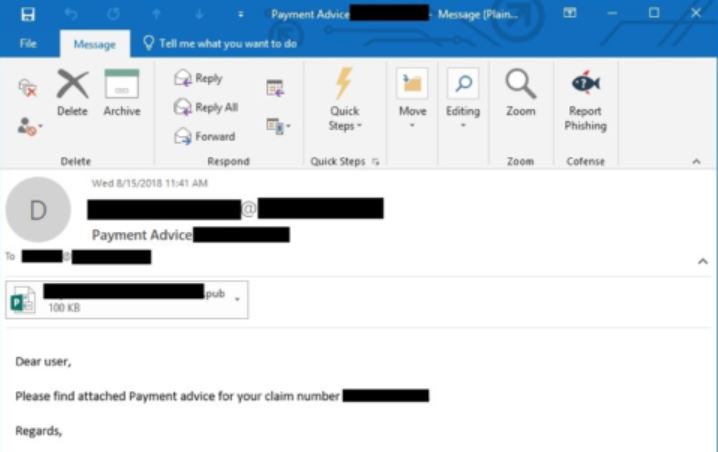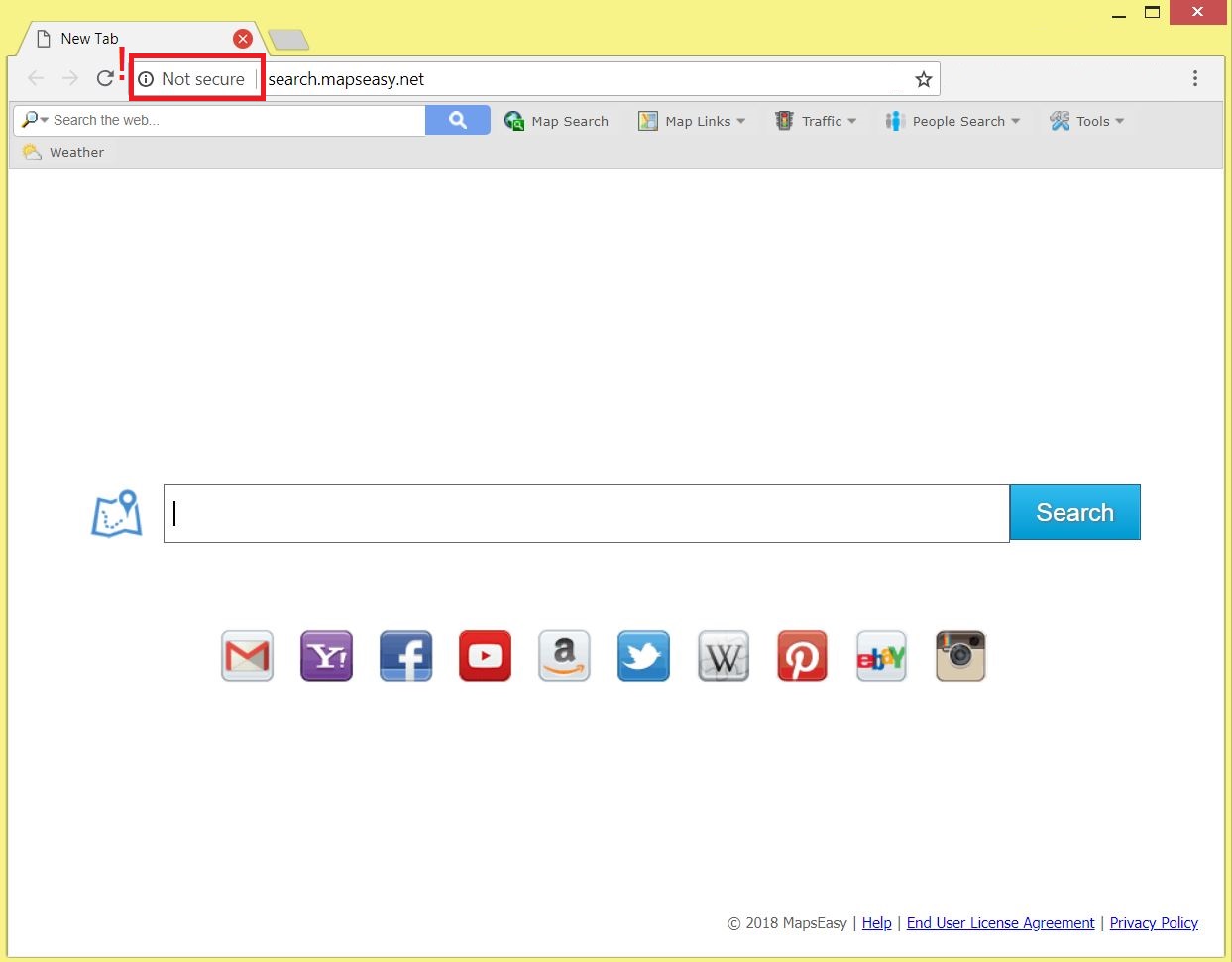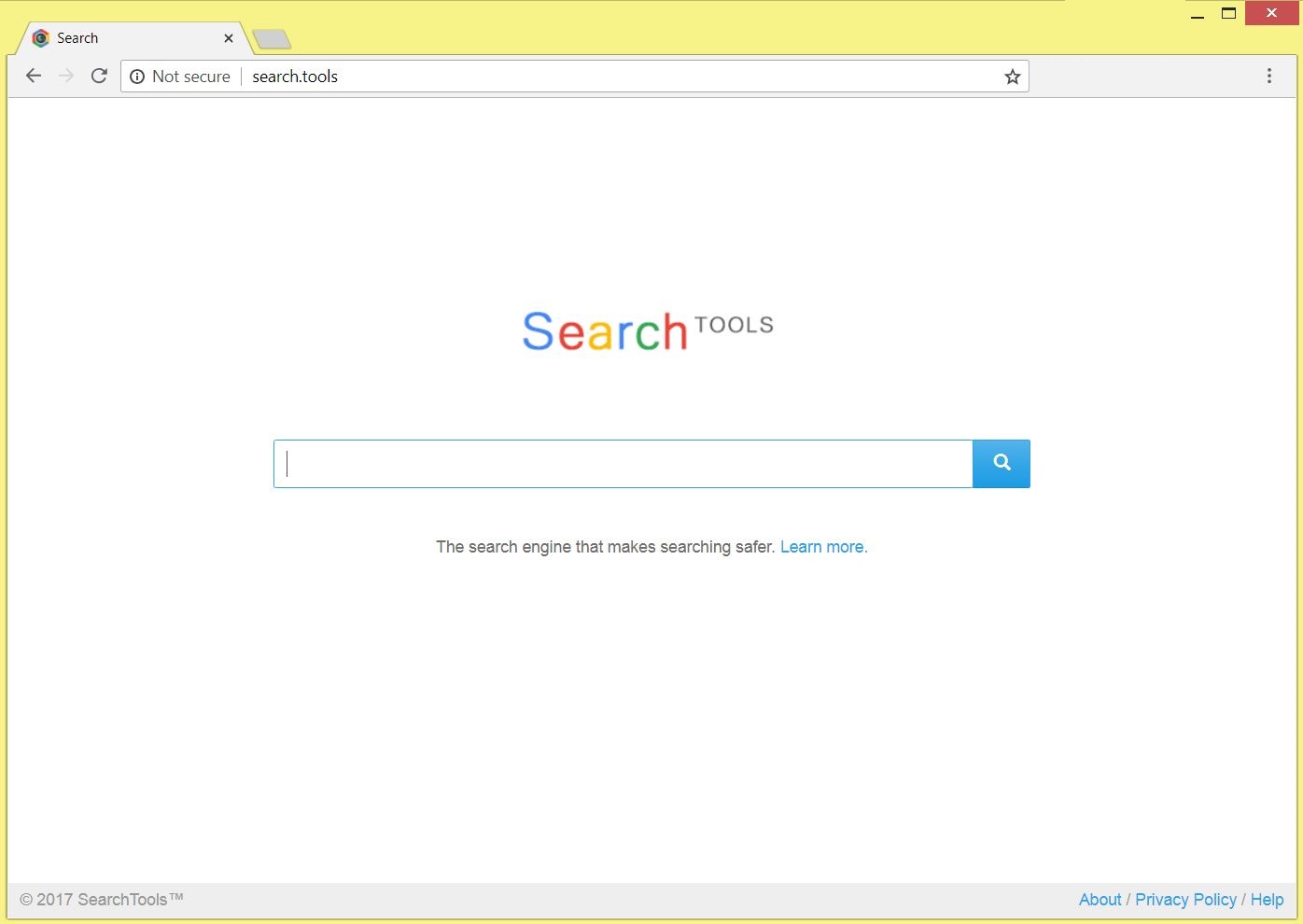
How to Remove Search.tools Hijacker
This article reveals more about the impacts of Search.tools hijacker and guides you through its thorough removal process from affected browser and system. Search.tools is classified as a browser hijacker that alters main settings of the browsers installed on affected…