Another Linux vulnerability has been discovered impacting Snapd, the package installed by default in Ubuntu and used in other distros like Debian, OpenSUSE, Arch Linux, Fedora and Solus. The vulnerability could enable a local attacker to obtain administrator privileges.
This means root access and taking over the system. The vulnerability, identified as CVE-2019-7304 and dubbed “dirty sock exploit” affects Snapd versions 2.28 through 2.37.
CVE-2019-7304 Dirty Sock Exploit: Details
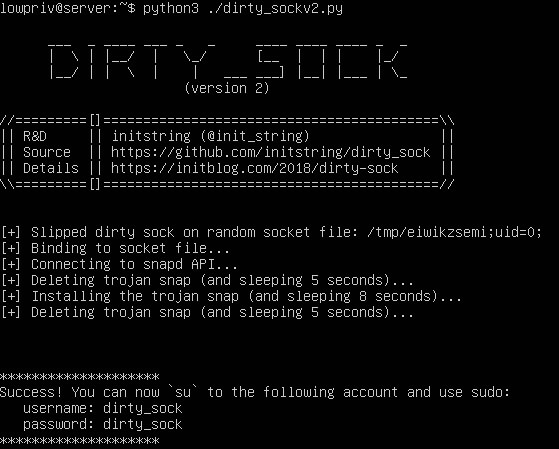
In January 2019, Chris Moberly discovered a privilege escalation vulnerability in default installations of Ubuntu Linux. The issue was triggered by a bug in the snapd API, a default service. Any local user could exploit this vulnerability to obtain immediate root access to the system, Moberly explained.
Here’s the official description of the CVE-2019-7304 vulnerability:
snapd 2.28 through 2.37 incorrectly validated and parsed the remote socket address when performing access controls on its UNIX socket. A local attacker could use this to access privileged socket APIs and obtain administrator privileges.
One of the first things an attacker would do when looking into ways to compromise a machine is to look for hidden services that are running in the context of root. HTTP servers are prime candidates for exploitation, but they are usually found on network sockets. So, there is “a good target for exploitation” – a hidden HTTP service that is likely not widely tested as it is not readily apparent using most automated privilege escalation checks, the researcher noted in his report.
It should be noted that Snapd is becoming a crucial component of Ubuntu, especially in the leaner spins such as Snappy Ubuntu Core for cloud and IoT. Unfortunately, malware has already sneaked in some of these packages. Last May, two packages, 2048buntu and Hextris, uploaded to the Ubuntu Snaps Store by user Nicolas, contained malware.
The vulnerability has already been reported to Canonical in late January. Fortunately, it’s already fixed in Snapd version 2.37.1 and later. Ubuntu and the other impacted Linux distros have already implemented a fixed version of the package.


