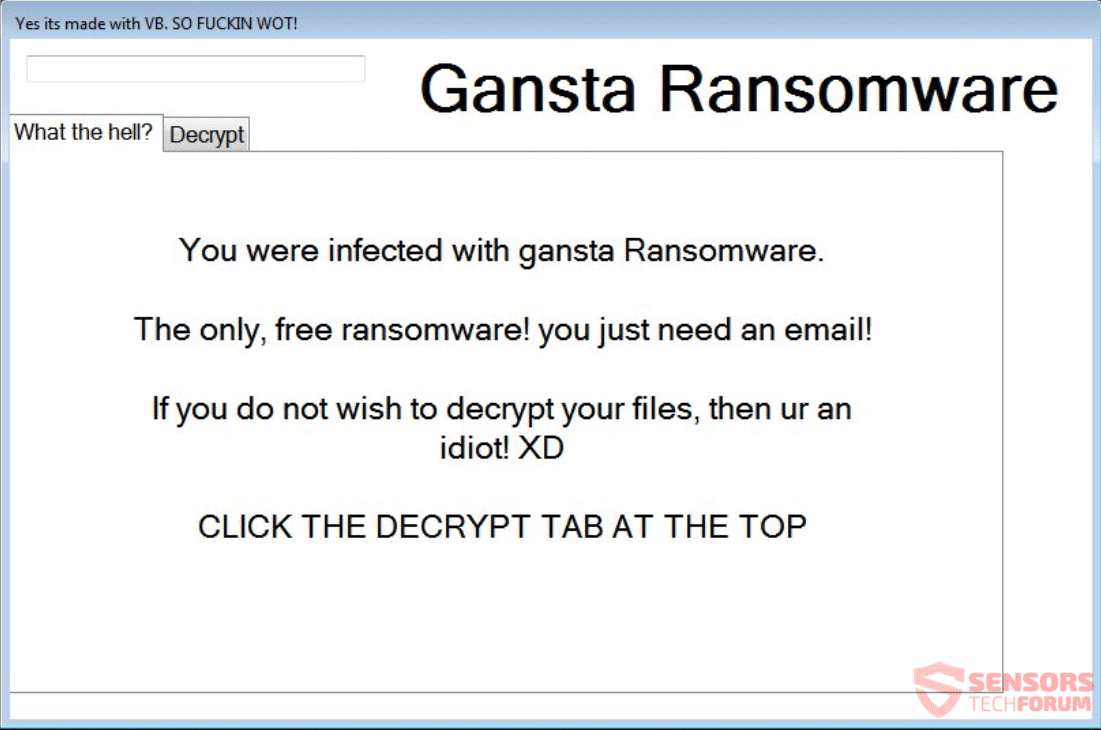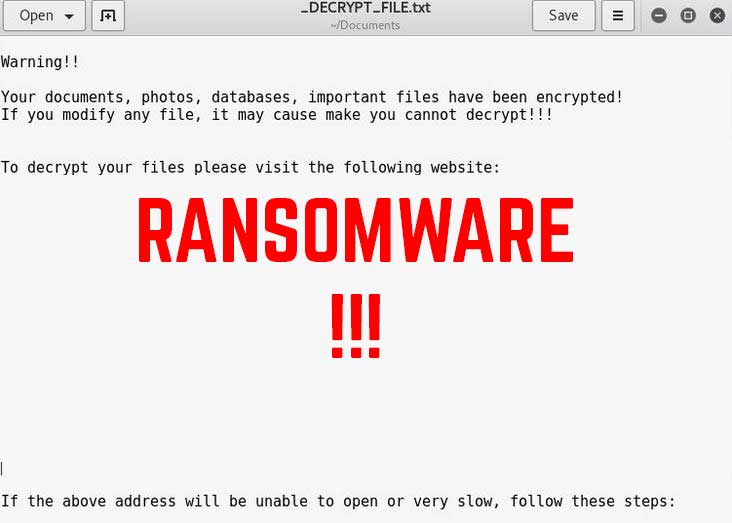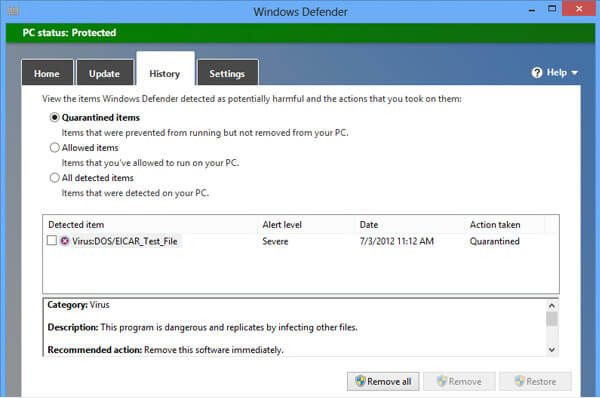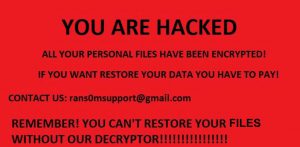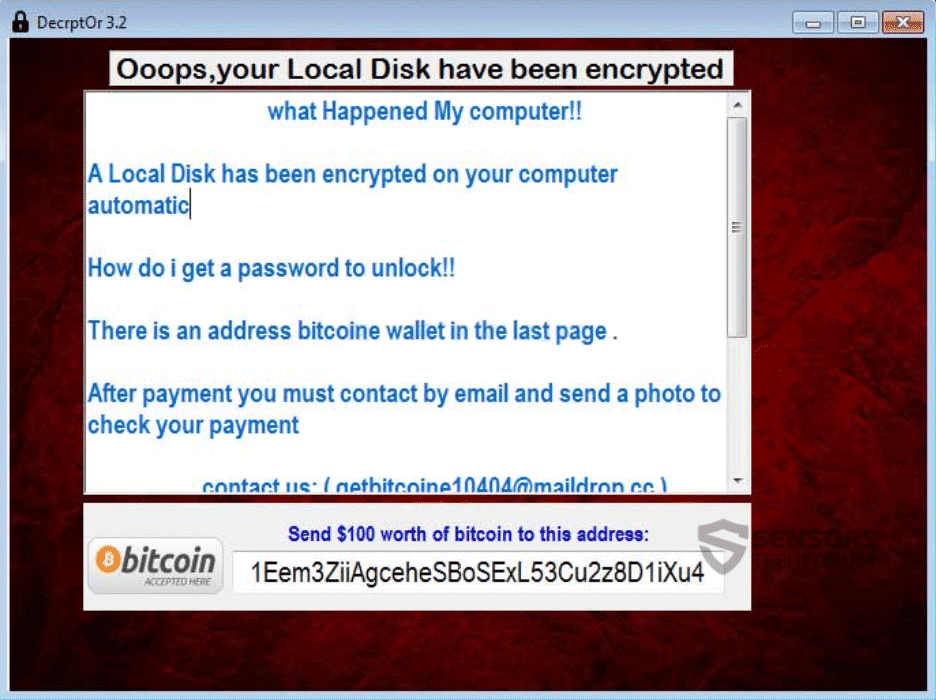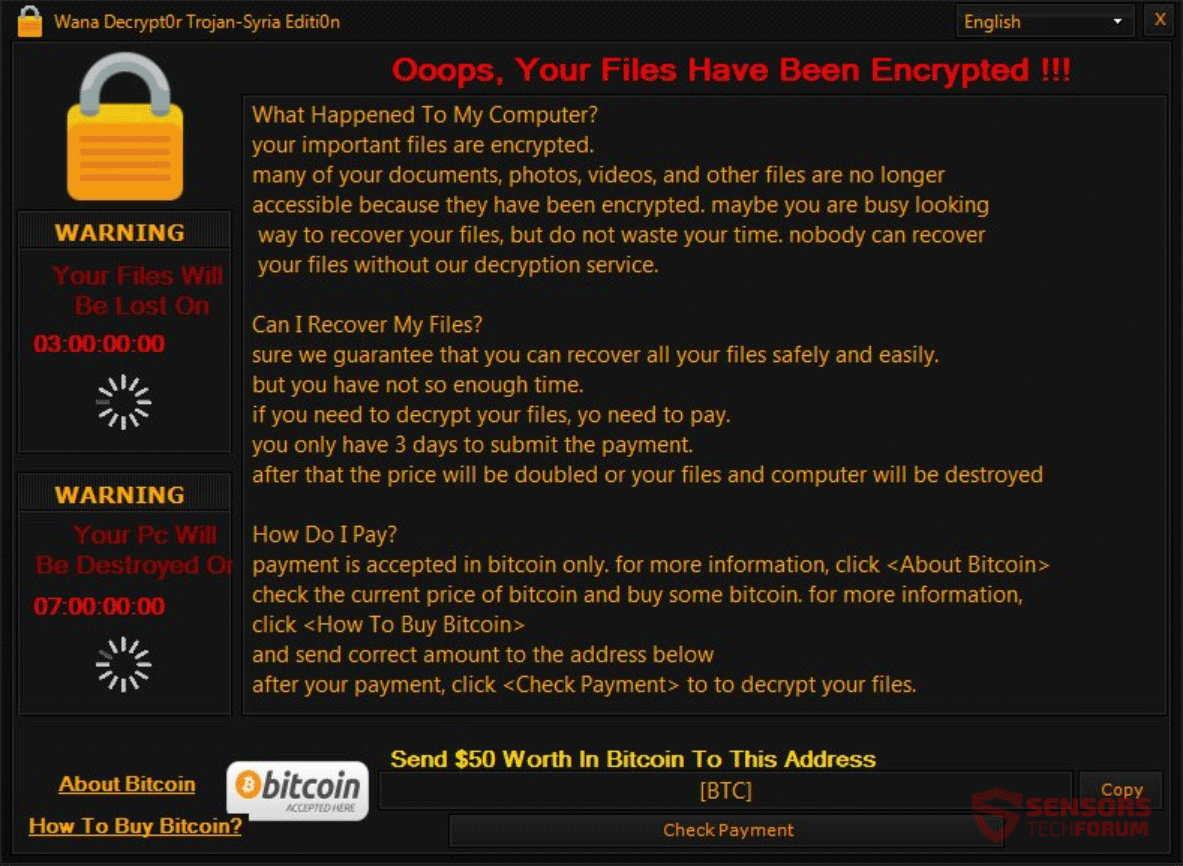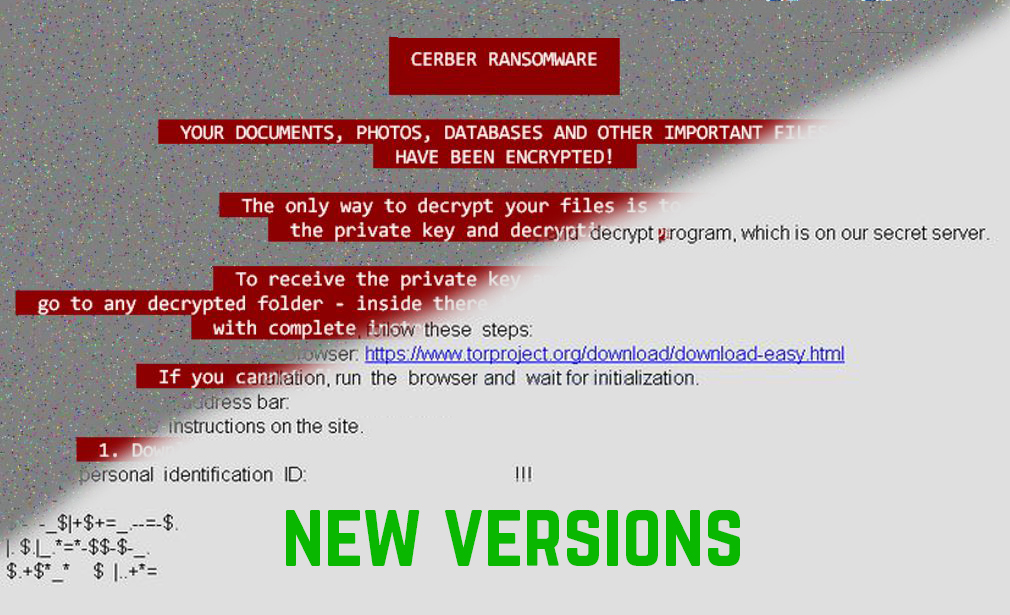
Locky and Cerber Ransomware Viruses Both Updated
Both Locky and Cerber ransomware have gotten fresh new updates and started spreading their new variants with new spam campaigns. The changes in the variants are not so radical, but more of incremental type of modifications and the malwares have…