 A very serious bug was discovered in Bash, a much popular command interpreter, posed a serious security risk to the Linux and Unix systems. According to the security experts, this problem should not be regarded as a server issue and dismissed, as Mac OS X uses Bash. The professionals claim that the bug in Bash might be even worse than Heartbleed. It seems that it is present in most Bash versions starting from 1.13 and up to 4.3. This was stated by the Akamai Unix and Linux network and telecom administrator Stephane Chazelas, as she was the first to spot the bug. The Department of Homeland Security and the Computer Emergency Response Team have issue a warning that if exploited, the bug could allow a remote hacker to get a malicious code on the affected system. In fact, the vulnerability database of NIST has rated the bug 10 out of 10 in terms of severity.
A very serious bug was discovered in Bash, a much popular command interpreter, posed a serious security risk to the Linux and Unix systems. According to the security experts, this problem should not be regarded as a server issue and dismissed, as Mac OS X uses Bash. The professionals claim that the bug in Bash might be even worse than Heartbleed. It seems that it is present in most Bash versions starting from 1.13 and up to 4.3. This was stated by the Akamai Unix and Linux network and telecom administrator Stephane Chazelas, as she was the first to spot the bug. The Department of Homeland Security and the Computer Emergency Response Team have issue a warning that if exploited, the bug could allow a remote hacker to get a malicious code on the affected system. In fact, the vulnerability database of NIST has rated the bug 10 out of 10 in terms of severity.
How does Bash affect the system?
The vulnerability is associated with how Bash program handles the environment variables. When a variable is assigned a function, the definition gets an extra code too. The attacker has the simple task to append several commands – this is the so called classic code-injection attack. By doing so, the attacker will be able to hijack remotely the affected machine.
All researchers who have looked at the flow confirmed that the Bash bug can be easily exploited if the code is injected in environmental variables. This might include different scripts which set the environment for DHCP clients or ForceCommand feature in OpenSSH sshd, the mod_cgid and mod_cgi modules in Apache HTTP Server.
As the chief of the Cloud Security Alliance, Jim Reavis, stated in his blog, there are many programs on UNIX and Linux systems that use Bash to set environmental variables and then these variables are used at the execution of other programs.
Bash – Heartbleed Comparison
The servers of UNIX and Linux are used in the data centers throughout the world and are embedded in many devices. This vulnerability has been known for a long period of time. Since Bash is quite widespread, many security researchers are making a comparison with Hertbleed. This is an OpenSSH vulnerability which was discovered in April. Some of the experts are wondering if Bash is the second edition of Hearbleed. However, it is very hard for this to be told. Bash is a serious issue, as it offers the attaches an access to the command shell, which allows the cyber criminals to do whatever they want on the machine.
If we compare the size, the Apache Web servers give power to most of the websites on a global basis. Professionals know that there are plenty of machines that are not based on UNIX and Linux, which use Telnet and OpenSSH. At the same time DHCP allows users to hop on and off the available networks. With all that being said, we should be aware that besides the servers and computers there are other embedded systems including routers, which are vulnerable to hijacking.
One of the most detailed analyses of the Bash bug, Errata Security’s Graham, performed various scans and found several thousand vulnerable servers. Even so, it is still quite difficult for the security experts to estimate the seriousness of the problem. The experts say that Heartbleed bug was present only when a OpenSSL vulnerable version has been installed. This, however, is not the case with the Bash bug. With the Bash bug, the machine is vulnerable if it has an application that takes in user input and setting in in an environment variable. The web fames are generally not affected. The users should know that not all routers and embedded devices use Bash. In fact the Debian-derived systems might use other interpreter called Dash. The devices that are embedded usually use BusyBox that is not vulnerable.
Bash – vulnerable or not?
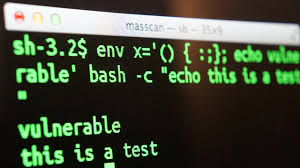
→The users can check if they are vulnerable to the Bash bug by following several commands, which are provided by CSA. They should open a terminal window and enter the following command at the $ prompt:env x='() { :;}; echo vulnerable’ bash -c “echo this is a test“.
In case the machine is vulnerable, there will be a text:
vulnerable
this is a test
In case the user has updated Bash he will just see:
this is a test
The expert Red Hat commented that, if the user has several machines, it might be worth it going ahead and applying the available patches. However, if the user has thousands of machines to patch, then maybe it’s worth waiting for several more hours. In fact, the main Linux distributions are now trying to work on a fix. The security consultants warn the users that even if they have not heard about Bash and do not run it, still the user might have software running on the computer which has the Bash processes.

