Vurten Virus – Remove and Restore .improved Files
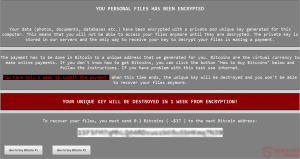
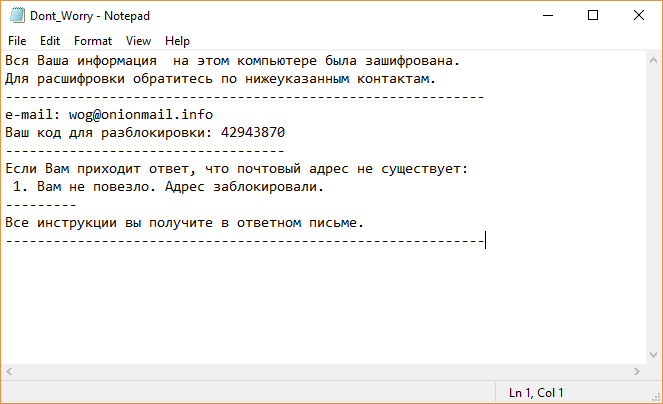
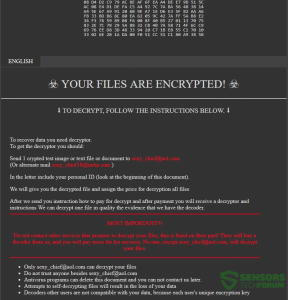
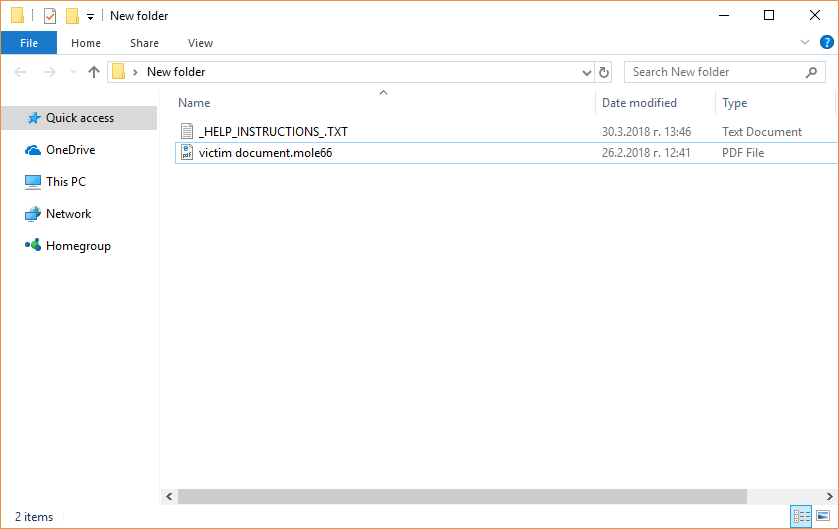
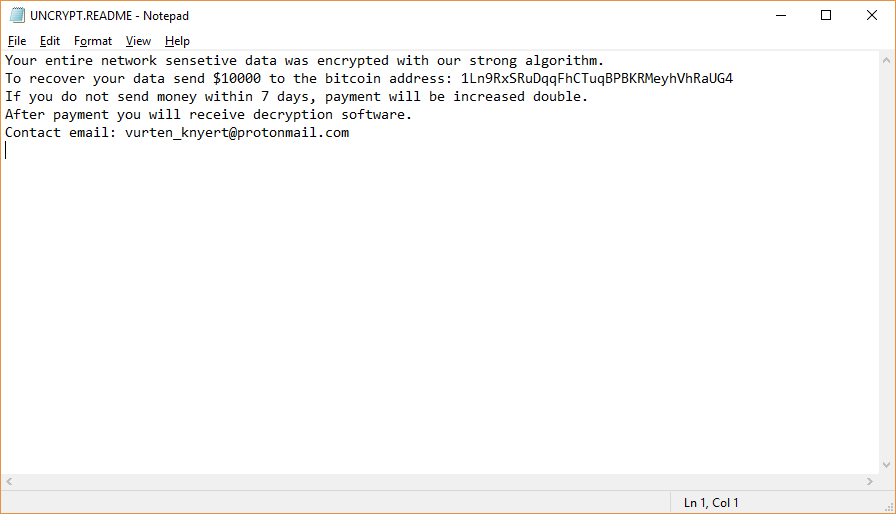
Vurten virus is a new ransomware that has recently been discovered by virus researchers, it encrypts target data with the .improved extension. At the moment the collected so far samples seem to be test versions of the malware. Further updates…