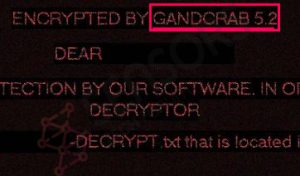
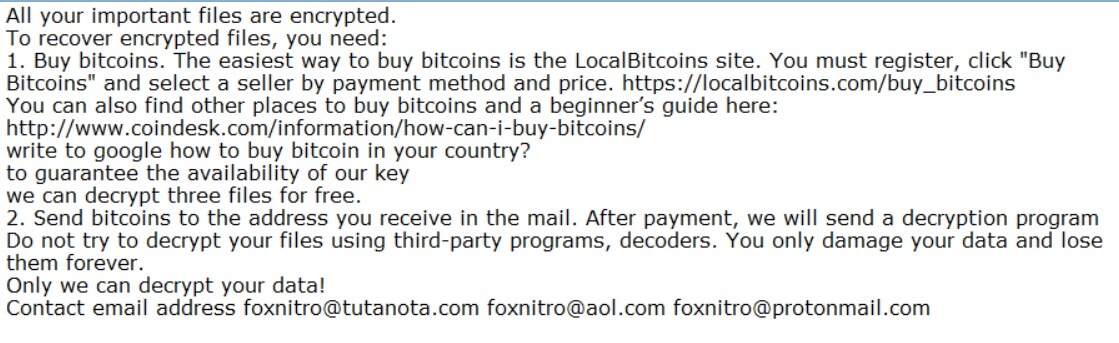
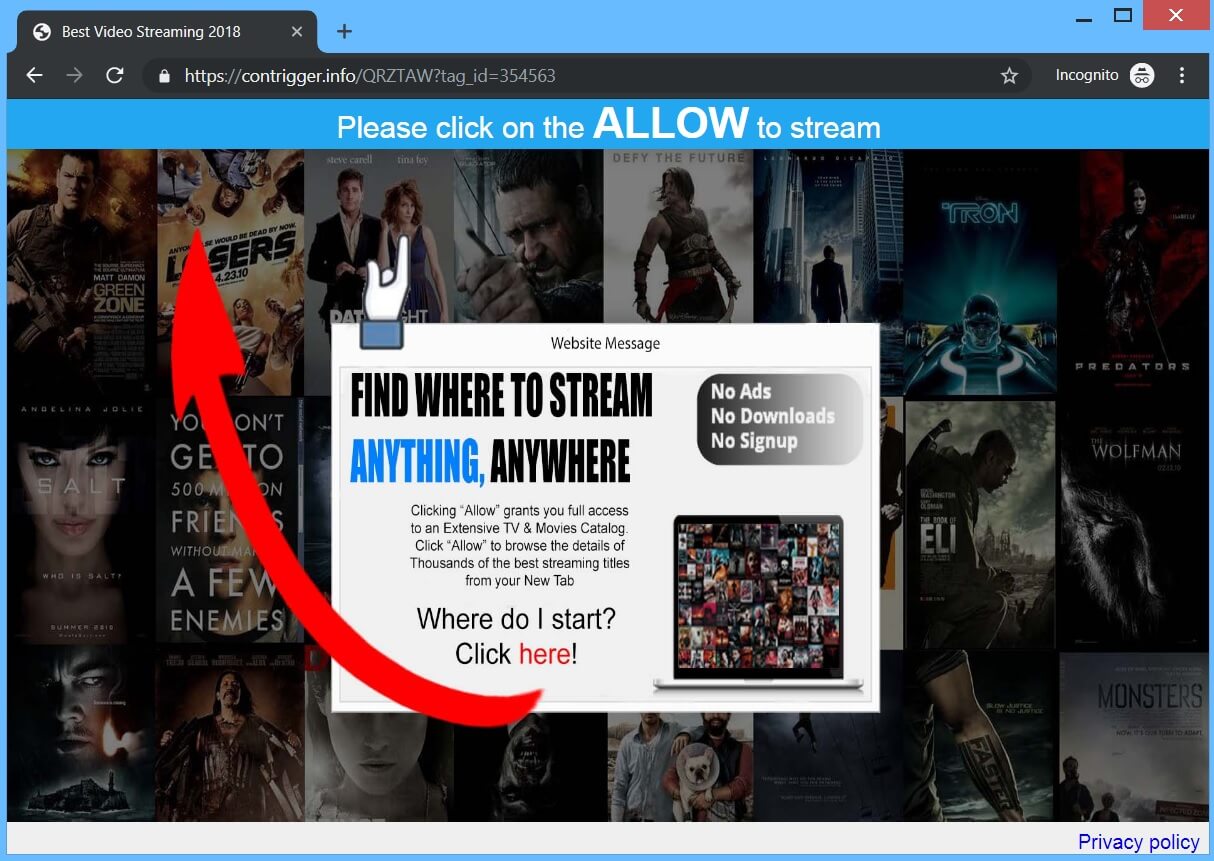
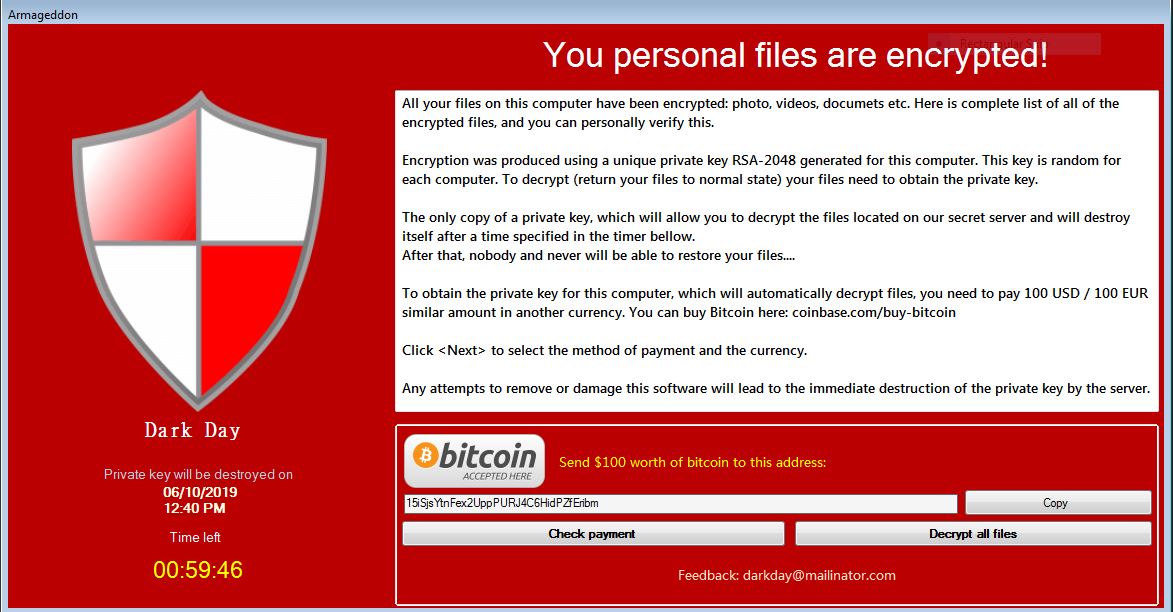
Landpage.co Facebook Virus – How to Remove It
Update July 2019! What is Landpage.co? Is landpage.co a virus? Can you get a virus through Facebook Messenger? SIDENOTE: This post was originally published in June 2019. But we gave it an update in July 2019 The domain Landpage.co was…




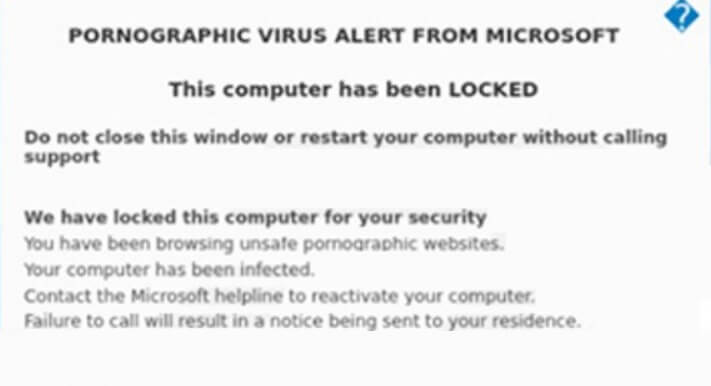



![[LOCKED] Files Virus – Remove It stf-LOCKED-virus-ransom](https://cdn.sensorstechforum.com/wp-content/uploads/2019/06/stf-LOCKED-virus-ransom-note.jpg)