There is a new RAT (Remote Access Tool/Trojan) that goes by the name of Pupy. It is open-source so everybody can have full access to its capabilities. It can be used by administrators, penetration testers, engineers, but unfortunately, also by black hats. Pupy has a multi-platform usage and an embedded Python programming language interpreter. This makes the thought of this tool used by cybercriminals terrifying.
This is how it looks like inside:
| Name | Pupy RAT |
| Type | RAT, Trojan |
| Short Description | The tool is basically a trojan if it’s used by black hat hackers. |
| Symptoms | The RAT can download and upload files and information, migrate to other processes, execute commands and also has a keylogger. |
| Distribution Method | Exploit Kits, Targeted Attacks |
| Detection Tool | Download Malware Removal Tool, to See If Your System Has Been Affected by malware |
| User Experience | Join our forum to discuss the Pupy RAT. |
Pupy Trojan – Distribution
There are lots of possibilities for distributing Pupy as it is with a free license and everybody has access to it and can modify it as they see fit. A very effective way of it being inserted into your system can be with the use of Exploit Kits as this is quite common for similar Tool agents. We believe that targeted attacks and spam emails as ways of distribution can be just as effective. It is really probable we see that in the near future.
Pupy Trojan – Technical Details
Pupy is classified as RAT. RAT stands for Remote Access Trojan. It could easily be implemented to stay hidden on a system and steal sensitive information as an APT (Advanced Persistent Threat). It has the potential to infect you with more malware, and as now it is quite popular, you can easily get ransomware like TeslaCrypt and CryptoWall 4.0.
Pupy has the Python language embedded in its programming and can inject .dll files in Windows systems and is reported to work effectively under Linux, Mac OS X and Windows operating systems. The whole Python interpreter is fully loaded from memory so there may be little to no trace on the disk of a computer.
The following features are already implemented and working:
- migrate
- inter process architecture injection also works (x86->x64 and x64->x86)
- command execution
- interactive shell (cmd.exe, /bin/sh, /bin/bash, …)
- tty allocation is well supported on target running a Unix system. (Looks like a SSH shell)
- interactive python shell
- download
- upload
- persistence
- screenshot
- webcam snapshot
- in memory execution of PE exe both x86 and x64
- socks5 proxy
- local port forwarding
- shellcode execution
- keylogger (monitors keys, the windows titles the text is typed in and the clipboard)
- mouselogger: (takes small screenshots around the mouse at each click and sends them back to the server)
As it can have a constant connection to remote locations, hackers behind the Trojan may also steal sensitive data and files, upload malware, spy on you and countless other things.
Pupy Trojan Removal
This Trojan can spy on you, access personal information on your PC and eventually may infect you with different malware types. It may track your personal information and send all data to cybercriminals, from which they can profit. To completely get rid of the Pupy Trojan horse from your PC, carefully follow the step-by-step removal instructions provided below.
Preparation before removing Pupy RAT.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
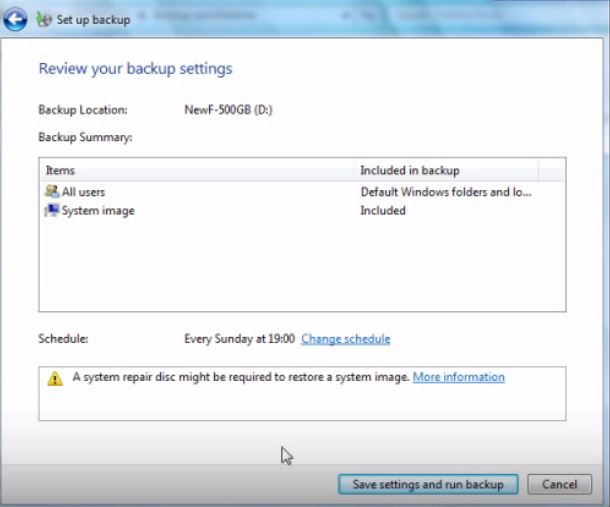
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
- Scan for Malware
- Fix Registries
- Remove Virus Files
Step 1: Scan for Pupy RAT with SpyHunter Anti-Malware Tool



Step 2: Clean any registries, created by Pupy RAT on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Pupy RAT there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.Step 3: Find virus files created by Pupy RAT on your PC.
1.For Windows 8, 8.1 and 10.
For Newer Windows Operating Systems
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.

2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.

3: Navigate to the search box in the top-right of your PC's screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be "fileextension:exe". After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:

N.B. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.For Windows XP, Vista, and 7.
For Older Windows Operating Systems
In older Windows OS's the conventional approach should be the effective one:
1: Click on the Start Menu icon (usually on your bottom-left) and then choose the Search preference.

2: After the search window appears, choose More Advanced Options from the search assistant box. Another way is by clicking on All Files and Folders.

3: After that type the name of the file you are looking for and click on the Search button. This might take some time after which results will appear. If you have found the malicious file, you may copy or open its location by right-clicking on it.
Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software.
Pupy RAT FAQ
What Does Pupy RAT Trojan Do?
The Pupy RAT Trojan is a malicious computer program designed to disrupt, damage, or gain unauthorized access to a computer system. It can be used to steal sensitive data, gain control over a system, or launch other malicious activities.
Can Trojans Steal Passwords?
Yes, Trojans, like Pupy RAT, can steal passwords. These malicious programs are designed to gain access to a user's computer, spy on victims and steal sensitive information such as banking details and passwords.
Can Pupy RAT Trojan Hide Itself?
Yes, it can. A Trojan can use various techniques to mask itself, including rootkits, encryption, and obfuscation, to hide from security scanners and evade detection.
Can a Trojan be Removed by Factory Reset?
Yes, a Trojan can be removed by factory resetting your device. This is because it will restore the device to its original state, eliminating any malicious software that may have been installed. Bear in mind that there are more sophisticated Trojans that leave backdoors and reinfect even after a factory reset.
Can Pupy RAT Trojan Infect WiFi?
Yes, it is possible for a Trojan to infect WiFi networks. When a user connects to the infected network, the Trojan can spread to other connected devices and can access sensitive information on the network.
Can Trojans Be Deleted?
Yes, Trojans can be deleted. This is typically done by running a powerful anti-virus or anti-malware program that is designed to detect and remove malicious files. In some cases, manual deletion of the Trojan may also be necessary.
Can Trojans Steal Files?
Yes, Trojans can steal files if they are installed on a computer. This is done by allowing the malware author or user to gain access to the computer and then steal the files stored on it.
Which Anti-Malware Can Remove Trojans?
Anti-malware programs such as SpyHunter are capable of scanning for and removing Trojans from your computer. It is important to keep your anti-malware up to date and regularly scan your system for any malicious software.
Can Trojans Infect USB?
Yes, Trojans can infect USB devices. USB Trojans typically spread through malicious files downloaded from the internet or shared via email, allowing the hacker to gain access to a user's confidential data.
About the Pupy RAT Research
The content we publish on SensorsTechForum.com, this Pupy RAT how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific trojan problem.
How did we conduct the research on Pupy RAT?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of trojans (backdoor, downloader, infostealer, ransom, etc.)
Furthermore, the research behind the Pupy RAT threat is backed with VirusTotal.
To better understand the threat posed by trojans, please refer to the following articles which provide knowledgeable details.


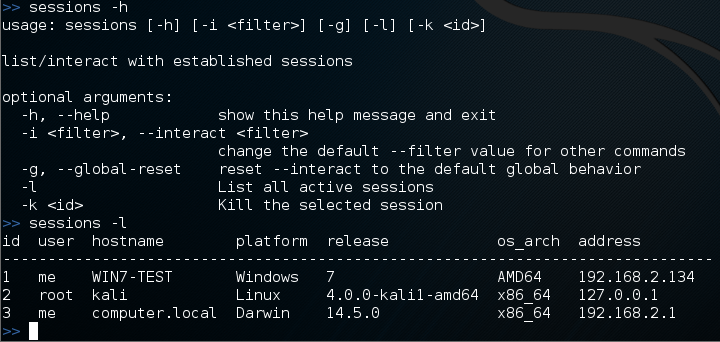
 1. For Windows 7,XP and Vista.
1. For Windows 7,XP and Vista. 2. For Windows 8, 8.1 and 10.
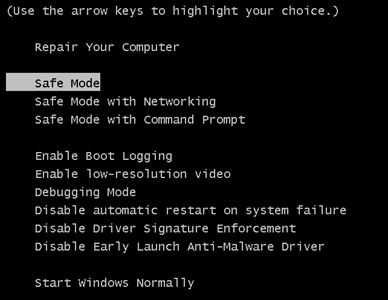
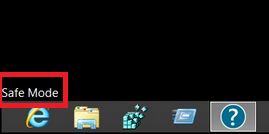
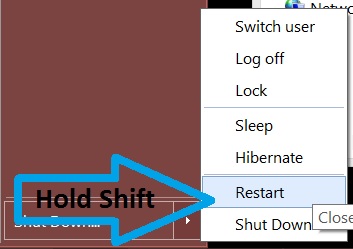
2. For Windows 8, 8.1 and 10.
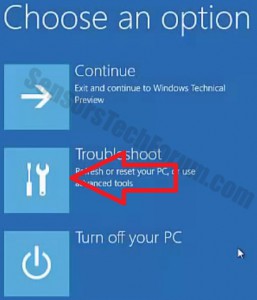
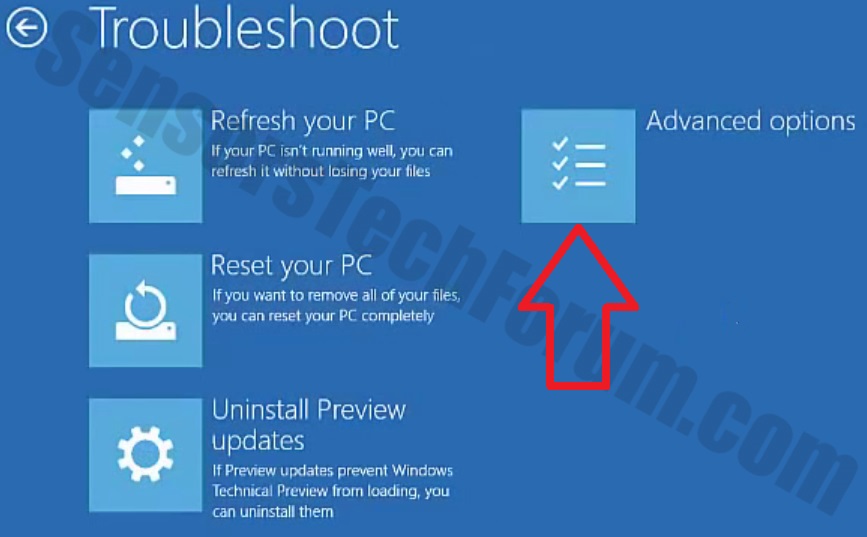
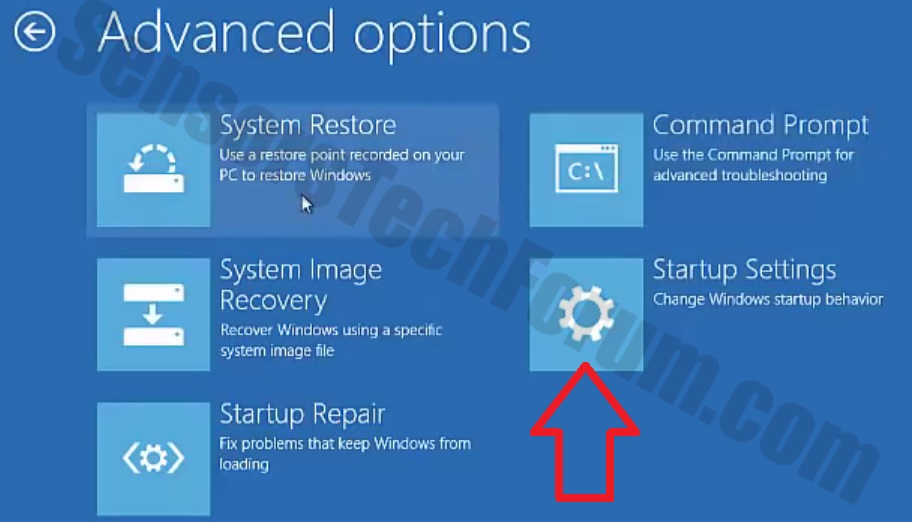

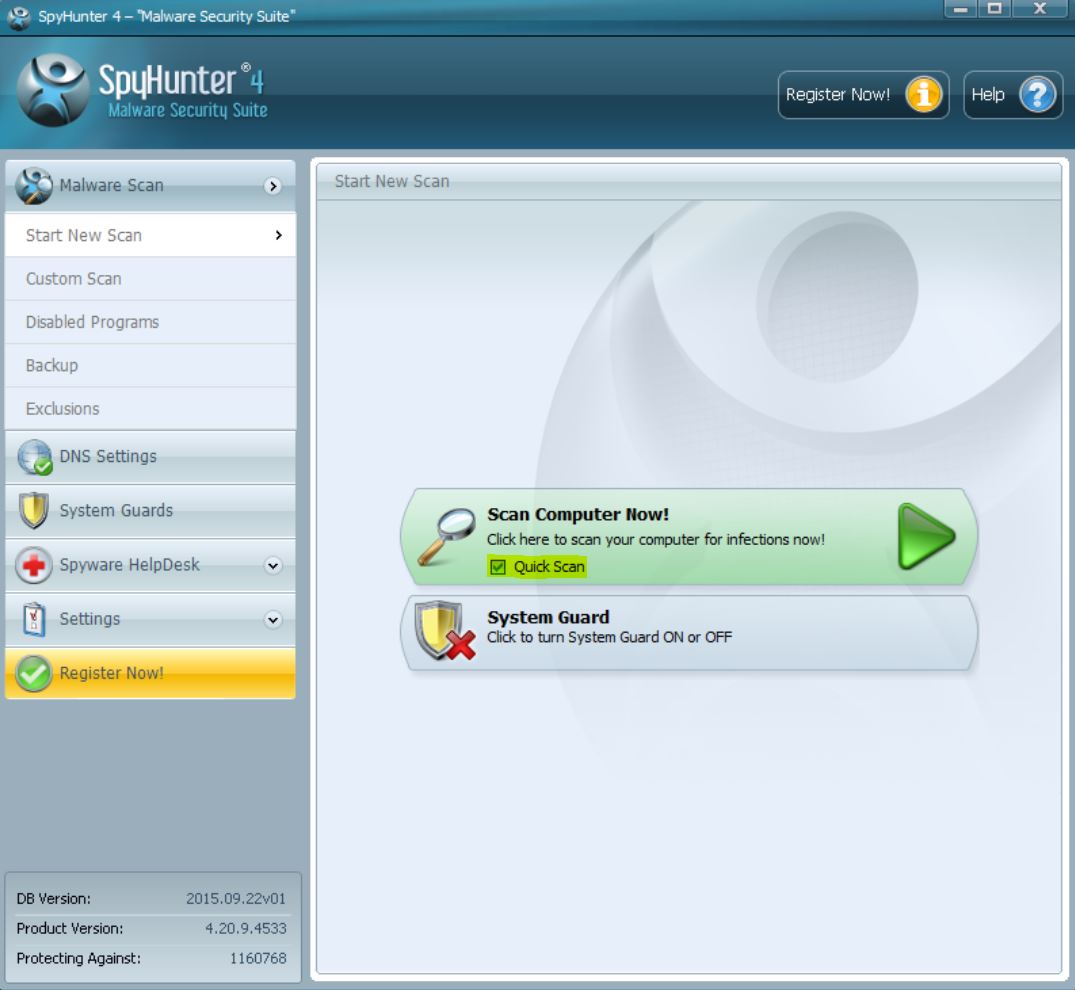
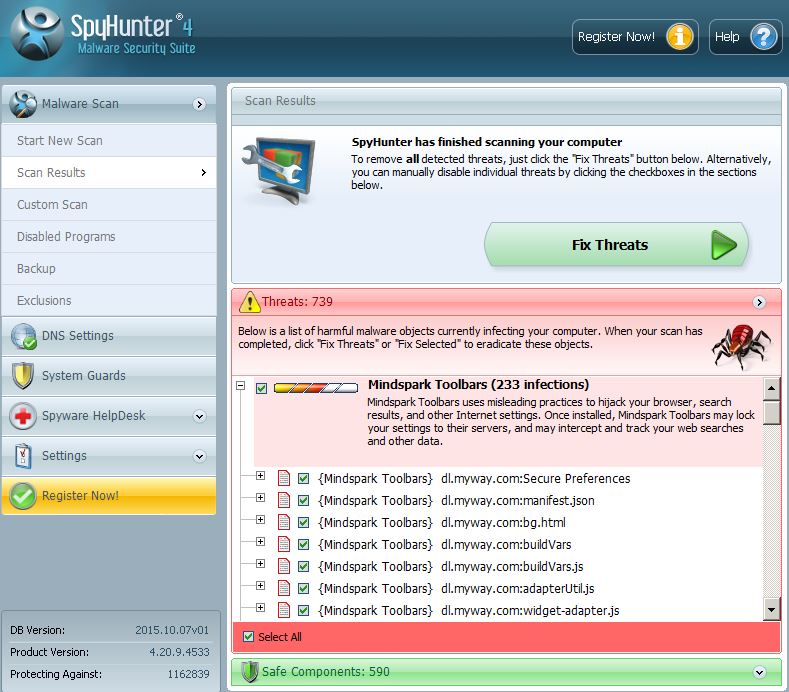
 1. Install SpyHunter to scan for and remove Pupy RAT.
1. Install SpyHunter to scan for and remove Pupy RAT.
 1. Install Malwarebytes Anti-Malware to scan for and remove Pupy RAT.
1. Install Malwarebytes Anti-Malware to scan for and remove Pupy RAT.
 1. Install STOPZilla Anti Malware to scan for and remove Pupy RAT.
1. Install STOPZilla Anti Malware to scan for and remove Pupy RAT.