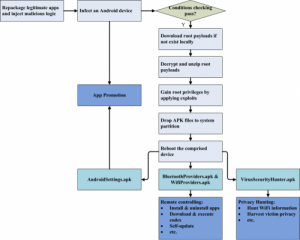
Serious Java Deserialization Vulnerability Uncovered in 70 Libraries
In the beginning of 2015, the security researchers Gabriel Lawrence and Chris Frohoff revealed a Remote Code Execution vulnerability that could be exploited via the Apache Commons Collections. The latter is just one of the most well-known and widely used…