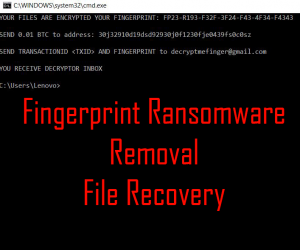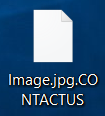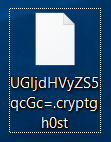
Remove .BI_D Files Virus (LockCrypt Ransomware) + Restore Data
This article provides information about a data locker ransomware dubbed .BI_D files virus that encrypts important files and demands a ransom payment. By the end of it, you will know how to remove the threat and how to restore .BI_D…