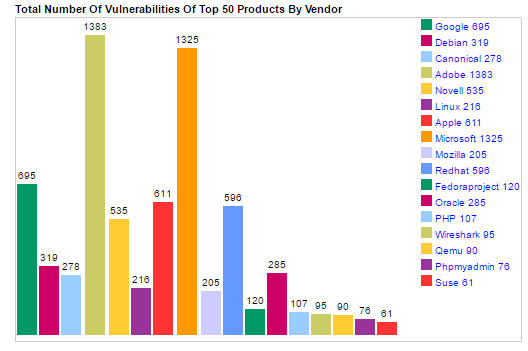
CVE Details has released a detailed list of the top 50 products and vendors mostly affected by vulnerabilities in 2016. In terms of products, the compilation is led by Google’s Android, which has reported a total of 523 vulnerabilities. However, when it comes to vendors, Adobe is on top of the list with 1383 reported flaws.
Related: CVE-2016-7855 Flash Bug Exploited in Limited Attacks
The analysis is based on flaws passing through MITRE’s Common Vulnerabilities and Exposures database. It is indeed quite an accurate dataset – the numbers reveal that a total of 10,098 vulnerabilities were disclosed and assigned numbers throughout 2016. The number can only go bigger if statistics from other databases are included.
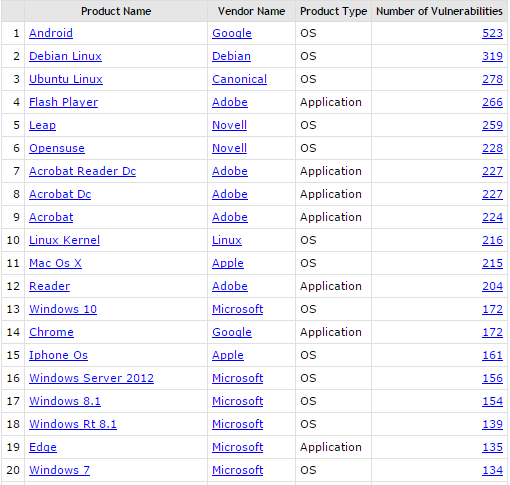
Android is followed by the Debian Linux operating system with 319. Next on the list is Canonical’s Ubuntu Linux with 217. Adobe’s Flash Player is fourth, with 266 reported bugs. To our own surprise, this year Apple’s Mac OS X has a patch load bigger than Microsoft’s Windows 10. Mac OS X has fixed 215 flaws, whereas Windows 10 has patched 172 vulnerabilities. Microsoft Edge, which has been advertised as the most secure browser, is at the 19th position, with 135 issues.
Related: CVE-2016-5195, Plenty of Flaws Fixed in Android’s December Bulletin
Here’s the exact top 20 list, the rest you can check CVE Details’s page:
More about CVEs
Basically, a CVE can be referred as to a catalog of known security threats. As visible by the name, the threats are usually divided into two big sub-categories:
Vulnerabilities.
Basically, vulnerability is nothing but a software mistake that enables a bad actor to attack a system or network by directly accessing it. Vulnerabilities can permit an attacker to act as a super-user or even a system admin and granting him full access privileges.
Exposures.
Exposure is a bit different. It provides a malicious actor with indirect access to a system or a network. An exposure could enable a hacker to harvest sensitive information in a covert manner.
CVEs serve to standardize the way disclosed vulnerabilities and exposures are identified; a process which is quite important to security administrators. Thanks to the standardization, they could access specific technical details about active threats through the CVE information sources.
The CVE database is sponsored by the US Department of Homeland Security and US-CERT. The not-for-profit organization MITRE maintains the CVE catalog and the website that is available to the public. MITRE also manages the CVE Compatibility Program that promotes the use of standard CVE identifiers by authorized CVE Numbering Authorities.