EncryptServer2018 Ransomware Removal – Restore .2018 Files
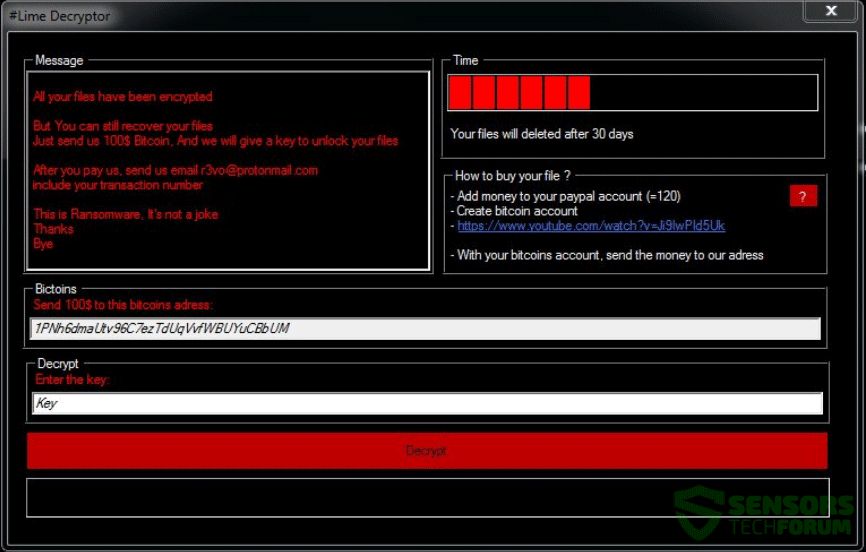
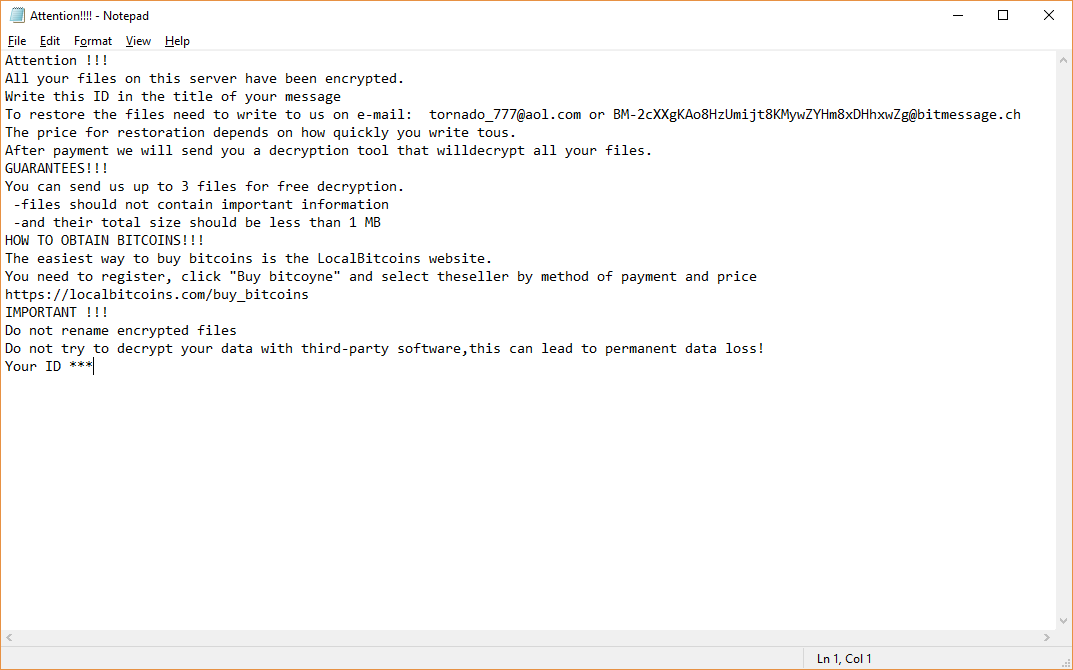
This article will help you remove EncryptServer2018 ransomware efficiently. Follow the ransomware removal instructions provided at the end of the article. The EncryptServer2018 ransomware is a newly discovered virus threat that follows the behavior patterns of the famous malware families.…