Security professionals detected a massive attack against Facebook users with a distinct virus that is being distributed via Google Chrome hacks and malicious tactics. The attack uses several stages of malicious JavaScript code that is injected into the browser. Social engineering attacks are being used and the virus can penetrate other browsers as well. Google Chrome users were found to be the most popular target of the hackers.
New Facebook Virus Attack Overview
The Facebook malware uses social engineering tactics to win the trust of the intended victims. The initial spread is through messages using the Messenger service. The worrying fact about the ongoing attack is that the original source of the accounts is not known. There are two main potential causes for the large number of reported infections:
- Browser Hijackers ‒ Counterfeit extensions for the most popular web browsers are constantly being made by computer criminals. Their aim is to confuse the victims into installing them posing as useful add-ons. Most of them are readily released for Mozilla Firefox, Google Chrome, Internet Explorer, Microsoft Edge, Opera and others. Once installed they harvest sensitive information about the victims including their private data: account credentials, passwords, history, form data, bookmarks and settings. In addition the hackers can monitor the activity and behavior of the users or install other malware.
- Malicious Sites ‒ The Facebook virus can spread through malicious scripts injected into the users computers. They are usually found on hacker-controlled sites or ads that pose as legitimate services or impose lucrative offers.
Detected instances that feature the Facebook malware use complex scripts and algorithms that are rated as advanced. The security engineers found out that depending on the attained sample it may produce different effects on the infected computer.
Facebook Virus Example Infections
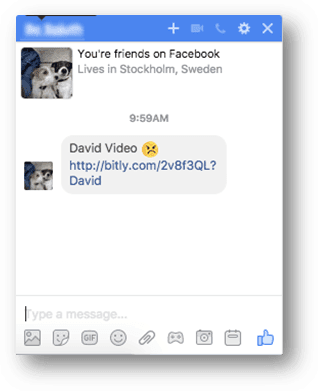
One of the most popular ways of getting infected is by clicking on a link sent by a counterfeit or hacked Facebook profile. The message will pop-up via the Facebook Messenger. It will lead directly to the malware or a hacker-controlled page which in turn delivers the threat. An example message reads “David Video” and points to a Google Docs document. The name of the person may be different or chosen at random using a readily available list. Once the victims open the link they are directed to open it. Beware that the link can be both in its full format or shortened using a service (such as bit.ly). A recent example of dangerous virus infections through similar tactics has been detected in the OhNo Ransomware.
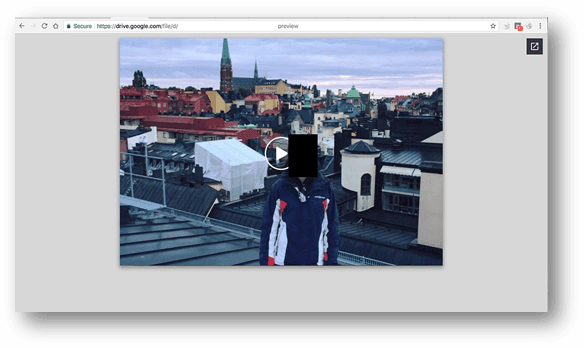
This displays an image that appears as a fake video with the hacker user’s profile picture placed inside the frame. In turn this redirects the users to a fake YouTube page that opens up a notification prompt asking the users to install a Google Chrome Web extension. This is one of the probable sources of the ongoing attacks. Once the dangerous malware has been installed on the victim machine it can be used by the hackers to spread additional threats or control the system at will.
Its interesting to note that the impact caused by Google Chrome seems to be the largest. The hackers analyze the used web browser and have programmed different consequences depending on the used software.
Users of Mozilla Firefox the open-source app will find that their browser will be redirected to a landing page chosen at random. The hackers use templates to generate a large number of sites that all contain a fake Adobe Flash update prompt. When interaction is made with it a malicious executable is downloaded to the computer which can be chosen by the hackers. It may be a browser redirect, virus or a dangerous ransomware instance.
The Mac OS X Safari version of the Facebook virus redirects to a very similar page that is customized to appeal to such users. Instead of the usual .exe file the JavaScript code downloads a .dmg file containing adware code.
The social network has long been the target of computer hackers as it is one of the most popular Internet services. The criminals attempt to both abuse, copy or fake it as part of their tactics to spread computer viruses to the intended targets. So far computer experts have been able to identify several different popular types of Facebook viruses along with specific removal instructions.
Consequences of a Facebook Virus Infiltration
A successful infection can lead to privacy and security incidents on the local machine and all other devices found on the network. The detected samples show that it is possible to download a predefined set of threats. Depending on the attack goals of the criminals behind the operation the following consequences can take place:
- Malware Delivery ‒ The hacker operators can choose to infect the compromised hosts with customized malware or ransomware samples. Effectively this allows the perpetrators to use the Facebook virus as an effective way of spreading the threats.
- Trojan Operations ‒ A trojan module can be instituted on the victim machines which makes it possible for the hackers to remote control it at all times.
- Information Harvesting ‒ As part of the payload module the Facebook virus executable can extract sensitive information from the infected machine. This includes both system hardware data, software configuration settings and user credentials stolen from applications, usually web browsers.
- Botnet Recruitment ‒ Hacked computers can be recruited to a worldwide botnet capable of inflicting attacks against predefined hosts.
The hackers have implemented stealth protection by means of programming the Facebook virus to only function if run by the criminal routine. The background process will download the malicious program if it is triggered by the Google Chrome store obtained from the Webstore. If it is installed separately from the Webstore it will not run in the usual routine.
The security experts noted that the Facebook virus code contains references to another script in obfuscated form. This reveals a sequence that is initiated after the infection with the Google Chrome extension has been made. All loaded tabs are injected with a “listener” script. When a new tab is loaded a request to a hacker-controlled site is made. If the remote servers are configured to respond to the signal then a hacker-orchestrated action will follow.
Succesful infiltrations caused by the Facebook virus lead to the creation of malware-infested messages that are sent to friends of the hacked victim.
Facebook Virus Attack a Highlight for the Last Quarter
The second quarter of 2017 is noteworthy for mass email spam messages and other schemes that employ primarily social engineering tricks. The aim of the hacker operators is to confuse the intended victims and make them infect themselves with the payloads ‒ usually ransomware and other virus instances.
In the last several years the security experts note that there is a rise of fake notifications and pop-up scams that all lead to hacker-controlled sites redirecting to computer viruses. Financial and banking Trojans are on the rise as criminal groups worldwide are attempting to steal valuable personal data and credit card information. Recently identity theft and spying have become as prevalent as financial abuse, criminally-obtained data on targets can have an ever higher price than ordinary credit card numbers if sold to the right dealer on the underground markets.
All of this has lead to the development and coordination of large-scale attacks both against end users and company and even government networks. The prevalence of phishing messages that come in various shapes and forms ‒ from redirect pages to template emails. All of them are made with the same goal, to direct dangerous viruses and ransomware to the victims.
This Facebook virus sample indicates that computer hackers worldwide are continuing the tradition of implementing complex infection schemes. Stay protected by always employing an effective security anti-spyware solution.

How to Remove the Facebook Virus and Protect Your Computer
The Google Chrome security team has been able to effectively disable the detected signatures related to malicious web extensions from the Chrome Web Store. However all infected victims will have their Facebook access tokens stolen from the browsers. This effectively allows hackers to gain access to the profiles of the victims.
The use of a quality anti-spyware solution can effectively safeguard against an incoming attack. A powerful deep system scan can reveal active infections on a host system, they can be removed with a few mouse clicks by the user.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter