Dridex Trojan Uses New Zero-Day Exploit in Latest Attacks
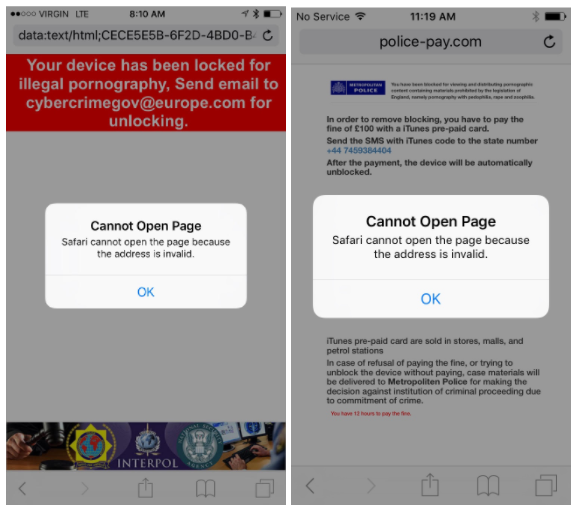
A vulnerability used by the trojan horse Dridex to infect computers has been detected and reported to take advantage of Microsoft Word files. A large e-mail campaign spreading the Dridex trojan horse using a new Microsoft Word exploit has been…