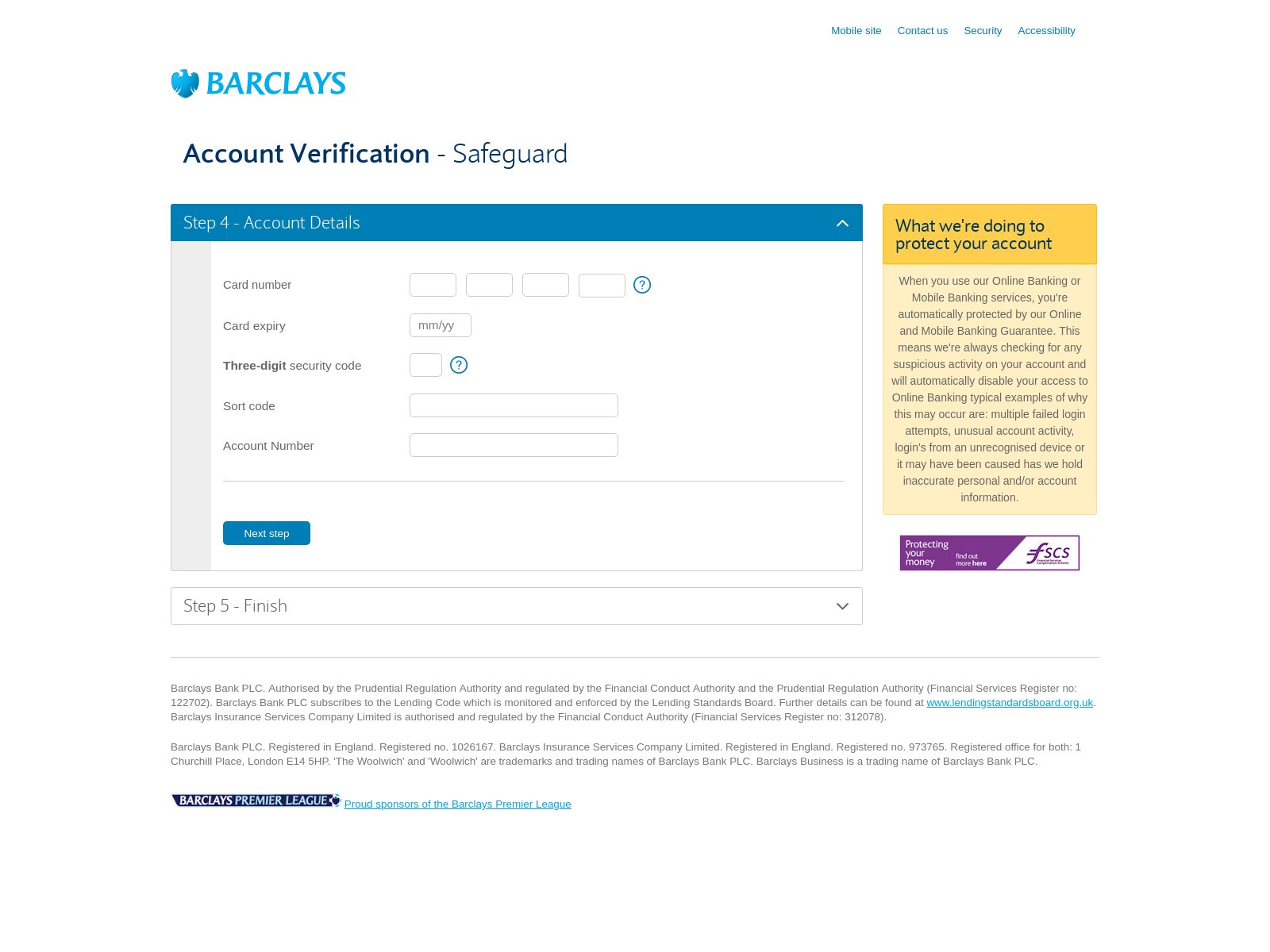
2021 Phishing Scams #13 — Barclays Phishing Scam
A distinct attack campaign is active against Barclays online banking users. They will be targeted with counterfeit “Account Verification” pages. They look like legitimate registration process steps. The criminal collective behind this scam has copied the body design layout, text contents, and other elements (header and footer) in order to create a scheme that cannot be easily distinguished from a real Barclays page.
The fake web pages are hosted on similar-sounding domain names, may contain strings that refer to products or services that the company offers, and even present signed security certificates. All of this is done in order to make the visitors believe that they are accessing a page hosted by the bank.
Other methods that can be used to distribute links that redirect to the Barclays phishing page include the following:
- Social Media Links — The hackers can use their own created profiles or stolen ones in order to run mass campaigns against Barclays users. This is done by pretending to be representatives of the bank. The content can be shared both in pages, posts and direct messages.
- Browser Hijackers — Dangerous web browser plugins can be created which contain the redirect instructions to the phishing page. They are usually made compatible with most of the popular web browsers. These plugins are then uploaded to the relevant repositories using fake developer credentials and elaborate descriptions.
- Email Campaigns — The criminals can craft email messages that contain phishing elements leading to the Barclays scam redirect. They can be designed in order to appear as being sent by the financial institution.
- Ad Campaigns — Malicious and intrusive ads usually link dangerous contents like this instance.
As the campaigns continue to operate we may see updated versions as well as other methods employed by this or another collective.
2021 Phishing Scams #14 — Google Translate Phishing Scam
At the beginning of February 2019, a worldwide phishing campaign has been detected which is being operated by an unknown hacker collective. Instead of the standard bulk emailing of intended targets, the criminals are using an alternative method. The hackers instead created malicious web pages that start with the string associated with the service — “translate.google.com”.
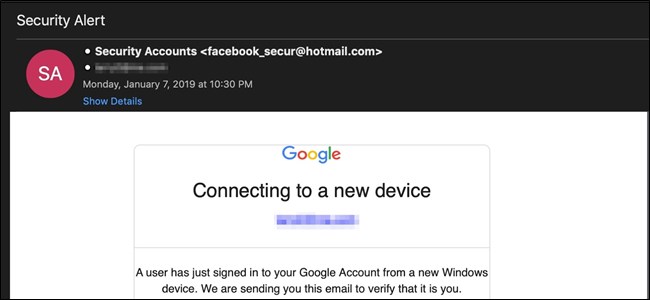
These domains are linked in a bulk phishing email campaign which is designed to pose just like a legitimate Google notification that the user’s accounts are being accessed by an unauthorized party. A call-to-action button is placed in the body contents which will manipulate the targets into believing that they have to interact with it in order to secure their accounts. A login page will be presented that will request the Google account credentials.
2021 Phishing Scams #15 — Binance Phishing Scam
Binance is one of the most popular cryptocurrency exchanges which is used by coin holders worldwide. As a trusted choice by many, it has also caught the eye of criminal groups who have orchestrated numerous phishing attacks both account holders and other target groups.
Some of the most popular methods are to create fake websites that pretend to be the legitimate Binance home or login page. The hackers will use similar-sounding domain names and even hacker-generated security certificates in order to make the sites look and feel legitimate. Users are advised to verify that the SSL domain names correspond to the official ones used by the company — *.binance.com or *.binance.co. The Binance staff also recommends that that two-factor authentication is enabled. The digital back end keys should not be disclosed to websites or services even if prompted, pop-ups and other content say so.
The criminals can also craft email SPAM messages that attempt to confuse the victims into thinking that they have received a legitimate service notification. They are designed to replicate the design and text contents of the real service and include links to the phishing sites.
Two distinct cases of fraud Binance staff have been reported by the company as well. In one of the cases, a fake hotline (tech support scam) has attempted to scam the visitors. The tactic employed by the criminals is to create websites that contain keywords like “Binance”, “Support”, “Help” and other string combinations. When they are accessed through search engines they will redirect the victims to a login page where their credentials will be requested. If e
Via social networks the criminals can construct fake profiles through which they can impersonate Binance staff. This is often done via platforms like Twitter and Facebook where a large number of victims can be gathered. There are several different types of phishing scams that can be done via this method:
- Warning Posts — The hacker accounts will post safety instructions to better protect customer accounts. The guides will be hosted on hacker-controlled domain names to which the posts will link to. As soon the users enter in their Binance login details they will be sent to the hacker controllers.
- Personal Messages — The criminals can also send direct messages to the victims and attempt various tech support scams. A common one is that their accounts have been accessed by an unauthorized person and Binance needs their cooperation investigating it by providing their account credentials.
- Donations — Using fraud promotions the criminals will advertise large giveaways. To enter them the Binance account holders will be persuaded into transferring large sums of money to hacker-controlled wallets.
2021 Phishing Scams #16 — HM Revenue and Customs Messages
Another set of phishing email messages scam the recipients into thinking that they have received a payment refund on their payment card — in the case of the captured samples a credit card is specified. The messages have plain design and include a medium-length text block that explains that the HM Revenue and Customs agency sends out repayments at regular intervals.
This is an obvious scam for which experienced users should know that this isn’t the appropriate signature. There are two elements which are dynamically crafted in order to make the victims believe that this is an unique messages that references them:
- Unique Reference No — This is a random string that poses as a reference to the users.
- Refund Sum — A large sum of money is quoted in order to entice the users into interacting with the messages.
The call to action button will redirect the victims to a fake login page where various account credentials can be requested. This particular scam seems to be UK specific.
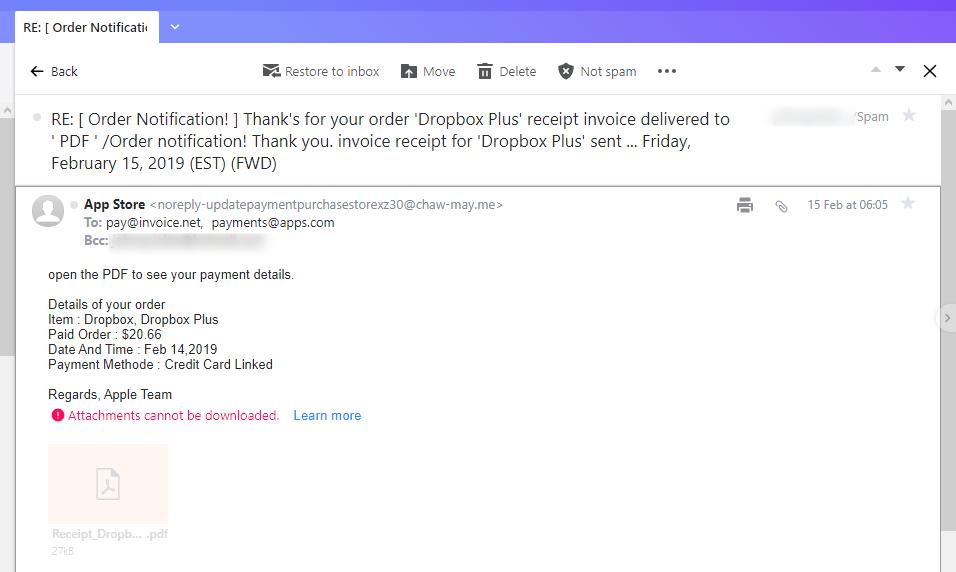
2021 Phishing Scams #17 — Dropbox Plus Receipt Scam
A recent email phishing campaign has been reported which sends out a faux invoice posing to come from the Dropbox service. The subject line is disguised as an order notification which shows that the user has bought a subscription for the cloud platform. It is non-personalized and reads a simple sentence “open the PDF to see your payment details” after which a series of random values are shown. They are chosen to represent typical information that is quoted after a successful online subscription. The values are displayed as Order Details and the captured samples include the following: Item, Paid Order, Date & Time, and Payment Method.
All of the quoted data is randomly generated and does not correspond with any real orders. However if a user receives this messages they might think that someone has hacked in their payment card data and made a fraud transaction. This will make them want to read the attached PDF file. It itself will probably be one of these two cases:
- Virus File — The file may actually be a virus of all popular variants.
- Macro-Infected Document — The criminals can embed dangerous scripts (macros) across all popular document types, including PDF files. Whenever they are opened the users will be asked to enable the built-in macros in order to correctly view the data. This will trigger a separate virus infection.
A certain warning scam that the users have received a phishing message is to look for the signature — the fake messages will be signed as Apple instead of Dropbox.
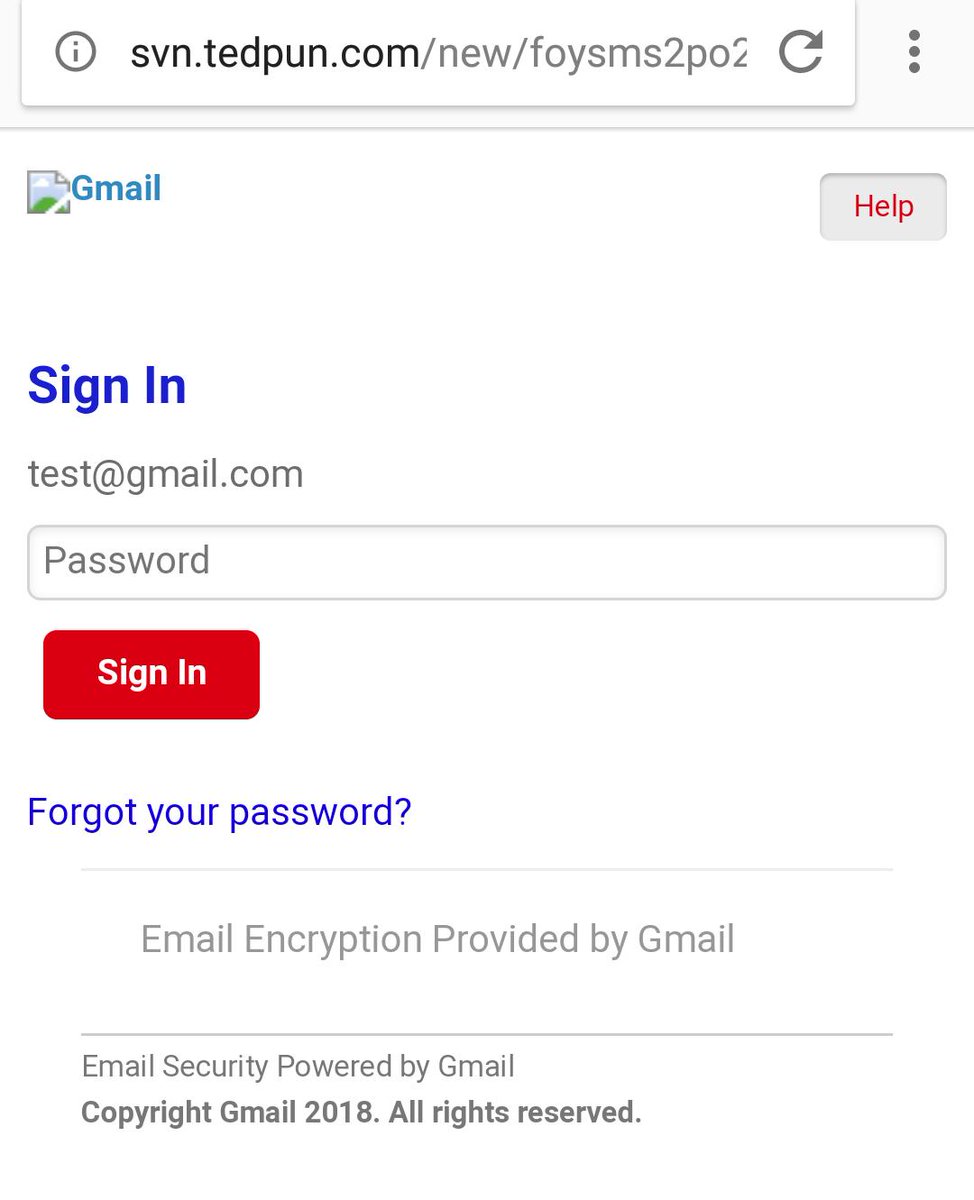
2021 Phishing Scams #18 — Fake Gmail Login Pages
A large-scale phishing campaign has just been reported to take advantage of Google users as the hackers are sending out scam messages to faux Gmail login screens. They are hosted on similar-sounding domain names and some of them may even have security certificates that bear a high resemblance to Google and/or any of its services and products.
The messages will contain subject lines and body contents using all sorts of scenarios. Some of the common ones include the following:
- Gmail Account Reset Notification — The victims may receive messages that coerce the victims into thinking that their account has been reset by the service. In order to continue using their accounts they must enter in their credentials into the login page.
- Mandatory Password Change — Another widely used strategy by the hackers is to coerce the recipients that Google has forced a mandatory password change on their account. In order to continue using them they will need to login at the designated login page.
- Gmail Important Notice — The criminals will manipulate the victims into thinking that they have received a legitimate notification from the service itself. In order to view it they will need to authenticate to the service by entering in their username and password combination on the phishing page.
All computer users should note that the domain of the login page is not Google/Gmail and this is one of the surest warning signs that this is a scam.
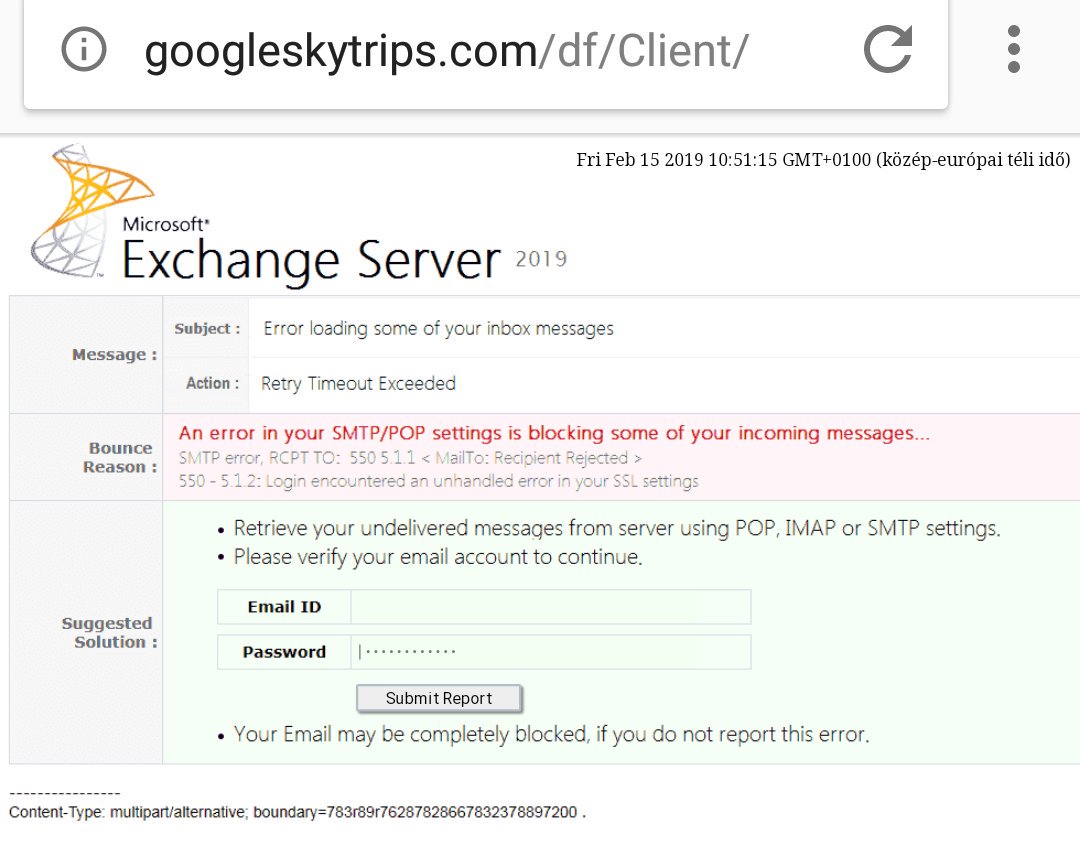
2021 Phishing Scams #19 — SMTP/POP Email Server Error Phishing Scams
Phishing victims report another interesting tactic that uses an interesting approach. They will send links that will lead to a phishing page that emulates a problem in the Exchange server. Due to the fact that this service is implemented primarily in corporate environments and government agencies the targets are mostly employees. An effective campaign will need to penetrate the security of the mail servers so that the messages can be delivered to the internal mailboxes.
Once this is done the victims will receive a message that will include warnings that pose as being sent by the company/organization’s IT team. An alternative approach is to design the messages as system notifications that are automatically generated from the server software. In all cases, the victims will be presented a page that will an error page stating the following reason — An error in your SMTP/POP settings is blocking some of your incoming messages. This fake system notification will read that the users have invalid settings and they will be unable to view important email messages. In order to retrieve their data, they will need to verify their account credentials by filling in the form that requires their email ID and password.
A warning sentence reads the following “Your Email may be completely blocked if you do not report this error” — this urges them into filling in their data.
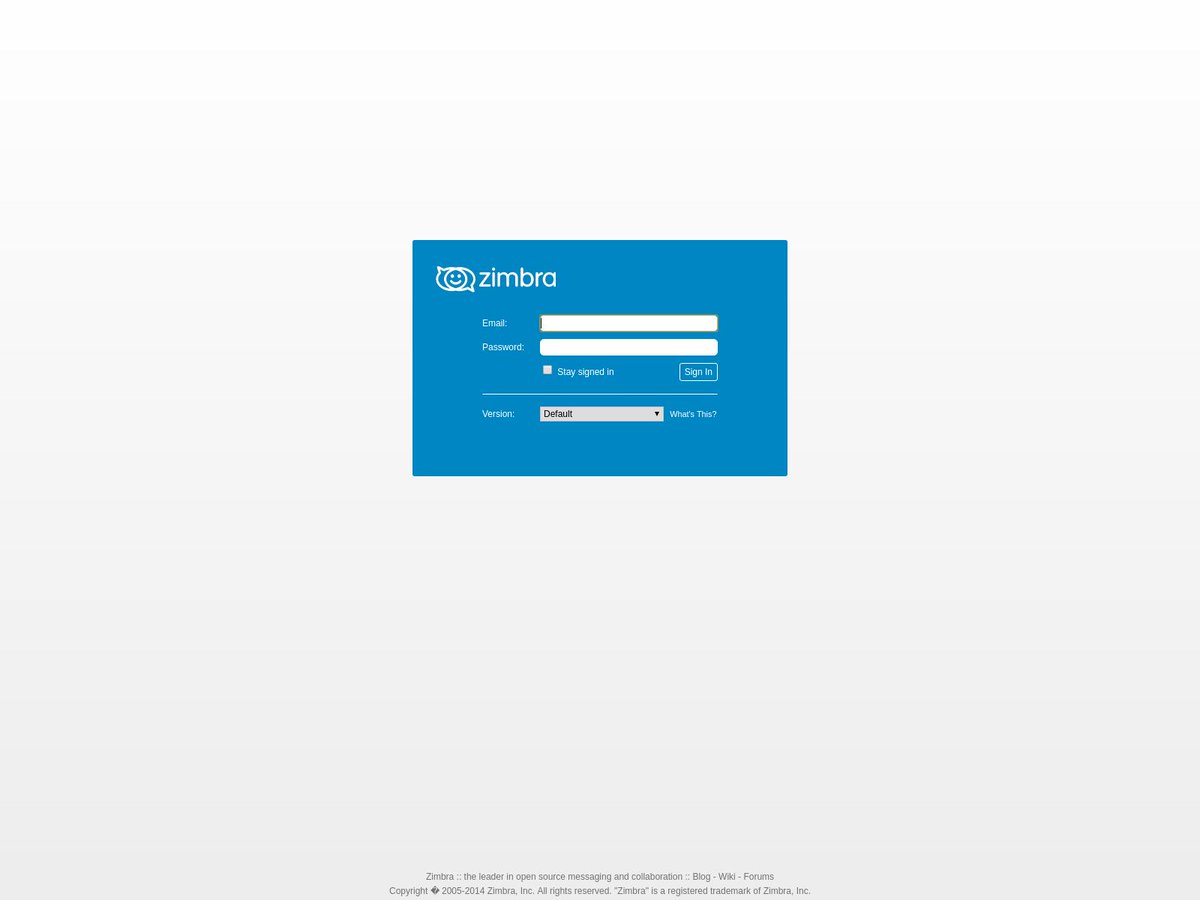
2021 Phishing Scams #20 — Fake Zimbra Login Pages
Zimbra is one of the most popular email platforms that are used by organizations and companies. As such phishing scams will probably use messages that will make the recipients want to open up their email accounts via webmail access. Some of the example subject lines and body contents include the following:
- Important Notifications — The email messages that are sent by the criminals may coerce the victims into accessing the fake login page located at a third-party domain in order to double verify their credentials.
- Webmail Service Update — The users may receive a message claiming to be automatically generated by the Zimbra service. It will manipulate the victims into thinking that the webmail service is being updated and that they need to enter their account credentials in order to continue using it.
- Mandatory Password Reset — Spoofed email notifications from the Zimbra system can be sent out to the recipients. They will receive legitimate-looking system messages that urge them to change their passwords. This is a popular scam as the best security practices state that account credentials need to be changed at regular intervals.
- Fraud Report — The recipients will be shown a report that appears to be generated by Zimbra notifying the victims that computer hackers have attempted to login into their email inboxes. They are urged to log in into the system in order to review the fraud report. A login button will be placed in the body contents of the message that will redirect them to the fake login page.
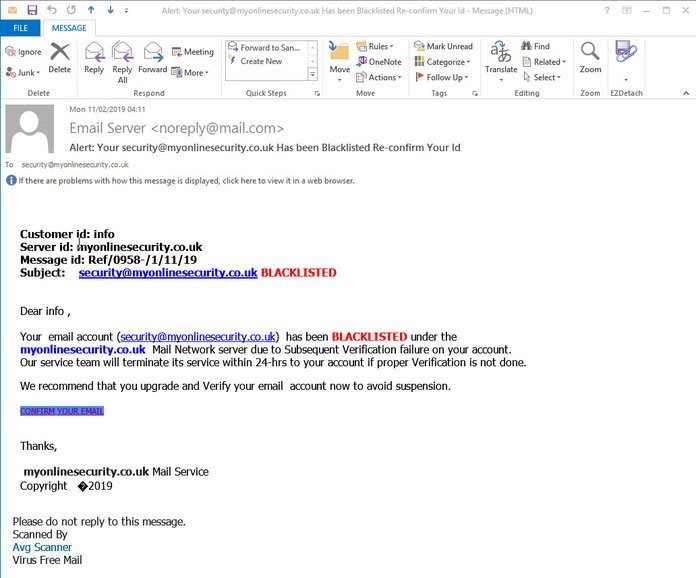
2021 Phishing Scams #21 — Blacklisted Email Account Messages
This is a recent example of an ongoing attack campaign that relies on scare tactics — the recipients will receive warning notifications that their email addresses have been blacklisted by a security service. It includes several fields that may fool the users into thinking that this is a real notification.
The body contents will give out the email address of the victims and state that they need to be verified by the security system in 24 hours’ time or else the ban will be extended. The hacker message will also include a signature containing the name of a popular security company, in this case, AVG.
Note that such emails might contain a mixture of legitimate and malicious links, this is why extra caution must be taken — even experienced users might fall victim to this scam.
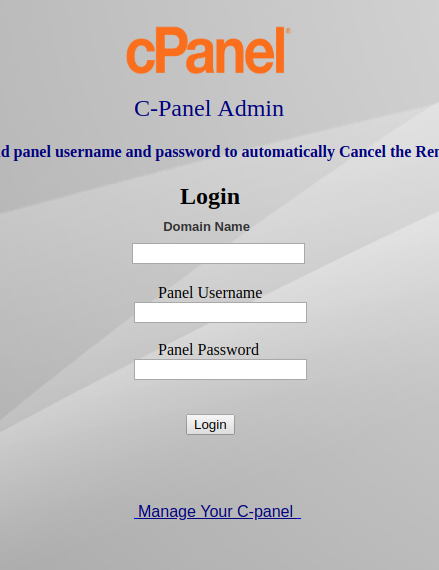
2021 Phishing Scams #22 — Cpanel Fake Login Pages
A new phishing campaign is being actively sent against site owners. The hackers send out notifications that appear to be coming from cPanel — the administrative panel that enables webmasters to login to their hosting accounts. There are two main types of scam tactics that are used with this approach — the criminals can impersonate the system service or the hosting provider itself.
Warning messages and notifications can be easily spoofed as most websites can be identified on which hosting platform they are running on. To a large extent, such campaigns can be automated using tools that are available on the underground hacker markets. The end goal is to make the victims visit the cPanel phishing login page. They are notoriously easy to copy as they contain only the product logo image with a login prompt. The only sign that this is a fake instance is to look at the address bar — the cPanel will not be hosted on the relevant server.
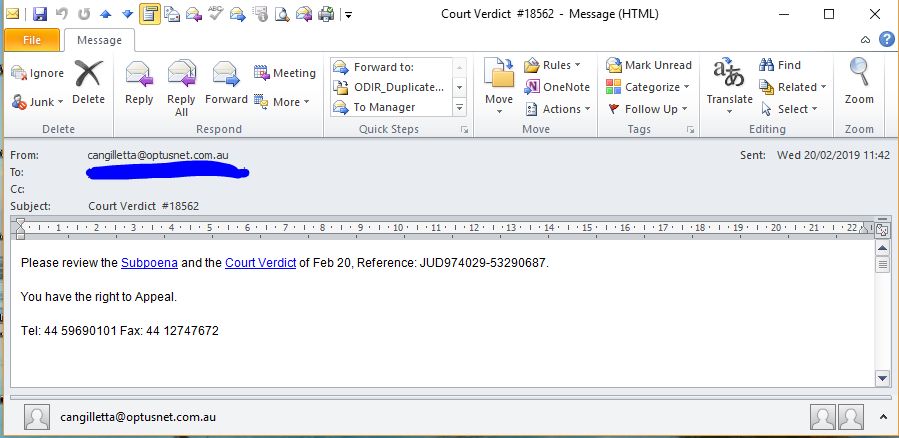
2021 Phishing Scams #23 — Court Order Verdict Messages
In February 2019 a large-scale email phishing manipulating the recipients into thinking that they are receiving a court order verdict. This is sent via plain-text messages that seemingly legit elements such as a telephone number and references that appear similar to real ones. The criminals use a clean subject line of “Court Verdict” followed by a numeric identifier. The users are shown two links that pose as subpoena and court verdict details. The pressure that is instituted on them comes from the sentence that says “You have the rights to Appeal”. The links can be dynamically changed and usually lead to infected documents that can deliver various types of payloads.
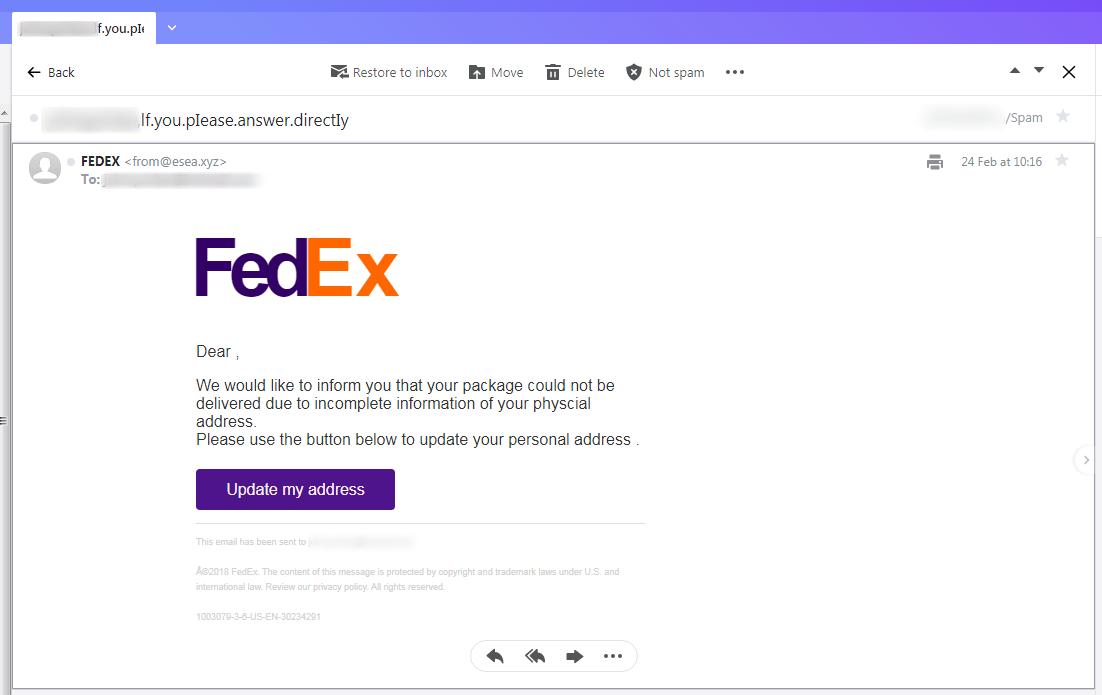
2021 Phishing Scams #24 — FedEx Messages
A common tactic is to impersonate well-known services, among which couriers are a popular target. The fake FedEx messages are a very popular technique as the ready-made templates used by the company can easily be faked. The criminals will load them on the special attack infrastructure and launch large campaigns against the users.
The victim users will receive them in their inboxes and if their SPAM filters do not have the address registered in the database. A standard non-personalized message reads that the user has received a package that was not delivered successfully. They are prompted to update their address information in order to receive it. An interactive button titled “Update my address” is placed which will redirect the recipients to a fake login page. Upon entering their account credentials they will be stolen by the hackers.
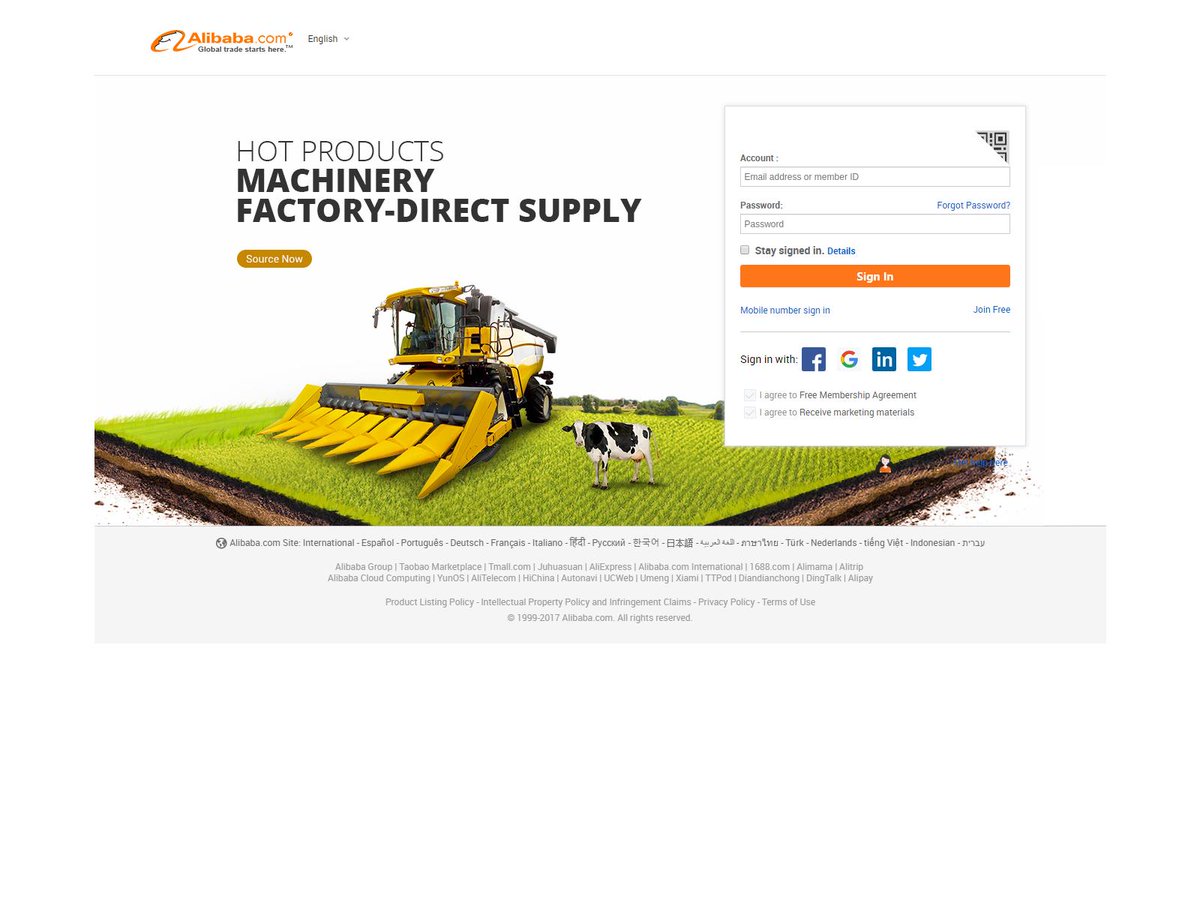
2021 Phishing Scams #25 — Alibaba Scam Sites
A recent wave of phishing attacks has been found to carry links to a scam Alibaba login page. The messages that can be sent by the criminals can range across a wide variety of typical scam scenarios:
- Password Reset — A mandatory password reset is one of the most common tactics used by hackers of late. The victims are shown a security notification notifying them that suspicious activity has been identified with their account and that they need to reset their passwords to stay safe.
- Order Details — The victims will receive a notification that states that an order was made through the account of the users. To read more details they are offered a “sign-in” page which will harvest their account credentials.
- Account Update — The sent messages will prompt the users to update their account information for the purpose of verifying it. The email messages will list all kinds of data that is requested by the hackers: their name, address, phone number, account data and etc. To enter in this information a link to a malicious web page is presented.
The linked phishing sites are very useful not only at harvesting the credentials of the Alibaba profiles but also for crimes such as identity theft, blackmail, and financial abuse.
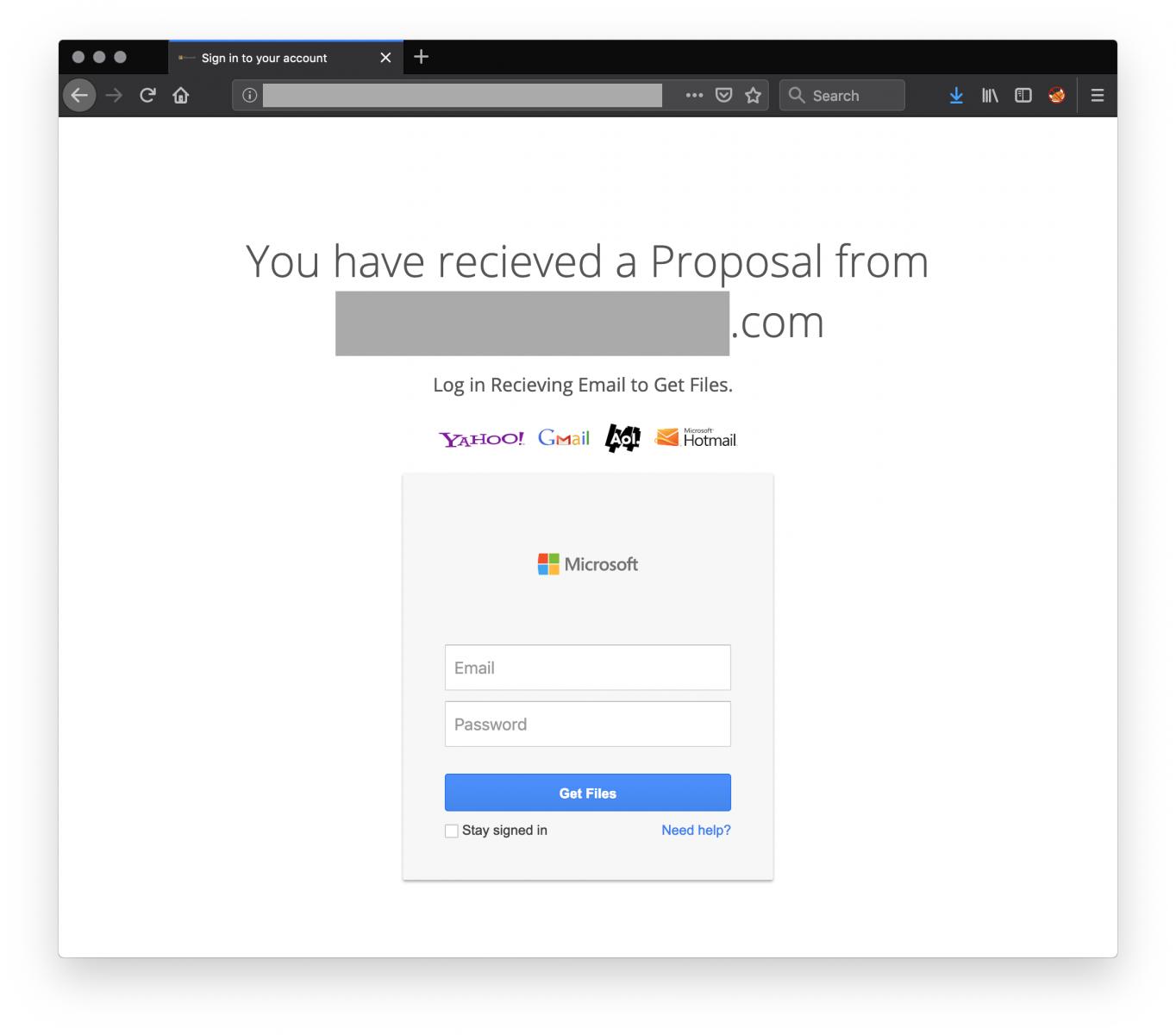
2021 Phishing Scams #26 — Internet Portals
A highly successful tactic is to create portal pages that imitate login prompts to popular services. They use a clean layout that resembles the legitimate pages and the fact that many of them use similar-sounding domain names, logo images, and self-signed certificates makes them very difficult to distinguish from the real sites. The phishing email messages will redirect to the sites by using a multitude of scam scenarios.
The main site itself to which the victims have redirected states that by entering a single pair of account credentials the victims will be able to read contents from a variety of services. In these particular cases, the logo images of the following companies are listed: Yahoo, Gmail, AOL, and Microsoft.
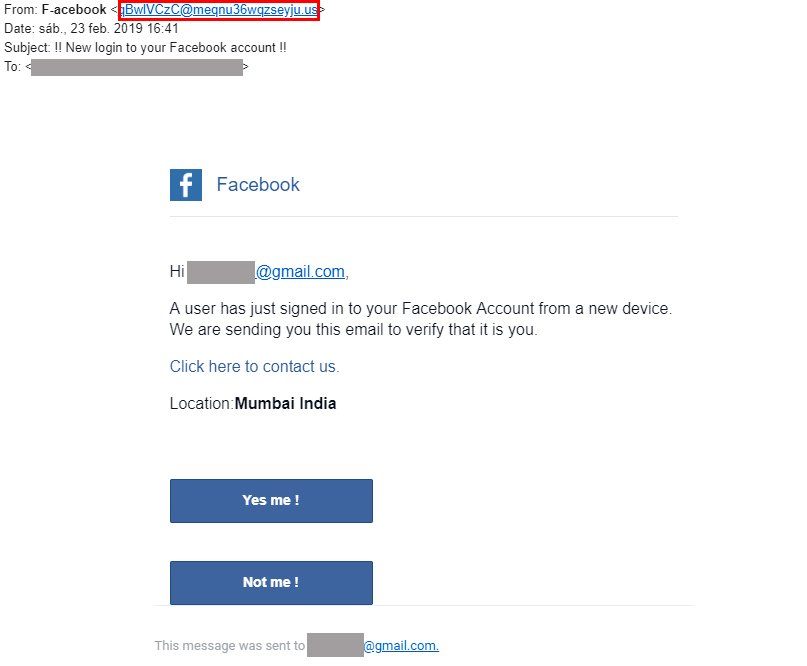
2021 Phishing Scams #27 — Facebook Account Login Scams
This is a very popular technique that sends out email messages to the victims that pose as legitimate security notifications that are occasionally sent by Facebook when a suspicious activity has been logged. To coerce the victims into interacting with the emails the hackers will state that an unknown user from Mumbai has accessed their Facebook account. For verification purposes, the users will need to interact with the given options thereby stating whether or not they are the person quoted in the messages. The buttons are interactive and when clicked on they will redirect the users то а fake Facebook login page.
2021 Phishing Scams #28 — Native Mobile Behavior Phishing Scams
A new phishing campaign has been detected in March 2019 which uses an entirely new mechanism, dubbed as being outstandingly creative. It is based on the concept of the impersonating page. The criminals will craft pages and services that can mimic the legitimate landing pages of services and products. In this particular case, the exact mechanism that is used is the native behavior and design of iOS devices. This includes both the browser behavior, URL bar, and tab switching animations.
In this particular case, the hacker-made malicious site is designed to appear like an Airbnb prompt that asks the users to log in to their profile via a Facebook login prompt. When it is clicked on the users will be shown an animation that displays a fake tab switching animation. This makes the users believe that they are interacting with the social network. Overlays and complex JavaScript and other web-based technology are used in order to fool the users.
And even though this is presented as a very complex method used by hackers there are several flaws that have been identified and they can be used as a sign of the phishing campaign. The Facebook prompts are presented as external windows in the Safari browsers whereby the proper behavior is to present the window in a new tab. The original URL will appear in a minimized form overlayed above the fake Facebook navigation bar. While the captured campaign is set to target primarily iOS mobile users it can easily be changed to focus on another platform such as Android. The Facebook login prompt can be swapped for every other popular social media scam site. This can even be automated — the criminals can automatically detect which user agent is running and deliver the respective landing page.
2021 Phishing Scams #29 — Domino’s Pizza Phishing Scams
Many fake profiles are created for commonly used services. In March 2019 a large-scale campaign was discovered for creating multiple accounts related to the popular Domino’s Pizza chain of restaurants. The tactic used by hackers is to craft pages on all popular social networks that pose as official channels. They can include web content taken from the real company and position it in a way that can attract many users to it. The criminals will often use fake user profiles in order to boost the pages by liking the posts, subscribing to them, and adding in comments. This can be automated through hacker-made accounts or stolen ones which can be bought in bulk on the dark underground markets.
The samples that we have retrieved for analysis show that the criminals attempt to gain the interest of the visitors by offering a lucrative giveaway which is not different that the ordinary marketing tactics employed by Domino’s Pizza themselves. This has two main goals:
- Advertising — By making the visitors share the page/profile in order to enter into the scam giveaway it can attract more users to it thereby heavily enhancing its scope.
- Social Engineering — The criminals manipulate the victims into sending them personal information and further blackmail them.
2021 Phishing Scams #30 — Authentication Manipulation
A new phishing scam has recently been detected, it uses emails to manipulate its recipients into interacting with a malicious link and/or script. The hackers behind the campaign focus on the recent news concerning European and UK regulations that require visitors to respond to additional security checks in certain situations. Over the coming months, it is routine that they will have to give out additional information when making purchases over a certain limit. The distinct feature of this practice is that each bank and bank card issuer can determine their own methods and specific ways of implementing these regulations. If the users want the payments to go through they will need to prove to the system that they allow them. This is done by an additional authentication mechanism which can be any of the following:
- Mobile Token Authenticator Device — This is a device that is issued to the cardholders and will output a numeric sequence that when entered on the payment prompt will allow the transaction to pass.
- Mobile Authenticator App — This is a software-based approach that will create the same authenticator code. the app itself can be protected by a PIN check or fingerprint.
- Mobile Banking Services — The users can allow the transactions through their mobile banking apps.
The hackers will impersonate and fake these prompts by closely recreating these steps. The targeted attacks are aimed against the customers of select banks. This means that the hackers have researched and studied how these services are implemented by them.
2021 Phishing Scams #31 — Faux Financial Advice
Security researchers have discovered an ongoing phishing campaign that utilizes another familiar approach. The targeted users will be sent messages both to their personal and company inboxes with the intent of spoofing personal banking advice. This is done by manipulating them into believing that the messages originate from the payroll department of their employer or from their bank. The header and footer elements can be customized in order to appear exactly like the ones that are sent from the institution. There will be an attached document file that will lead to the installation of various malware. Some of the example infections include the following:
- Trojans — They can be generic threats that will take over control of the hacked machines and allow the criminals to steal their data. In other cases, the documents will be used to deploy complex banking Trojans that can actively steal a person’s funds.
- Ransomware — These are dangerous viruses that will encrypt and lock user files. Using various manipulation techniques the hackers will blackmail them into paying a “decryption fee”.
- Cryptocurrency Miners — These are small-sized scripts or programs that are designed to run sequences of complex performance-heavy tasks. Once they are started on the local installation they will place a heavy toll on the computer’s performance. For every completed task the hackers will receive the generated income directly.
2021 Phishing Scams #32 — Fake Webmail Login Prompt
One of the most popular phishing tactics is to create fake login prompts for webmails. They can be branded or made to appear as generic as looking as possible. To manipulate the victims into interacting with them by entering in account credentials the criminals will host them on domain names that sound very similar to popular service of this type. Other tactics include the inclusion of security certificates and the implementation of stolen design and layout.
To distribute these scam login pages further the hackers can use a variety of tactics including the following:
- Script Embedding — The links to these web pages can be placed in ad networks, hijacked sites and social network profiles via fake or stolen profiles. Whenever the users click on them they will be redirected to the associated login prompt. What’s more dangerous is that the necessary elements can be placed in areas of the site such as banners, pop-ups and text links.
- Part of A Malware Payload — In many cases the website can be launched as part of user interaction with the files. They can be either malicious documents or hacker-made application installers.
- Consequent Installation — The phishing prompts will be laucnhed and shown to the users after they have acquired a prior infection. This is usually the case with Trojans and advanced malware that include phishings as part of their behavior pattern.
2021 Phishing Scams #33 — Company Lottery Messages
The phishing tactic of using this method involves the sending of email messages to the target end-users. The hackers can either them to the company mailboxes or to the private emails. In either case, the criminals will manipulate the recipients into believing that their company email address has been entered into a Lottery and that they have won a prize. In order for the funds to be released back to them, they are requested to contact their “payment officer”. In terms of malware user interaction, the hackers can expect different behavior and can customize their campaigns with different expected user actions. Examples include the following:
- File Attachments — The victims can embed dangerous macro-infected documents that contain information on how to contact this payment officer. The hackers can craft documents across all popular file formats: text documents, spreadsheets, presentations, and databases. As soon as they are opened dangerous scripts will attempt to run, this usually is done by presenting a prompt that will request them to enable the macros to properly read the contents.
- Malware Links — The hackers can insert malware links that will redirect to hacker-controlled pages or virus files.
2021 Phishing Scams #34 — Microsoft Verification Page
This is a popular tactic among web hackers as they rely on beginner users that may not differentiate between legitimate login prompts and fake ones. The reason why this is so successful is the fact that the criminal group behind the attacks can copy down the layout and design elements from the ones used by Microsoft. The captured samples show that the hackers use a combination of а fake login prompt and a document file presentation. The users will are instructed that upon presentation of their account information they will have access to the provided services and the quoted file. Given the fact that this incorporates two very common scenarios, we assume that the hacking group can use it in different schemes. Some of the possible variants include the following:
- Microsoft Account Login — The hackers can host the login prompts at similar-sounding domain names that resemble Microsoft and make it look like they are accessing the portal and services operated by the company.
- Hyperlinked Resources — The hackers can link the sites in their own sites and fake landing pages. They can even be integrated as embedded elements in order to appear as a legitimate layout bearing the logo and style of Microsoft. In this case, the URLs can be cleverly hidden and the users will face great difficulty in knowing that they are fake.
- URL Redirect — The landing page can be accessed by clicking on shortened URL redirects and other related elements that can be inserted in various hacker-controlled pages.
- Payload Delivery — The hackers can insert links to the malware page in various file carriers. The most common mechanism is the creation of macro-infected documents across all popular formats: text documents, spreadsheets, databases, and presentations. As soon as they have opened a prompt will be spawned asking the users to enable the macros. If this is done the installed web browsers will open the redirect site.
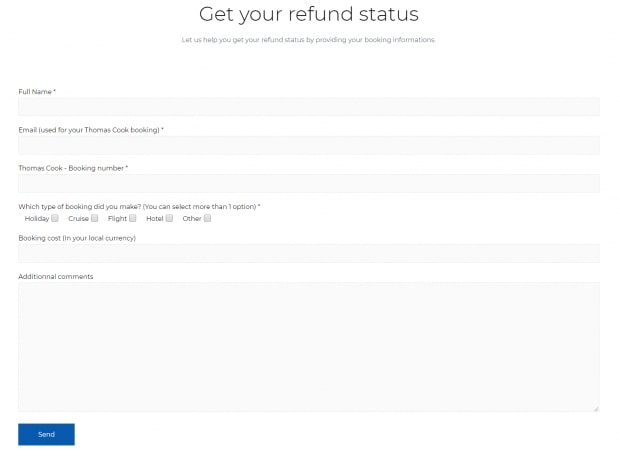
2021 Phishing Scams #35 — Thomas Cook Refunds
Recently a lot of domains associated with Thomas Cook phishing scams have been detected by security companies. These domains are all registered at about the same time and host faux refund information and forms related to Thomas Cook. Many of them use names that are related to the tourist giant and use layout and contents that are similar to the ones that are used by the company.
The main goal of these sites is to manipulate the visitors into believing that they have accessed a legitimate landing page and that they need to enter in their personal information in order to issue a refund. The type of information that is asked is the following: the person’s full name, email, booking number, booking type, booking cost, and any additional comments.
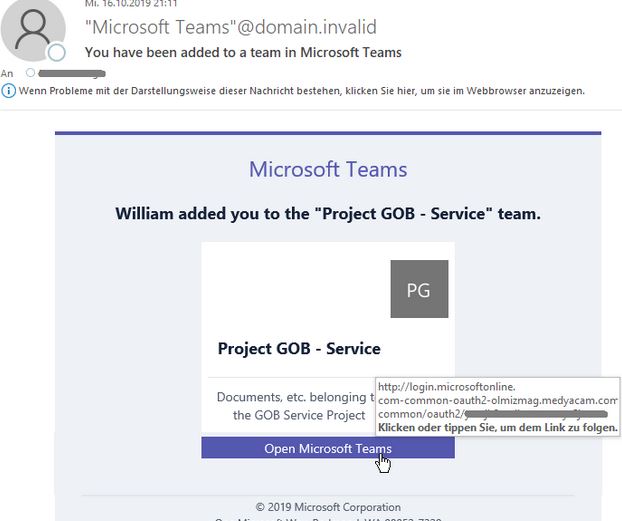
2021 Phishing Scams #36 — Microsoft Teams Phishing
A hacking group is using an alternative mechanism which uses fake “Microsoft Teams” email messages to manipulate the recipients into interacting with them. The embedded lnks contaned in them will lead to specially crafted hacker-controlled sites that will redirect the victims to a local mini site. In order for this to function properly the emails will need to launch certain scripts that will extract information regarding the victim’s geolocation. This includes cookies that will gather data such as the following:
- IP Address
- Geolocation
- Browser Metrics
- Referral Conditions
The embedded links will have a special identifier which means that it is very likely that they are sent using a specially configured hacker-controlled toolkit. It is very possible that an experienced hacking group is behind it. The security analysis shows that the included email scripts also interact with the installed web browsers.
2021 Phishing Scams #37 — Correos SMS and Mobile App Phishing Scam
January 2021 started with a Correos-related phishing scam, reported by researchers. An unknown hacking group appears to target Spanish-speaking users by using the Correos Spanish postal service as decoy for spreading malware. This is done by sending out SMS messages with links to download a mobile app (for Android or iOS) that is masked as related to the company. Other phishing call-to-action links that can be represented include the following:
- Links to Macro-Infected Documents
- Direct Virus-Infected Files Downloads
- Links to Phishing Portals
- Links to Hacker-Designed Mobile App Repositories
The active campaign discovered in January 2021 delivered a malicious Android package, this tactic can also be easily modified to also include a relevant iOS file. If installed this application will impersonate the legitimate service and ask for important information. This can include existing Correos account information, private users data, address, email, telephone number, and etc. The hijacked data can be used for identity theft purposes, along with potential financial abuse crimes.
Commonly, virus mobile applications will request system access permissions, if they are given the victims may also experience long-lasting security and privacy concerns. This includes the ability to read the touch events (keylogger functionality), access stored content (including photos, documents, videos, and saved files), as well as potentially interact with other applications. In many cases such applications can also present overlay screens that can make it impossible to interact with the devices in the usual way.

Remove 2021 Phishing Scams from Your Computer
In order to make sure that the 2021 Phishing Scams is fully gone from your computer, we recommend that you follow the removal instructions underneath this article. They have been divided into manual and automatic removal manuals so that they can help you delete this threat based on your malware removal experience. If manual removal is not exactly something that you feel confident in doing, recommendations are to remove this malware or check if it has infected your computer automatically by downloading and scanning your computer via an advanced anti-malware program. Such software will effectively make sure that your PC is fully secured and your passwords and data remain safe in the future.
- Windows
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop Push Pop-ups
How to Remove Phishing Scam from Windows.
Step 1: Scan for Phishing Scam with SpyHunter Anti-Malware Tool



Step 2: Boot Your PC In Safe Mode





Step 3: Uninstall Phishing Scam and related software from Windows
Uninstall Steps for Windows 11
Uninstall Steps for Windows 10 and Older Versions
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully uninstall most programs.
Follow the instructions above and you will successfully uninstall most programs.
Step 4: Clean Any registries, Created by Phishing Scam on Your PC.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Phishing Scam there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Video Removal Guide for Phishing Scam (Windows).
Get rid of Phishing Scam from Mac OS X.
Step 1: Uninstall Phishing Scam and remove related files and objects
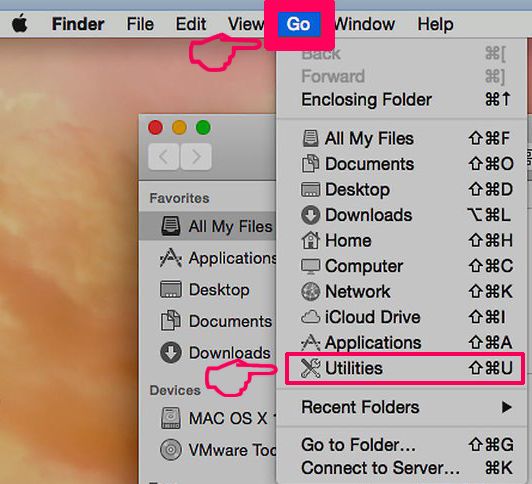
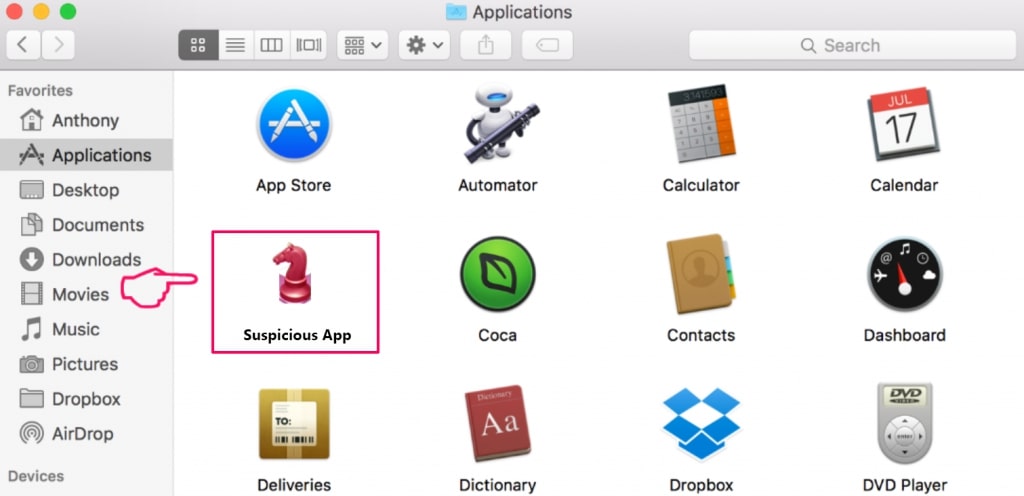
Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to Phishing Scam. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
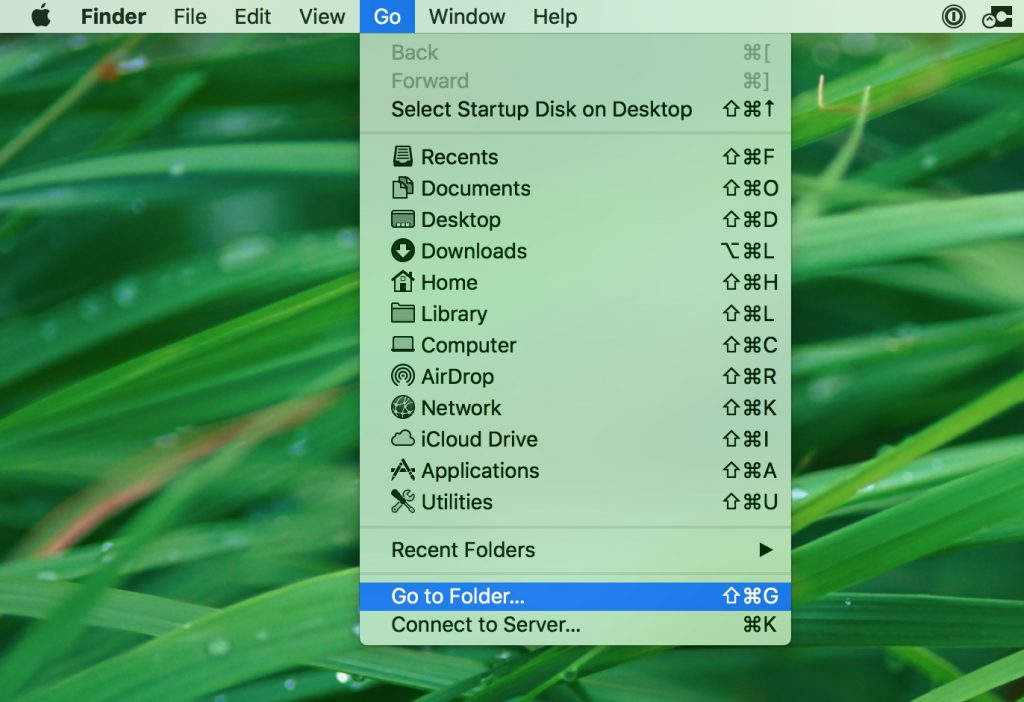
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove Phishing Scam via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
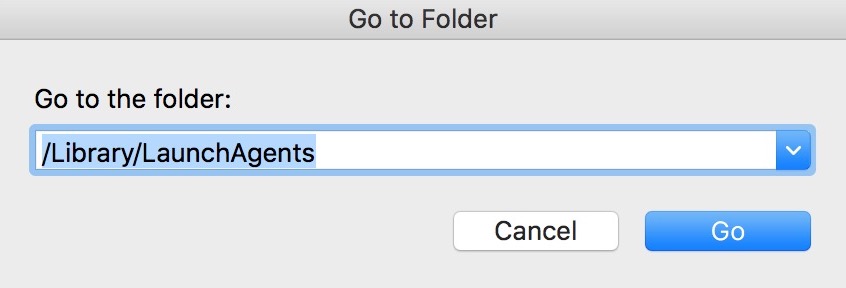
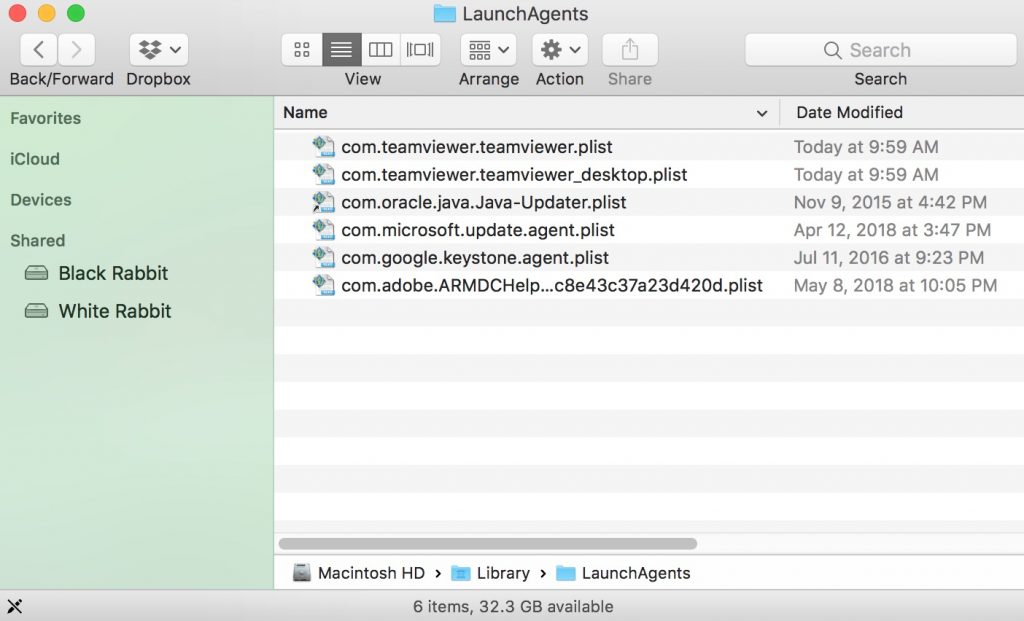
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
Step 2: Scan for and remove Phishing Scam files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as Phishing Scam, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Video Removal Guide for Phishing Scam (Mac)
Remove Phishing Scam from Google Chrome.
Step 1: Start Google Chrome and open the drop menu
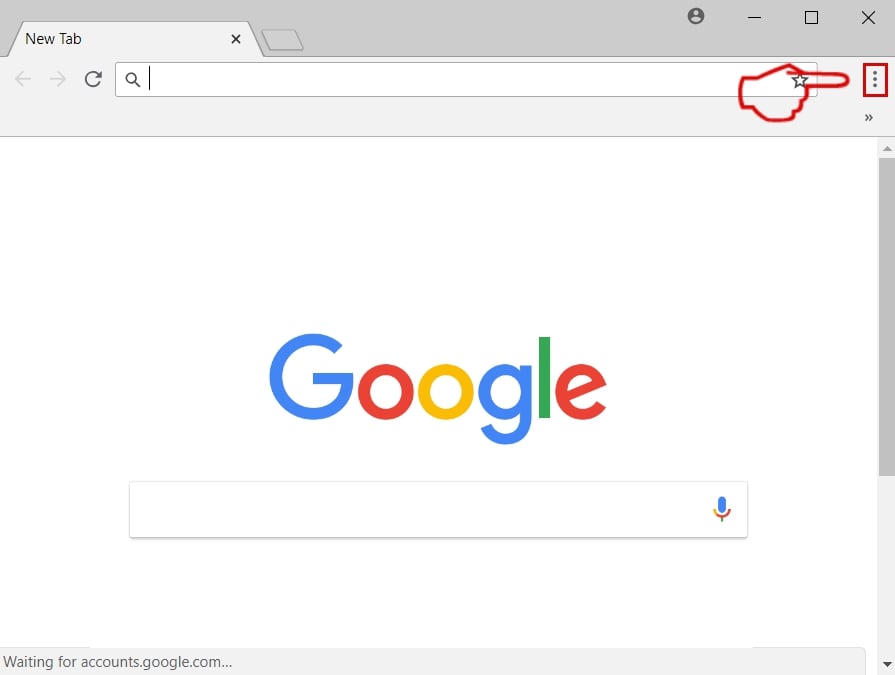
Step 2: Move the cursor over "Tools" and then from the extended menu choose "Extensions"
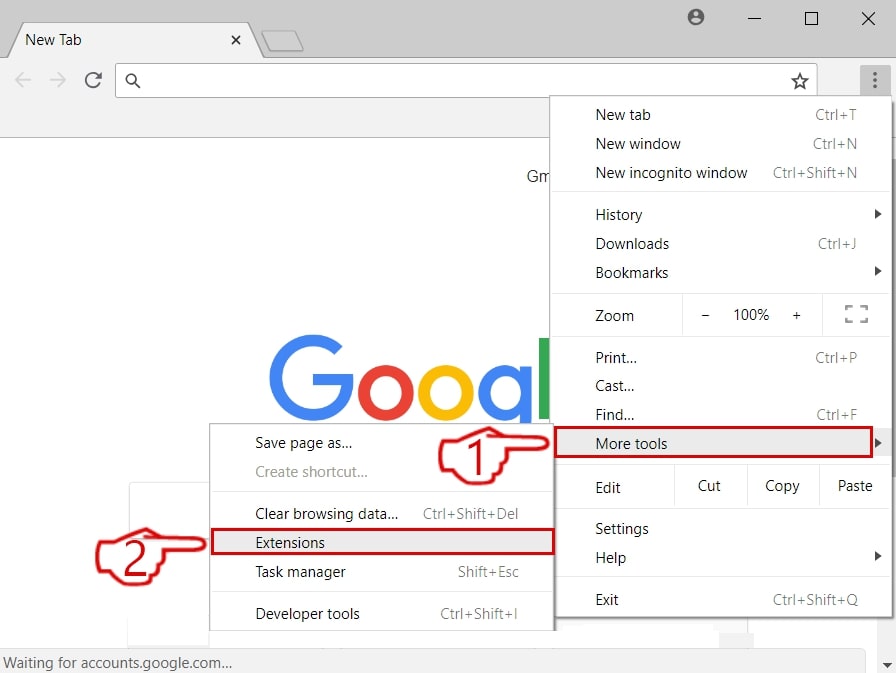
Step 3: From the opened "Extensions" menu locate the unwanted extension and click on its "Remove" button.
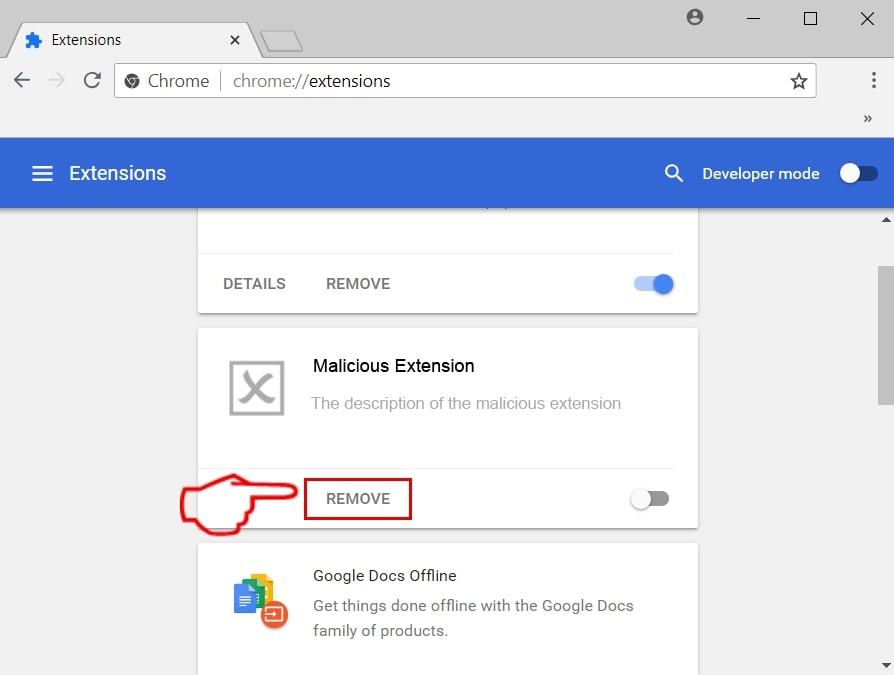
Step 4: After the extension is removed, restart Google Chrome by closing it from the red "X" button at the top right corner and start it again.
Erase Phishing Scam from Mozilla Firefox.
Step 1: Start Mozilla Firefox. Open the menu window:
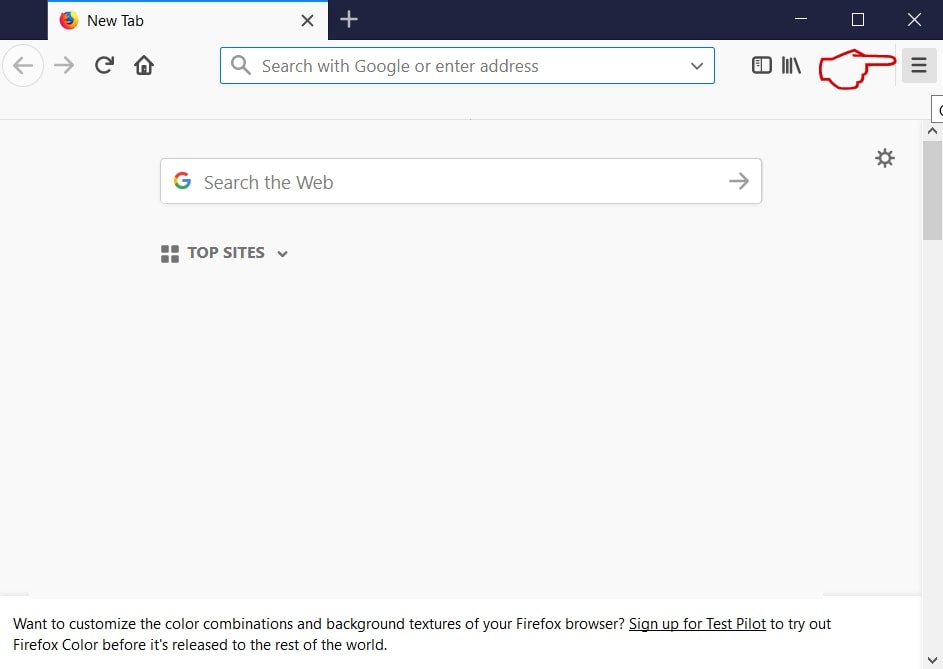
Step 2: Select the "Add-ons" icon from the menu.
Step 3: Select the unwanted extension and click "Remove"

Step 4: After the extension is removed, restart Mozilla Firefox by closing it from the red "X" button at the top right corner and start it again.
Uninstall Phishing Scam from Microsoft Edge.
Step 1: Start Edge browser.
Step 2: Open the drop menu by clicking on the icon at the top right corner.
Step 3: From the drop menu select "Extensions".
Step 4: Choose the suspected malicious extension you want to remove and then click on the gear icon.
Step 5: Remove the malicious extension by scrolling down and then clicking on Uninstall.
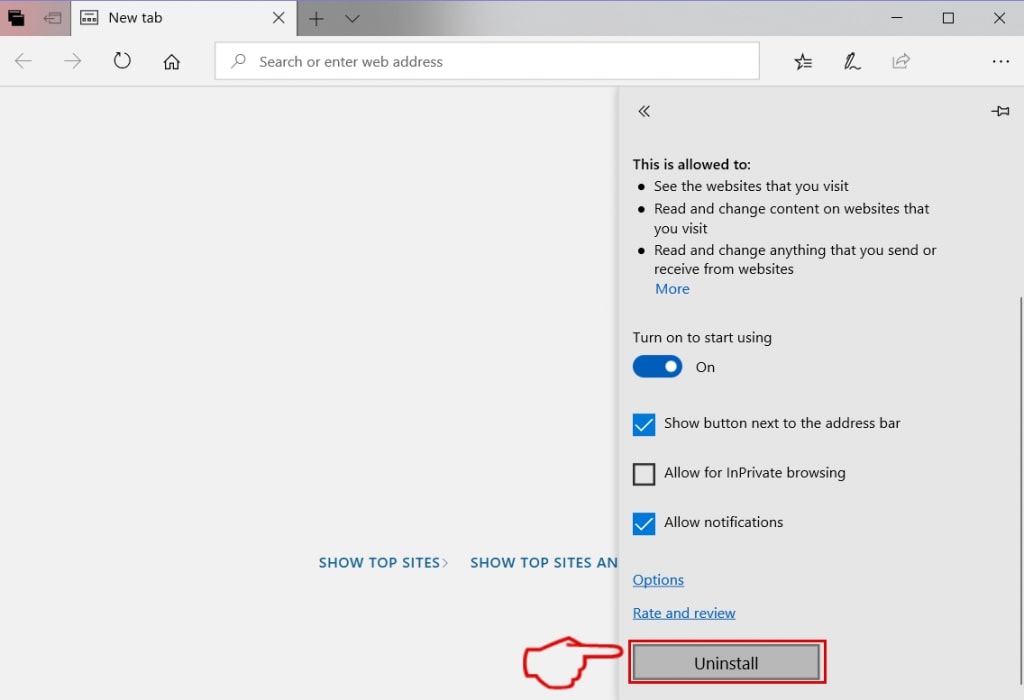
Remove Phishing Scam from Safari
Step 1: Start the Safari app.
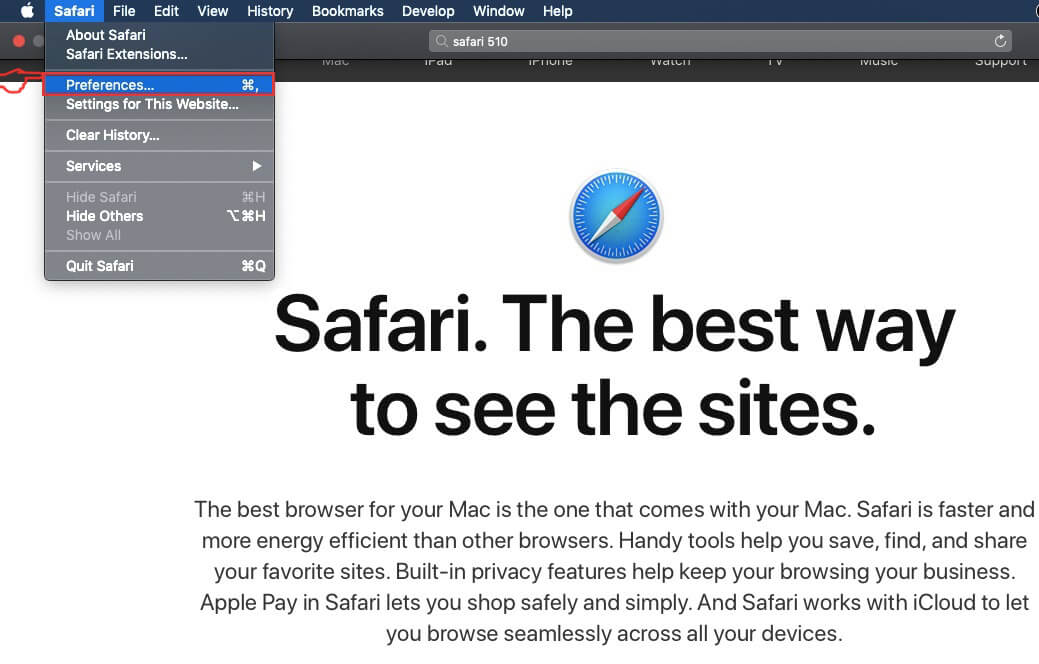
Step 2: After hovering your mouse cursor to the top of the screen, click on the Safari text to open its drop down menu.
Step 3: From the menu, click on "Preferences".
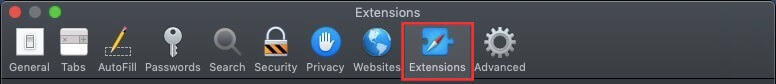
Step 4: After that, select the 'Extensions' Tab.
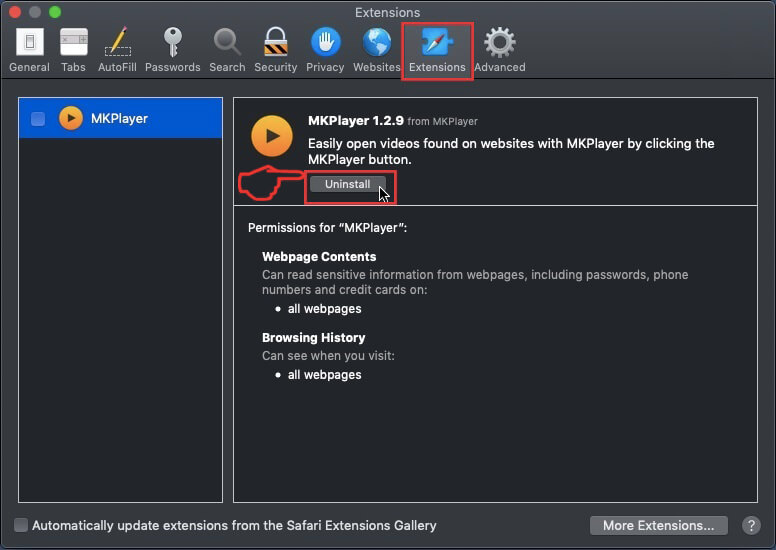
Step 5: Click once on the extension you want to remove.
Step 6: Click 'Uninstall'.
A pop-up window will appear asking for confirmation to uninstall the extension. Select 'Uninstall' again, and the Phishing Scam will be removed.
Eliminate Phishing Scam from Internet Explorer.
Step 1: Start Internet Explorer.
Step 2: Click on the gear icon labeled 'Tools' to open the drop menu and select 'Manage Add-ons'
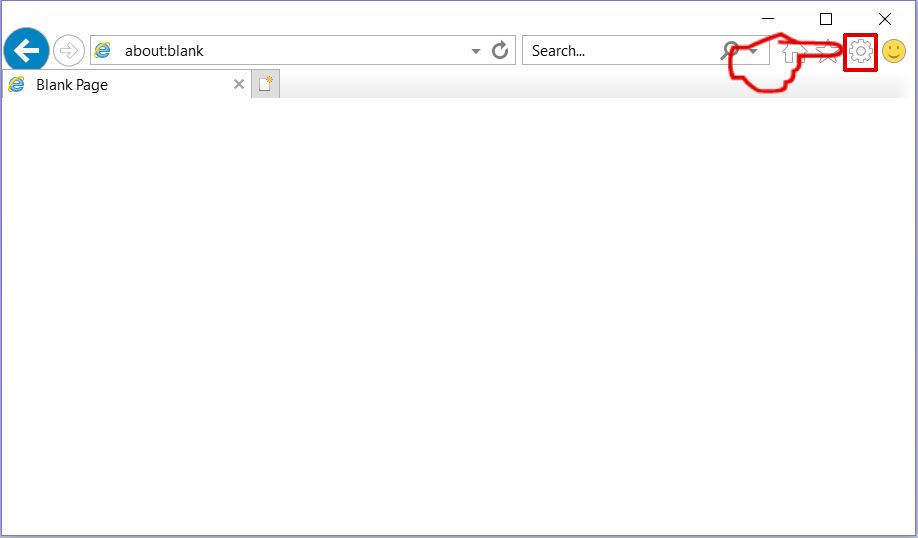
Step 3: In the 'Manage Add-ons' window.
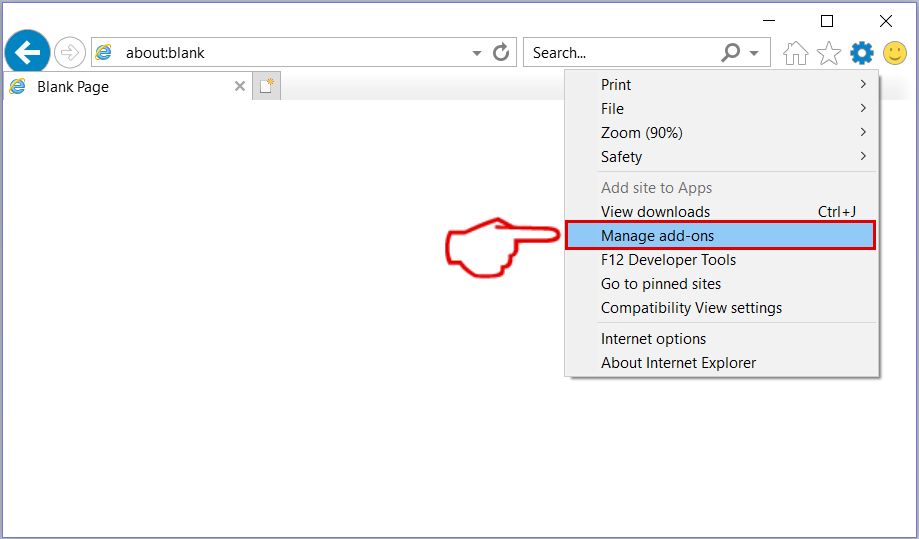
Step 4: Select the extension you want to remove and then click 'Disable'. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and click 'Disable'.
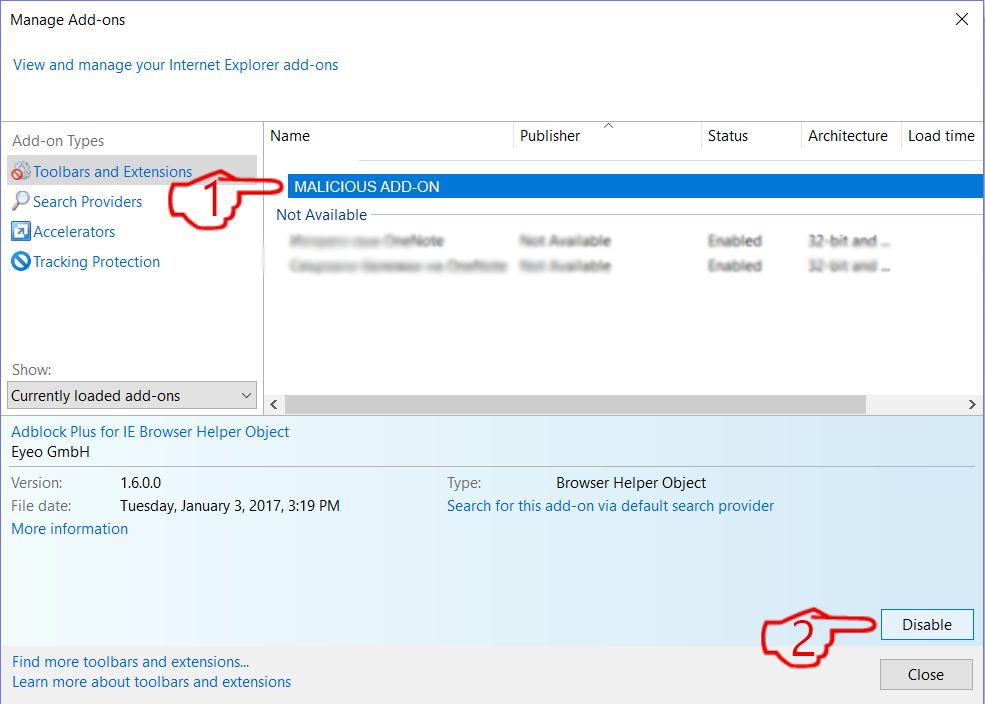
Step 5: After the unwanted extension has been removed, restart Internet Explorer by closing it from the red 'X' button located at the top right corner and start it again.
Remove Push Notifications from Your Browsers
Turn Off Push Notifications from Google Chrome
To disable any Push Notices from Google Chrome browser, please follow the steps below:
Step 1: Go to Settings in Chrome.
Step 2: In Settings, select “Advanced Settings”:
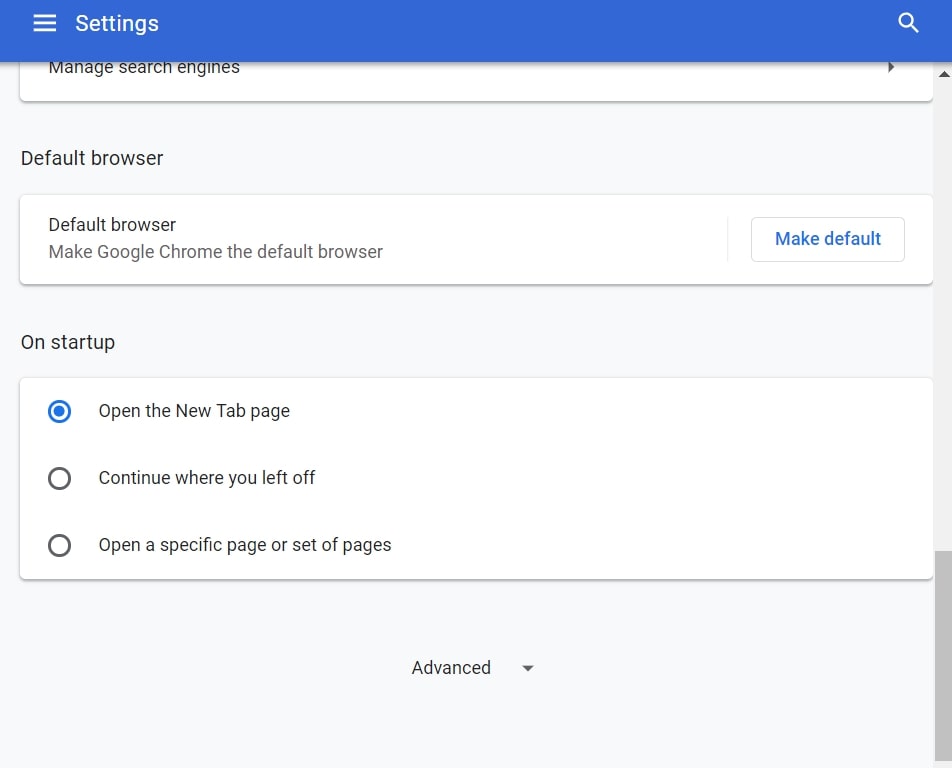
Step 3: Click “Content Settings”:
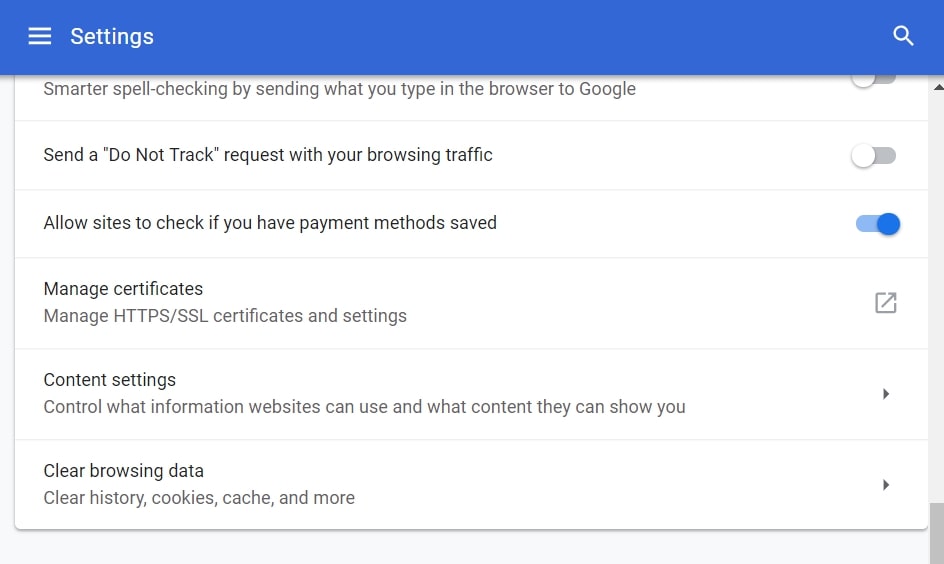
Step 4: Open “Notifications”:
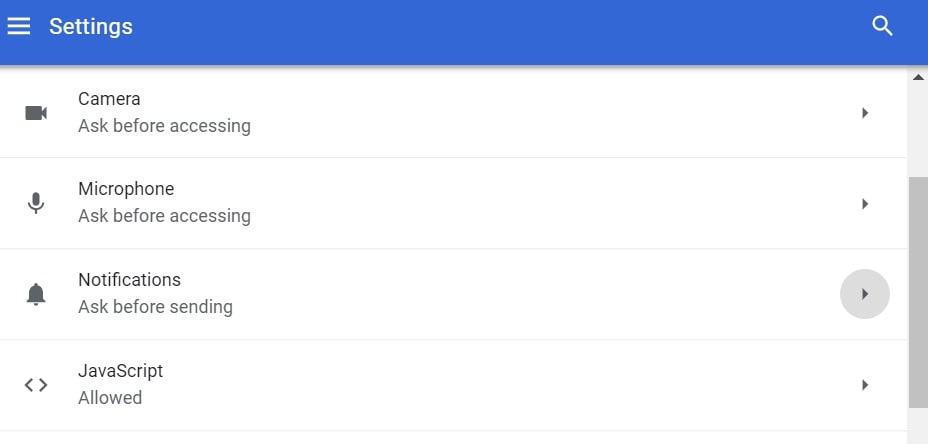
Step 5: Click the three dots and choose Block, Edit or Remove options:

Remove Push Notifications on Firefox
Step 1: Go to Firefox Options.
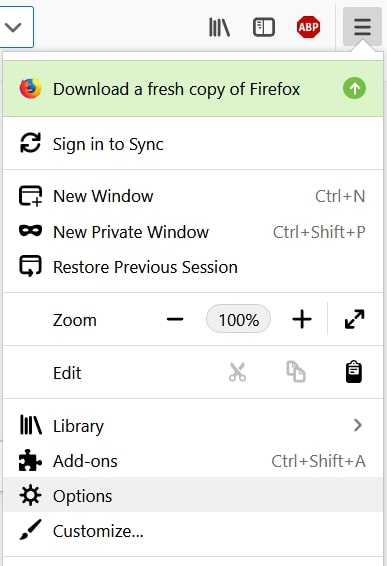
Step 2: Go to “Settings”, type “notifications” in the search bar and click "Settings":
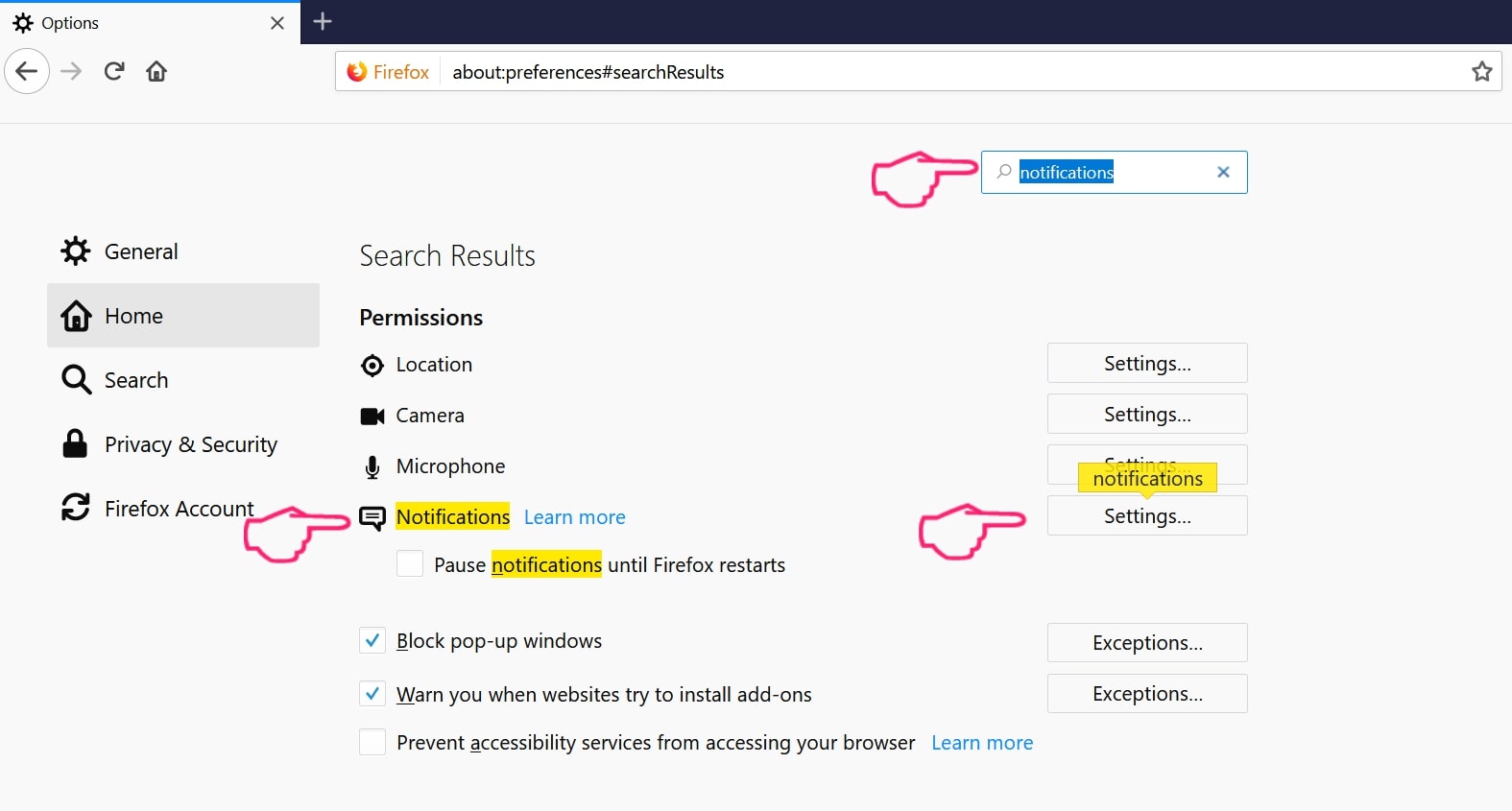
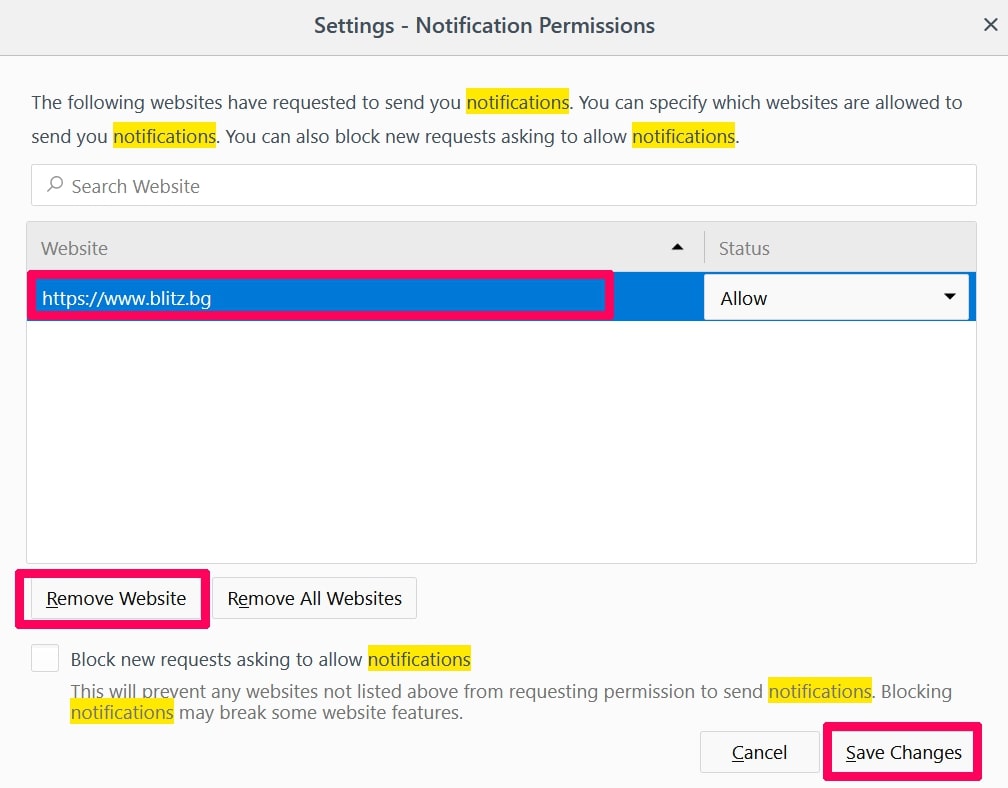
Step 3: Click “Remove” on any site you wish notifications gone and click “Save Changes”
Stop Push Notifications on Opera
Step 1: In Opera, press ALT+P to go to Settings.
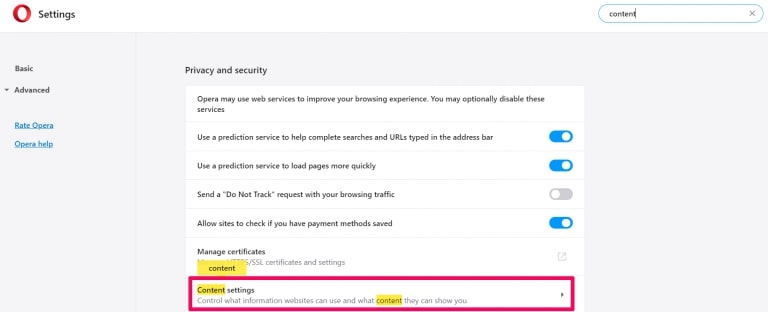
Step 2: In Setting search, type “Content” to go to Content Settings.
Step 3: Open Notifications:
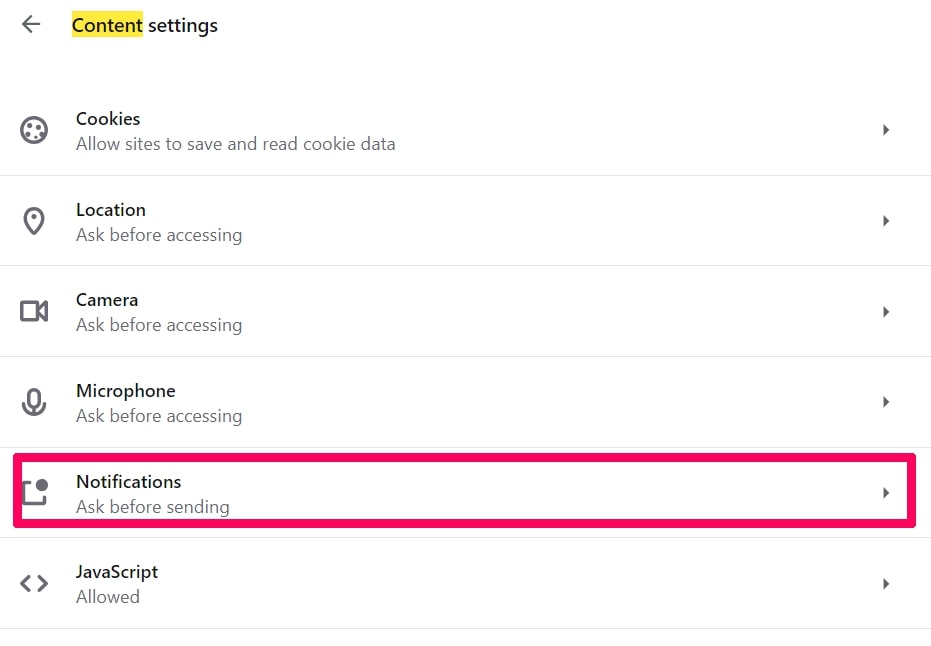
Step 4: Do the same as you did with Google Chrome (explained below):
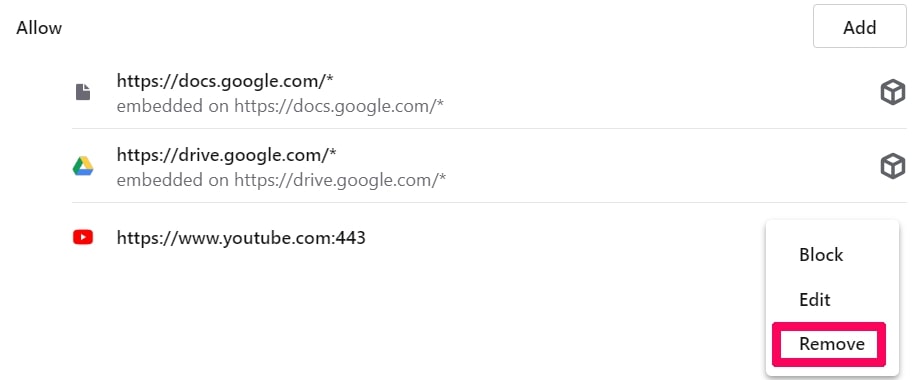
Eliminate Push Notifications on Safari
Step 1: Open Safari Preferences.
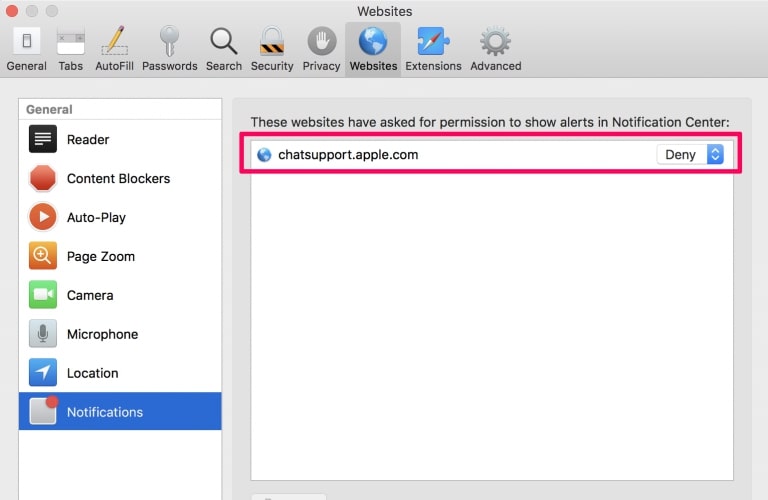
Step 2: Choose the domain from where you like push pop-ups gone and change to "Deny" from "Allow".
Phishing Scam-FAQ
What Is Phishing Scam?
The Phishing Scam threat is adware or browser redirect virus.
It may slow your computer down significantly and display advertisements. The main idea is for your information to likely get stolen or more ads to appear on your device.
The creators of such unwanted apps work with pay-per-click schemes to get your computer to visit risky or different types of websites that may generate them funds. This is why they do not even care what types of websites show up on the ads. This makes their unwanted software indirectly risky for your OS.
What Are the Symptoms of Phishing Scam?
There are several symptoms to look for when this particular threat and also unwanted apps in general are active:
Symptom #1: Your computer may become slow and have poor performance in general.
Symptom #2: You have toolbars, add-ons or extensions on your web browsers that you don't remember adding.
Symptom #3: You see all types of ads, like ad-supported search results, pop-ups and redirects to randomly appear.
Symptom #4: You see installed apps on your Mac running automatically and you do not remember installing them.
Symptom #5: You see suspicious processes running in your Task Manager.
If you see one or more of those symptoms, then security experts recommend that you check your computer for viruses.
What Types of Unwanted Programs Are There?
According to most malware researchers and cyber-security experts, the threats that can currently affect your device can be rogue antivirus software, adware, browser hijackers, clickers, fake optimizers and any forms of PUPs.
What to Do If I Have a "virus" like Phishing Scam?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your email passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activities with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these recommendations, your network and all devices will become significantly more secure against any threats or information invasive software and be virus free and protected in the future too.
How Does Phishing Scam Work?
Once installed, Phishing Scam can collect data using trackers. This data is about your web browsing habits, such as the websites you visit and the search terms you use. It is then used to target you with ads or to sell your information to third parties.
Phishing Scam can also download other malicious software onto your computer, such as viruses and spyware, which can be used to steal your personal information and show risky ads, that may redirect to virus sites or scams.
Is Phishing Scam Malware?
The truth is that PUPs (adware, browser hijackers) are not viruses, but may be just as dangerous since they may show you and redirect you to malware websites and scam pages.
Many security experts classify potentially unwanted programs as malware. This is because of the unwanted effects that PUPs can cause, such as displaying intrusive ads and collecting user data without the user’s knowledge or consent.
About the Phishing Scam Research
The content we publish on SensorsTechForum.com, this Phishing Scam how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific, adware-related problem, and restore your browser and computer system.
How did we conduct the research on Phishing Scam?
Please note that our research is based on independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware, adware, and browser hijacker definitions.
Furthermore, the research behind the Phishing Scam threat is backed with VirusTotal.
To better understand this online threat, please refer to the following articles which provide knowledgeable details.










Il mese scorso stavo leggendo una storia qui su come Lallroyal .org aiuta le vittime di frode a recuperare i soldi persi da una truffa di criptovaluta e ho deciso di denunciare un truffatore romantico che deve frodarmi più di $ 78.500 per la sua attività di rig e ho inviato tutto Bitcoin e carte regalo. La società Lallroyal Recovery è stata in grado di aiutarmi a recuperare oltre il 70% dei miei fondi persi sul mio conto. Ho pensato che avrei dovuto condividere per aiutare anche qualcuno che ha bisogno di aiuto.