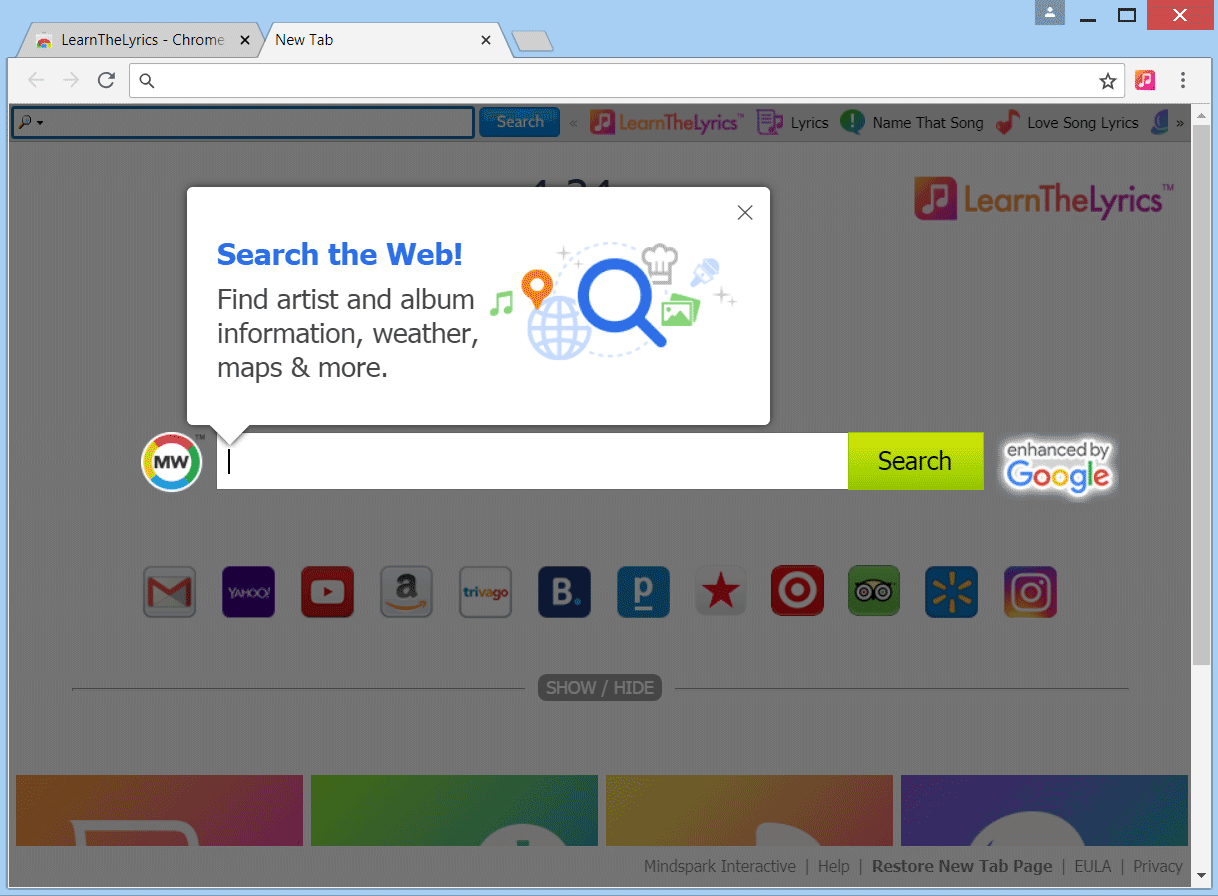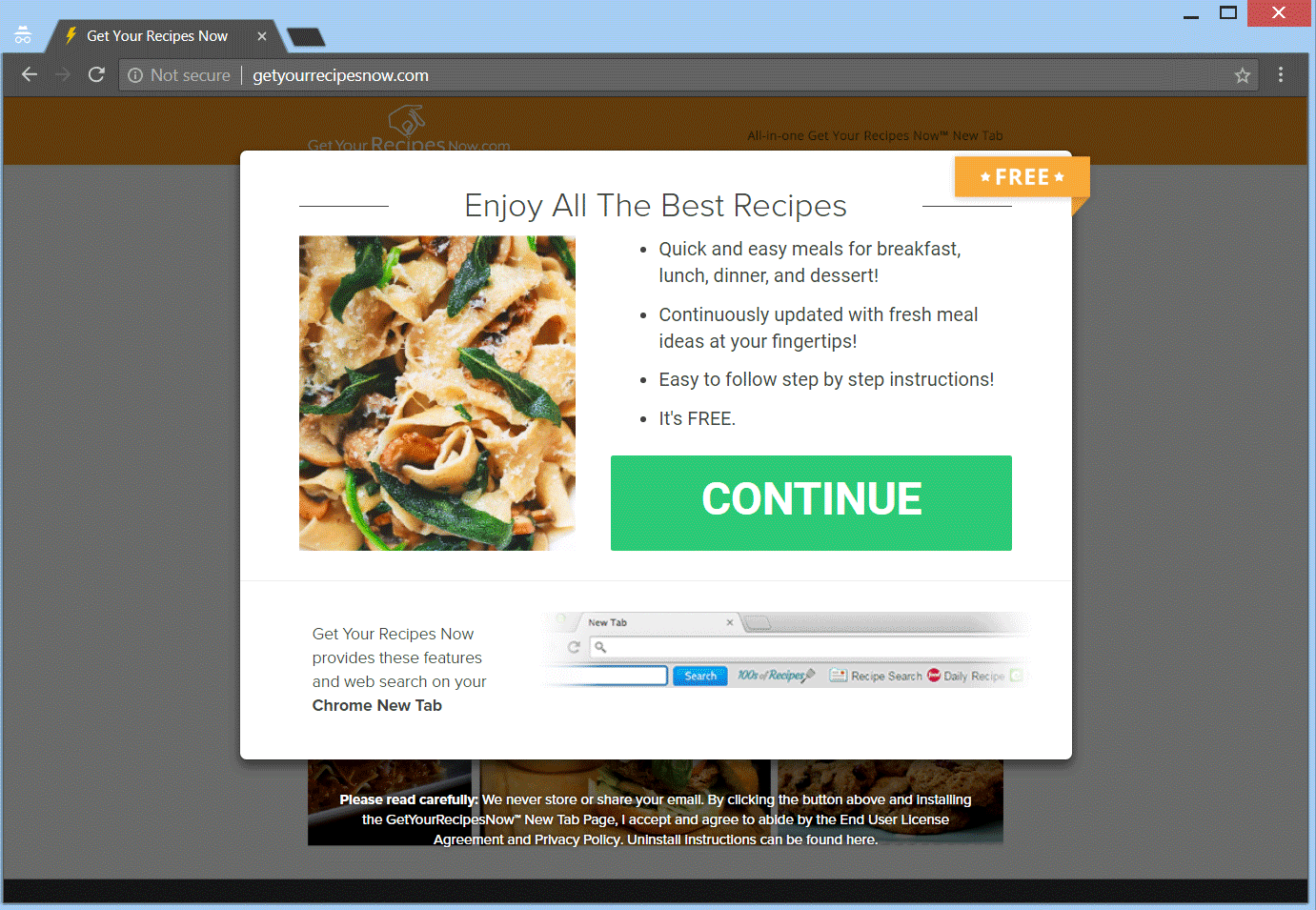
Remove Getyourrecipesnow.com Browser Hijacker
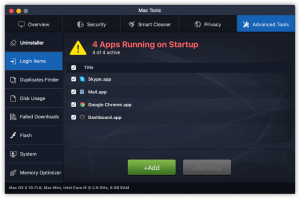
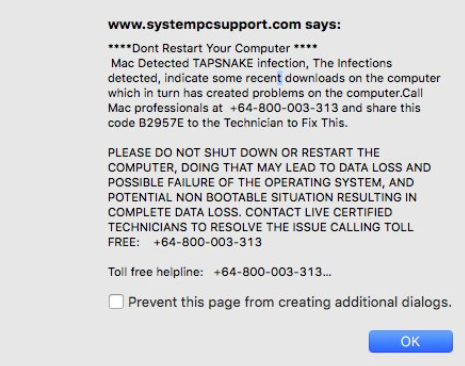
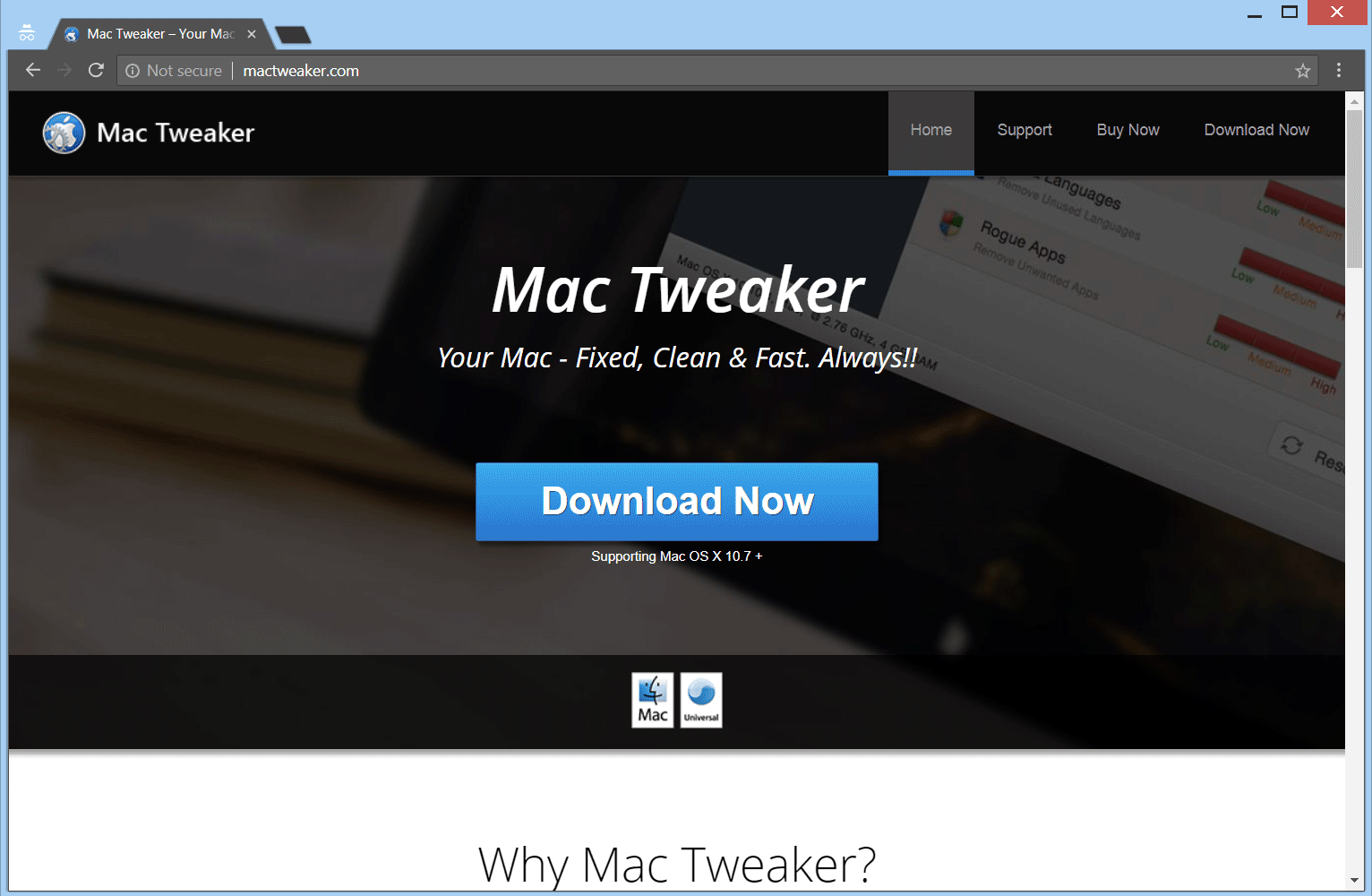
The article will help you to remove Getyourrecipesnow.com fully. Follow the browser hijacker removal instructions given at the end of the article. Getyourrecipesnow.com is the main page that will show up when you open a new tab page if you…