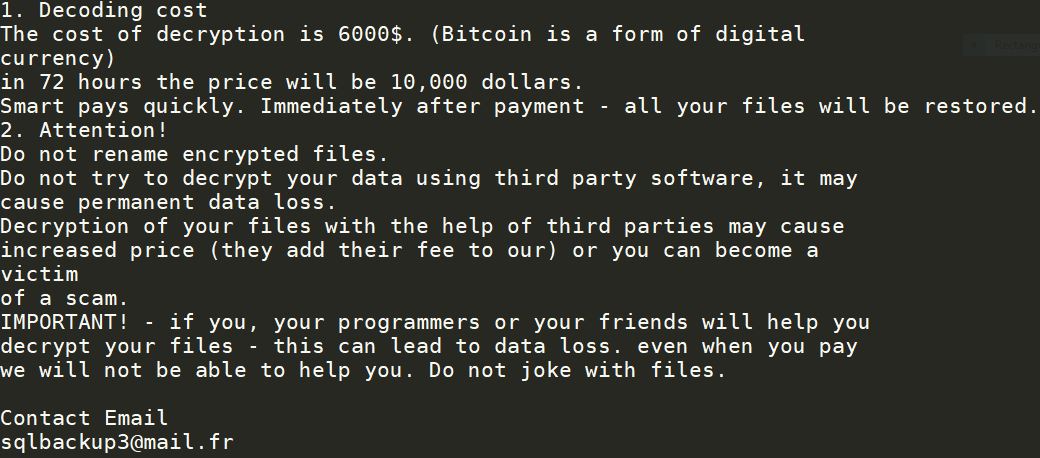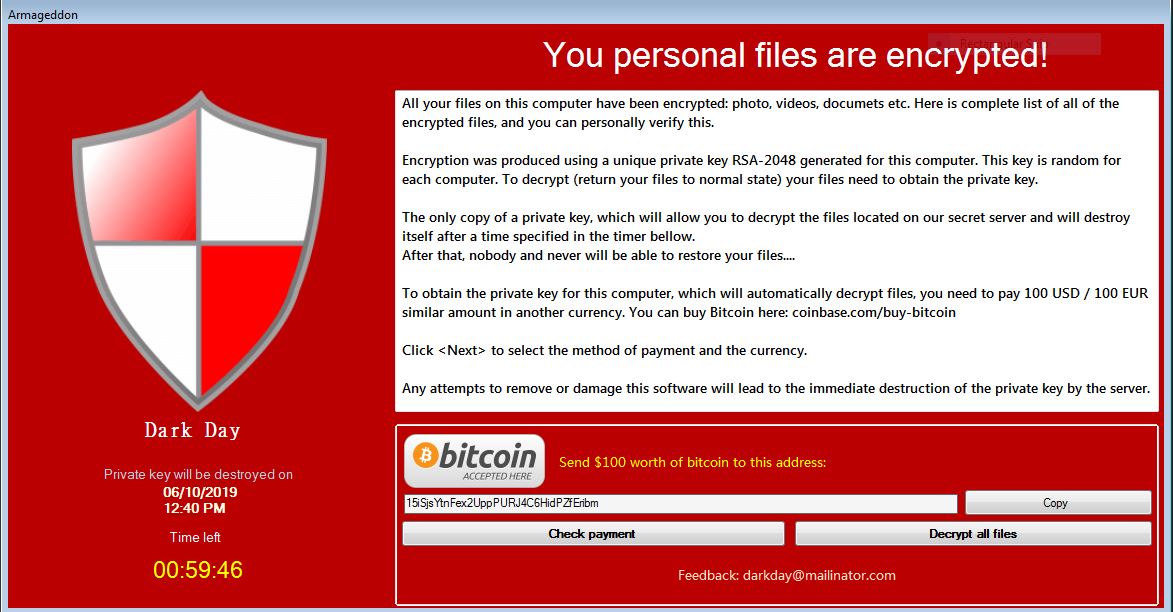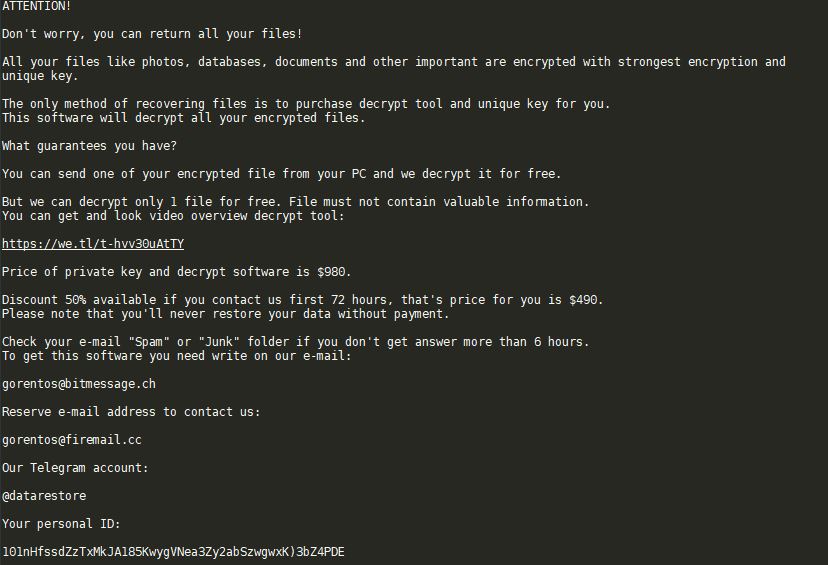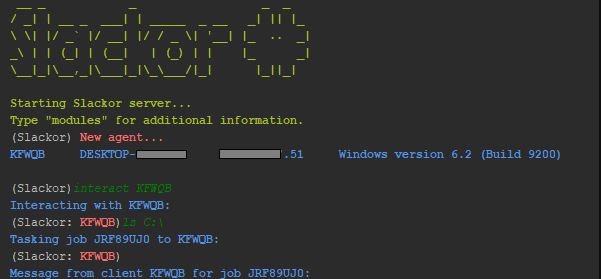
Slackor RAT Allows Hackers to Use Slack Servers
The Slackor RAT is a tool developed primarily for security researchers allowing for malicious actors to use Slack as a server backend. In real-world scenarios it can also be utilized by hackers in large-scale attacks. This can be extremely dangerous…