“Cybersecurity is the Biggest Threat to the World Economy, CEOs Say”
So reads the July 9 headline of a major news publication on its website just two short months ago.
Concerns about internet and network security have been around for as long as the internet has existed. But, the threats we face now are from bolder actors and have more dire consequences for national security and financial viability in every sector and industry.
On a global scale, the countries that are most targeted by cybercrime are developed countries with abundant resources. Those with the worst cyber-security, and a prime source of attacks, tend to be underdeveloped; the majority are somewhere in the middle economically and security-wise.
How bad is it? Take a look at some recent statistics.
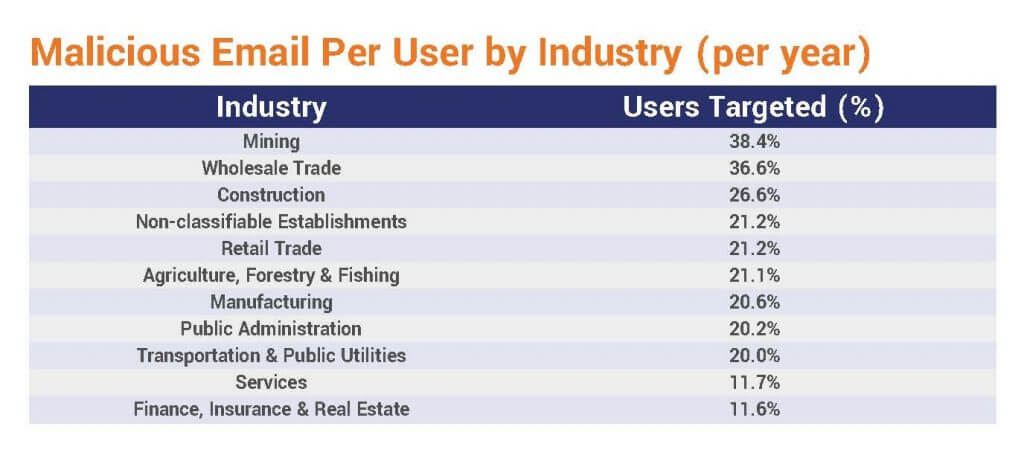
Cybersecurity Statistics
We always hear about the big money exploits, but the more common cybercrimes are targeting smaller businesses that don’t have the resources to recover. These attacks often don’t make the news. For every huge ransomware attack and record-breaking data breach, there are thousands of incidents of browser hijacking, unpatched software, expired security certificates, and crypto-mining occurring every hour of every day.
Here are some eye-opening facts to put things in perspective.
There’s a thriving cybercrime economy: While businesses are losing billions in revenue, cyber-criminals are netting more than $1.5 trillion per year in profit. Those numbers include outright theft, the proceeds of ransomware, and sales of data on the underground market.
Public and private cyber security spending is increasing – but not enough: The US government is reported to have increased spending for cybercrime prevention by 4.1 percent; businesses are increasing theirs by an average of 9 percent overall. Although those numbers add up to billions in spending, how is it being allocated, and is it enough? Small businesses, the biggest targets, are spending less than $5,000 per year on cyber security.
You may be under attack and not even know it: The average security breach goes undetected for up to six months. Most go unreported to the public or officials for 49.6 days after discovery.
SMBs are the biggest targets: According to SCORE, small-to-medium businesses are targeted by cyber criminals in 43 percent of cases.
If you haven’t been attacked yet, you will be: Seventy-six percent of businesses were targeted for phishing attacks and other exploits in 2018. Those numbers are expected to increase over the next five years.
Top 10 Cybersecurity Threats You Should be Aware Of
As attacks reach record proportions and cyber criminals recycle and update old exploits for the new age, cyber security is uppermost in our minds. As IT and business professionals, we’re at the front lines of the fight for privacy protection and preserving data integrity.
Where are the biggest threats to global cyber security, and how can we protect ourselves from criminals who seem to be one step ahead of regulations and security defenses?
1. Privacy is Becoming a Government Concern
In light of record data breaches and public concerns about privacy, governments are stepping in to address the problem with legislation regarding how companies can collect data and implementing strict penalties for its misuse. These new laws range from the controversial and intrusive “snooping laws” in Australia to Europe’s 2018 General Data Protection Regulation (GDPR).
2. Cyber Risk Insurance Will Become a Normal Operating Expense
It was only a matter of time before the cyber security situation became so dire and financially draining that insurance would become necessary to limit risk and liability. Such policies already exist, but they may become a routine business expense that’s tailored by industry and covers such things as loss of reputation and negative publicity.
There are a lot of companies at the forefront of crafting solutions and educating IT pros about cybersecurity issues. There may come a time when using advanced security products like a next generation firewall to screen out the bad guys at the door, a VPN to encrypt your web traffic, and a full-featured security software suite to scan for malware and other nasty stuff will net you a discount on your cybersecurity insurance in the same way that you can get a break on homeowners insurance by installing a home alarm system.
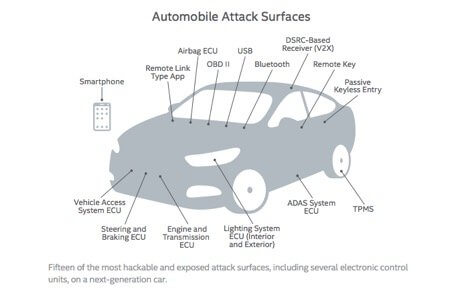
3. IoT Networks are Vulnerable and Growing
The internet of things (IoT) was meant to use advanced tech to make life and business more efficient and convenient. It has also opened up new ways for cyber criminals to exploit our vulnerabilities. This is the attack surface of the average late-model car alone:
IoT networked toys and games are even contributing to child endangerment and exploitation.
The problems range from companies placing all of their devices on the same network to leaving default passwords in place. Global and local inter-connectivity of accounts, appliances, climate and access control, and personal entertainment devices is expected to reach 31 billion by the year 2025. We need to get a handle on this issue now rather than later.
4. Cryptojacking is Replacing Ransomware as the Biggest Threat
The big news of the past few years has been ransomware attacks that have shut down entire companies and even city governments. While these attacks are expected to continue and grow in sophistication, a new, more covert threat is emerging: cryptojacking.
What is cryptojacking? It’s powered by a malicious virus that’s loaded onto unsuspecting computers and mobile devices. The purpose is to hijack your system resources, not your data. The malicious coding allows a remote actor to quietly mine cryptocurrencies in the background using your browser, and you may never know it’s happening. Signs include greatly reduced performance and system overheating with no apparent cause.
5. Attackers Will Become Smarter and Harder to Detect
It seems like most criminals are one step ahead of the law, and cyber criminals are no different. As systems become more sophisticated, hackers will continue to create targeted code that’s more malicious and harder to detect and mitigate.
We’re already seeing variants on older exploits and hacks, and this will only increase in the future as we become more connected and coding sources remain open. Cyber criminals will also continue to base their operations in countries where detection and punishment are rare.
6. State-Sponsored Attacks Will Increase
Government after government reports state attacks on elections systems and infrastructure. Hackers may cause financial loss, but state-sponsored cyber terrorism has the potential to cause widespread, lasting damage to entire communities or even countries. There will also be a rise in disinformation and propaganda, which will only add to the sense of unreality with the widespread use of technology that enables things like Deep Fakes to exist.
7. Your Health and Medical Information are More Vulnerable
Healthcare remains one of the hardest-hit sectors for cyber crime. Medical and insurance information is being used for everything from insurance fraud to blackmailing public officials. As more medical facilities migrate to a digital environment for everything from consultations to patient management, this type of breach will continue to cause harm.
8. Third-Parties Will Become More Prominent, and Risky
Third-party software vendors, and even security consultants, may pose a serious risk to your data and bottom line. One need only look at the recent Capital One breach to see that in action, but SMBs with small budgets are most at-risk. They have limited budgets for tech and services, and so must rely on products like SaaS and IaaS to remain technologically viable in the modern era. This gives them limited control over security and access restriction.
9. The Sticky Problem of AI
AI has the potential to allow paraplegics to walk again and make our working days more productive. But, there’s also the potential for abuse and ethical dilemmas. Advanced technology can improve the quality of life for many, but there are unintended consequences that can leave countless others behind in terms of access and employment. Then, there are legal implications of widespread use – or misuse – of facial recognition and other tech that could invade our privacy or lead to profiling and harassment.
10. Digital Diplomacy Will Become a New International Discipline
All of these problems, and others that are yet developing that we have no space to discuss, will lead to the evolution, by necessity, of digital diplomacy and agreements like the Tech Accord. The goal is to promote collaboration between governments and the tech sector on solutions to combat cyber security and ethical issues that will affect everyone on the planet at some point.
Final Thoughts
Technological advances continue to present a security challenge for IT experts, business leaders, governments, and everyday people. Don’t leave your cyber security as an afterthought. With the knowledge and security tech available to even the smallest companies, there’s no reason to wait until it’s cleanup time to address vulnerabilities within your networks. Knowing where the threats are originating gives you a heads-up about what’s out there. Putting the strongest measures in place to combat them will give you a little peace of mind and preserve your future viability as a business.
About the Author: Sam Bocetta
 Sam Bocetta is a former security analyst for the DoD, having spent 30+ years bolstering Cyber defenses for the Navy. He is now semi-retired, and educates the public about security and privacy technology. Follow Sam @sambocetta
Sam Bocetta is a former security analyst for the DoD, having spent 30+ years bolstering Cyber defenses for the Navy. He is now semi-retired, and educates the public about security and privacy technology. Follow Sam @sambocetta