A new type of attack could allow a malicious actor with a mid-range thermal camera to capture keys pressed on a standard keyboard. The discovery has been made by three University of California professors. In other words, our fingers’ thermal residue on keyboard keys can be recorded by a hacker who can later use it to reveal the user’s passwords or any other text he/she has typed.
The Thermanator Attack Explained
“If you type your password and walk or step away, someone can learn a lot about it after-the-fact,” said Professor Gene Tsudik of the academic team.
The attack has been called Thermanator and it can be used to retrieve sensitive user information such as passwords and PINs, as well as short strings of text. The Thermanator attack requires several conditions to be met in order to function properly. First, attackers need to place a specialized camera with thermal recording capabilities near the victim. The camera should also be able to capture the keys of the victim’s keyboard, otherwise it won’t work.
According to the researchers’ explanation of the Thermanator attack (see paper), it is a distinct type of insider attack, where a typical attack scenario proceeds in the following steps:
STEP 1:The victim uses a keyboard to enter a genuine password, as part of the log-in (or session unlock) procedure.
STEP 2:Shortly thereafter, the victim either: (1) willingly steps away, or (2) gets drawn away, from the workplace.
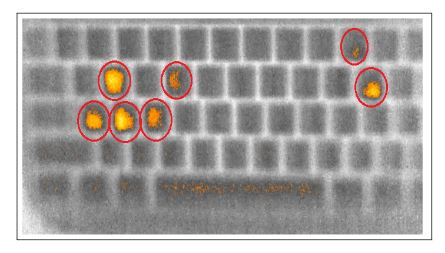
STEP 3:Using thermal imaging (e.g., photos taken by a commodity FLIR camera) the adversary harvests thermal residues from the keyboard.
STEP 4:At a later time, the adversary uses the “heat map” of the images to determine recently pressed keys. This can be done manually (i.e., via visual inspection) or automatically (i.e.,
via specialized software).
With these requirements being met, the attacker becomes able to uncover keys pressed by the victim even without special hacking knowledge. The captured keys can be assembled into possible strings and can be deployed in a dictionary attack. A dictionary attack is a popular technique for deciphering ciphers and authentication mechanisms by attempting to determine the decryption key or passphrase. This is done by using hundreds or even millions of likely possibilities.
The researchers carried out several experiments where they had 31 users enter passwords on four different keyboard models. Then, eight non-experts in hacking were asked to obtain the set of pressed keys using the recorded data from the thermal camera. The results of these tests revealed that thermal data recorded up to 30 seconds after the text entry is sufficient for an unprofessional attacker to recover entire set of keys the targeted user has pressed.
If you are the type of user who presses one key at a time using only two fingers are more susceptible to the Thermanator attack.
Is there any conclusion to the researchers’ Thermanator discovery?
Shortly put, the research “exposes the vulnerability of standard password-based systems to adversarial collection of thermal emanations”. Based on the results of the study, the researchers believe that these attacks “represent a new credible threat for password-based systems”, suggesting that it may be time to re-evaluate the use of passwords.