Steam Vulnerability Allowed Malicious Operators to Gain License Keys
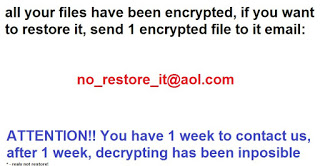
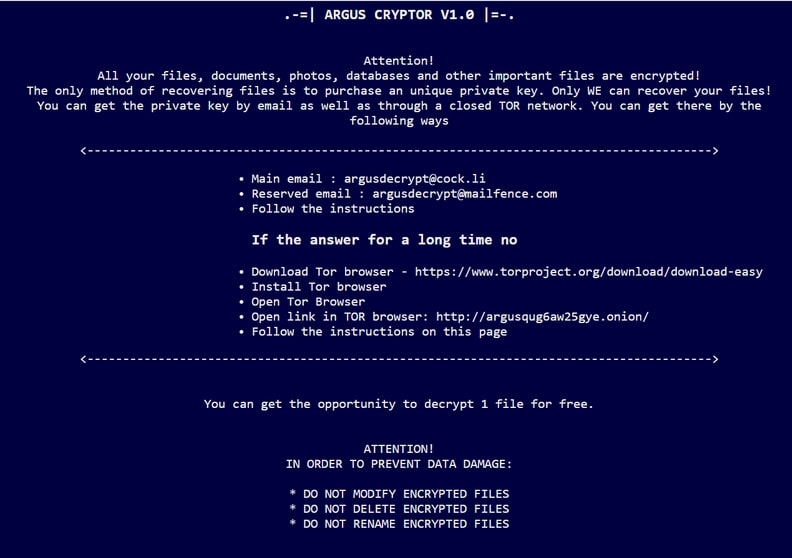
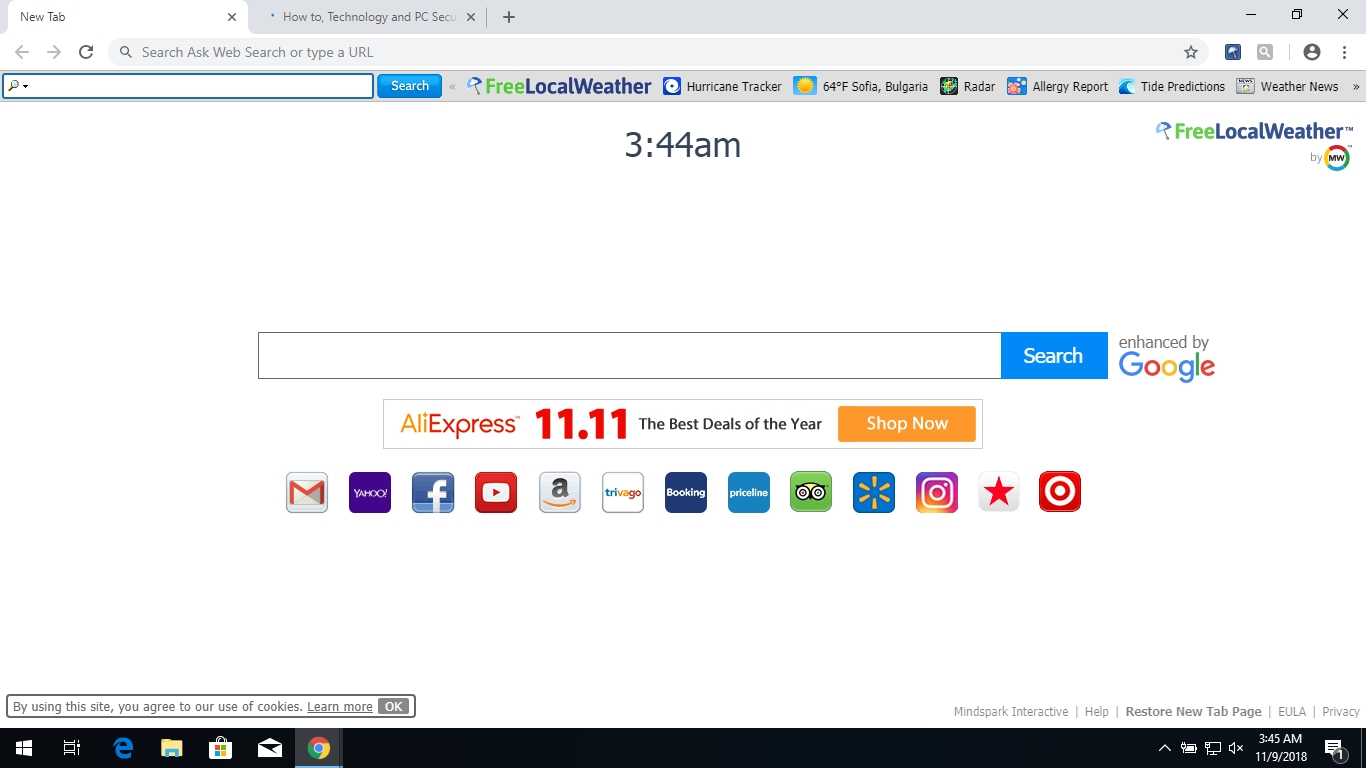
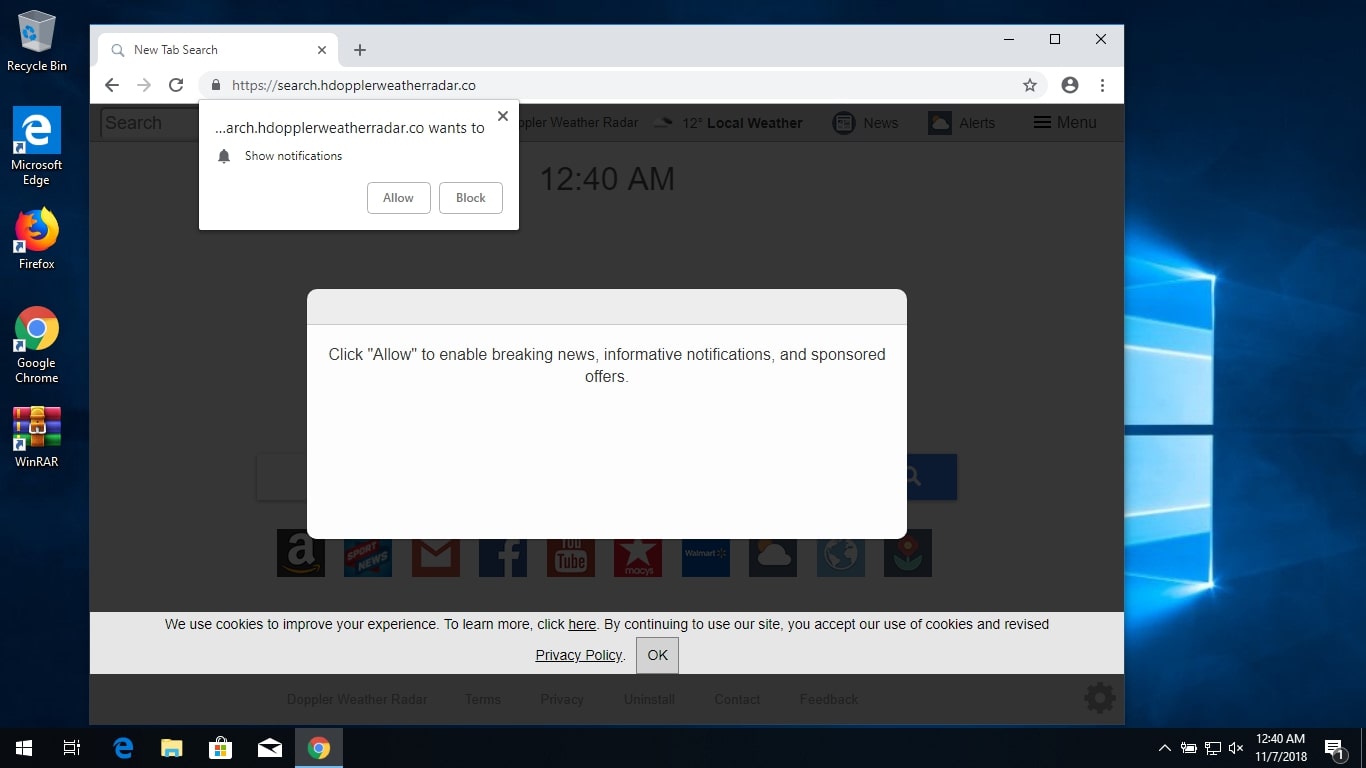
A security researcher discovered a dangerous Valve vulnerability allowing malicious users to reveal the license keys for the available content on the store. This means that every computer game or software can be acquired by leveraging it. The expert has…