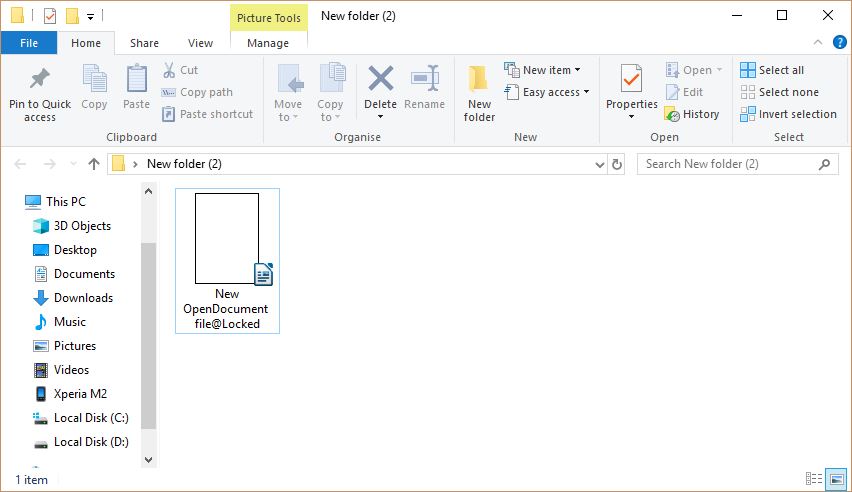
New Gandcrab 5 Strains Distributed As Ransomware-as-A-Service
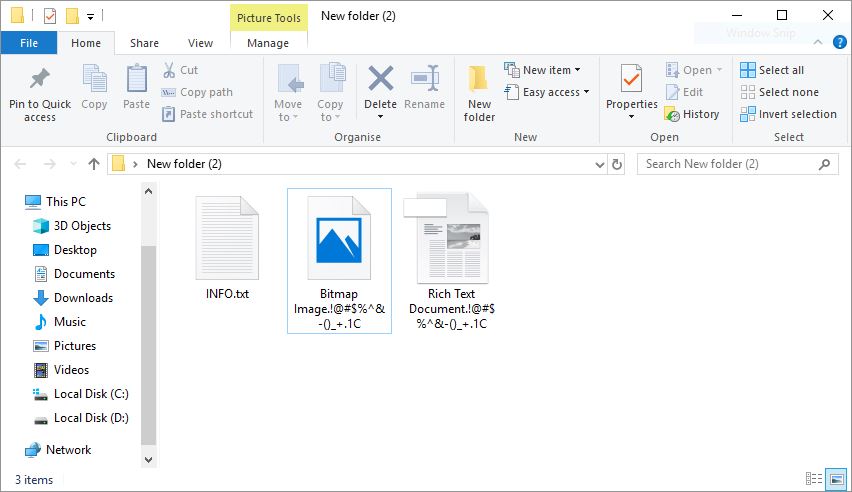
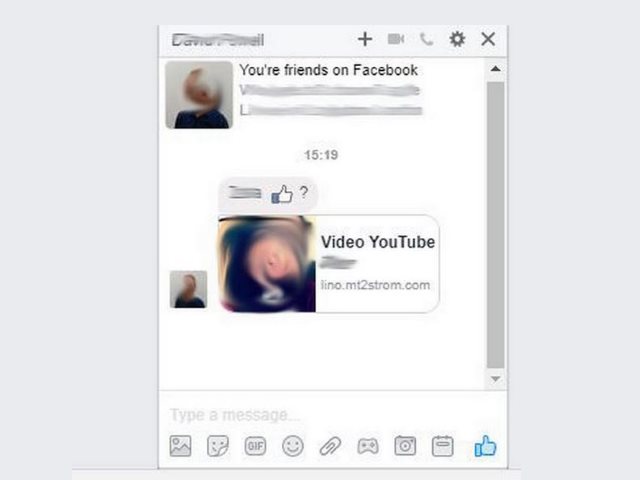
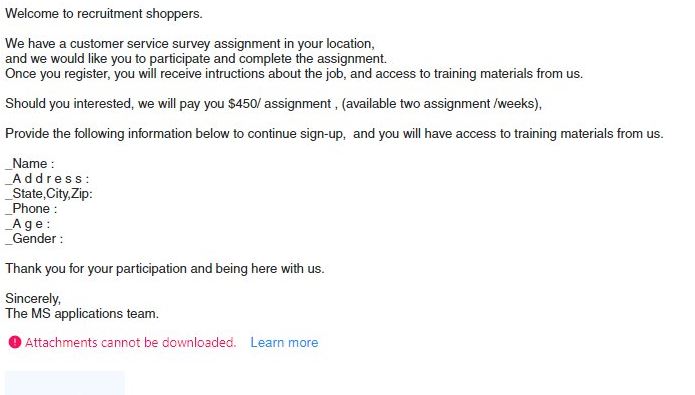
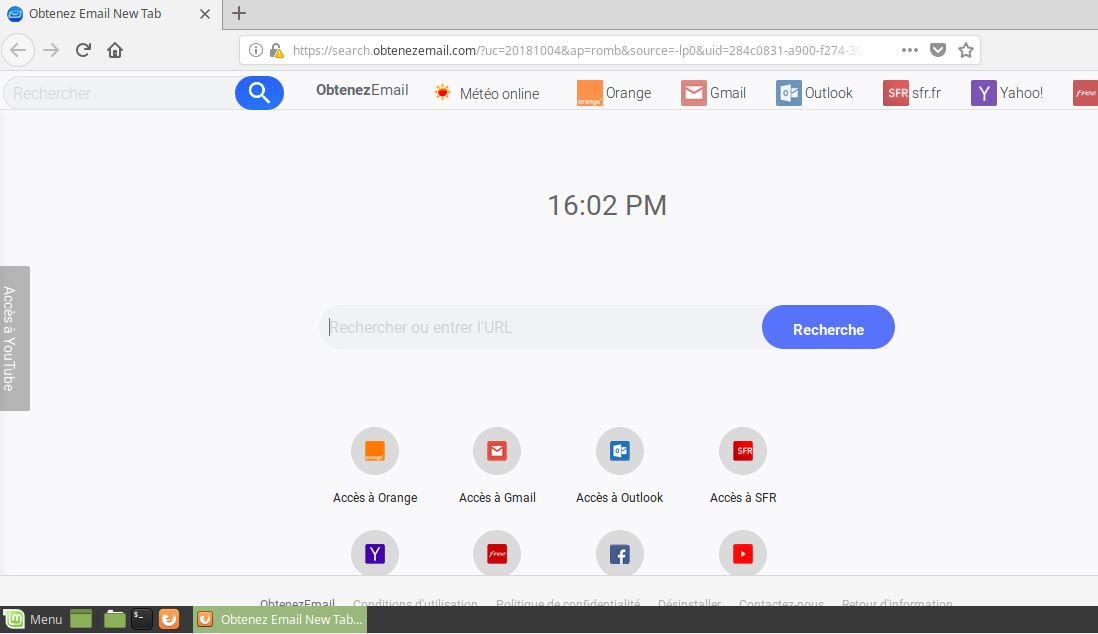
GandCrab 5 ransomware strains were recently released by different hacker collectives as ransomware-as-a-service. The available research shows that the developers behind them are probably offering them in underground markets in the form of RaaS. Gandcrab 5 Ransomware Used In RaaS…