Bronze President Hackers Behind Massive Cyber Espionage Campaign
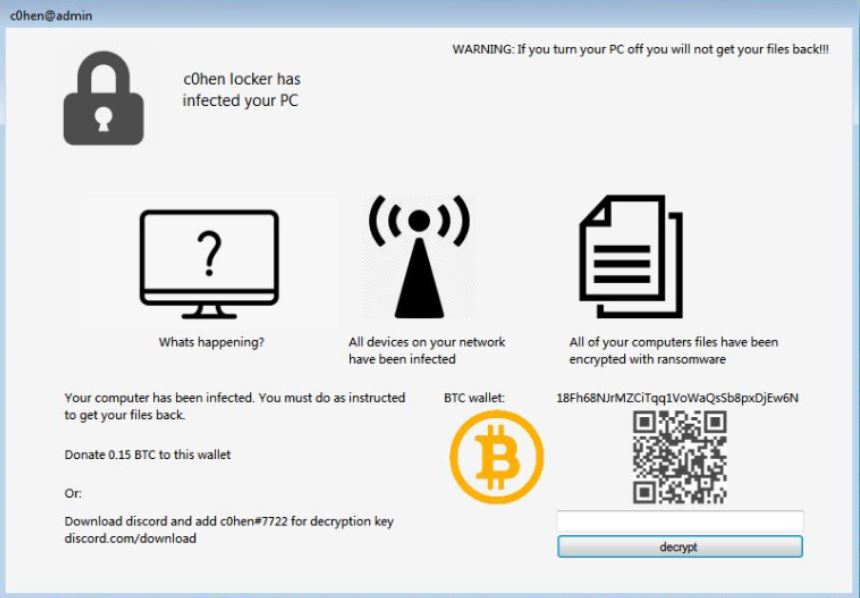
A security research group has uncovered a dangerous hacking group known as Bronze President. Apparently the criminals are responsible for an extensive cyber espionage campaign targeting networks located in Asia. They are using a combination of custom code and publicly…