WordPress administrators are facing a sophisticated email campaign that leverages fake WordPress security advisories to exploit a non-existent vulnerability, identified as CVE-2023-45124. Security experts from Wordfence and PatchStack have intercepted and reported this malicious campaign, aiming to raise awareness among WordPress users.
CVE-2023-45124: Malicious Campaign Aimed at WordPress Admins
The deceptive emails, disguised as official WordPress communications, falsely notify administrators of a critical remote code execution (RCE) flaw on their sites. The email urges recipients to address the supposed security issue by downloading and installing a plugin provided in the message:
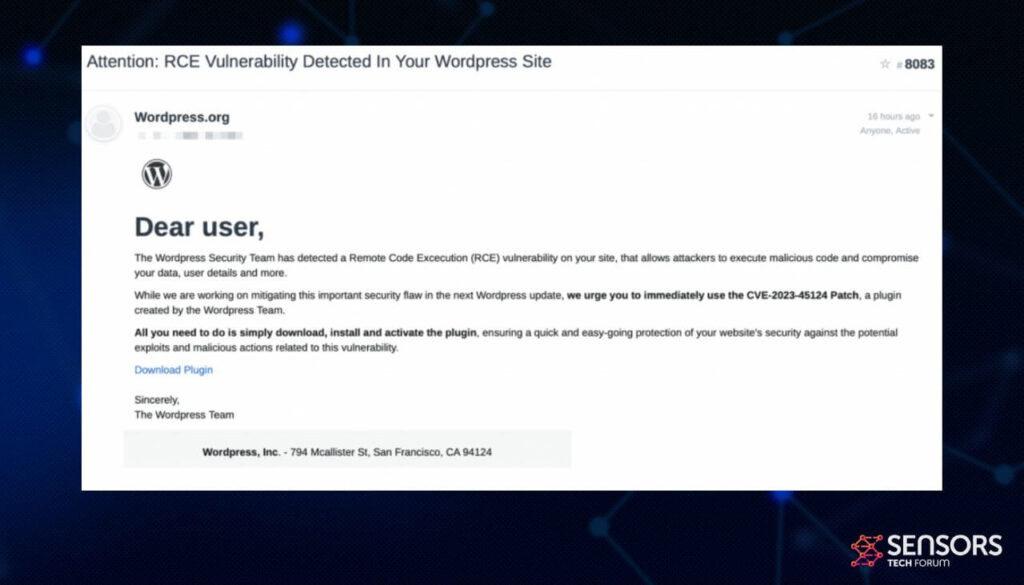
Upon clicking the ‘Download Plugin’ button, victims are directed to a deceptive landing page at ‘en-gb-wordpress[.]org,’ meticulously crafted to resemble the legitimate ‘wordpress.com’ site. The fake landing page features a fraudulent plugin entry, showcasing an inflated download count of 500,000 and fabricated user reviews praising the patch’s efficacy in restoring compromised sites and thwarting hacker attacks.
Once installed, the malicious plugin, disguised as a security patch, creates a hidden admin user named ‘wpsecuritypatch’ and transmits victim information to the attackers’ command and control server (C2) at ‘wpgate[.]zip.’ Subsequently, the plugin downloads a base64-encoded backdoor payload from the C2, saving it as ‘wp-autoload.php’ in the website’s webroot.
The backdoor exhibits sophisticated functionality, including file management capabilities, a SQL client, a PHP console, and a command line terminal. In addition, it divulges detailed information about the server environment to the attackers.
Importantly, the malicious plugin conceals itself from the list of installed plugins, necessitating a manual search in the site’s root directory for removal. While the operational goals of this plugin remain undisclosed, security analysts speculate that it could potentially serve various malicious purposes, such as injecting ads, redirecting visitors, stealing sensitive information, or even blackmailing website owners by threatening to leak database contents.


