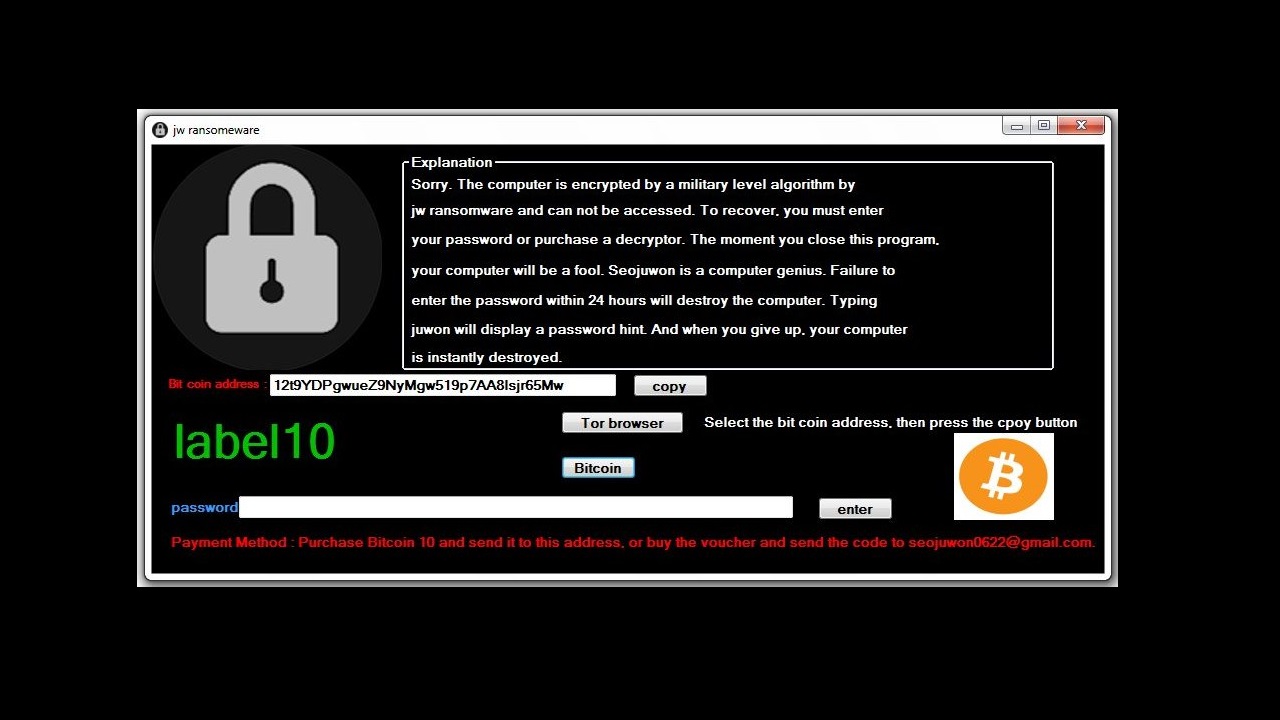
Remove Juwon Ransomware Infections
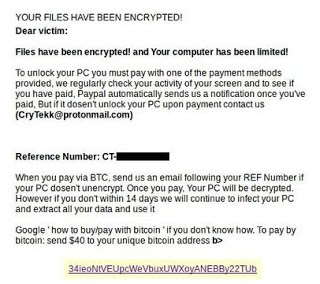
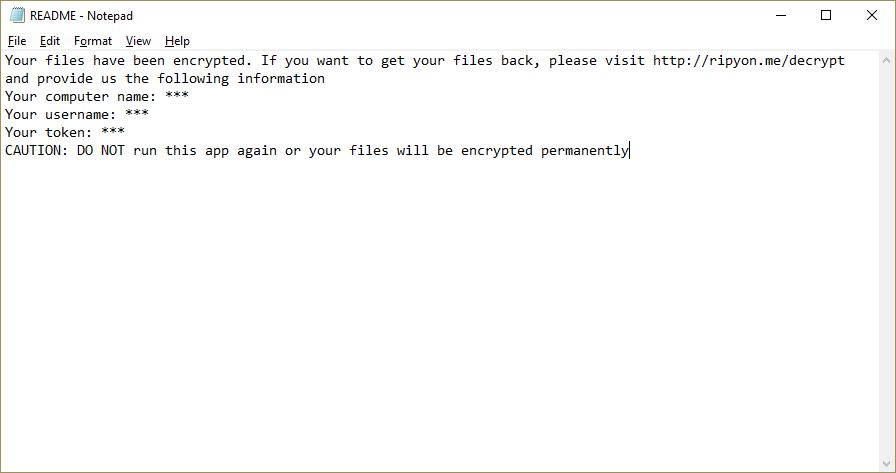
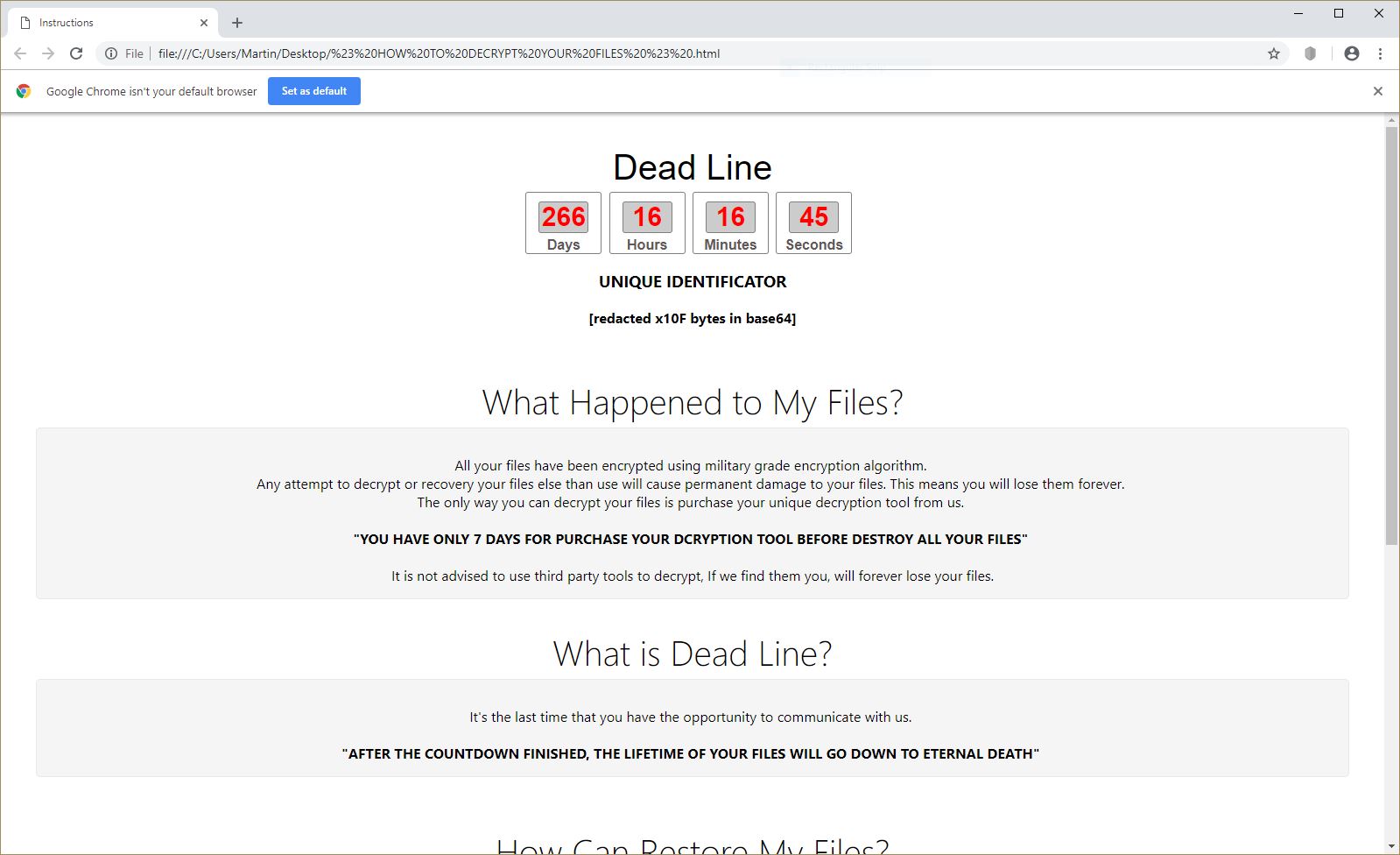
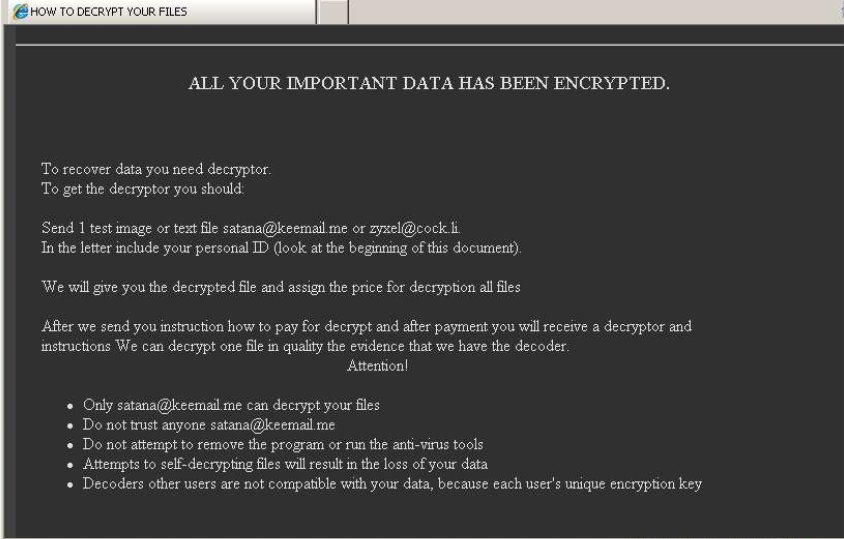
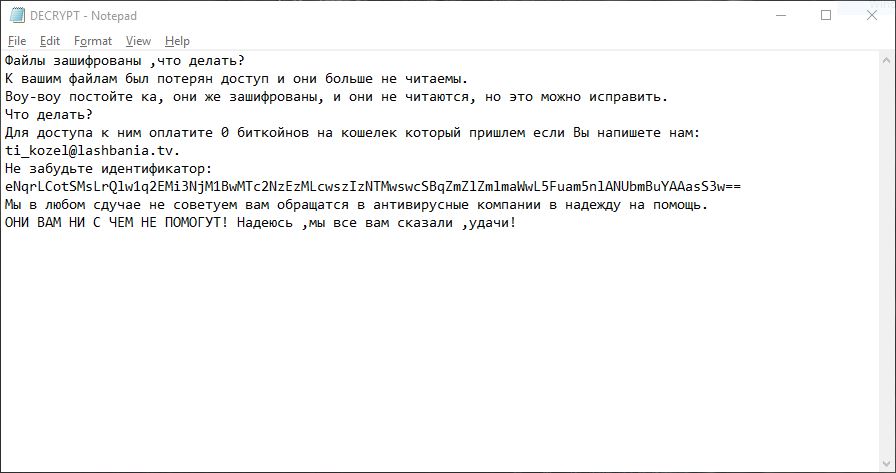
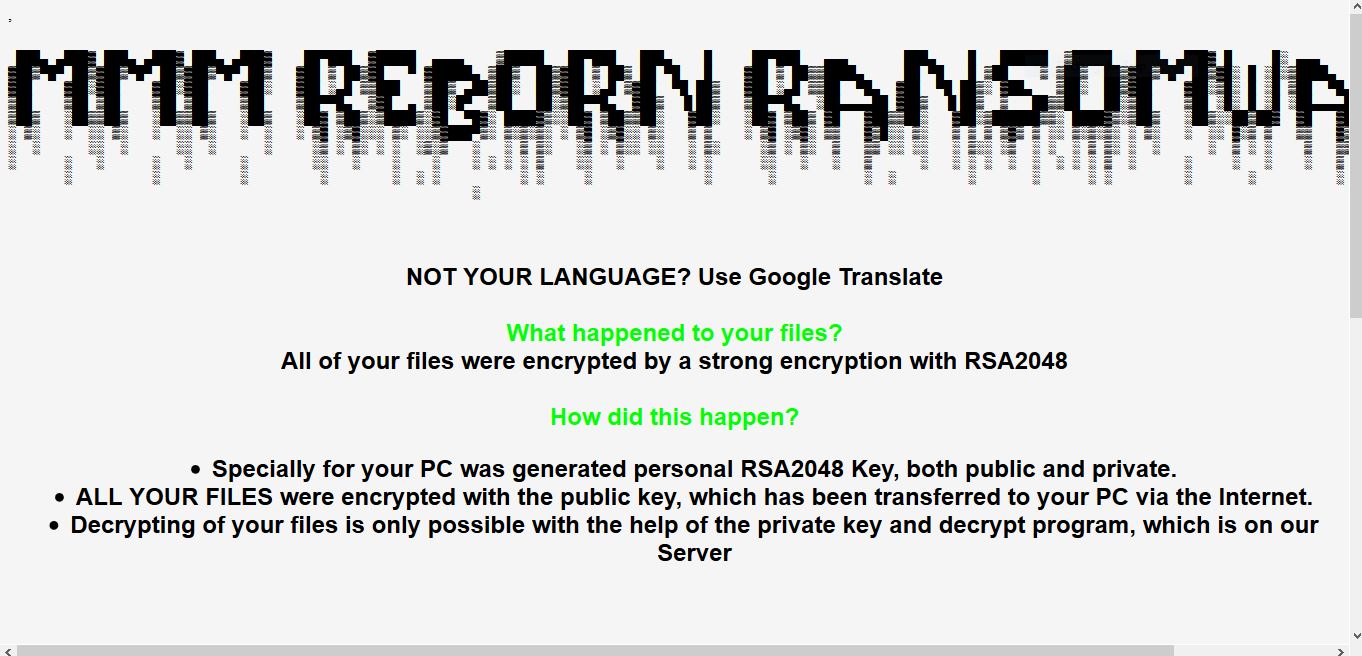
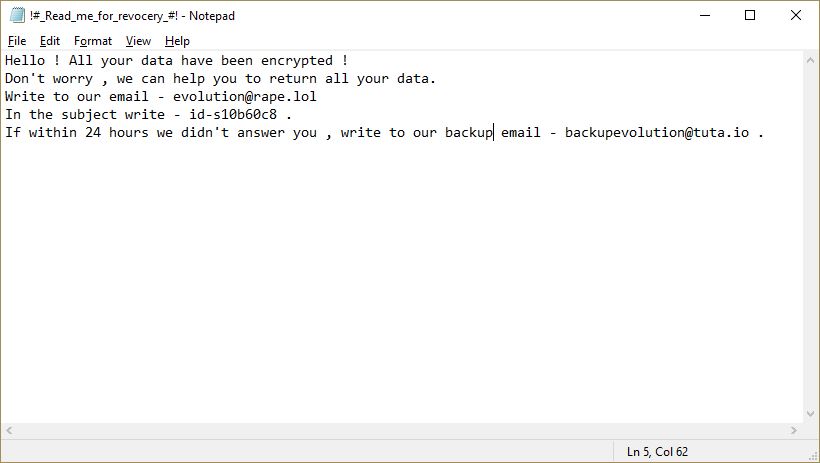
This article will aid you to remove Juwon Ransomware. Follow the ransomware removal instructions provided at the end of the article. Juwon Ransomware is one that encrypts your data with and demands money as a ransom to get it restored.…