Search.searchidd.com Redirect Removal
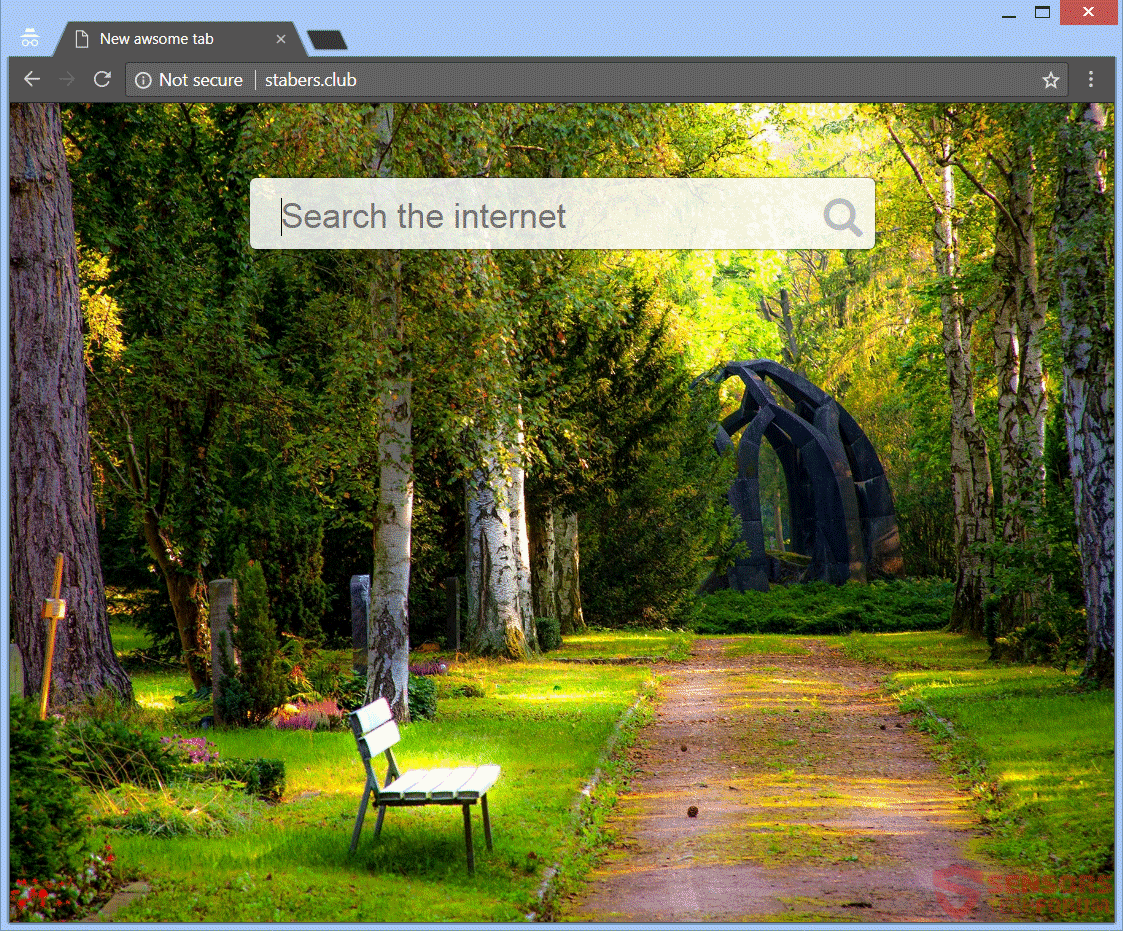
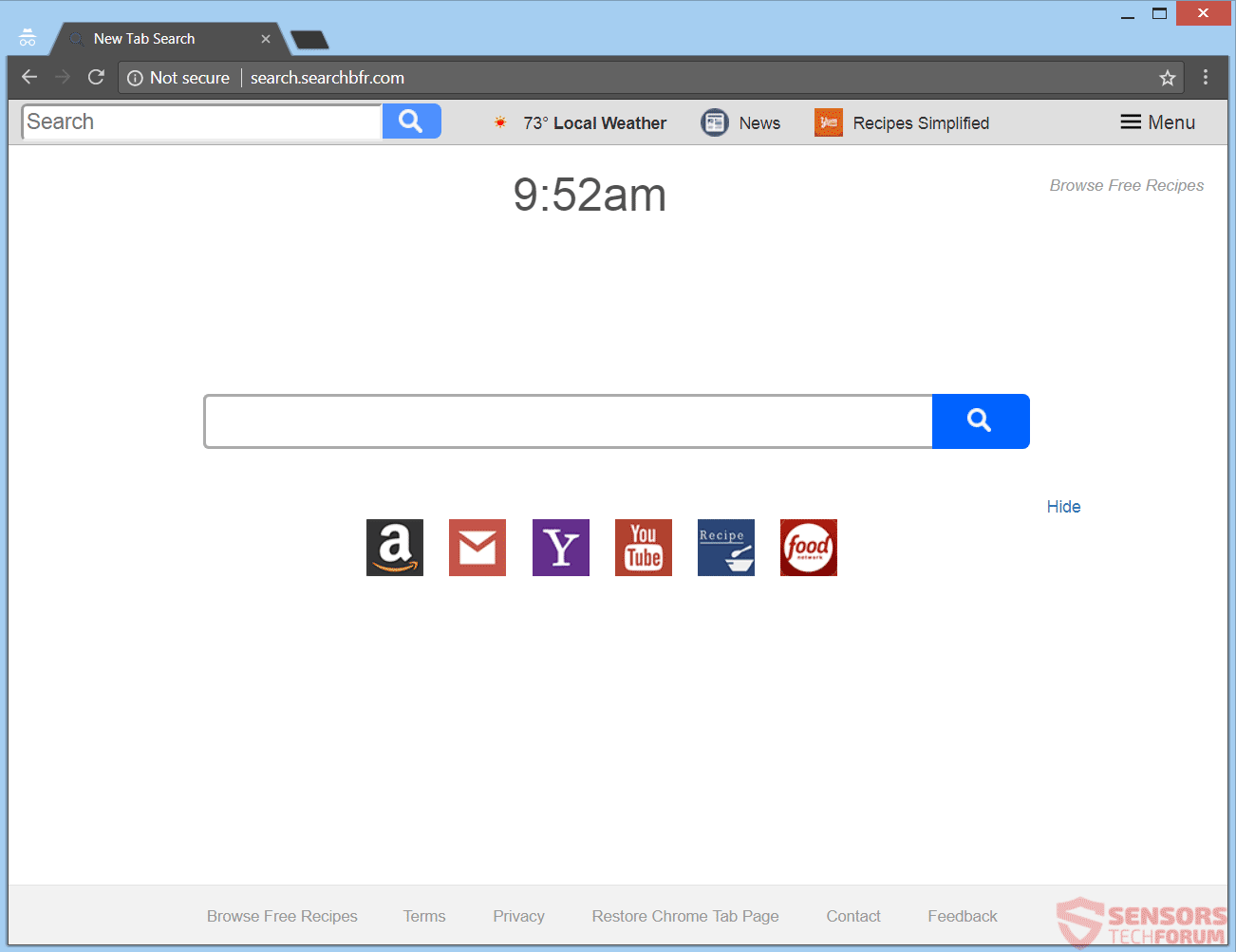
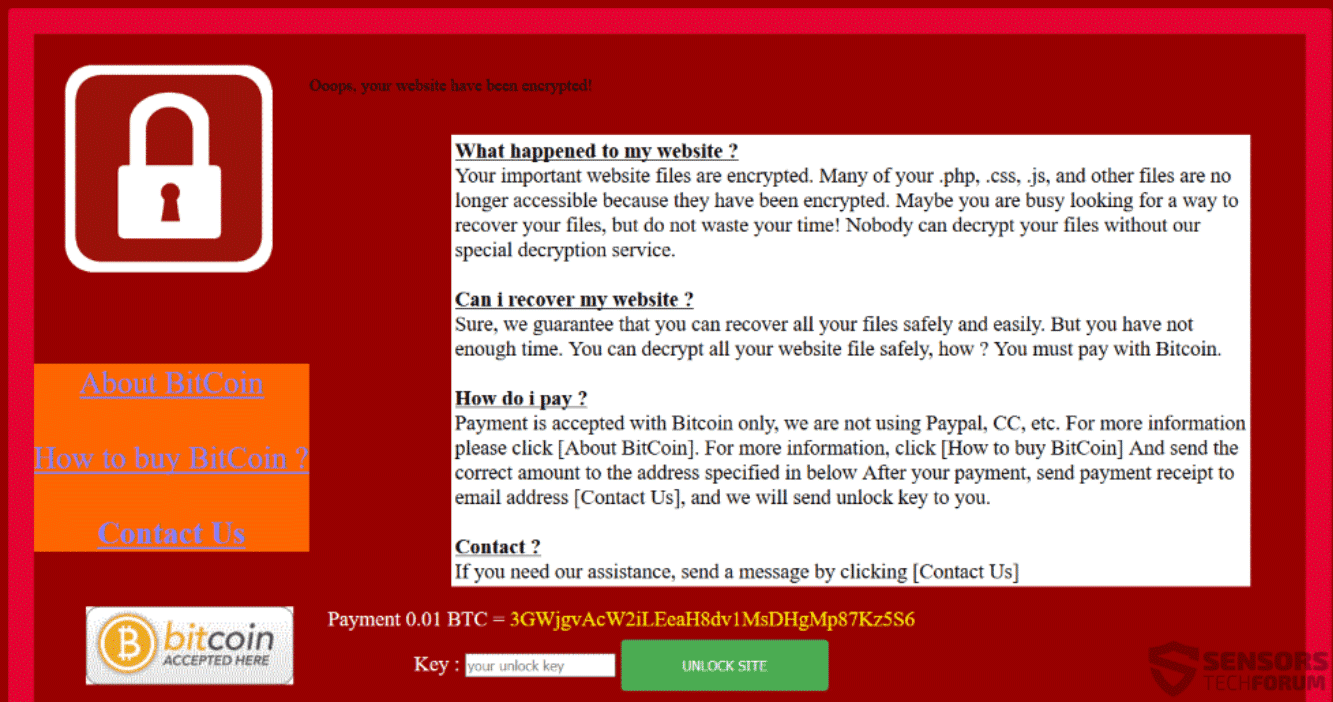
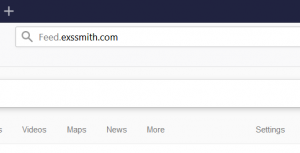
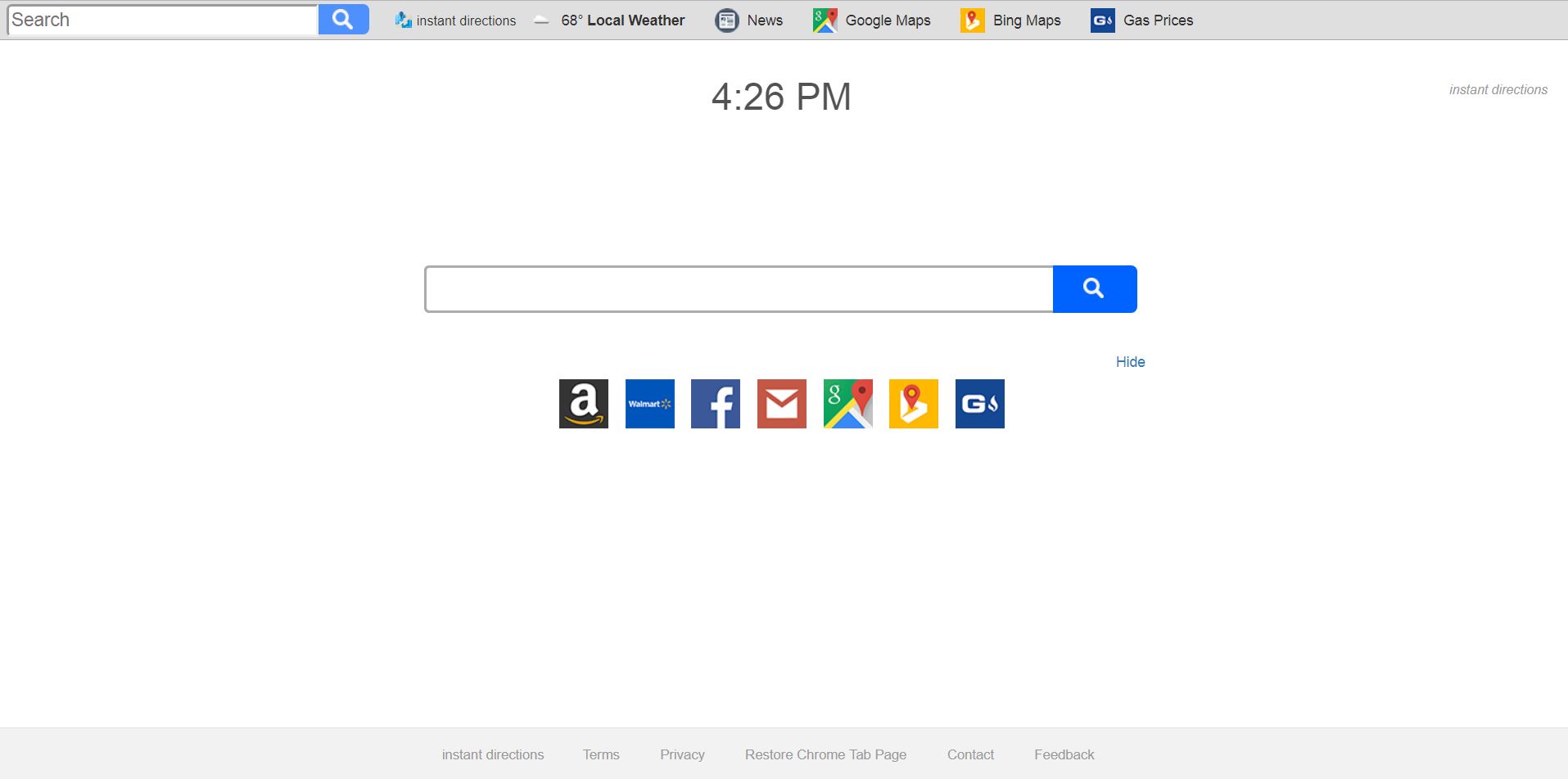
This article aims to help you with the removal of Search.searchidd.com redirect from affected browser and system. Follow the detailed guide at the end to get rid of this annoying website in full. Search.searchidd.com website pushes a hoax search engine…