Known for engineering the sophisticated remote access trojans, CypherRAT and CraxsRAT, the EVLF threat actor has revolutionized how cybercriminals infiltrate and exploit Android devices globally. This article delves into the motives driving the development of such potent malware, the global impact on cybersecurity, and the concerted efforts by the cybersecurity community to counter these threats.
Who Is EVLF? A Closer Look at the Creator of CraxsRAT and CypherRAT
EVLF, as identified by cybersecurity experts, is the notorious figure behind the creation of the remote access trojans (RATs) known as CypherRAT and CraxsRAT.
Operating out of Syria, this entity has emerged as a pivotal player in the cybercriminal world, offering malware-as-a-service (MaaS) to various threat actors around the globe. Through a sophisticated online storefront, EVLF has successfully marketed these tools, securing a reputation for innovation in malicious software development.
The EVLF name gained notoriety not just for the tools’ capabilities but also for employing a sales model that made these powerful malware tools accessible to a broad range of cybercriminals, significantly impacting global cybersecurity landscapes.
Deciphering the Motive: Why Create CypherRAT and CraxsRAT?
The development of CypherRAT and CraxsRAT by EVLF was driven by the aim to offer deep access and control over infected devices. These tools are engineered to infiltrate Android operating systems, granting users the ability to commandeer cameras, microphones, and even the device’s location data.
The primary motivation behind creating and distributing these RATs appears to be financial gain, with EVLF selling lifetime licenses to these malware tools and catering to the demand within the cybercriminal community for sophisticated espionage capabilities.
In addition, the ongoing updates and customization options provided suggest a commitment to maintaining the relevance and efficacy of these tools in the constantly evolving cybersecurity landscape.
The Impact of CypherRAT and CraxsRAT Malware on Global Cybersecurity
The infiltration of CypherRAT and CraxsRAT into the cybersecurity ecosystem poses a significant threat to individuals and organizations worldwide. These malware tools have streamlined the process for cybercriminals to obtain sensitive information and exert control over compromised devices.
Their capabilities to bypass Google Play Protect and manipulate infected devices remotely have made Android users particularly vulnerable. The proliferation of these RATs, driven by EVLF’s marketing and distribution efforts, underscores a critical challenge for cybersecurity professionals: the need to adapt to and address the rapidly diversifying tools available to cybercriminals. For users looking to protect their devices, employing comprehensive security solutions can offer robust protection against such sophisticated threats.
How Researchers Traced Back to EVLF
Tracking down the individuals behind cyber threats is a complex process that involves piecing together digital evidence. In the case of EVLF, a notorious malware developer, cybersecurity researchers embarked on a meticulous investigative journey. This section explores the digital footprints that led to the unmasking of EVLF, shedding light on the collaboration within the cybersecurity community that played a pivotal role in identifying the malware developer.
The Digital Footprints That Led to EVLF’s Identification
The trail leading to EVLF began with the investigation of the malware’s architecture and the distribution model. Researchers pinpointed unique coding patterns and operational behaviors in the CypherRAT and CraxsRAT malware strains that were consistent across various attacks.
By examining the malware’s code, they discovered clues hidden within the software’s metadata, such as specific compiler artifacts and unique obfuscation techniques that hinted at a single developer or team. Furthermore, the use of a specific crypto wallet for transaction activities associated with the malware sales provided a crucial financial tie. This wallet, having transactions spanning over three years, was key in tracing back to EVLF.
The breakthrough came when the individual attempted to withdraw a significant amount from this wallet, leading to a direct interaction with the wallet service provider that required identity verification. This request for verification inadvertently left a digital paper trail that researchers could follow.
Also, EVLF’s digital presence extended beyond the malware itself. The operation of a public web shop and the distribution of malware through platforms like GitHub and Telegram provided further evidence. Social media interactions, forum posts, and the response to the freezing of the cryptocurrency funds were all parts of the digital jigsaw puzzle. Each piece provided insights into the operations, motivations, and possible geographical location of EVLF.
Collaboration in the Cybersecurity Community: Unmasking a Malware Developer
The identification of EVLF was not the effort of a single organization. It required a collective endeavor from multiple cybersecurity entities, showcasing the power of collaboration. By sharing findings, tools, and intelligence, researchers could cross-reference data and validate their hypotheses. Platforms like forums, closed groups, and research sharing meetings became conduits for information exchange.
One organization’s discovery of a unique malware signature could be complemented by another’s insight into command and control (C2) server patterns or payment activities associated with the malware’s use. This collaborative approach accelerated the process of connecting the dots, making it increasingly difficult for the malware developer to remain hidden.
Furthermore, public-private partnerships played a critical role. The involvement of cybersecurity firms, academic researchers, and law enforcement agencies across borders formed a formidable network against cybersecurity threats. Their unified strategy towards understanding, tracking, and dismantling the infrastructure of malware operations like those run by EVLF showcases the effectiveness of collective action in cybersecurity. This joint effort not only led to the identification of EVLF but also set a precedent for how the cybersecurity community can come together to tackle threats in the digital age.
The Technical Inner Workings of CypherRAT and CraxsRAT
The landscape of mobile malware is constantly evolving, with cybercriminals developing more sophisticated tools to bypass security measures and exploit vulnerabilities. Among these tools, CypherRAT and CraxsRAT stand out due to their advanced capabilities and the risks they pose to Android users. At the core of both these Remote Access Trojans (RATs) is a highly intricate design aimed at stealth and efficiency. These malwares enable unauthorized access to the victim’s device, allowing attackers to retrieve personal data, monitor user activities, and even control the device remotely without the user’s knowledge.
The Sophistication of CypherRAT Malware
CypherRAT exemplifies the advanced level of threat that modern malware represents.

Beyond just a simple tool for accessing private information, it possesses the ability to interfere with device operations and exfiltrate sensitive data without leaving typical traces of intrusion. This malware takes advantage of various techniques to remain undetected, including the use of encryption to conceal its communications and sophisticated evasion tactics that help it avoid being spotted by antivirus solutions. Its design is focused on minimizing its footprint on the infected device while maximizing its access to valuable data.
Anatomy of CraxsRAT: How It Evades Detection
CraxsRAT, much like CypherRAT, is designed to infiltrate Android devices without alerting users or security tools. It employs a multi-layered obfuscation technique that makes analysis and detection challenging for security professionals. One of the most concerning aspects of CraxsRAT is its ability to bypass Google Play Protect, a security feature meant to block harmful apps from being installed. It does this through sophisticated evasion methods that exploit loopholes in security frameworks.
In addition, CraxsRAT can inject itself into legitimate applications, further masking its presence and making its removal a complex task without specialized tools.
To safeguard against such threats, users are encouraged to download apps only from trusted sources and keep their devices updated. However, in the face of such advanced threats as CraxxRAT and CypherRAT, these measures may not always suffice. For those concerned about the security of their Android devices, employing a reputable security solution can provide an added layer of defense.
Understanding the technical aspects of these RATs highlights the importance of staying vigilant and employing comprehensive security measures. The continuous innovation by cybercriminals demands equally dynamic and effective defense strategies to protect personal and sensitive information from unauthorized access.
Protecting Yourself Against CypherRAT and CraxsRAT
Malware attacks can be devastating, leading to data loss, privacy breaches, and financial damage. However, adopting a preventive stance can minimize your risk. The first step in guarding yourself against threats like CypherRAT and CraxsRAT involves understanding their operation and implementing effective security measures.
Best Practices for Individuals and Organizations to Ward Off Malware Attacks
Ensuring your digital environment remains secure against malware requires a combination of vigilance, good practices, and reliable security tools. Here are essential strategies everyone should adopt:
- Update Regularly: Keeping your software and operating systems up to date is crucial. Developers regularly release patches and updates to fix vulnerabilities that could be exploited by malware.
- Download Wisely: Always download apps and software from official and verified sources. Unofficial platforms often host infected files that can compromise your device.
- Email Caution: Be wary of email attachments and links, especially if they’re from unknown sources. Phishing emails are a common method used by attackers to distribute malware.
- Use Strong Passwords: Enhance your security by using complex passwords and consider employing a reputable password manager to keep track of them.
- Enable Security Features: Make use of your device’s built-in security settings, such as biometric locks for smartphones or encryption options for sensitive data.
- Antivirus Software: Install a reputable antivirus program and ensure it’s always running and updated. Regular scans can detect and isolate harmful software before it can cause damage.
Following these practices creates a solid foundation for cybersecurity but requires consistency and awareness to be truly effective.
Community Efforts in Cybersecurity: The Role of Information Sharing
Combatting cybersecurity threats is a collective effort that benefits significantly from information sharing. By pooling resources and intelligence, the cybersecurity community can enhance its understanding of emerging threats, such as those posed by creators like EVLF. This collaborative approach enables the rapid development of defense mechanisms and security solutions.
Platforms for information exchange, such as industry conferences, online forums, and cybersecurity newsletters, serve as vital channels for disseminating knowledge and best practices. Engaging with these communities can empower individuals and organizations to improve their defenses, ensuring a higher level of protection against potential threats.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
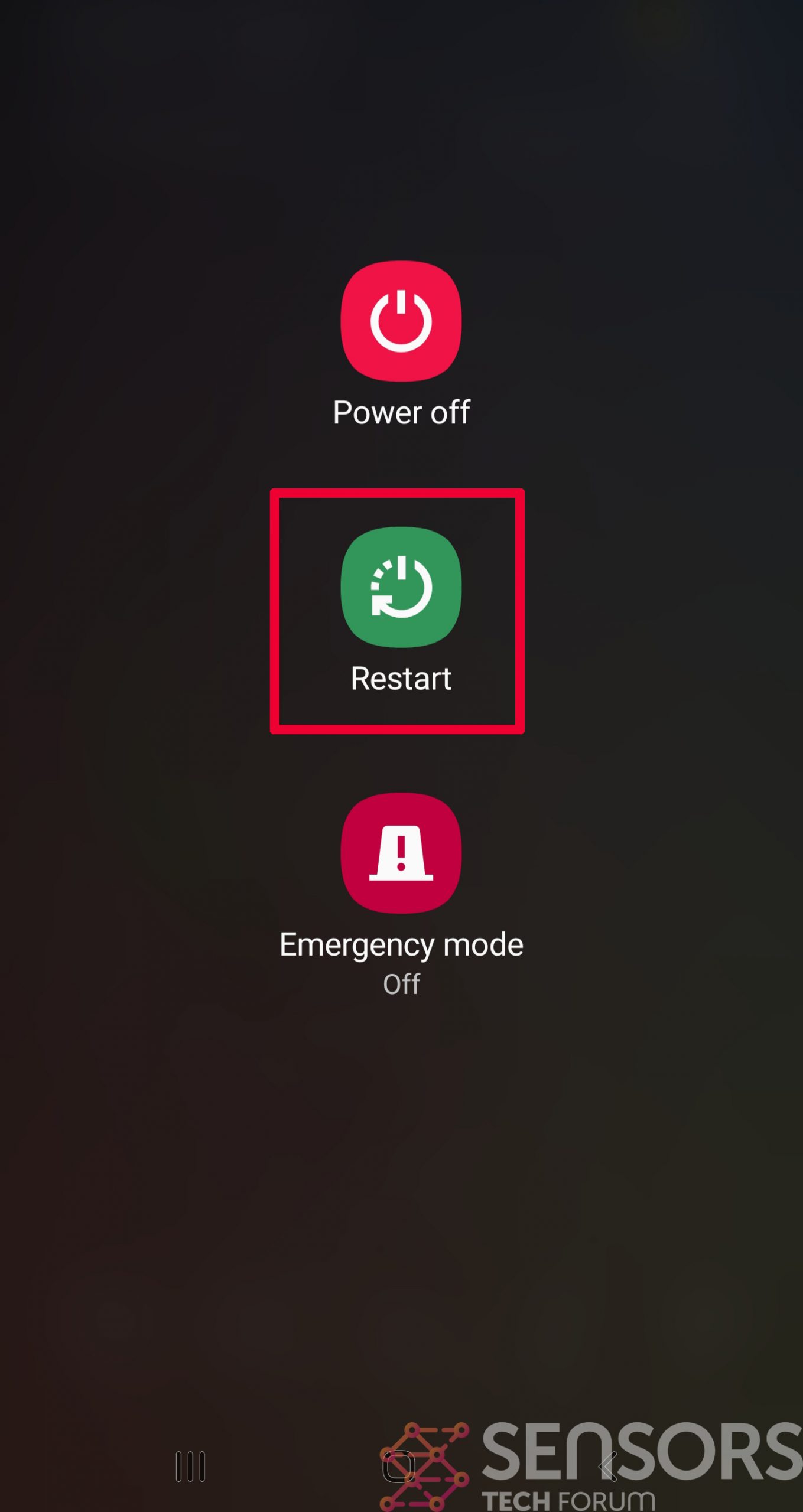
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:
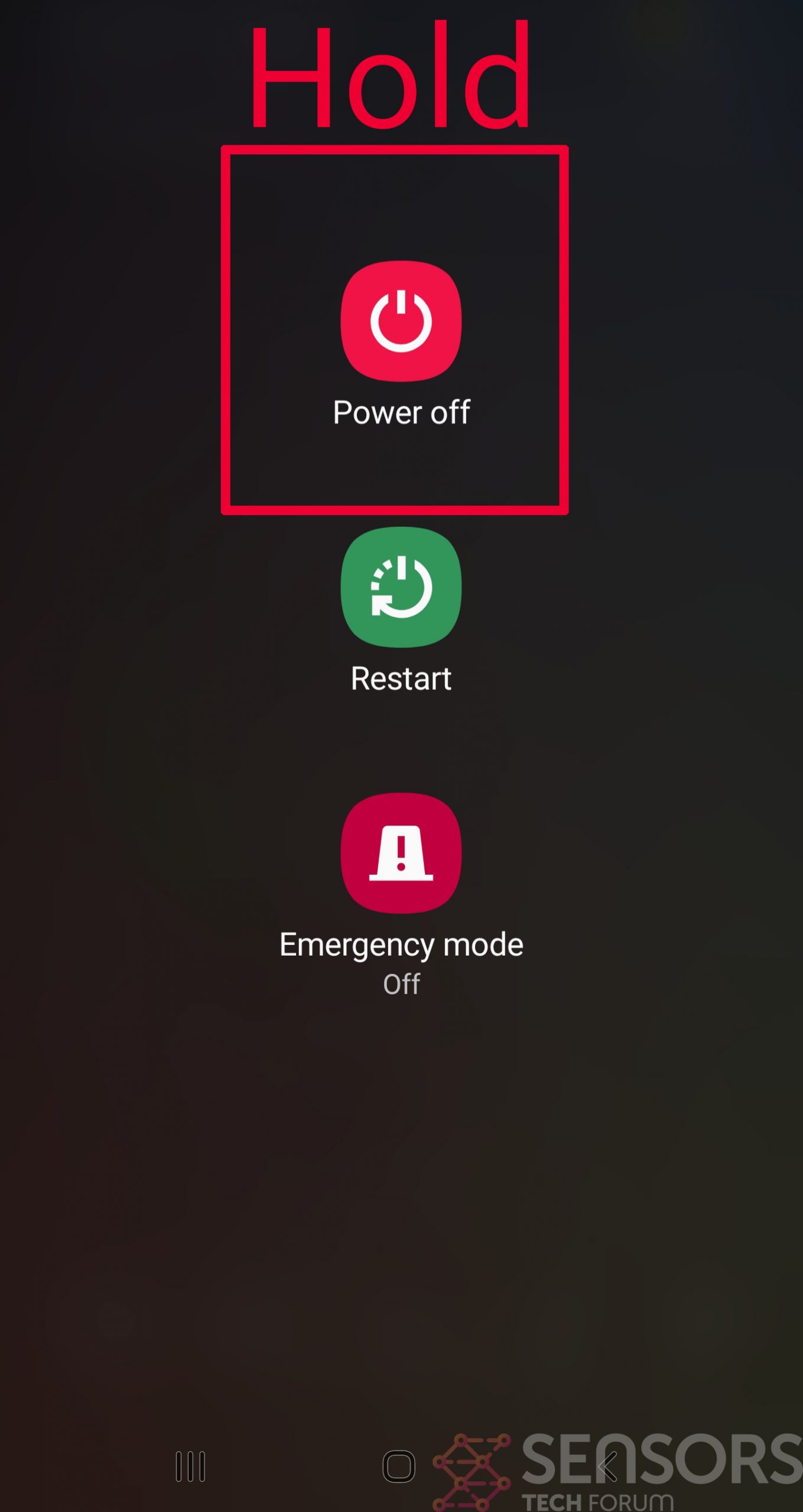
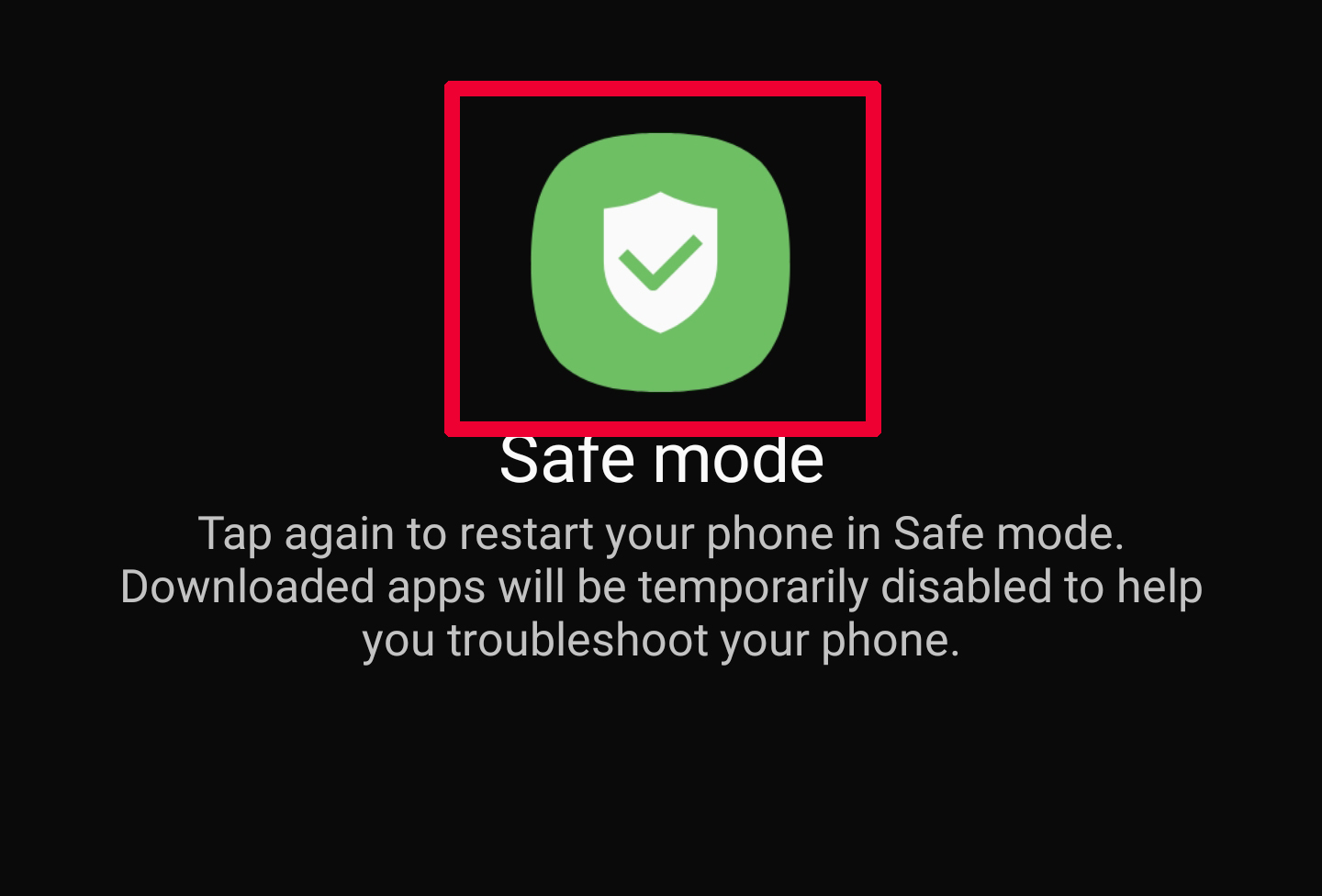

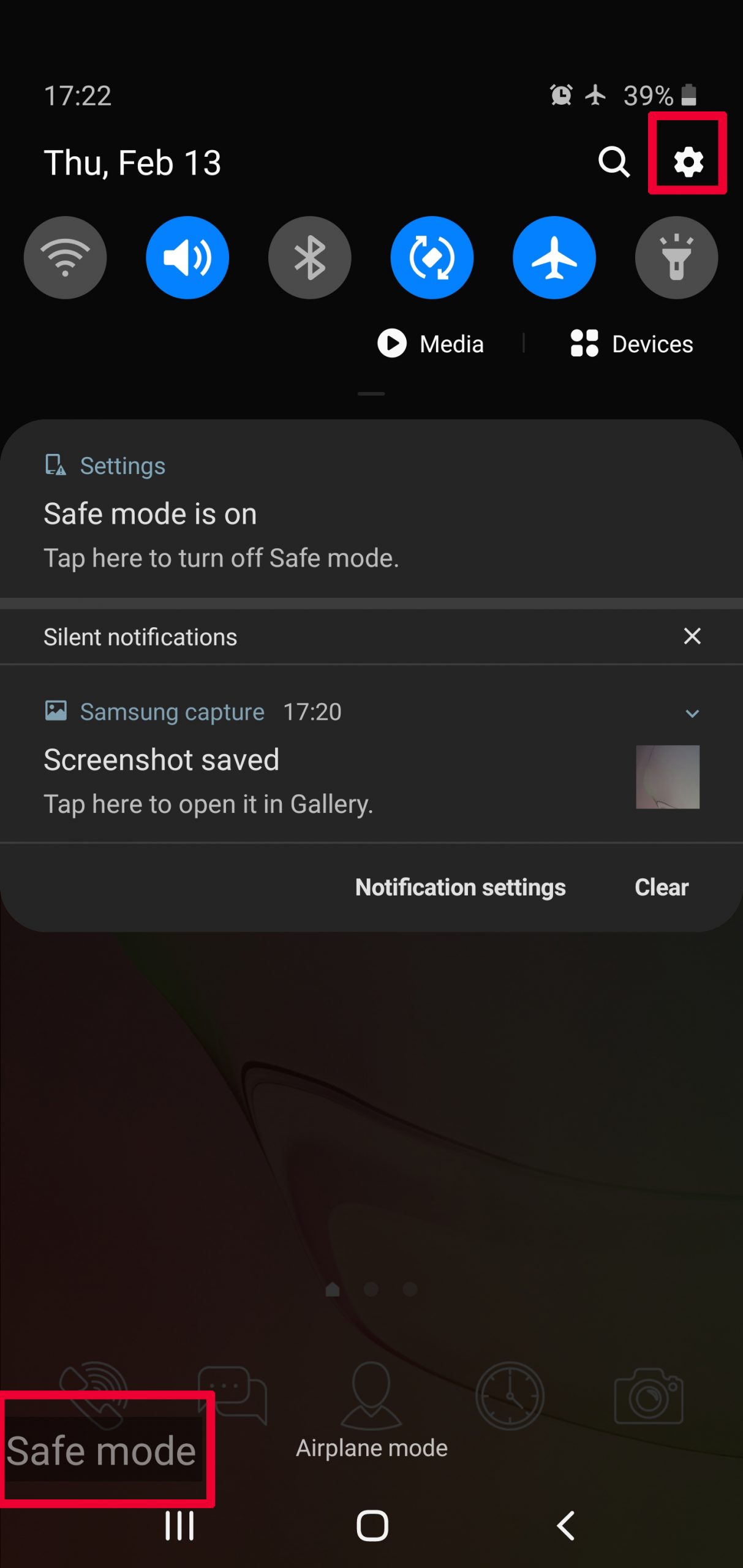
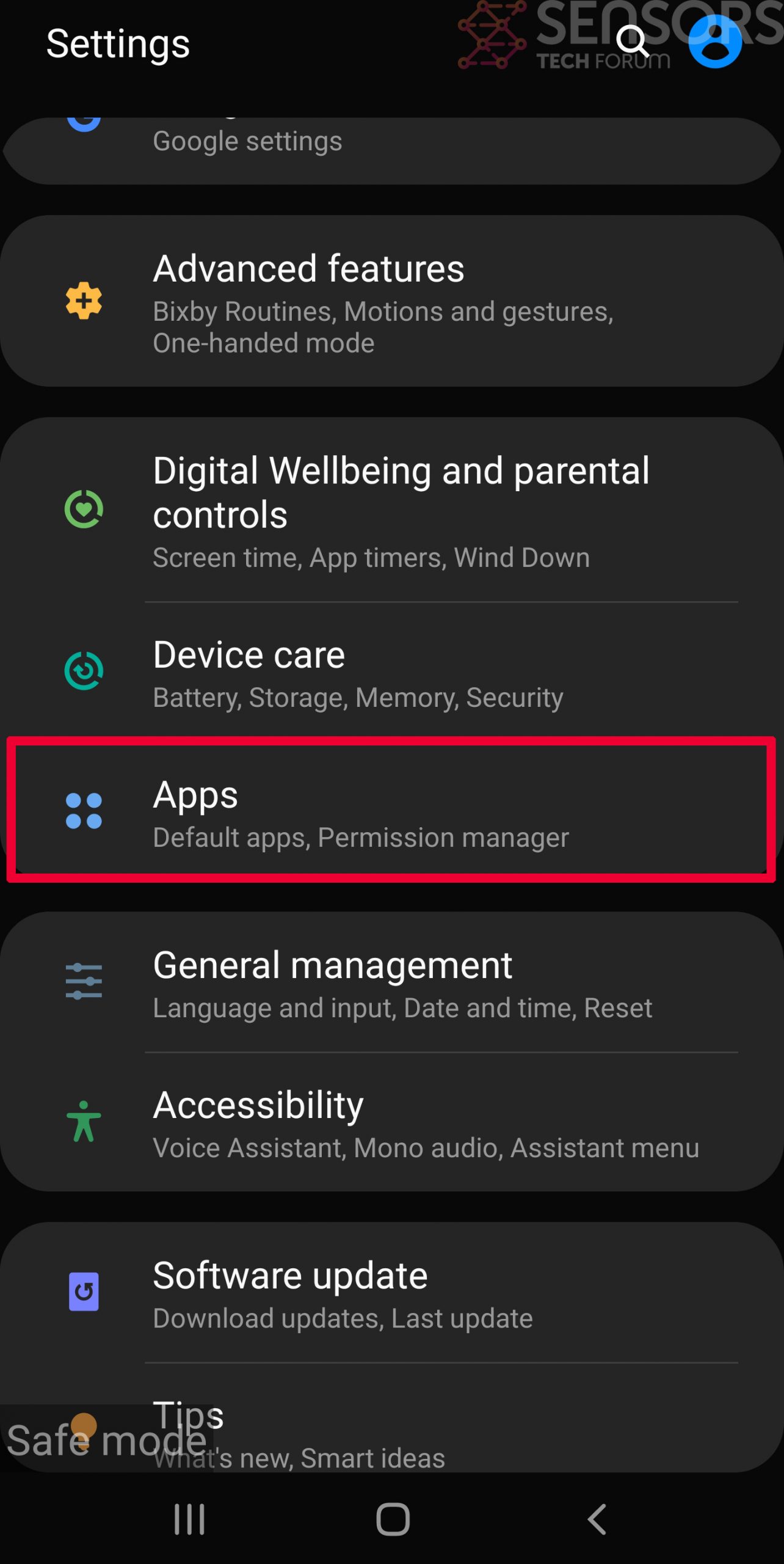
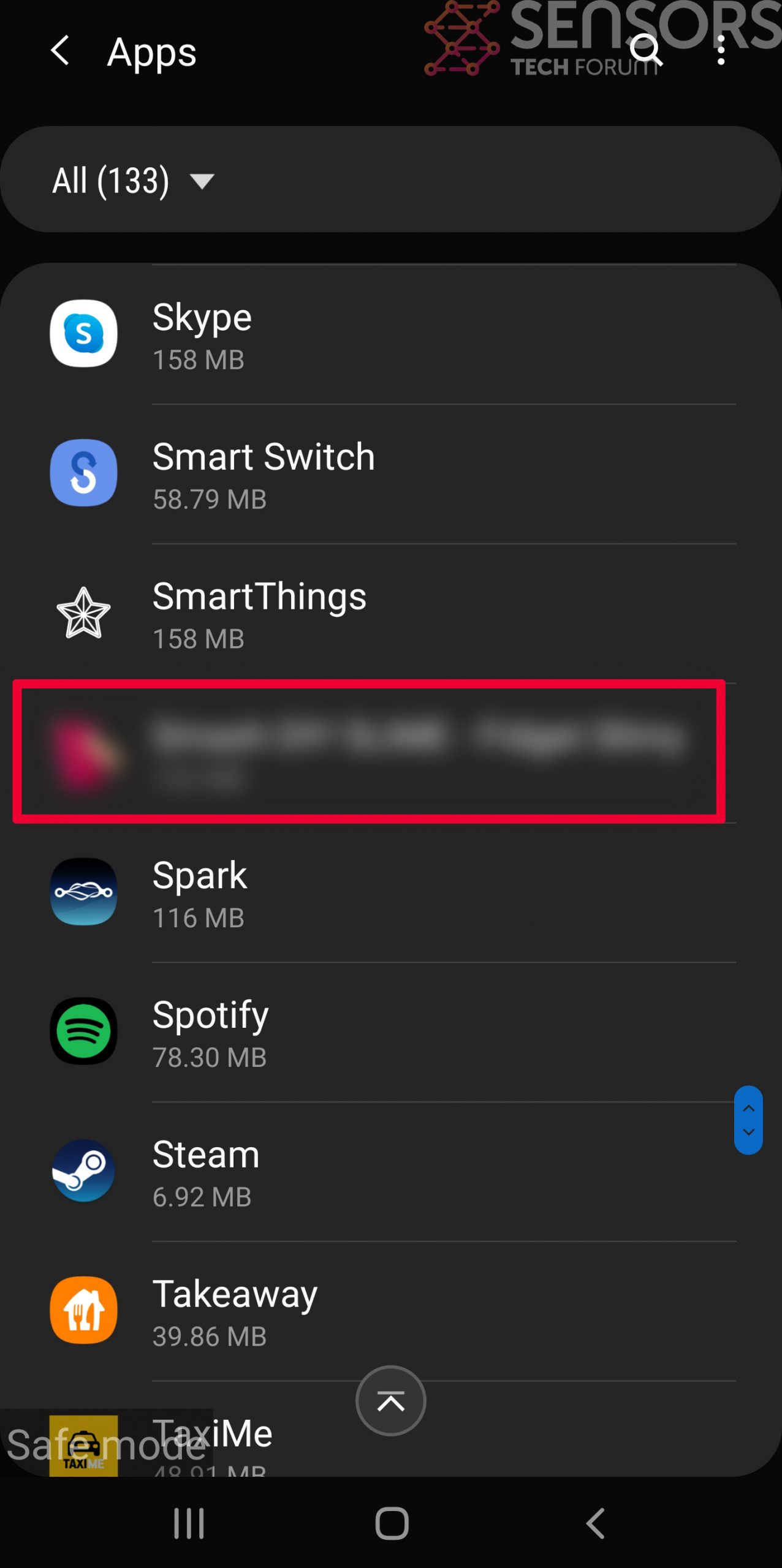
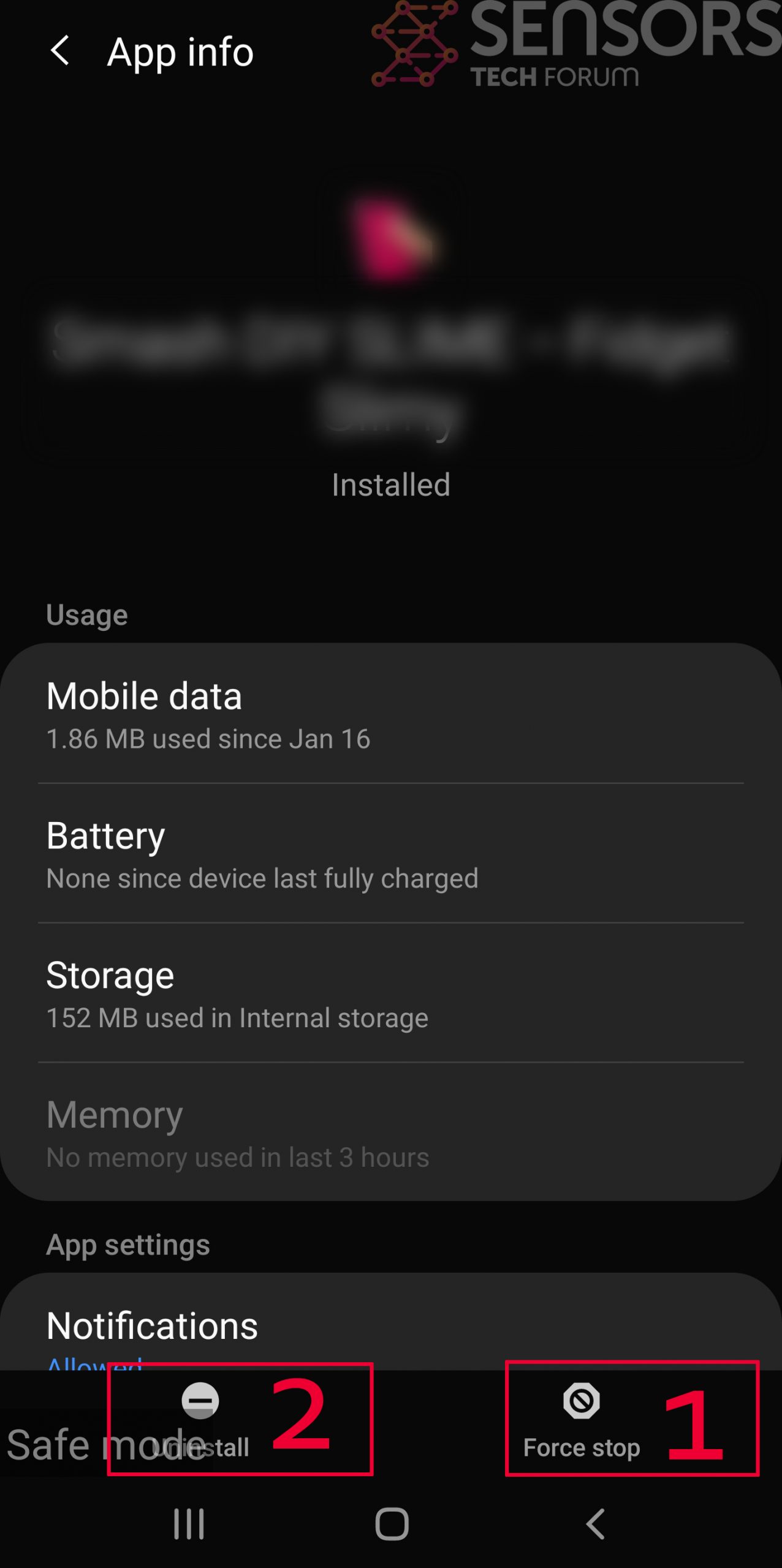
Step 3: Eliminate the App that Your Believe is the Virus
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
Simply locate the virus and hold-tap on the virus file to delete it.


