Malware attacks are on the rise and as CRO of F-Secure Mikko Hypponen said on Ted talks – “It is no longer a war against our computers, it is now a war against our lives.” To better protect ourselves from this menace we need to understand why some Antivirus Software does not detect malware and why some threats are successful when it comes to infection? We have decided to look into the bottleneck when it comes to infecting a system – obfuscation software.
How Does Obfuscation Work?
Obfuscators have been used for a while now. Their main purpose is to conceal the binary code of programs so that you may be able to prevent the competition from stealing it and copying it. When you use obfuscation in malware, the principle is rather the same. However, they conceal the contents of the malicious files so that they can evade anti-malware software.
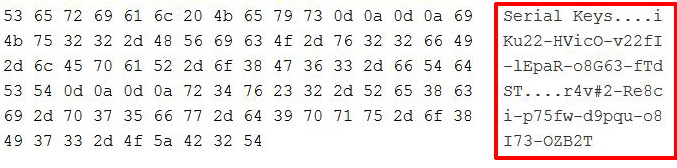
Here is how the hex code of an executable file looks before it has been obfuscated:
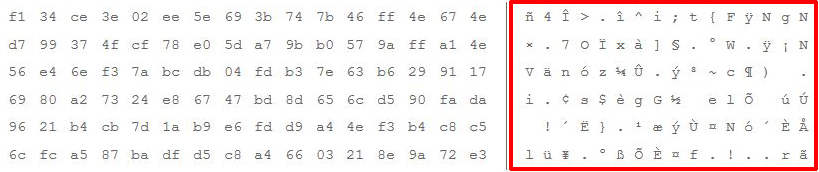
It is clear that you can even read the contents of the file, not to mention other information, such as who created it, and how was it made. However, when you apply the strong DES encryption algorithm to that very same file, here is what happens:
As visible from above, it is not possible to read the contents and anti-malware software is also not able to recognize the file with real-time protection. However, most malware threats have a payload that also drops other data and changes settings, and this is where it becomes complicated for the malware to evade the anti-malware software. Most advanced threats do not only perform obfuscation once, but they do it several times to make the file have several levels of protection.
Also, when it comes to file concealment, one of the most widespread obfuscation methods is called XOR. It basically performs the same operation as we demonstrated with DES above, however unlike DES, its code is easier to decipher. One method of doing this is to use a program that goes through different combinations via a brute force type of attack to decipher the XOR encoded file.
Obfuscators Summary
There are many different obfuscators, and they are often referred to by hackers as Crypters or Packers. They contribute significantly to the successful infection of a given PC. Since if a given obfuscation software is undetected, we strongly advise users to follow the recommended protection tips to avoid malware in the future.