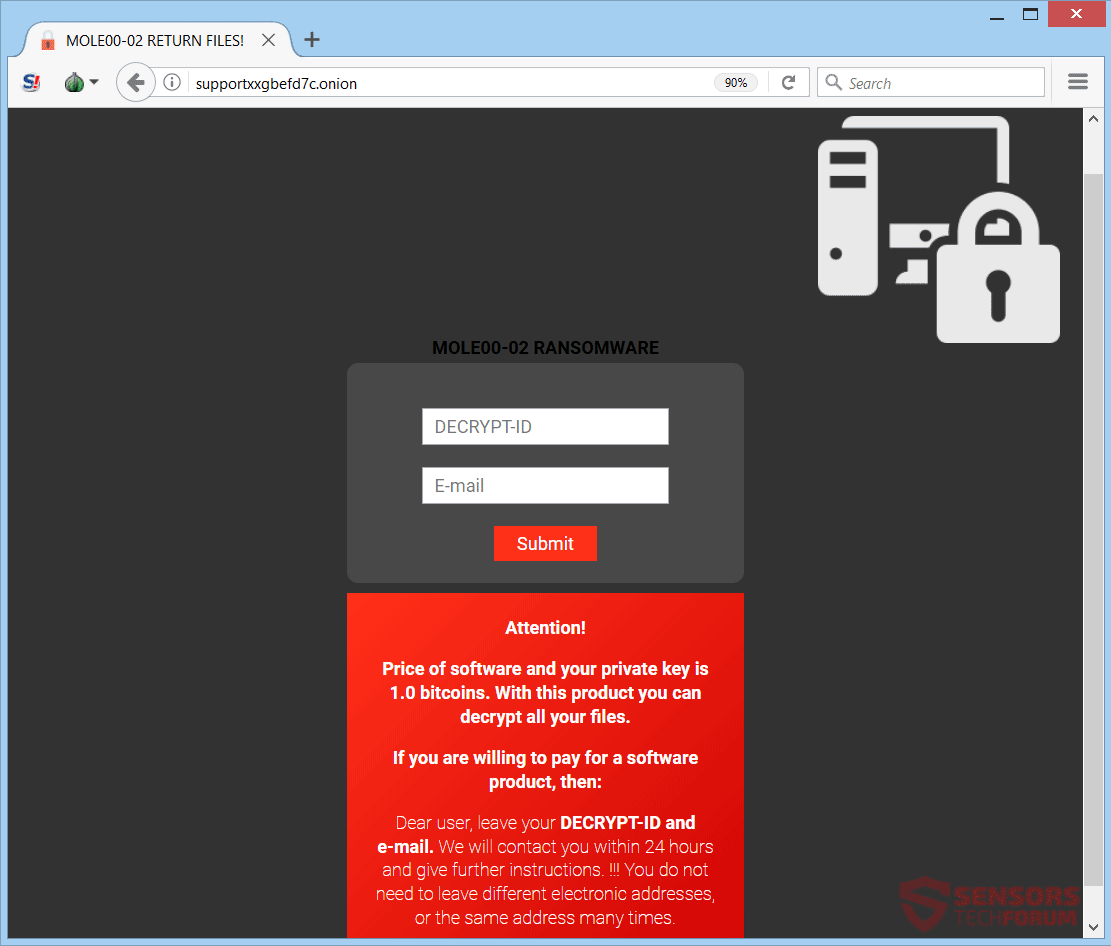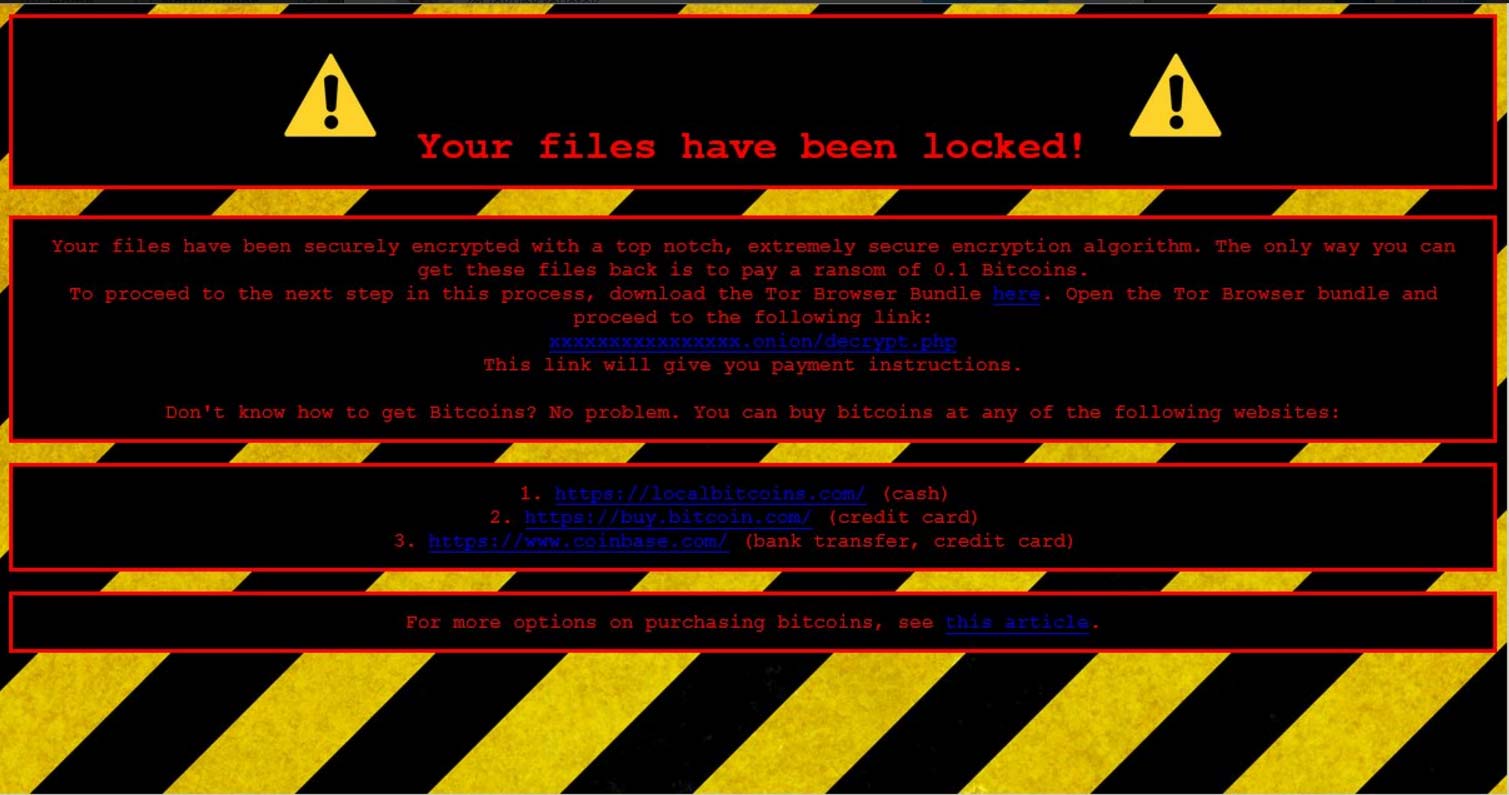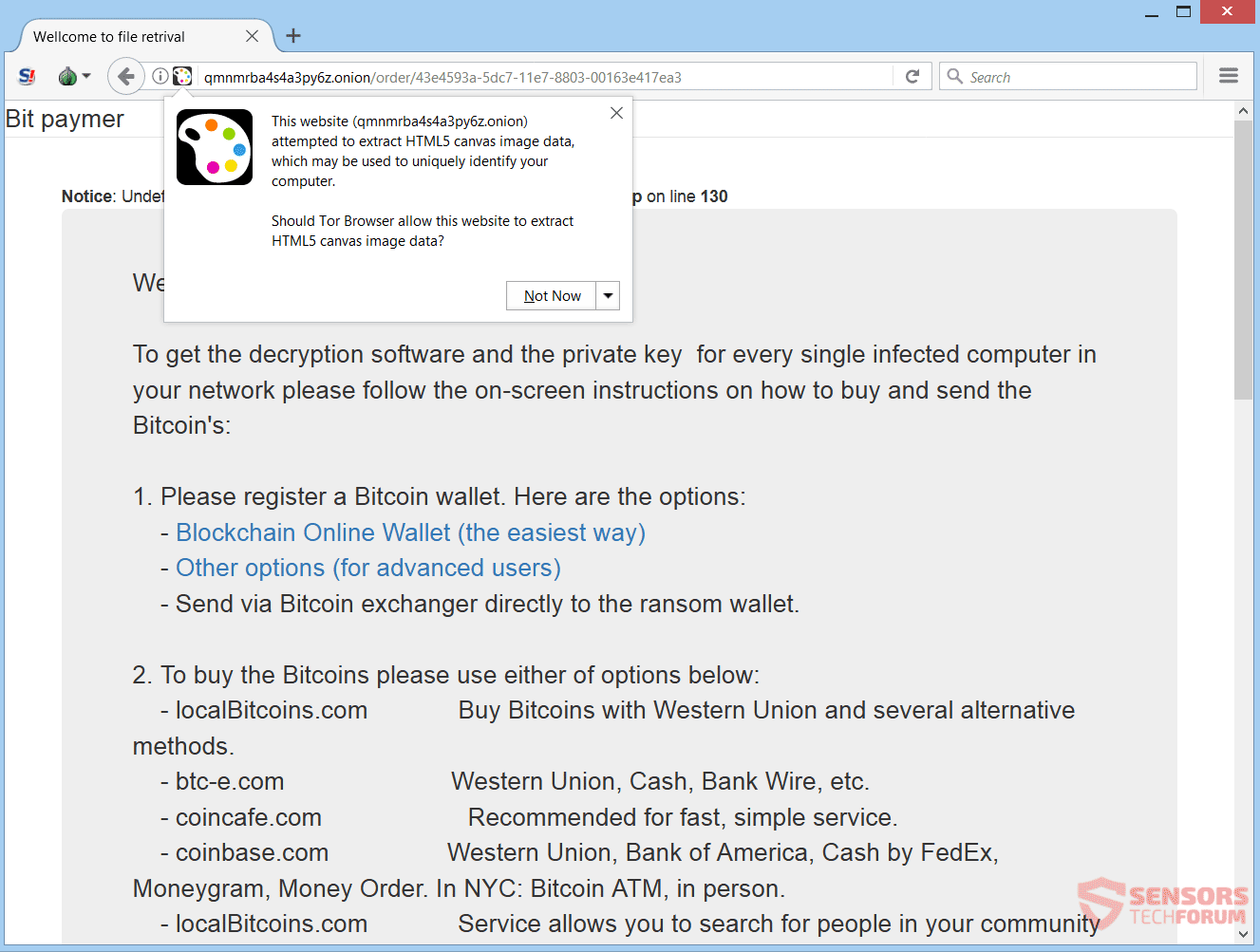
The Future Is Here: Employees Getting RFID Chips Implanted
The employment of implanted chips may have seemed like a conspiracy not too long ago but it’s already a fact. A scary fact. Apparently, an American company, 32M, is now offering chips to employees willing to get the implant in…