Researchers with Palo Alto Networks have discovered a new malware family affecting Apple OS X and iOS. Dubbed WireLurker, the malware compromises even non-jailbroken iOS devices.
This is the first malware type that infects iOS apps in a manner a traditional virus does. WireLurker also automates the malicious iOS applications via binary file replacement. The malware was detected for a first time in June this year by a Chinese developer with the Tencent Company. Shortly after his discovery numerous users started reporting about strange apps being installed on their non-jailbroken iPads and iPhones. Mac users also complained about launch daemons with names like “WatchProc” on their machines. The victims said they have installed apps from the Maijadi App store previously.
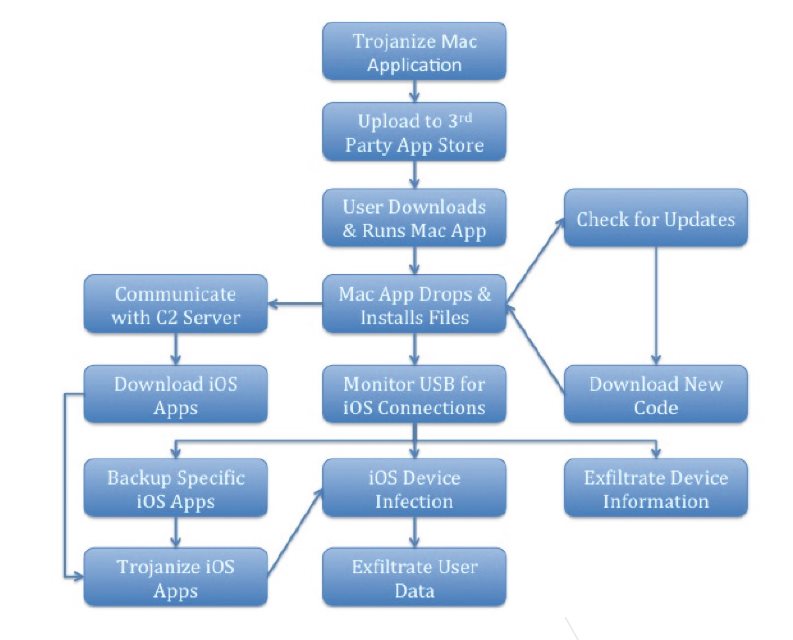
WireLurker – Infiltration Methods and Behaviour
The researchers found out that Mac apps downloaded from this store in the timeframe from April 30 to June 11 contained WireLurker. 467 applications that proved positive for Trojans were downloaded 356, 104 times. WireLurker would be distributed to the victim’s machine in one of these trojanized applications. Upon installation, the malware contacts the Control and Command Server and request updates. In case the compromised Mac is connected to other iOS devices via USB, the malware would detect them and define whether the device is jailbroken or not.
- Jailbroken devices: WireLurker would back up certain apps from the device to the Mac and repackage them with a malicious binary file. The modified applications would then be installed through an iTunes protocol.
- Non-jailbroken devices: WireLurker would install iOS apps that it downloads and exploit iTunes protocols that were implemented by the libimobiledevice library.
So far WireLurker has been upgraded multiple times. At first it wasn’t able to affect iOS devices, and the communication with the Command and Control server was in plaintext.
WireLurker’s Mission
The main purpose of the malware is to gather device specific information such as:
- Model, serial, phone number
- Device type
- User’s Apple ID
- Wi-Fi address
- Disk usage data
WireLurker will then send the collected information to the C&C server. The code structure exhibited by the malware is complex, its versions are containing multiple components, and it uses customized encryption in order to prevent anti-reversing. Researchers believe that WireLurker is being actively developed at the moment. What it would be used for in the future is still a blur.
Users are advised not to download applications from third party stores and under no circumstances to connect their iOS device to PC they do not trust. In case you suspect your device is already compromised, check the processes for questionable files.

