Security engineers discovered that the SLocker Android ransomware family code base has been published in a decompiled (raw) form. This allows every hacker This is a prominent threat that has produced many strains ever since its first iteration.
SLocker Android Ransomware Code Revealed
Malware experts were able to obtain the full source code in decompiled of one of the most dangerous Android ransomware families of late – SLocker. This is a prominent virus family that is associated with several distribution campaigns.
Image Source: Security Affairs
Note: Posting complete source code of viruses online is a dangerous practice as it allows hackers to easily create offspring threats.
The code was posted on the Git Hub which is one of the web’s biggest repositories of open-source software. This has helped researchers discover how the core engine works, but also gives the opportunity for computer criminals to easily modify the source and create offspring viruses. Such malware code is usually available on underground hacking communities for a fee.
The user who posted the code has used the “fs0c1ety” nick name and has posted a disclaimer stating that it has been reverse engineered from a live sample. The GitHub message reads the following:
Note: SLocker is intended to be used for security research purposes only. Any other use is not the responsibility of the developer(s). Be sure that you understand and are complying with the laws in your area. In other words, don’t be stupid, don’t be an asshole, and use it responsibly and legally.
SLocker Android Ransomware Infection Capabilities
The SLocker Android ransomware is part of the larger virus family that has been spawned as an offspring of the base code. It is a ransomware developed for the mobile operating system that has caused many infections, particularly in 2016 where more than 400 variants were identified in several large-scale attack campaigns.
SLocker is distributed mainly as counterfeit apps that pose as legitimate multimedia players, game guides and other popular software on the Google Play Store and other repositories.
It is an effective tool that follows the usual ransomware tactics:
- When the app is run for the first time it changes its icon and name to distract the user and hide its original name.
- An installation check is then performed. The SLocker engine runs a series of commands to determine if the device has been infected before. If the infection is new then a random number is generated in stored in a “SharedPreferences” folder.
- If there is any external storage available (microSD cards for examples) then a new thread is copied over to it.
- The virus engine immediately starts to encrypt user and system files based on a built-in list of target file type extensions. Like the computer equivalents the hackers can customize this list, mark the affected files with different extensions and change the cipher at will.
- Many SLocker Android virus strains execute the malicious code under a persistent state of execution. This means that the ransomware engine follows the commands and actively prevents manual removal attempts.
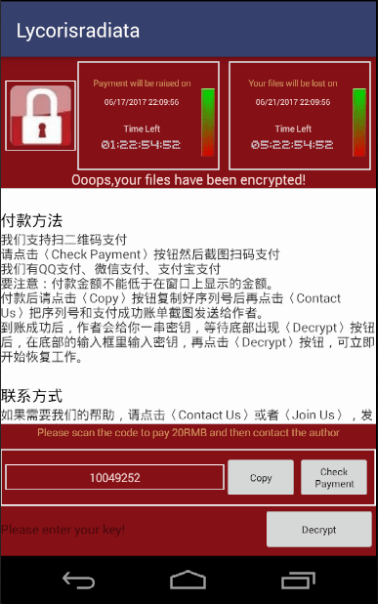
- The SLocker Android virus imposes a lockscreen that shows a ransomware message to the victims. It can be configured to show a different note based on the targets. Some of the latest variants imitate the infamous WannaCry virus family.
Some of the captured strains perform a thorough check before encrypting and/or renaming the victim files. This is done by enforcing a built-in target list. Here is an example:
- The lowercase paths to the target files must not contain the following strings: “/.”, “android”, “com” and “miad”. They refer to system locations and global app names. This is done to prevent device malfunction after the ransomware engine has been started.
- Having a removable storage (microSD card for example) available, the folders that are affected by the virus threat should have a smaller directory level than 3. The other enforced rule is to have the following strings in the file path: “baidunetdisk”, “download” or “dcim”.
- The files need to contain a dot (“.”) and the byte length of the encrypted names should be less than 251.
- The target files need to be larger than 10 KB and smaller than 50 MB.
Depending on the captured SLocker Android virus strain and version the threat may contact the hacker operators via the TOR anonymous network. Some of the criminals that operate SLocker variants have created command and control servers that can be used to remote control the infected devices and steal valuable data. Other versions may use SMS messages sent through a specific phone number or gateway.
Slocker Android Ransomware Ongoing Attacks
Depending on the attained virus the ransomware can be operated by a different hacker or criminal collective. This reflects on the ransomware payment, the lockscreen contents and other configurable factors. Some of the most common forms imitate the computer version of the WannaCry ransomware family.
The victims are shown a generic-looking ransom note that extorts the victims for a payment fee. The computer users are blackmailed to pay the fee in order to recover their data. The operators promise that once the money has been received, their files will be restored and the virus removed. In fact that this is not the case.
WARNING! Do not pay the hackers in any case. Use specialist security tools to remove active infections.
Some of the captured ransomware have set up separate payment methods – Alipay, WeChat and QQ. Most of the associated criminal collectives were identified to originate from China and Russia. The fact that the malware can be used to spy on the compromised devices reveals that a larger infected victim base can be used for mass identity theft. Over the years law enforcement investigations discovered that databases containing private data are often among the most traded commodities in the hacker underground networks.
Google Play Protect May Guard Against SLocker Android Ransomware Instances
Google has made the Google Play Protect service available for all Android users. This is a new feature that was first announced at the Google I/O conference back in May that is now active. The feature combines the security services that have been part of the Android system to date: Verify Apps and Bouncer in a single app. This move effectively allows mobile users to better protect themselves from malicious apps found on the Google Play Store. The Play Protect service actively scans all available apps on Google’s services for signs of malicious code. In addition it monitors software originating from third-party sources a well. One of the key benefits of having Google Play Protect is that it proactively scans the behavior patterns of all installed programs. Computer programmers discovered that some of the advanced malware activate their virus code after a certain delay. Ordinary antivirus products are unable to detect such infections.
Google Play Protect also monitors all installed applications. If a malicious action is identified then the app is immediately halted and the user is alerted. Users running the latest version of the Google Play services can access the settings by navigating to the Settings > Google > Security > Play Protect (previously Verify Apps) menu.
As explained in this article the SLocker Android malware is a dangerous virus family that has the ability to spread over millions of potential victims. The published code will allow criminals to create further versions. This is the reason why we advice all users to constantly stay updated about the latest security threats, incidents and best advice. Also, follow the steps below to further the security of your device.