Remove SearchAwesome Mac Adware — Mac Restore Instructions
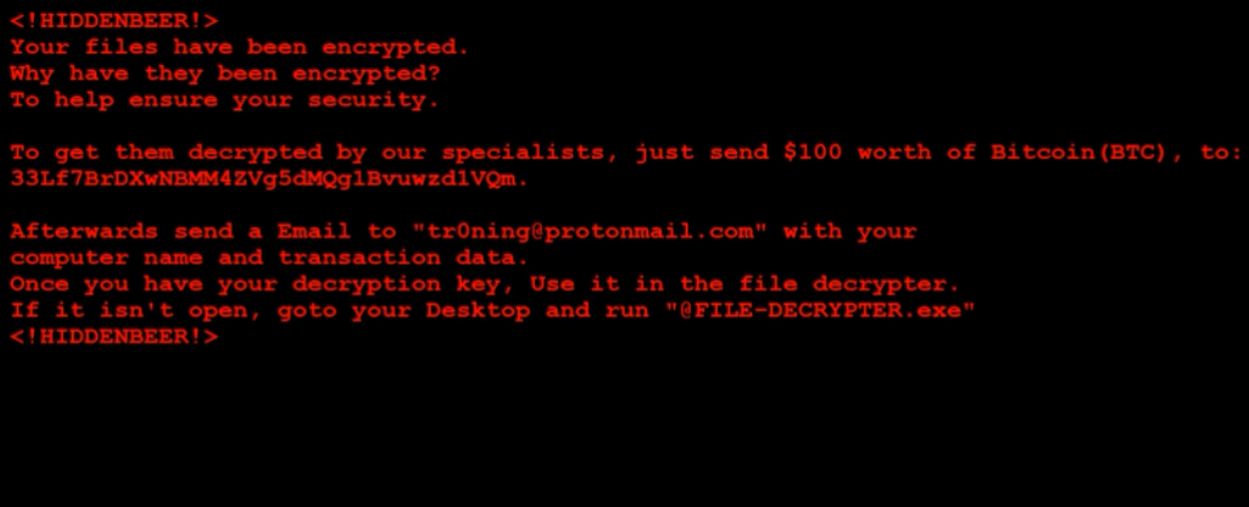
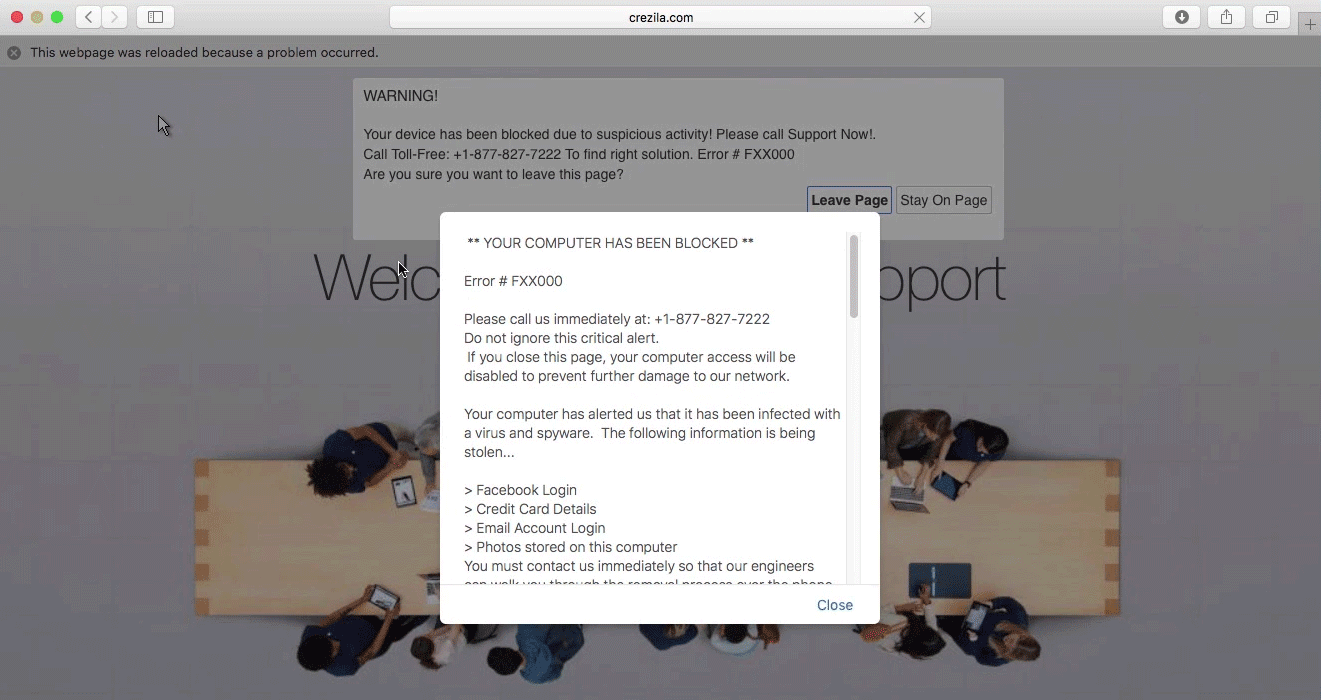
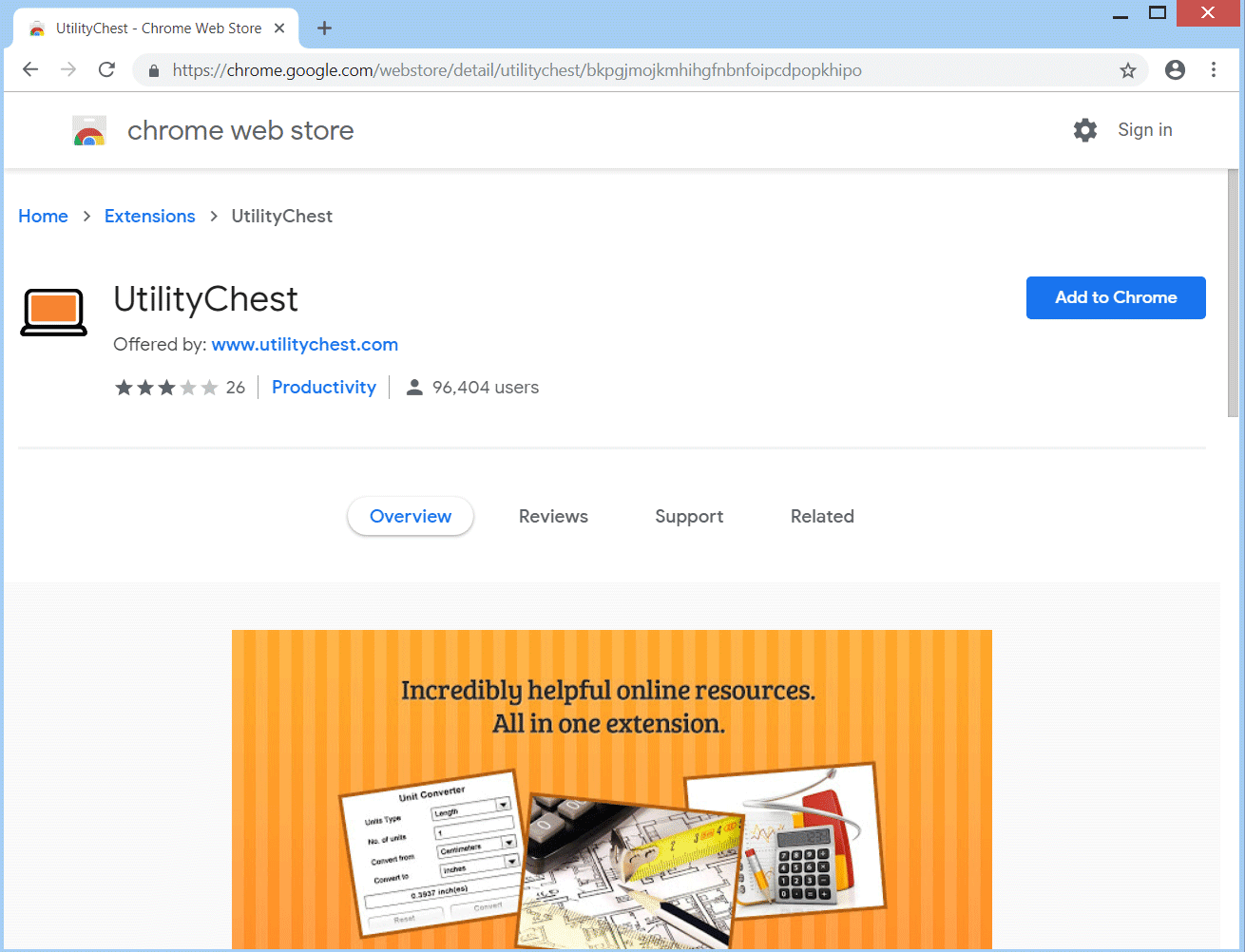
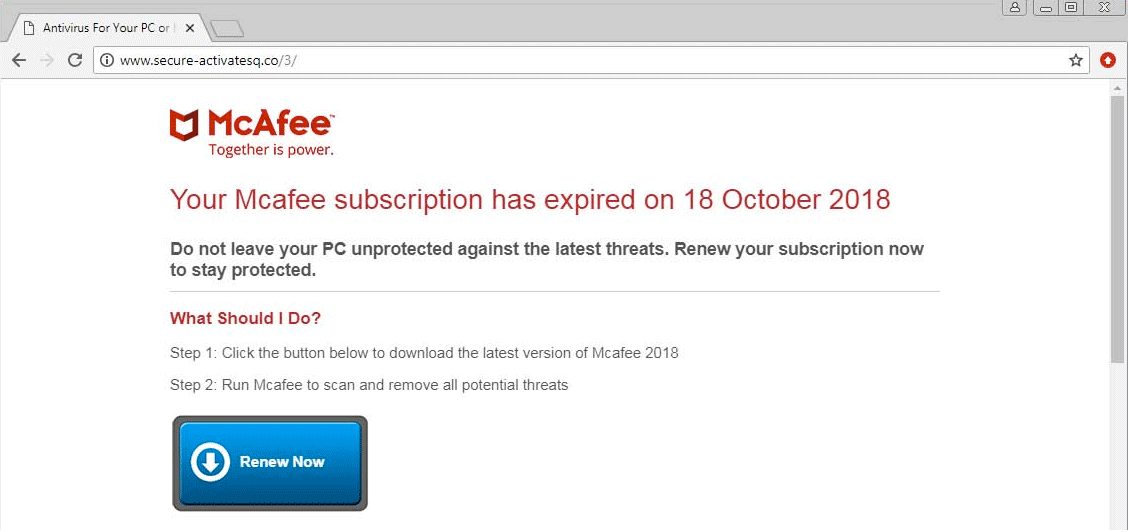
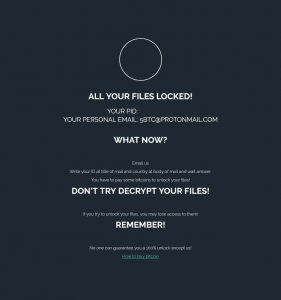
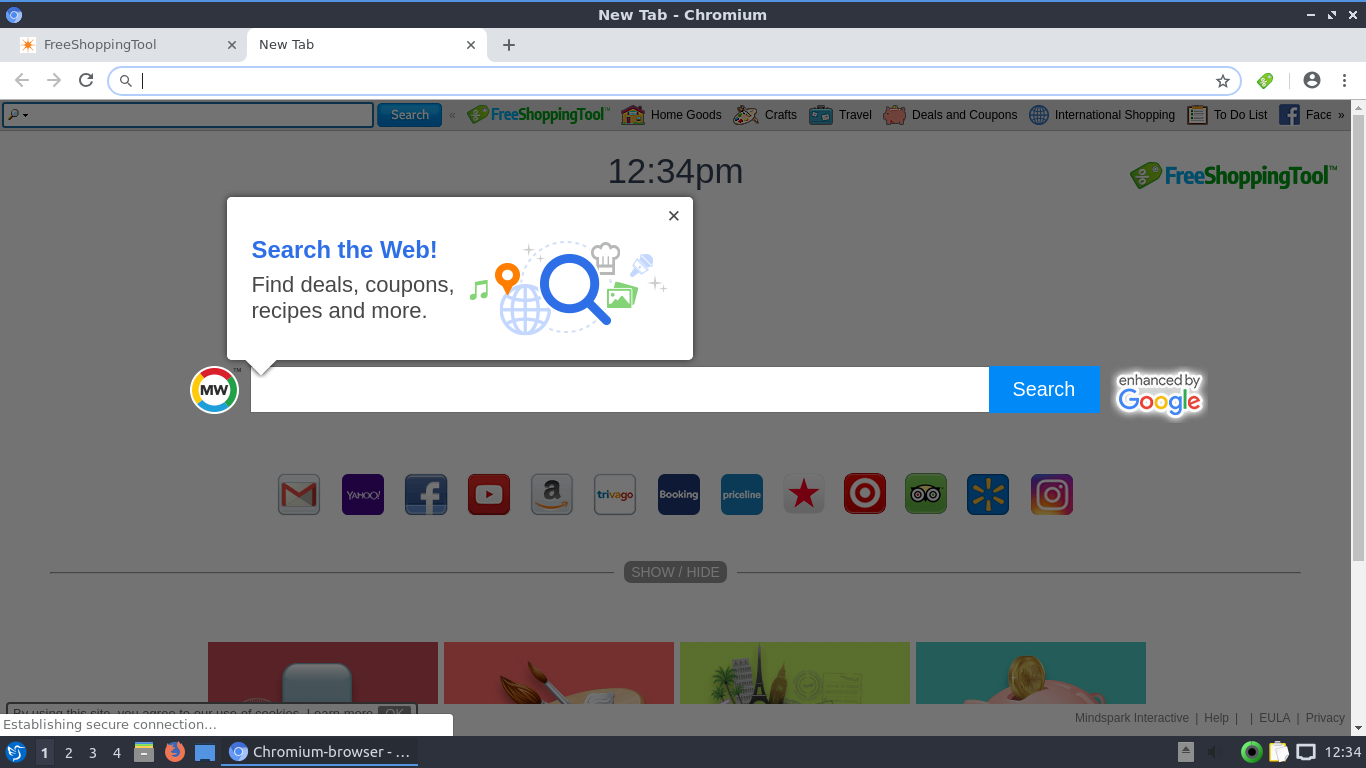
This article has been created in order to give you insight on how to quickly remove the SearchAwesome Mac Adware from your Mac effectively. The SearchAwesome Mac Adware is a very dangerous threat to all Mac computers as it can…