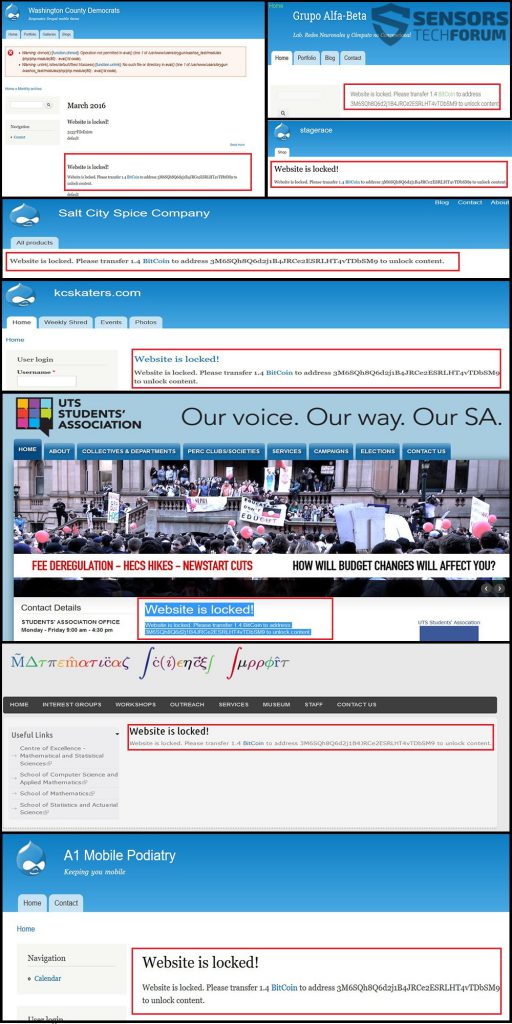
“Website is locked. Please transfer 1.4 BitCoin to address 3M6SQh8Q6d2j1B4JRCe2ESRLHT4vTDbSM9 to unlock content.” – This message is what users and website publishers see after a website is attacked with this nasty web ransomware. It has been reported by malware researchers to take advantage of the open source Drupal content management software. The ransomware locks the entire database of the website restricting access to users and the administrators of the website. To gain access back to the site, Drupal Ransomware demands 1.4 BTC, which is approximately 630 USD as a ransom payoff.
“Website is locked. Please transfer 1.4 BitCoin to address 3M6SQh8Q6d2j1B4JRCe2ESRLHT4vTDbSM9 to unlock content.” – This message is what users and website publishers see after a website is attacked with this nasty web ransomware. It has been reported by malware researchers to take advantage of the open source Drupal content management software. The ransomware locks the entire database of the website restricting access to users and the administrators of the website. To gain access back to the site, Drupal Ransomware demands 1.4 BTC, which is approximately 630 USD as a ransom payoff.

Threat Summary
| Name | “Drupal” Ransomware |
| Type | SQL Ransomware |
| Short Description | The ransomware performs an SQL Injection after which may lock the user out of his database and ask for ransom payment of 1.4 BTC. |
| Symptoms | Files on the database may be encrypted and inaccessible. A ransom note appears on the website’s pages. |
| Distribution Method | Targeted Attack |
| User Experience | Join our forum to Discuss Drupal Ransomware. |

“Drupal” Ransomware and How Does It Infect
This ransomware uses a technique that remains one of the most widely employed versus badly designed websites – an SQL injection attack. It is very effective, mainly because it directly attacks the database. The attack is conducted by attackers in several stages:
Stage 1: Targeting a site.
This is probably the most important stage because the outcome of the infection depends on it. The hackers who have experience with SQL injections are quite aware that they should choose a website which is not so well developed, especially security wise.
Since targeting a site is a time-costly process, experts at Udemy`s Blog have reported that that hackers use a technique called Google Dorking. It is a filtering of websites, based on specific criteria they are looking for, similar to how some spam bots target websites.
Click on the image below to see some recent (at the time of writing) examples of usage of Google “dorking” to find results based on different criteria:
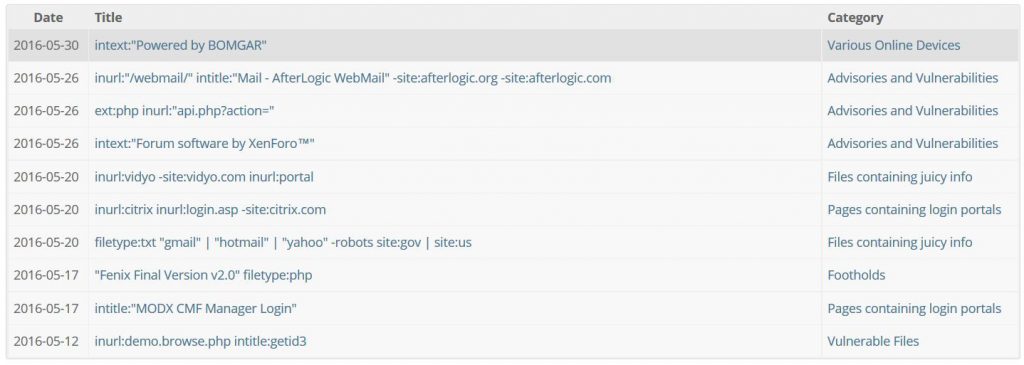 Source: Exploit-DB`s Google Hacking Database
Source: Exploit-DB`s Google Hacking Database
Google Dorking can also be used for the following filterings:
- Vulnerabilities and vulnerable files.
- Footholds that allow hackers to gain access to directories of unsecured web servers.
- Sites containing sensitive directories.(or secret ones)
- Vulnerable servers – servers with specific vulnerabilities which is most likely the type of dorking used by this ransomware.
- Error Messages.
- Network or vulnerability data.
- Different Online Devices.
- Web Server Information.
- Files that have usernames in them.(Only)
- Password files.
There can also be other information that might be found using this method.
After the hackers have bookmarked a list of several websites to attack, they begin to sort them out by looking for vulnerabilities in them. This can happen by simply adding an apostrophe after an index page of a website, for example:
→ Website.com/index.html’
If this website returns an SQL error, then it is vulnerable to an injection attack.
Stage 2: Performing the SQL Injection
This type of attack involves gather SQL information about the SQL database itself, such as trying to guess how many columns it has. After this, such information can be used to a command which can be typed directly on the index. From there, the cyber-crooks can use different tactics depending on what they want to do.

What the “Drupal” Attackers Have Most Likely Done
The attackers may have used malicious SQL injection to gain access to specific information that granted them access to the whole database. From there, they may have performed either encryption of the files or may have directly copied the content of the site onto their server. Either way, they leave the following message on different infected websites:
These websites point out to a very carefully planned attack that aimed for specific vulnerabilities of SQL databases related to websites using Drupal.

“Drupal” Ransomware – Conclusion, Database Restoring, and Prevention
If you have become a victim of this nasty attack, you have several options:
- To restore the files if you have a backup of your database somewhere.
- To contact the provider of your hosting and ask for any backups that they may have to your website.
- To hire a data recovery specialist to help you establish if the files are still in the database and if they can be decrypted if encoded with a cipher.
Either way, this is not a cyber-threat that fools around. Given the type of data which it encodes, we may see such attacks to become more widespread in the future. This is one of the reasons we strongly advise AGAINST paying any ransom money to cyber-criminals.
It is also a good practice to have a reliable anti-malware tool if you are working on a compromised website, because the criminals may have set malware to infect other devices that use the website.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter