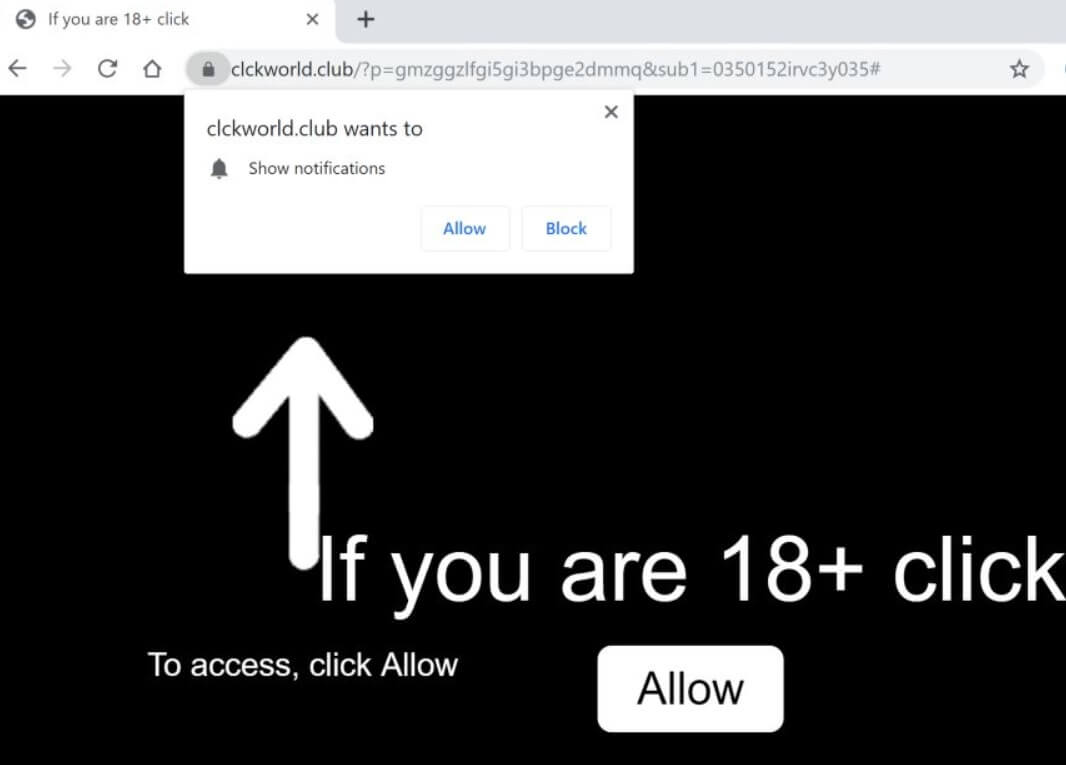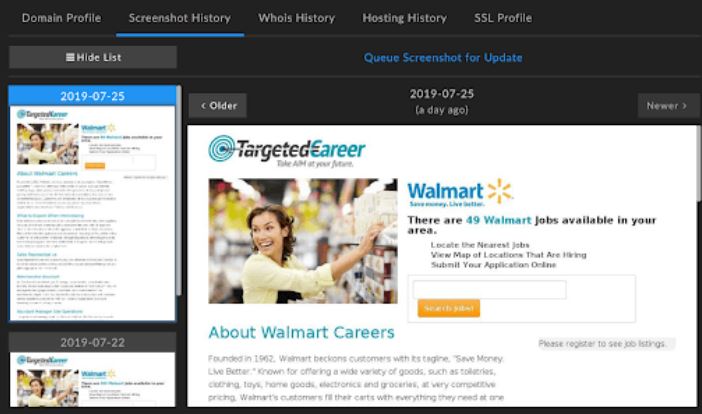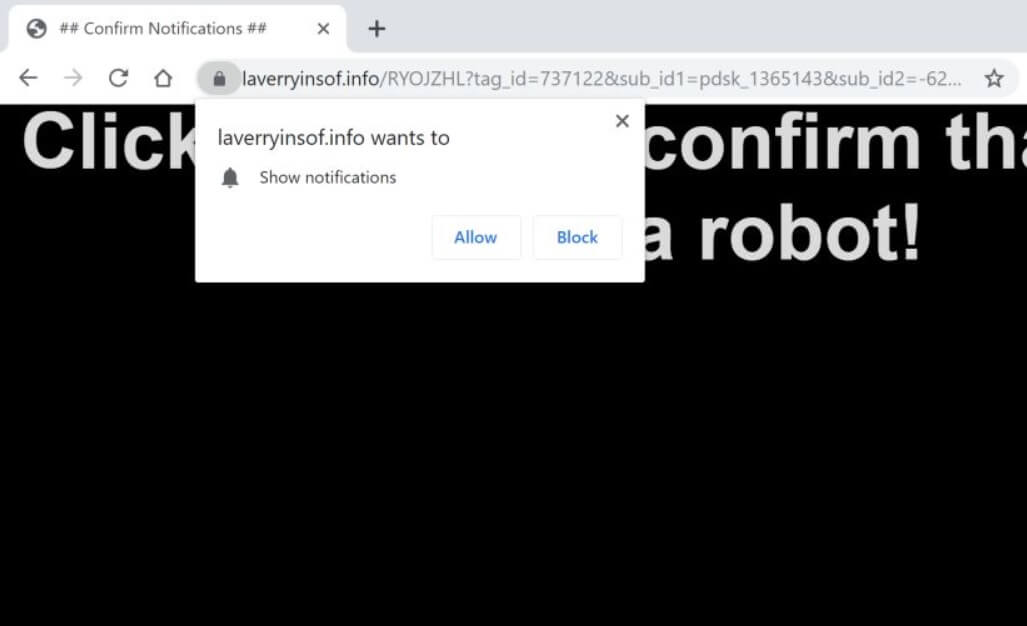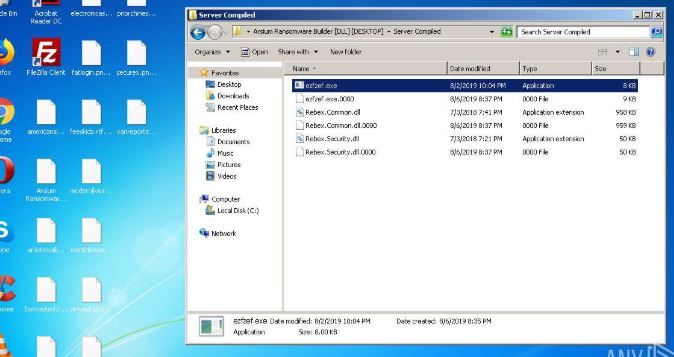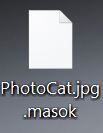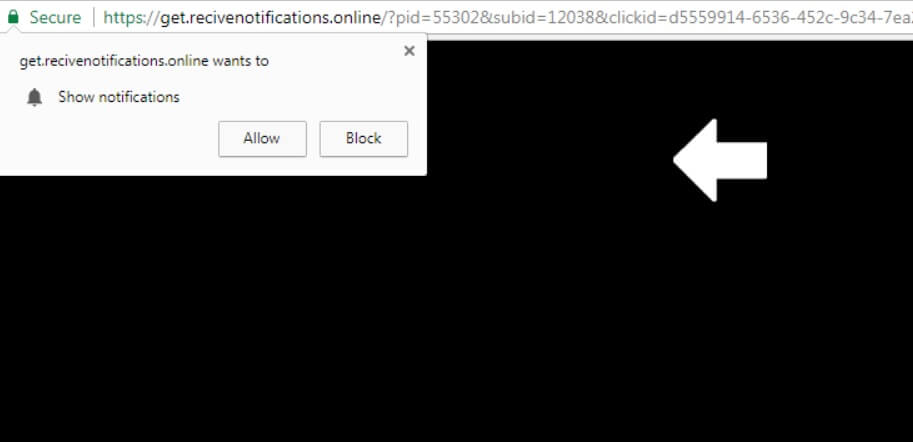
Remove Recivenotifications.online Notifications
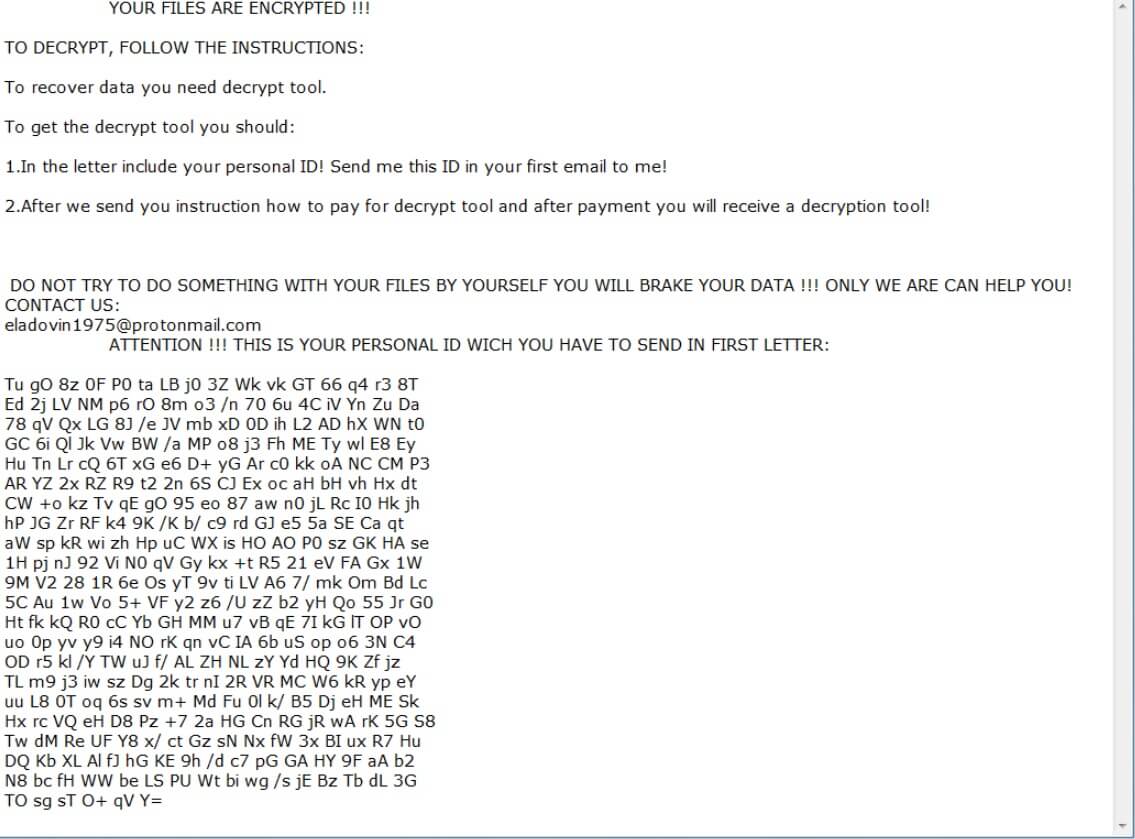
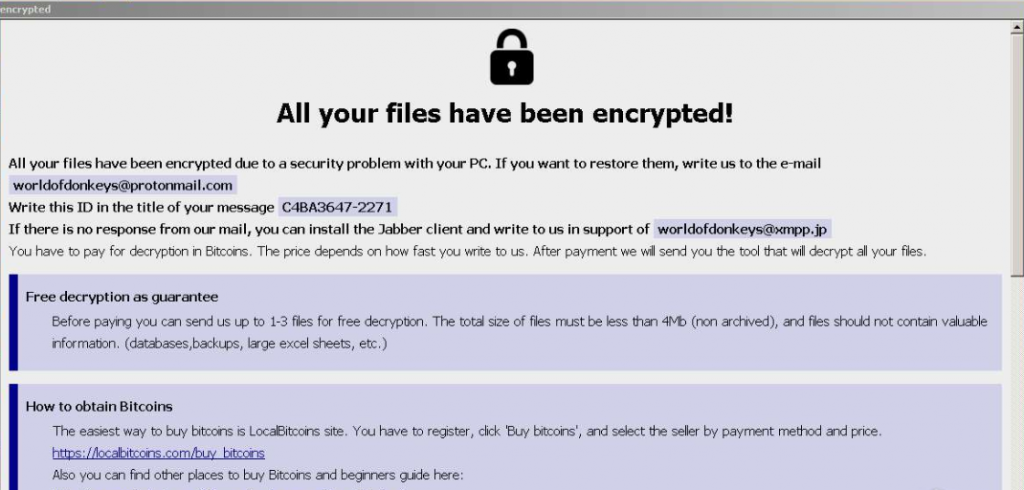
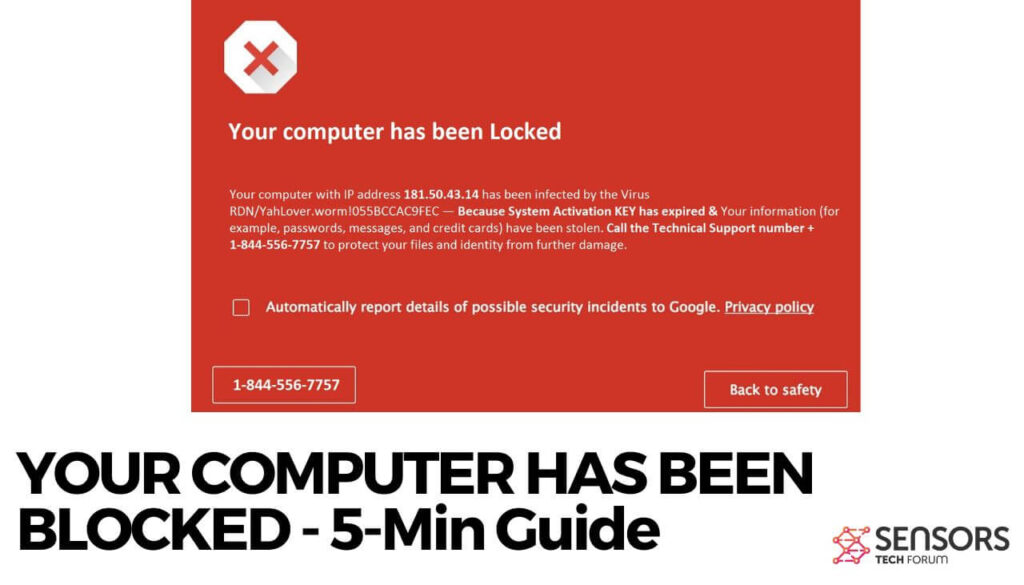
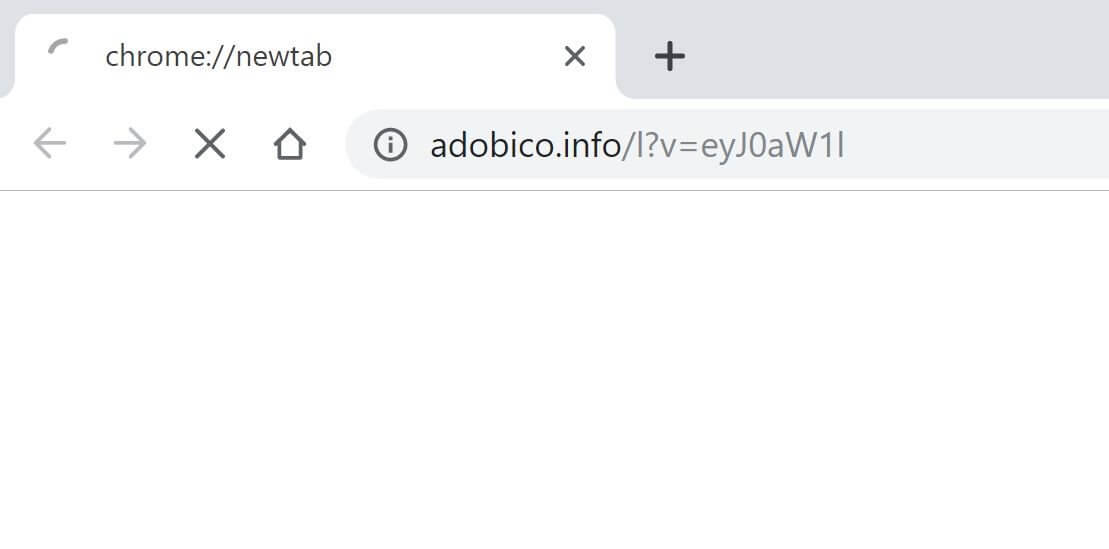
Recivenotifications.online push notifications can affect your browser. Recivenotifications.online will show ads, pop-ups, wanting you to allow permissions. Recivenotifications.online is a malicious URL address used for the purposes of redirecting users and showing push notifications. Some users believe it is a…