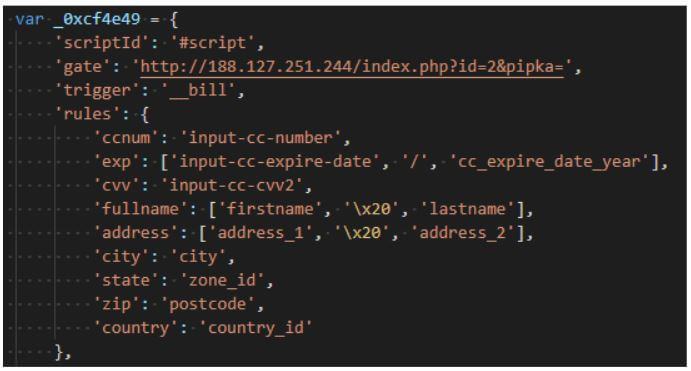
Pipka is the name of a new JavaScript skimmer, currenting targeting e-commerce websites. The skimmer is stealing payment card details, such as account number, card expiration date, CVV number, and cardholder name and address from websites’ checkout pages.
The Pipka skimmer was discovered by Visa Payment Fraud Disruption (PFD).
Pipka Skimmer Detected in the Wild
According to Visa’s report, the skimmer was first discovered in September this year. The skimmer has been named Pipka “due to the skimmer’s configured exfiltration point at the time of analysis.”
Pipka was identified on a North American merchant website that was previously infected with the JavaScript skimmer Inter, and PFD has since identified at least sixteen additional merchant websites compromised with Pipka. PFD previously reported on the use of Inter [another skimmer] to target service providers with malicious skimming code that was integrated into eCommerce merchant environments.
It is noteworthy that Pipka is capable of removing itself from the HTML of the compromised websites after execution, which makes it harder to detect. This behavior is not seen in most known skimmers.
The Pipka skimmer is configured to check for the payment account number field. All data harvested by the skimming malware is encoded with the help of base64 algorithm using ROT13 cipher. Before exfiltration, the malware performs a check to make sure that the data string hasn’t been previously sent to avoid sending duplicate data. If the string is unique, the data is exfiltrated to a command and control server, the PFD report said.
The most intriguing part of the skimmer, however, is its ability to eradicate itself from the HTML code of the compromised website. This is done after successful execution, and enables the malware to improve its evasive behavior. This feature hasn’t been detected in the wild, and is a “significant development in JavaScript skimming”.
PFD researchers believe that the Pipka skimmer will continue to be used in future attacks against e-commerce websites to harvest payment account data.
In November 2018, security researchers discovered that the Magecart malware was able to re-infect infected websites, after the skimmer was removed.


