 News have recently broken out that the same hacking group who have been detected to spread the malware, known as “Olympic Destroyer” to still be active and targeting different threat prevention facilities all over Europe and financial facilities in Russia.
News have recently broken out that the same hacking group who have been detected to spread the malware, known as “Olympic Destroyer” to still be active and targeting different threat prevention facilities all over Europe and financial facilities in Russia.
The malware has first gained popularity back during the Winter Olympic Games held in Pyeongchang, SouthKorea. Back then, it was quickly established that the malicious code is a part of a cyber-sabotage hack which is spreading a destructive worm and is most likely targeting organizations’ networks in order to conduct reconnaissance and also self-replicate while remaining undetected. Security experts have reported the malware to be a part of a very well organized operation. But even though the hack was organized, the attackers behind this malware have made some pretty serious mistakes which helped users to detect and also prove evidence of the hack.
The Activity and End Goal of Olympic Destroyer
The Olympic Destroyer’s goal was to enter organizations and look for digital signatures and forge these signatures in order to make it seem as if the malware was made by Lazarus APT, a hacking entity, believed t be from North Korea. However, security researchers quickly came down to the conclusion that the malware may not have been made by Lazarus at all. In addition to this, the malware was linked to several Chinese hackers as it has code from different threat actors, like the some people who were behind BadRabbit and the famous Netya ransomware viruses.
Furthermore, researchers have concluded that the infection procedure of the new variant of the Olympic Destroyer has been made to be more sophisticated than before, but in terms of infection methods, it was optimized and simplified by the attackers. It is now using the following technologies to infect systems and self-propagate:
- VBA code.
- Powershell.
- MS HTA.
- JavaScript.
- PowerShell.
One particular recent infection file according to malware researchers’ reports was a Microsoft Word document, called Spiez CONVERGENCE.doc, which in fact, contains malicious macros. These macros infect victims once they accept the content editing after opening the documents. In addition to this, researchers also report that the macros themselves were heavily obfuscated, meaning that they can not be easily detected. Here is how such an infection process works:
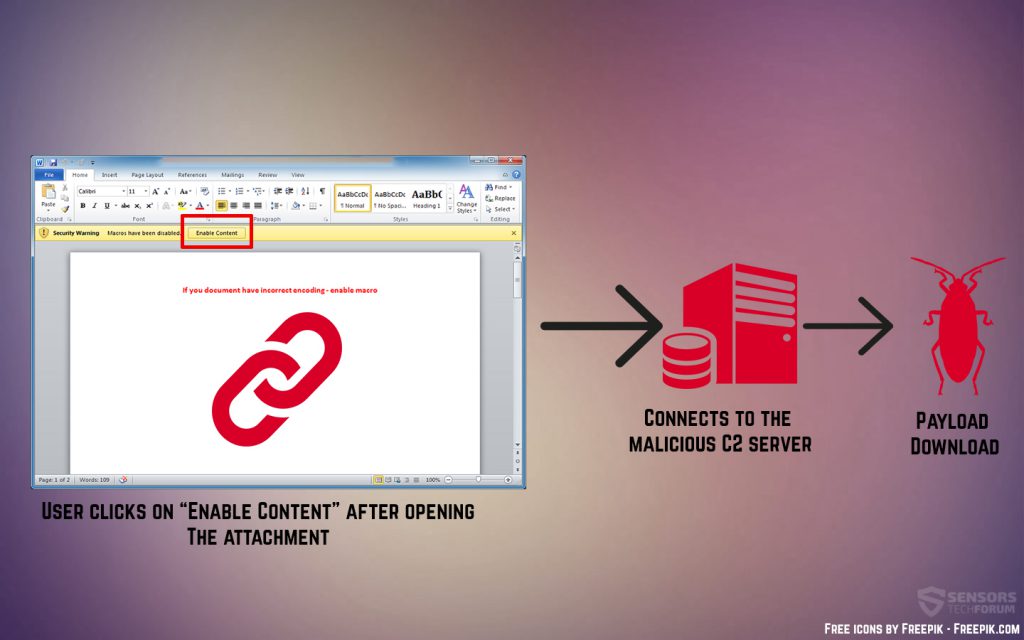
Once the victim triggers the macros, they execute a command in Powrshell. This command is also hidden and the infected system does not show indication of being infected. Once the script has been injected, it runs a new Powershell script. After this a so-called “array-based rearranging” occurs, which mutates the original code and hides all of the commands being executed to protect the hacker. For example, one thing that this may hide is the hacker’s IP address, or more specifically that of the command and control server.
After this is done, the malware uses a backdoor to take control of the victim’s computer as a part of a completed Stage 1 of infection. Then, it’s second stage is to execute a Stage 2 infection malware which runs an even bigger Poweshell scrip which downloads another payload file. Tis file is known as Powershell empire and it is an open source project, written in the Python language and Powershell language. IT allows the hacker to control compromised computers remotely without any form of files residing on the infected computers. What is interesting is that researchers claim that these types of hacking techniques that are file-less are often used by pen-testing companies in order to provide hacking for testing of the strength of a given company. In reality, the tool is effectively used with the main purpose of information stealing.
What Should Be Done?
According to researchers, it is very important to secure all of the ports on networks and learn how to effectively protect your organization from spear-phishing and malicious e-mail campaigns, since these types of worm infections may not only be fileless, but they may also spread automatically once the first infection on the organization network takes place. And with another big sports event already taking place, the Fifa World Cup 2018, there have already been infection campaigns ,related to the world cup by threat actors.


