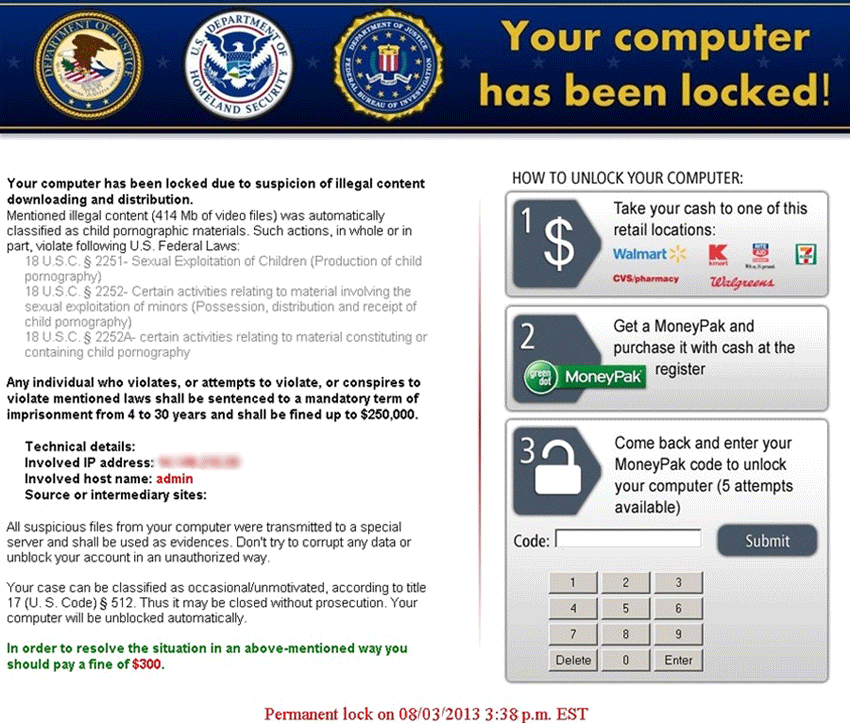
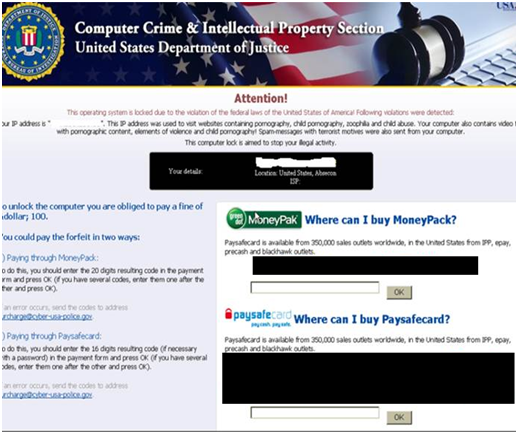
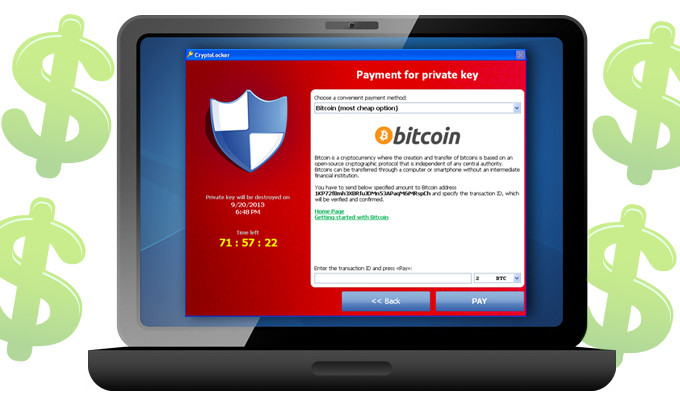
Kyle and Stan Malvertising Network – A New Threat for Windows and Mac Users
Kyle and Stan – A brand new malvertising network has been affecting Windows and Mac users who visit popular webpages such as amazon.com and youtube.com since May this year. The cybercriminals use Yahoo, Amazon and YouTube domains to infect users…