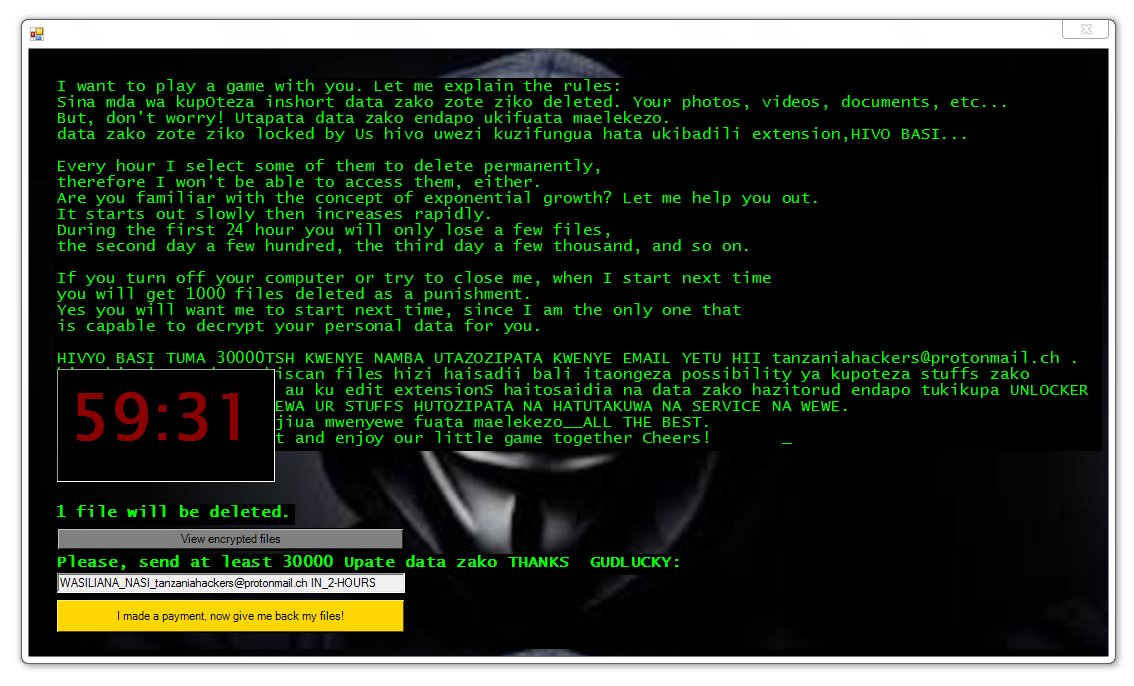
.locked_by_mR_Anonymous(TZ_HACKERS) Files Virus – Remove
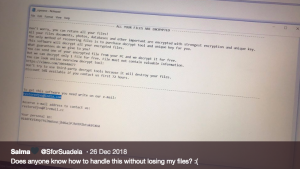
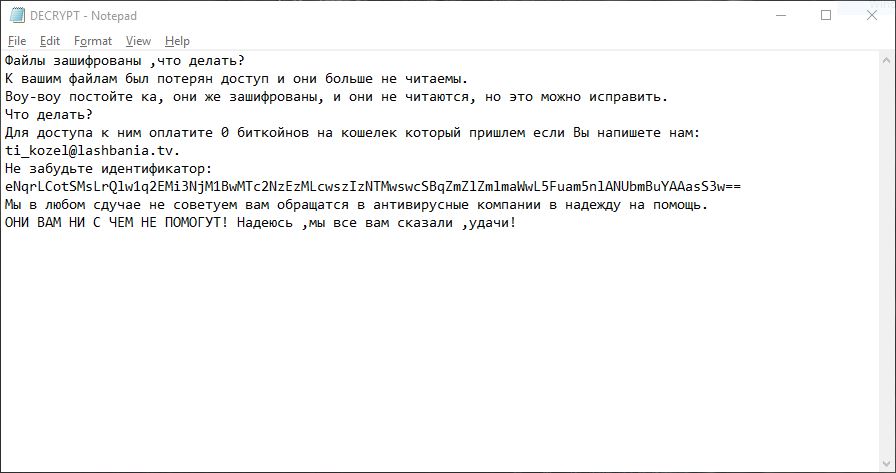
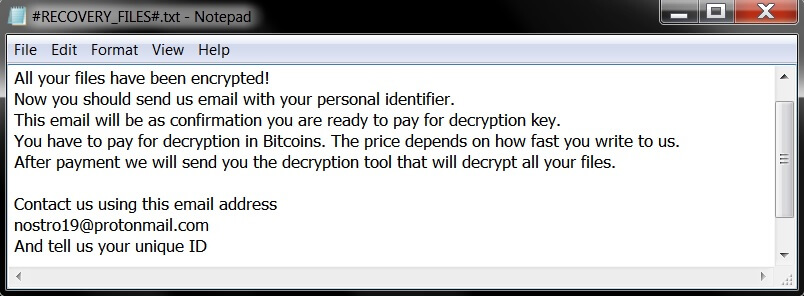
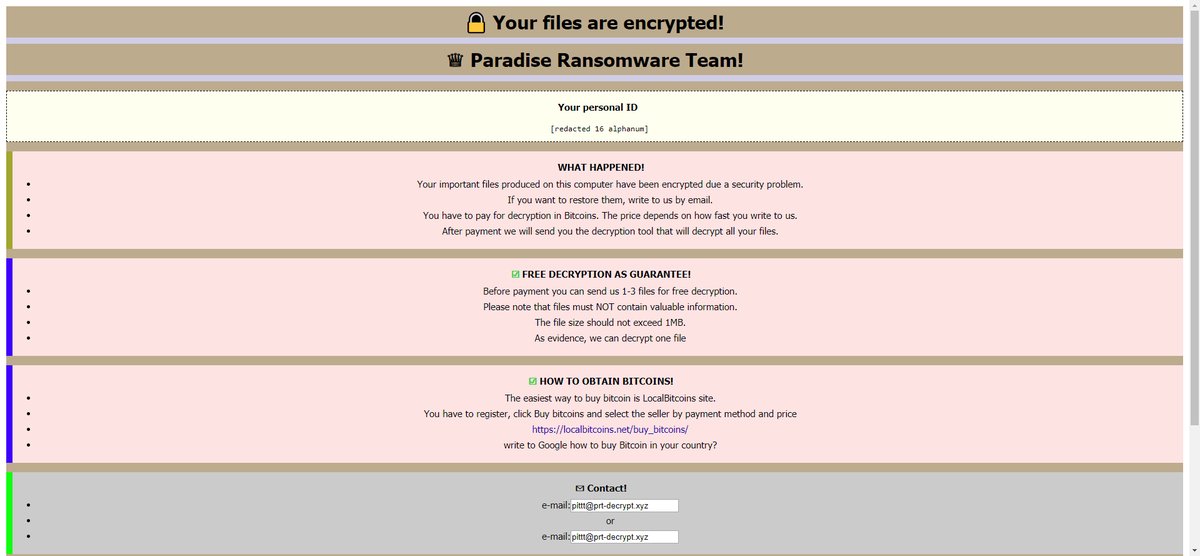
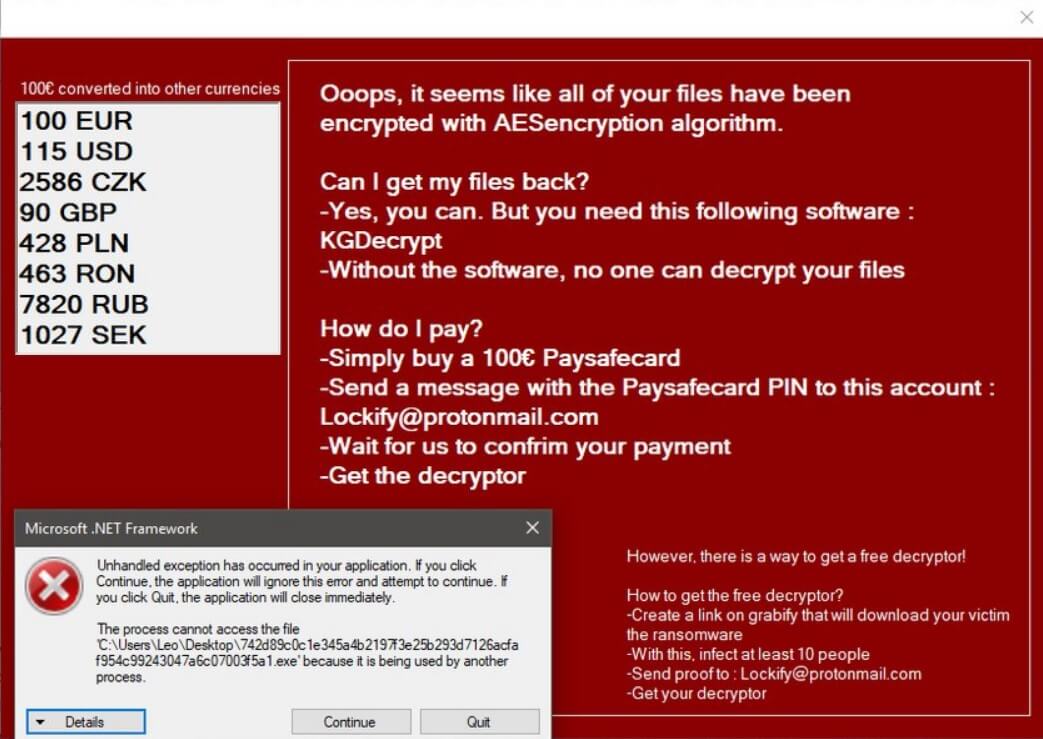
This article will help you to remove the .locked_by_mR_Anonymous(TZ_HACKERS) File Virus (Jigsaw) fully. Follow the ransomware removal instructions given at the end of the article. The .locked_by_mR_Anonymous(TZ_HACKERS) File Virus is a part of the Jigsaw ransomware family. The cryptovirus uses…