Vulnerabilities, vendors and enterprises. The three words often come together, to the horror of all concerned sites. Enterprises often lack sufficient patch management policy and incident response groups, or disregard the importance of proper education on security-related subjects. Thus, the frequency of zero-day and spear phishing attacks (among others) only seems inevitable.

Vulnerabilities are just like open doors that let malware in a system, program, browser, and sometimes games. Software vendors usually issue a security advisory and patch once a vulnerability is disclosed. However, cyber criminals often have enough time to exploit these weaknesses before the vendor finds out what is going on, or before the necessary patch is released.
In many cases, weeks or months before the vulnerabilities are found pass by, leaving an opened door for exploitation that can continue from several hours to several months. Widely-spread software such as browsers, browser plug-ins and Java/ Adobe Flash products are often prone to vulnerabilities and their malicious exploitation.
If you follow the daily portion of IT security news, you know exactly what we mean. In theory, any organization (both from public and private sectors) can become a victim of a security incident. In practice, there’s a lot to learn and keep in mind in order to spare yourself and your organization from security breaches, or to minimize the damages of such.
Let’s start from the beginning.
CVE 101 – Common Vulnerabilities and Exposures
The good news is there are several big databases that are focused on CVE researching and reporting, such as CVE Details.
First of all, let us explain what a CVE is. The abbreviation stands for Common Vulnerabilities and Exposures.
Basically, a CVE is part of a catalog of known security threats. As visible by the name, the threats are usually divided into two big sub-categories:
Vulnerabilities.
So, how do we understand vulnerabilities? Basically, a vulnerability is nothing but a software mistake that enables a bad actor to attack a system or network by directly accessing it. Vulnerabilities can permit an attacker to act as a super-user or even a system admin by granting him full access privileges.
Exposures.
An exposure is different than a vulnerability. It provides a malicious actor with indirect access to a system or a network. For example, an exposure could enable a hacker to harvest sensitive information in a covert manner.
The CVE Catalog Definition
CVEs serve to standardize the way disclosed vulnerabilities and exposures are identified; a process which is quite important to security administrators. Thanks to the standardization, they could access specific technical details about active threats through the CVE information sources.
The CVE database is sponsored by the US Department of Homeland Security and US-CERT. The not-for-profit organization MITRE maintains the CVE catalog and the website that is available to the public. MITRE also manages the CVE Compatibility Program that promotes the use of standard CVE identifiers by authorized CVE Numbering Authorities.
Here’s a list of the software vendors that are participating as CVE Numbering Authorities:
- Adobe Systems Incorporated (Adobe issues only)
- Apple Inc. (Apple issues only)
- Attachmate (Attachmate/Novell/SUSE/NetIQ issues only)
- BlackBerry (BlackBerry issues only)
- Cisco Systems, Inc. (Cisco issues only)
- Debian GNU/Linux (Linux issues only)
- EMC Corporation (EMC issues only)
- FreeBSD (primarily FreeBSD issues only)
- Google Inc. (Chrome, Chrome OS, and Android Open Source Project issues only)
- Hewlett-Packard Development Company, L.P. (HP issues only)
- IBM Corporation (IBM issues only)
- Microsoft Corporation (Microsoft issues only)
- Mozilla Corporation (Mozilla issues only)
- Oracle (Oracle issues only)
- Red Hat, Inc. (Linux issues only)
- Silicon Graphics, Inc. (SGI issues only)
- Symantec Corporation (Symantec issues only)
- Ubuntu Linux (Linux issues only)
Not any company can participate as a CNA. There are several requirements that need to be met:
First of all, a CNA should be a major software vendor with a significant user base and a particular security advisory capability. The other option to become a CNA is being an established third party that acts as a neutral collaborate between researchers and vendors.
Furthermore, as pointed out by MITRE, the CNA must be a settled distribution point for first-time vulnerability disclosures.
By following the CVE requirement to identify public issues, the CNA must only assign CVE-IDs to security issues that will be made public. Lastly, it must follow liable announcement practices that are widely accepted in security communities. All these requirements serve to make sure no mistakes happen.
The Exploit Database
Another database that should be ‘honored’ is Exploit Database sustained by Offensive Security.
The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software, developed for use by penetration testers and vulnerability researchers. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and present them in a freely-available and easy-to-navigate database. The Exploit Database is a repository for exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away.
The Exploit DB can be used for submitting samples. However, several rules have to be followed in order for the team to accept the submitted information.
Why Are CVE Databases Important? What Is Incident Response?
In November 2013, FireEye pointed out the increasing volume of targeted attacks. Today, industry statistics continue reveal a staggering percent of websites and applications having multiple vulnerabilities. Things are getting even worse, because in 2022, amidst an active cyber warfare, we’re seeing cybercrime be more initiative than ever before, and cybercriminals crafting innovative ways to reach their breach goals. Several years ago, KrebsOnSecurity published an article in which an underground forum called Enigma was revealed. It is only one of a growing community of private cyber crime forums, which have redefined the meaning of targeted attacks. The bid-and-ask forums such as Enigma connect crooks who are looking for access to specific data, resources or systems with capable and motivated malicious coders.
A more recent piece of statistics revealed that there were more than 15 billion user credentials for sale on underground forums. These credentials originated from more than 100,000 data breaches, with at least 5 billion of them being unique.
Despite the fact that spear phishing attacks are currently popular and many people are willing to pay for acquiring sensitive information this way, zero-day exploits shouldn’t be underestimated as well. At the very least, phishing attacks can be pointed at exploiting a particular, known vulnerability.
Why are zero-days so persistent? Google security researcher Maddie Stone pointed out in a presentation during the USENIX’s Enigma 2021 virtual conference that software developers should stop delivering faulty zero-day patches. To prove her point, the researcher shared an overview of the zero-day exploits detected in 2019.
Zero-day vulnerabilities can be exploited for more extended periods of time, making them rather dangerous. Twenty-four such flaws were detected in 2020, four more than the number detected in 2019. Stone noticed that six out of the 24 zero-days of 2020 were variants of previously disclosed flaws. Furthermore, three of the flaws were patched incompletely, making it easy for threat actors to create exploits. In a nutshell, the problem with re-occurring zero-days is that releasing partial patches creates opportunities for hackers to carry out their malicious attacks.
Since such attacks are a daily event in numerous organizations, incident response is a must.
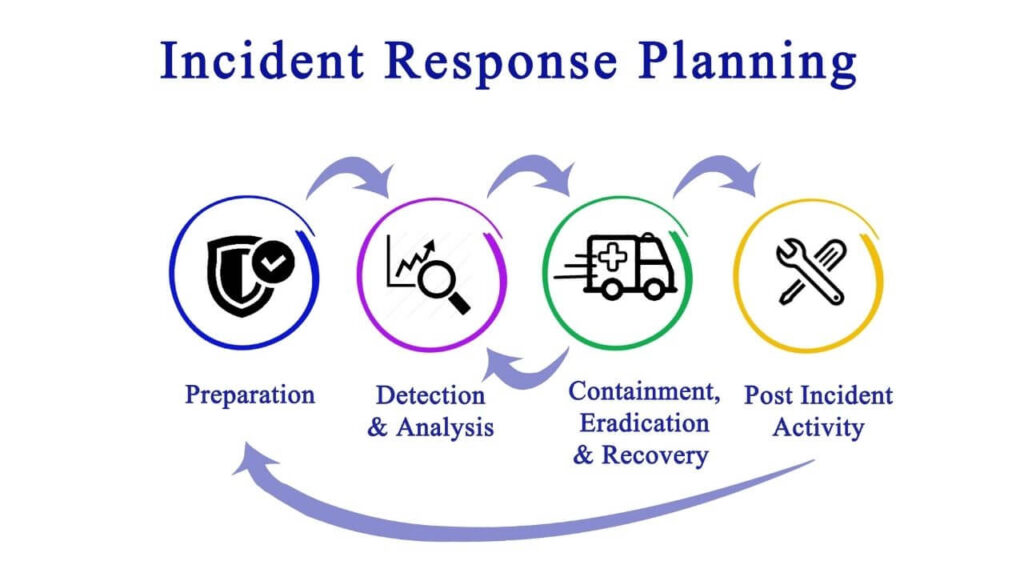
Incident response (IR) is an organized approach to addressing and managing the effects of a security breach. The goal of IR is to deal with the breach in the best way possible by limiting the damage and reducing the recovery expenses. A good incident response plan contains a policy that defines what an incident is and administers a step-by-step tutorial that should be followed strictly when an attack takes place.
The SANS Institute has compiled six steps to dealing with an incident a.k.a. an attack in the most sufficient way:
- Preparation. Enterprises should educate their employees and IT personnel of the importance of updated security measures and train them to respond to computer and network security incidents in a swift and adequate manner.
- Identification. The response team is signaled whenever a possible breach takes place, and should decide whether it is a security incident or something else. The team is often advised to contact the CERT Coordination Center, which tracks and records Internet security activities and collects the most recent information on viruses and worms.
- Containment.The response team decides on the severity and span of the issue. Disconnecting all affected systems and devices to prevent further damage is also applied.
- Eradication. The response team proceeds with the investigation to disclose the origin of the attack. The root cause of the problem and all malicious code leftovers are eradicated.
- Recovery. Data and software are restored from clean backup files, making sure that no vulnerabilities are left. Systems are monitored for any sign of proneness to a flaw.
- Lessons learned.The response team analyzes the attack and the way it was dealt with, and prepares recommendations for better future response and for the sake of incident prevention.


