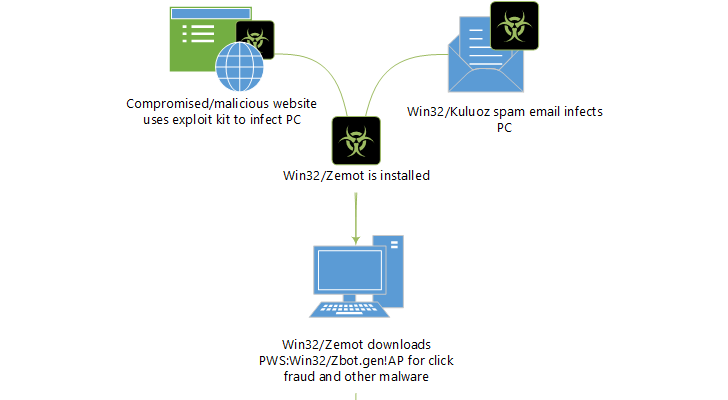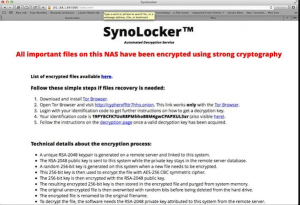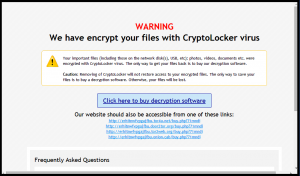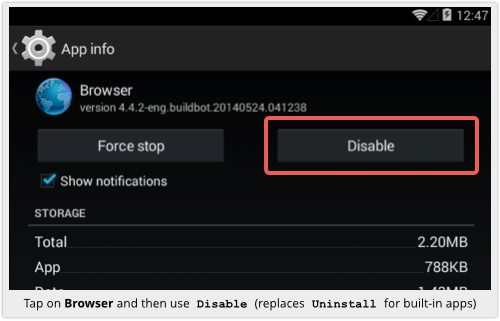
Android Browser with a Flow Attacking User’s Privacy
What Is the Android Browser Security Bug Android Security Bug has been found by the independent security researcher Rafay Baloch and is affecting 50 % of the Android users. The security bug has been found in the Android Browser app,…